Distributed credibility authentication method and system thereof based on software product library
A software product and product library technology, applied in the field of security certification, can solve problems such as difficult to achieve widely adaptable security products, large blacklist, computer security threats, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
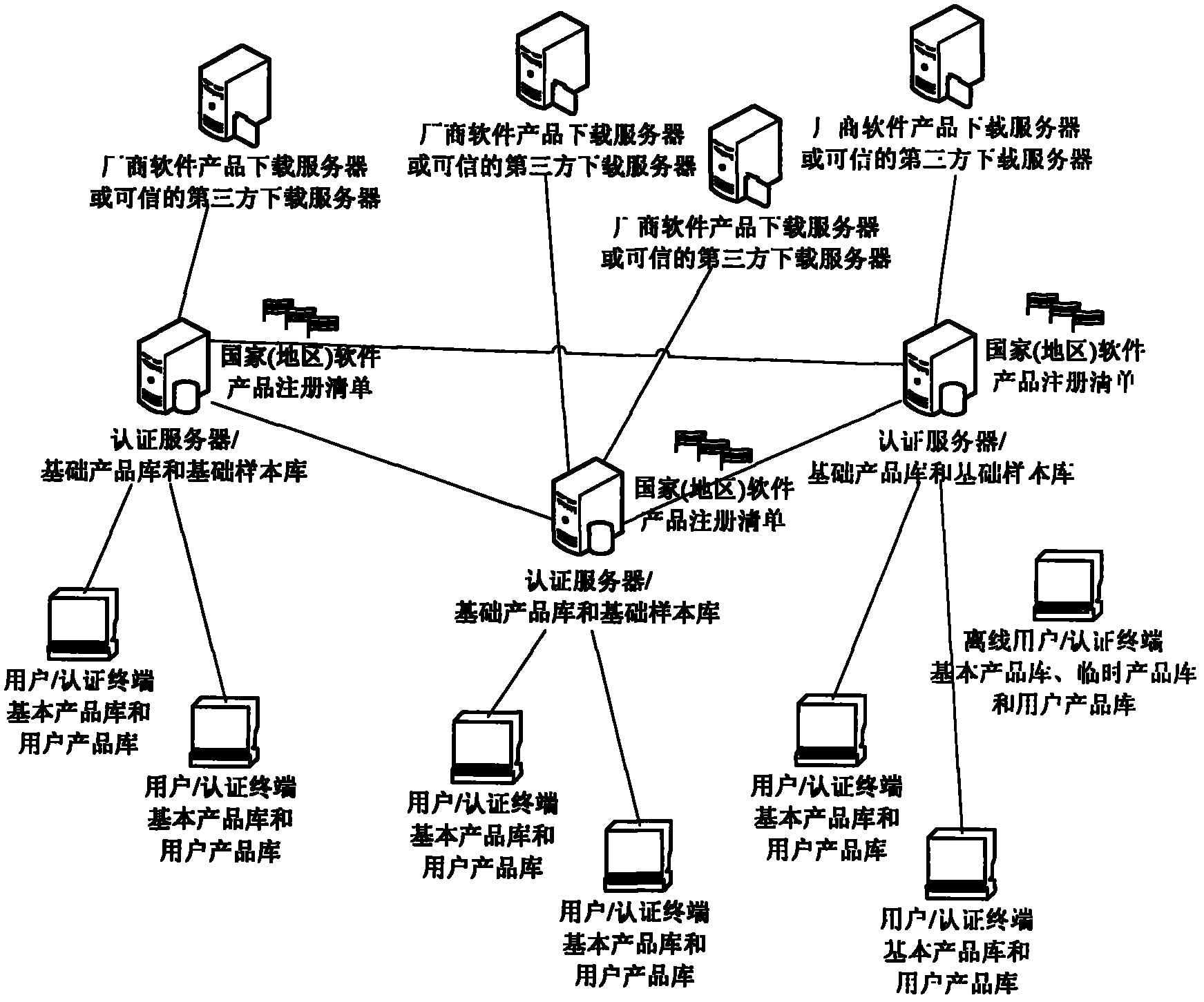
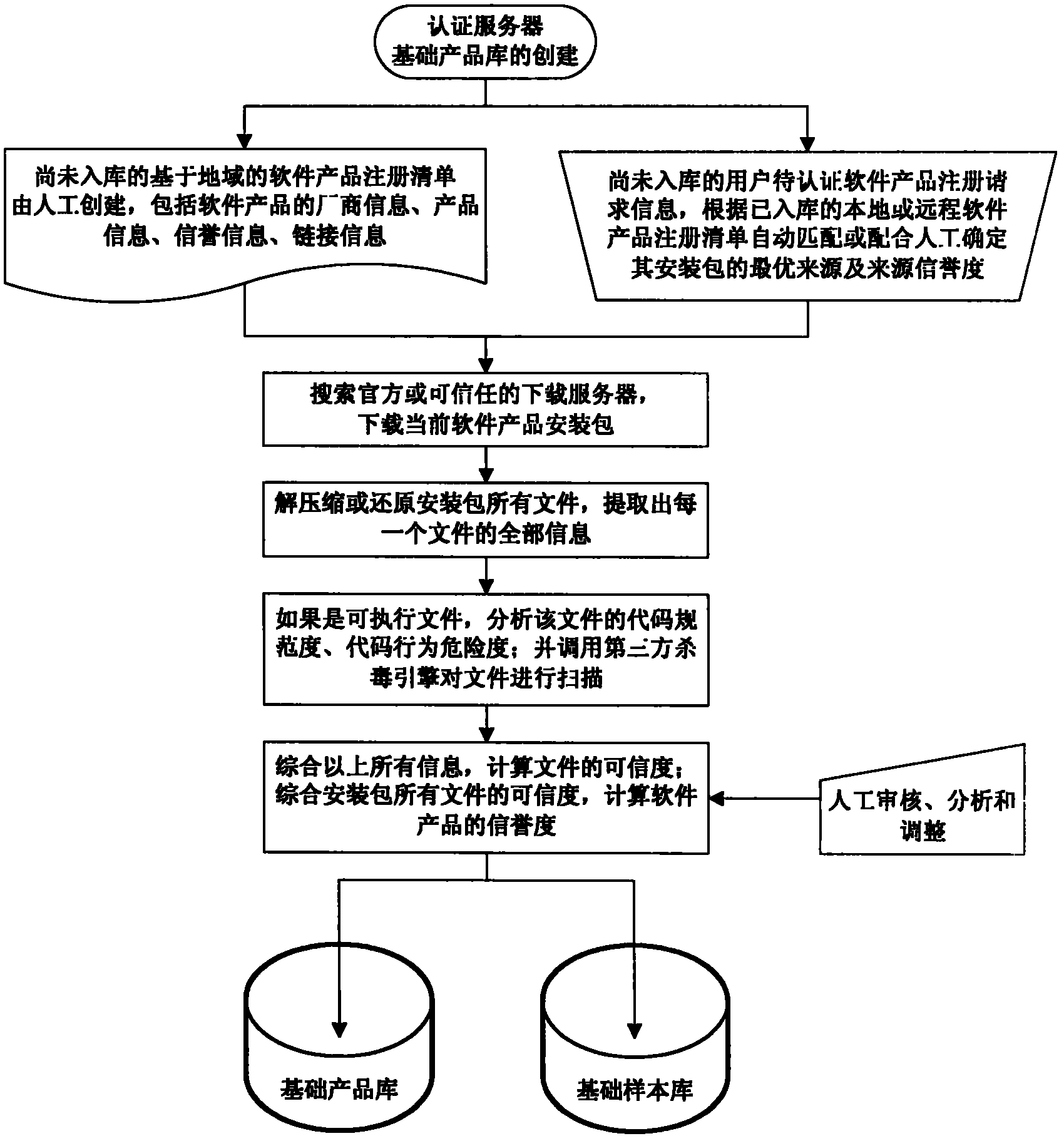
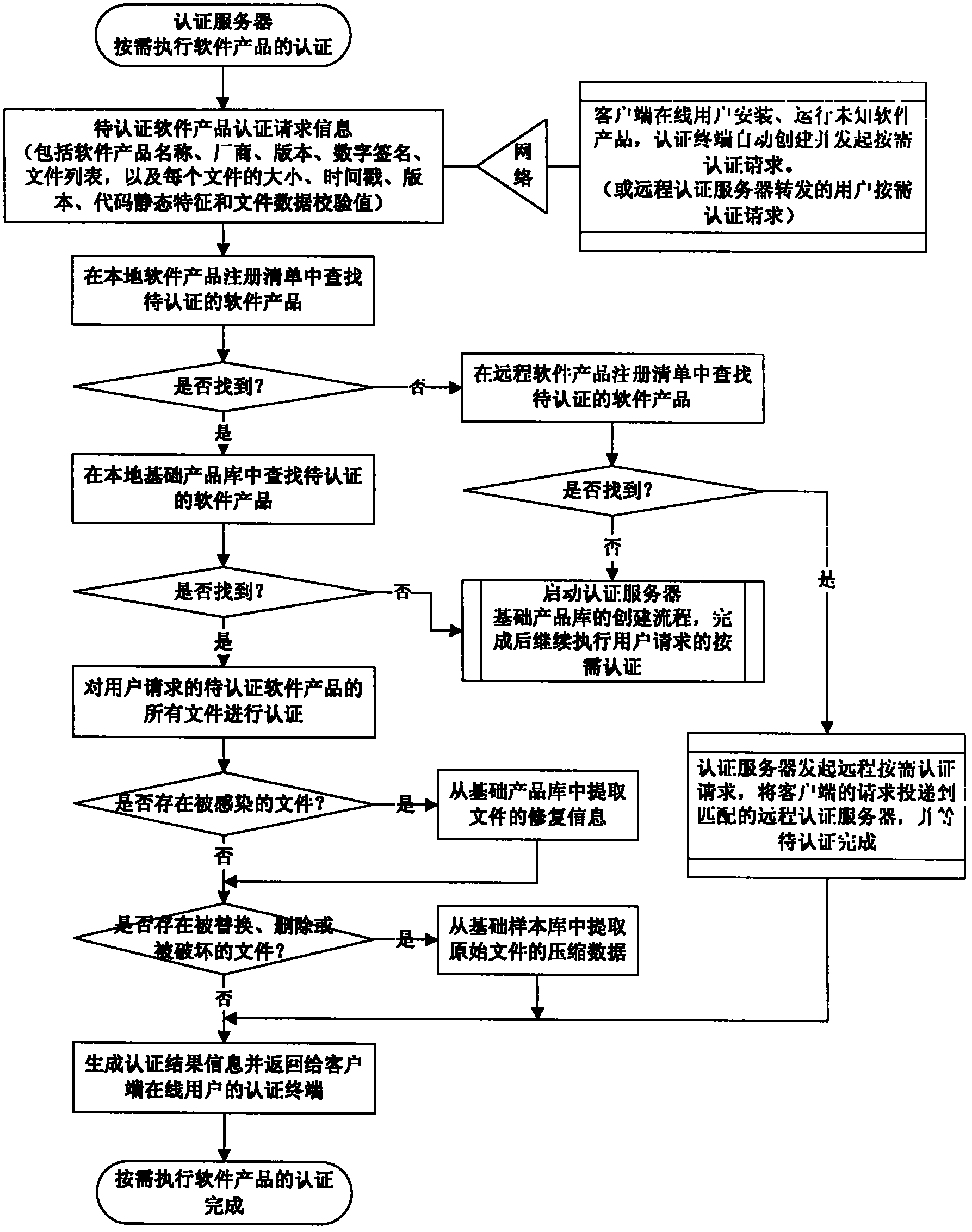
[0069] Attached below Figure 1-5 Embodiments of the present invention are further described.
[0070] The invention provides a distributed trusted authentication method and system based on a software product library, which can quickly scan the file system, application software, and operating environment of any computer user, and terminate and uninstall all unidentified files according to the security level required by the user. Executable code that meets the current security level, isolates all executable files that do not meet the current security level, protects user information and key data at a higher security level, prohibits running all executable code that does not meet the current security level, cooperates with active defense and The network firewall technology can eliminate all potential safety hazards on the user's computer, and realize a truly safe and reliable operating system environment that can run any software product without barriers, with different security...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com