Security audit system and method based on cloud computing
A security auditing and cloud computing technology, applied in the information field, can solve problems such as increasing the difficulty of public security law enforcement, polluting the Internet environment, etc., and achieve the effects of multiple data access methods, improved processing efficiency, and good data sharing.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
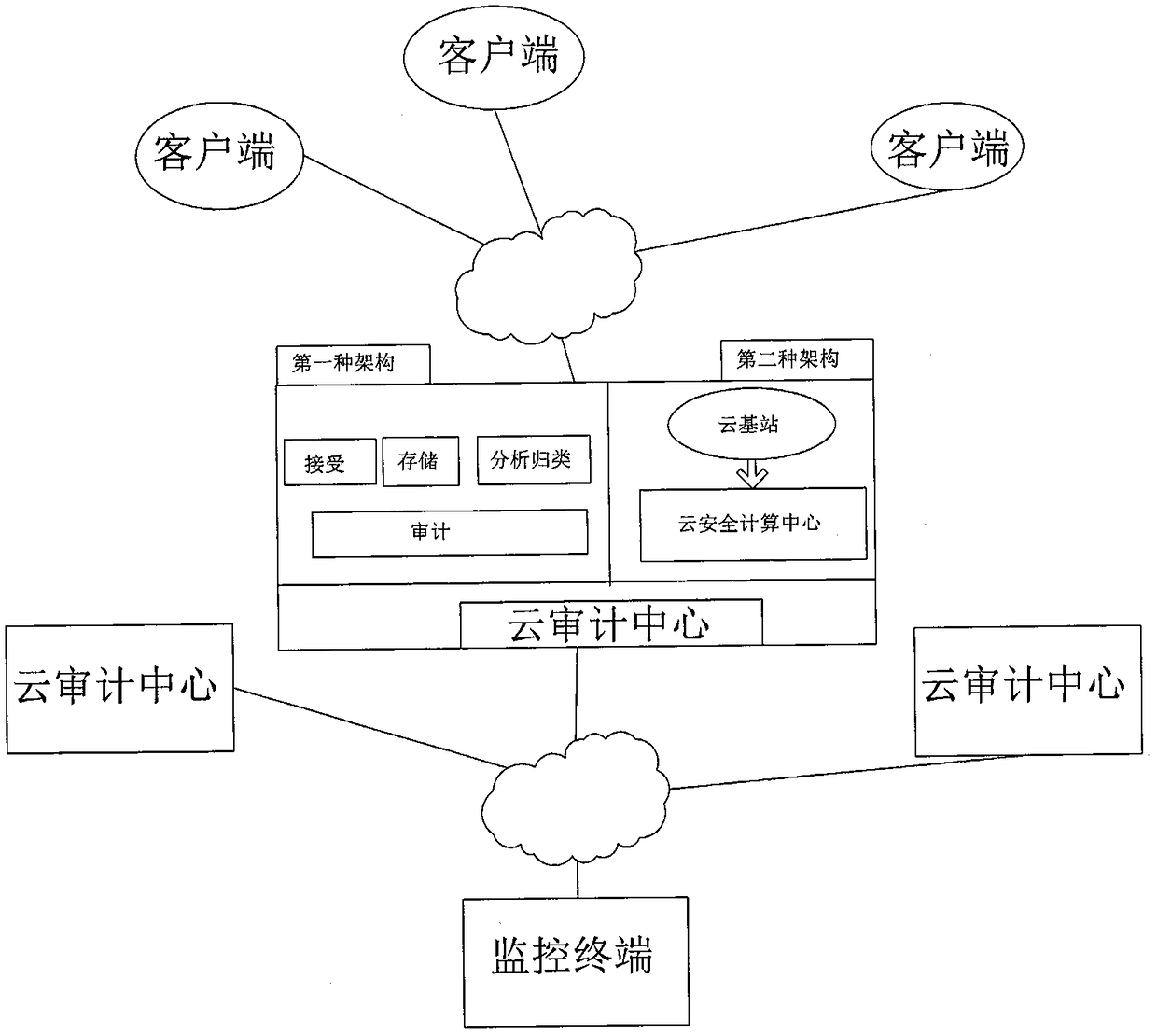
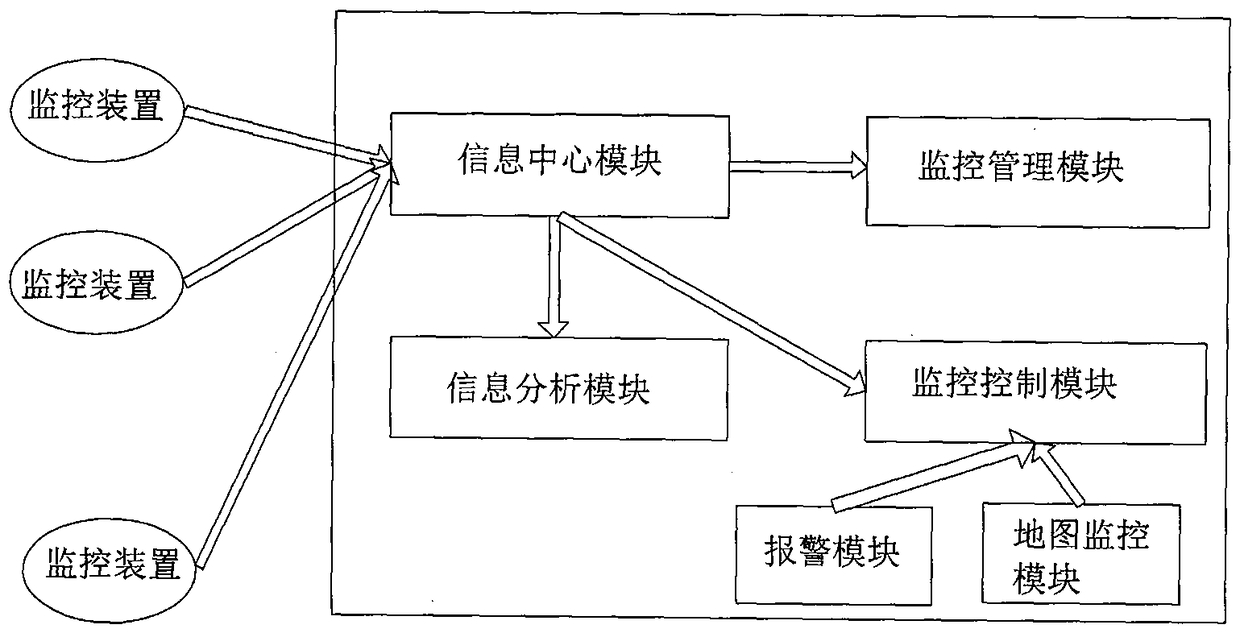
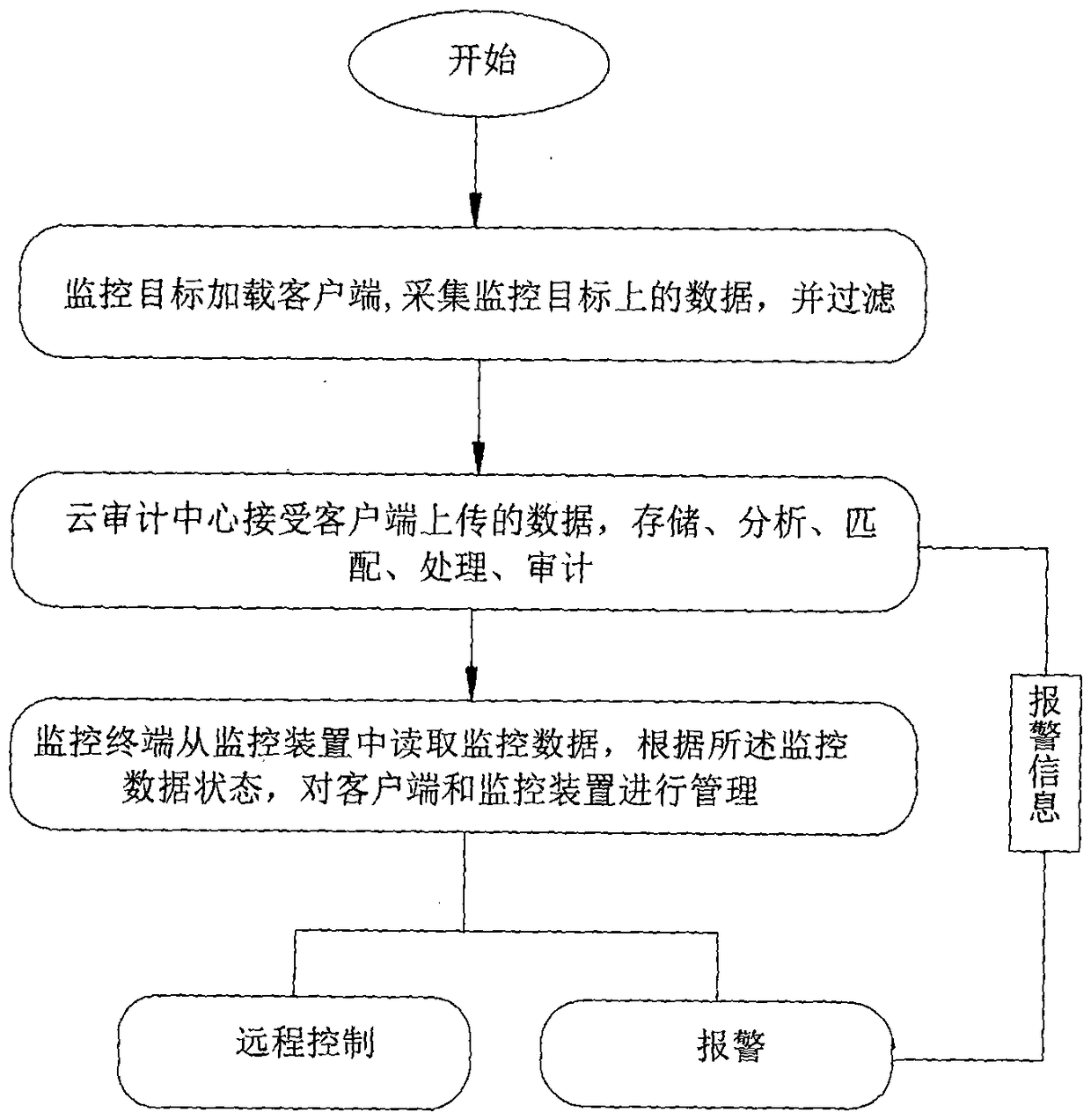
[0043] see figure 1 , The present invention relates to a security audit system and method based on cloud computing, which is mainly composed of a client, a cloud audit center and a monitoring terminal. The client is loaded on the monitoring target system, the client and the cloud audit center establish a connection through the communication network, and use the Internet to communicate, a one-to-many connection mode is formed between the client and the cloud audit center, and the monitoring terminal and the cloud audit center Establish communication connections between the centers, and use the Internet or 3G wireless network to communicate, also forming a one-to-many connection mode.
[0044] The client is used to complete the monitoring data collection of the monitoring target system by obtaining the current running status of the monitoring target system, behavior operation trigger events, underlying hardware instructions, and data protocol and process analysis and analysis, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com