Implementation method for security private cloud system
An implementation method and technology of a cloud system, applied in the field of cloud systems, can solve the problems of complex security problems of cloud systems, inability to ensure illegal copying by illegal users, and difficulty in solving problems.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
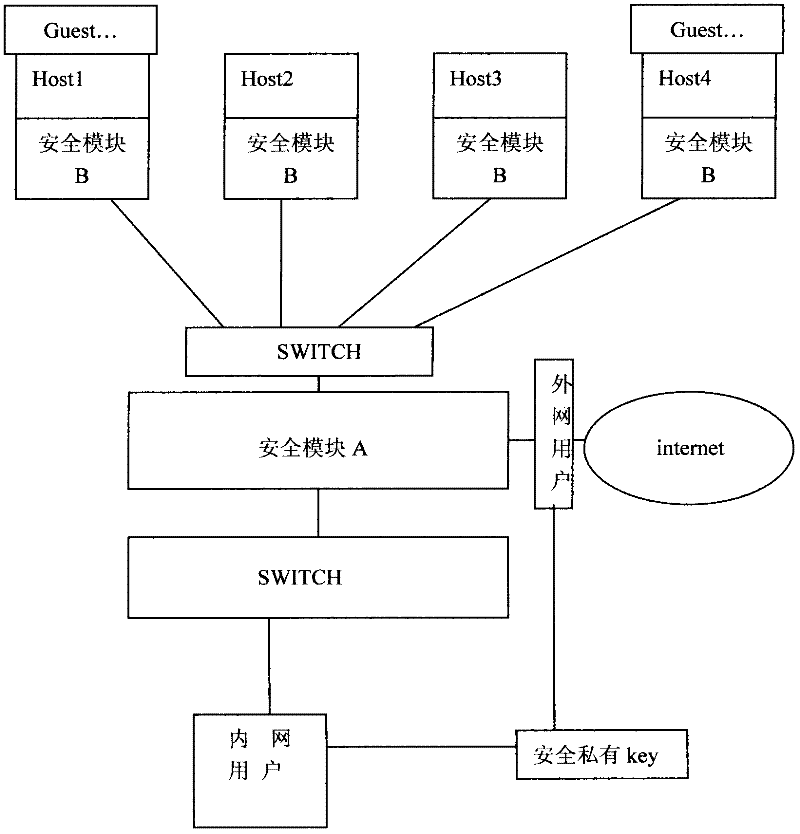
[0019] Such as figure 1 As shown, the implementation method of the secure private cloud system described in the embodiment of the present invention, as can be seen from the figure, if users and external network users want to access HOST, they can only pass through security module A and security module B; if cross-machine HOST or GUEST Access to each other can only be through security module B;
[0020] Through the use of dynamic port technology, access process code HASH summary and server-side verification technology and timing control technology after verification, the user's 3389 port fraud is prevented; after the user logs in, the user name UUID and password and the login program's own HASH summary + access time period + the IP of the accessed machine + time stamp, encrypted by the pki module of the client, and sent to the security module A, the security module finds its public key with the corresponding user name UUID, and then decrypts, verifies the password, and the HASH...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com