A Composite Intrusion Detection Method Based on Bagging Algorithm
An intrusion detection and composite technology, applied in the field of network information security, can solve the problems of high false negative rate and false positive rate, low intrusion detection accuracy, and poor generalization ability, so as to achieve improved speed, high discrimination accuracy, and reduced error The effect of positive rate and false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The specific embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings.
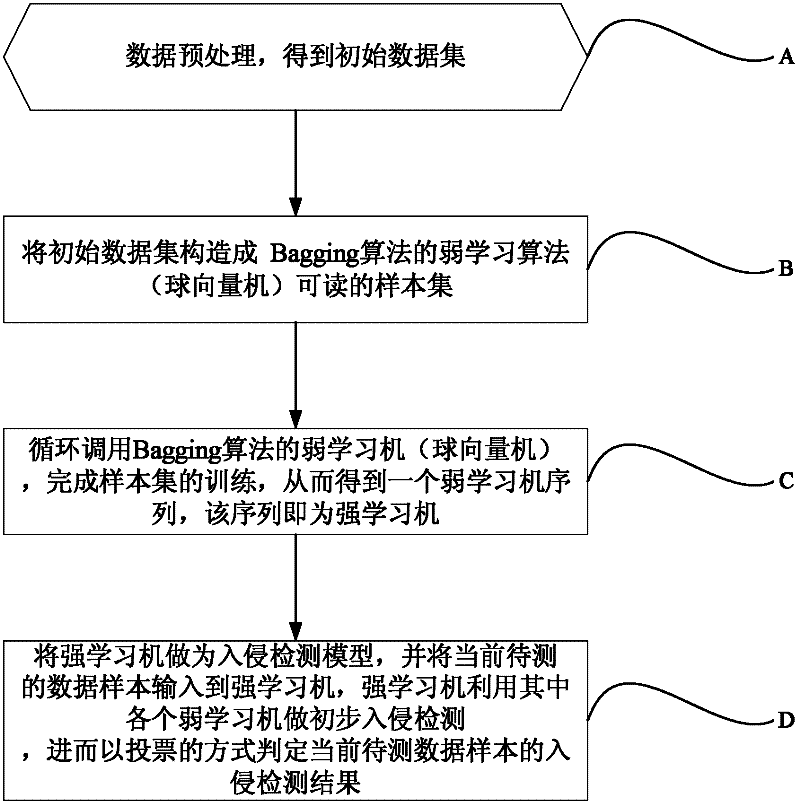
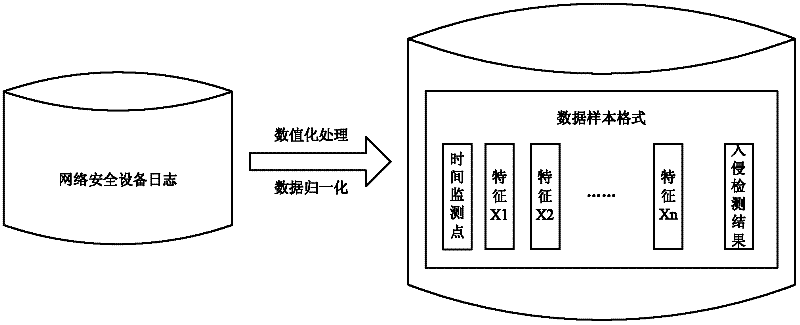
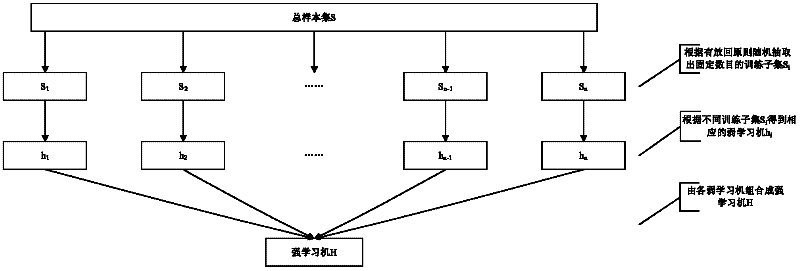
[0050] The present invention theoretically abstracts the intrusion detection problem into a multi-classification problem in pattern recognition, abstracts various influencing factors of intrusion detection and discrimination into an input vector of a multi-classification problem, abstracts the intrusion detection result into an output vector of a multi-classification problem, and then The artificial intelligence algorithm is used to fit the functional relationship between the independent variable and the dependent variable, so that the network security device record to be tested only needs to input its corresponding input variable, and the intrusion detection result of the record can be obtained. Therefore, the artificial intelligence method based Intrusion detection has the advantages of fast computing speed and high reliability. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com