Reconfigurable cipher processor and anti-power consumption attach method
An anti-power consumption and anti-attack technology, which is applied in the fields of electrical digital data processing, instruments, digital data authentication, etc., can solve problems such as side-channel attacks that have not yet been seen, and achieve strong anti-attack ability, low circuit overhead, and high flexibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment example
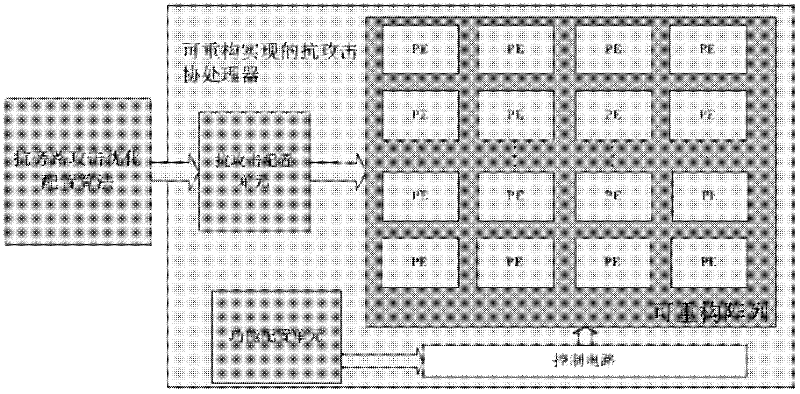
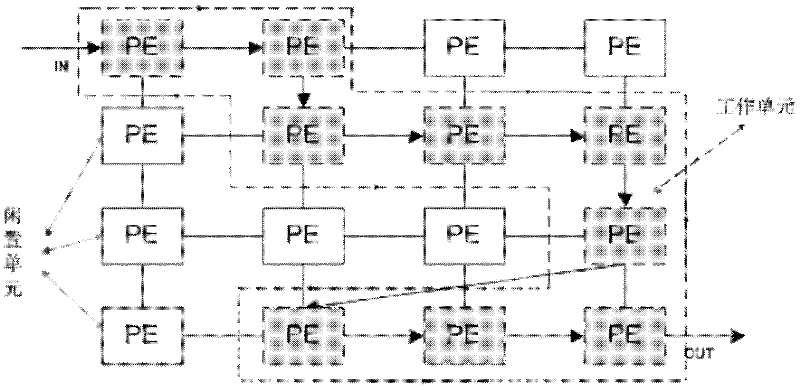
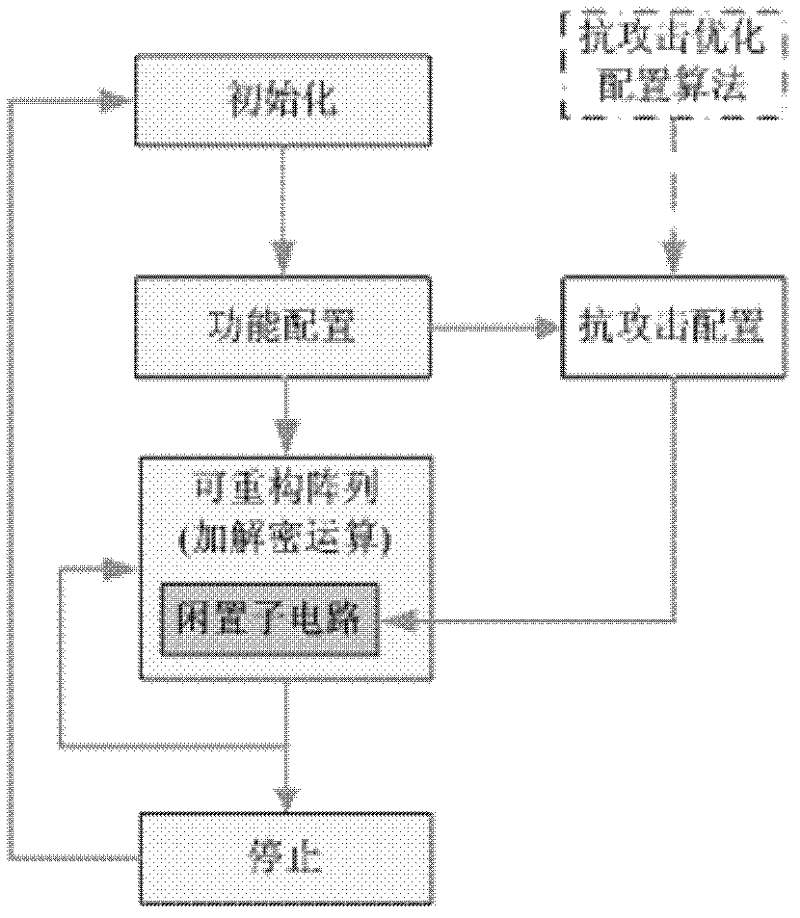
[0033] In a specific implementation case of a method for resisting power consumption attacks of a reconfigurable cryptographic processor, a specially designed coarse-grained reconfigurable array cryptographic processor is used, and various algorithms such as AES and DES are implemented. The following uses DES Taking the specific implementation of the algorithm as an example, the anti-attack method of the present invention is illustrated by using the differential power analysis attack based on the Hamming distance power consumption model as the attack means. According to the Hamming distance power consumption model of CMOS circuits, the total number of 0→1 transitions and 1→0 transitions of the registers in the circuit within a certain period of time is used to describe the power consumption of the circuit during this period. Therefore, for power consumption attacks, in this case, only the usage of registers in the cryptographic processor is concerned. The registers used by the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com