Detection method and system of clone terminal devices
A technology of terminal equipment and detection method, which is applied in the field of communication transmission, can solve the problems of damage to the interests of operators and consumers, wrong locking of legal terminals, etc., and achieve the effect of shortening the clone detection cycle, avoiding wrong locking, and maintaining safe operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
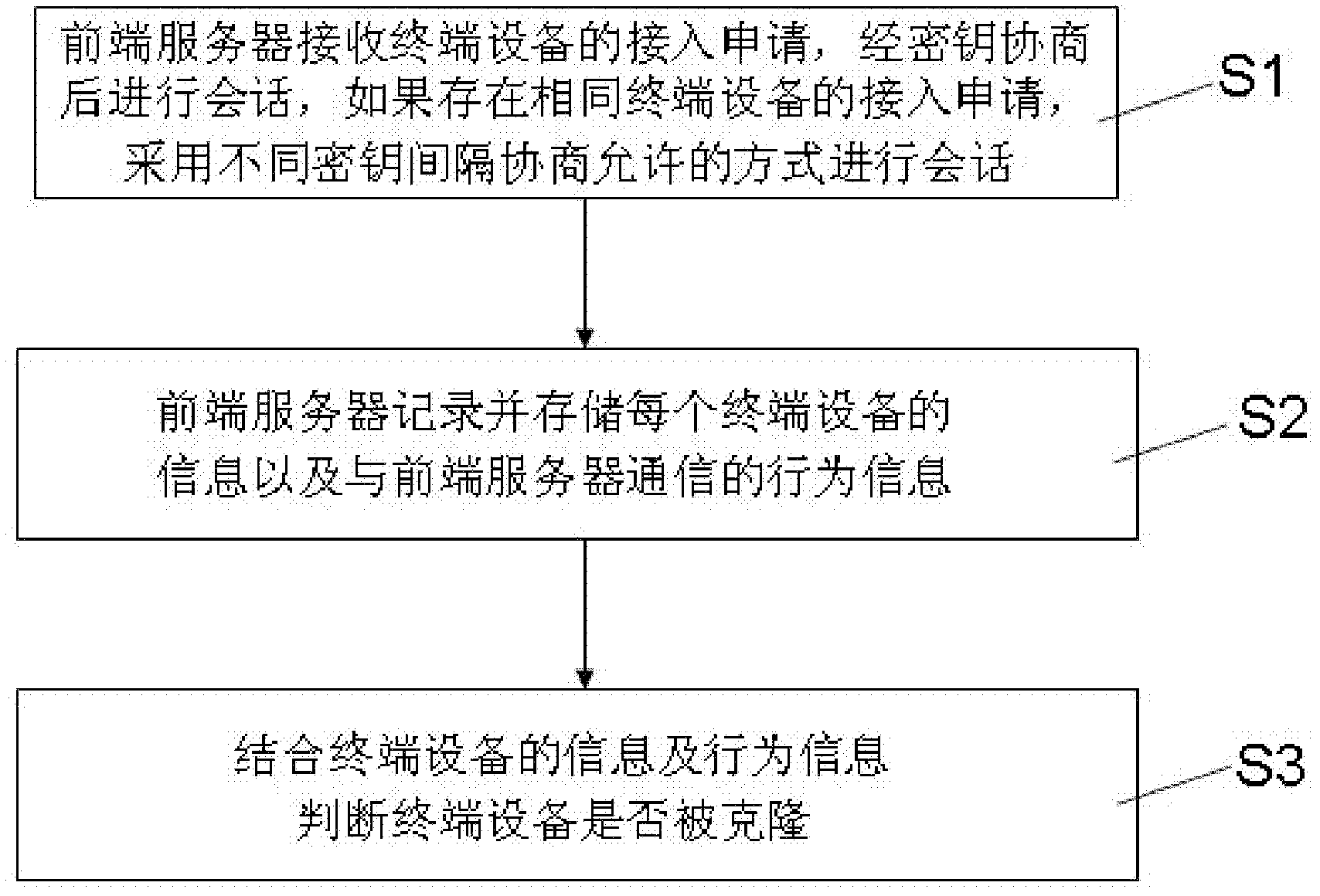
[0034] The technical principle of the present invention: a detection method for cloning terminal equipment proposed by the present invention adopts a dual processing strategy combining "incident interference" and "post-event monitoring".
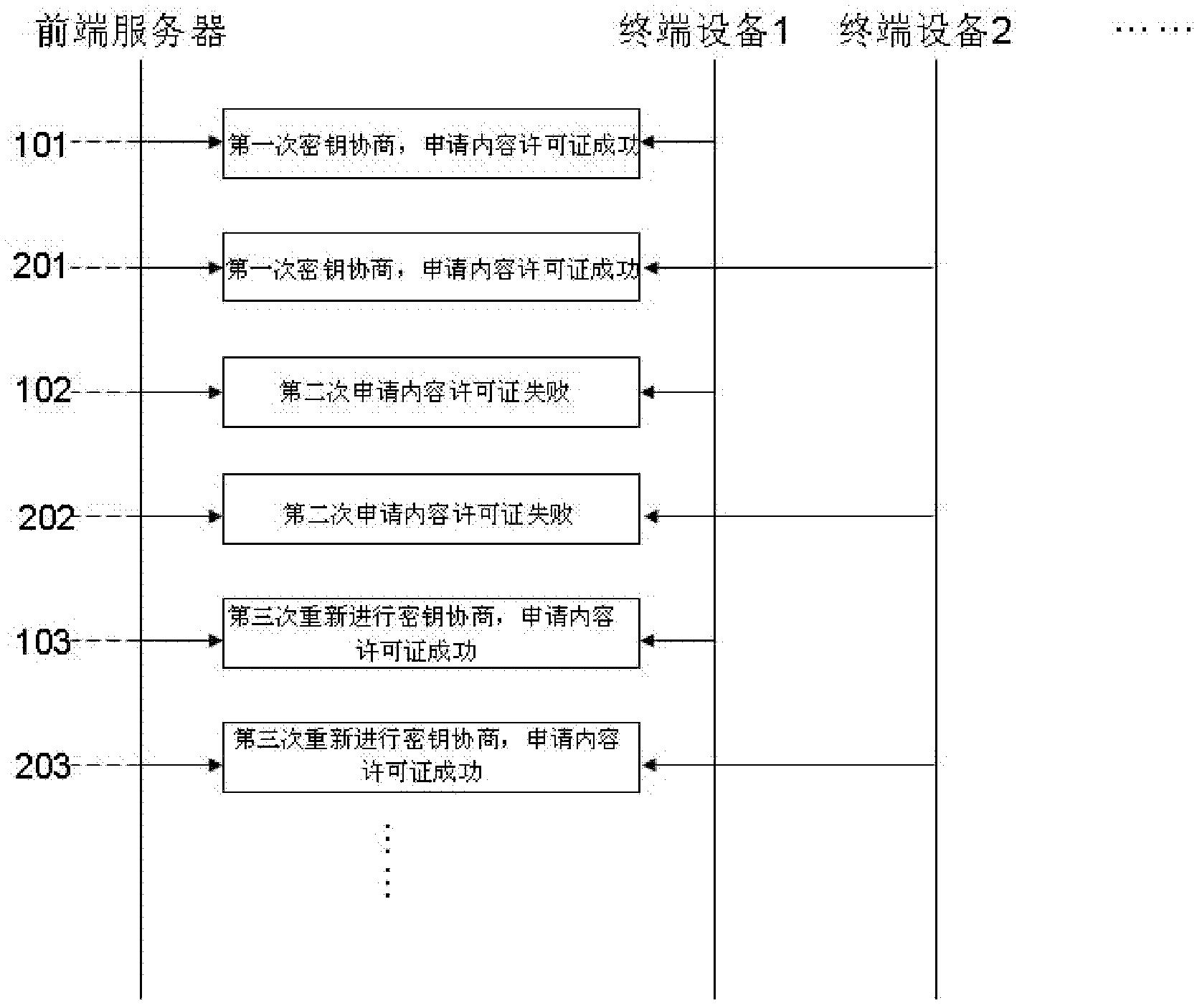
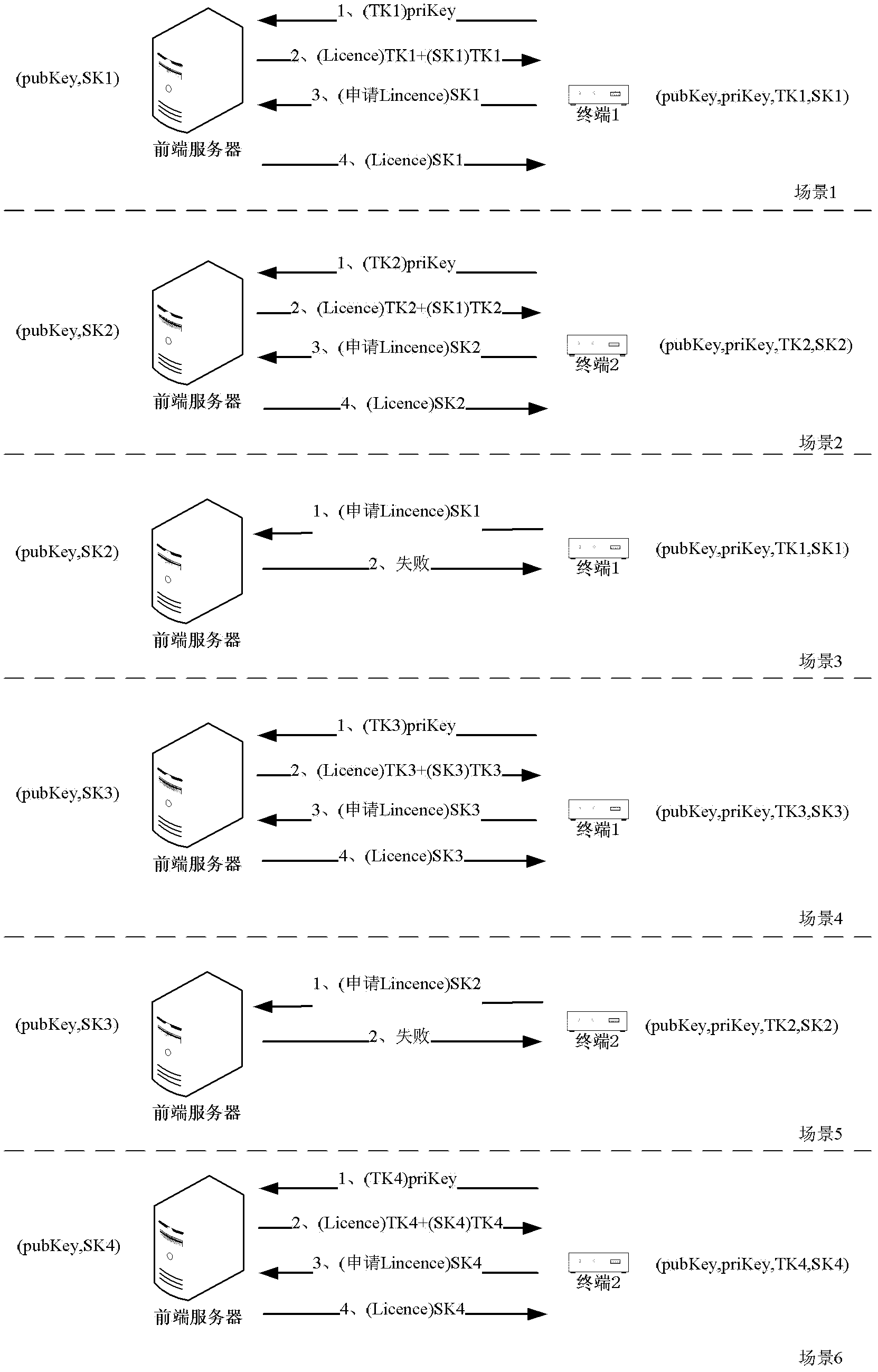
[0035] "Incident interference" means that when applying for a content license, the legitimate terminal device and the cloned terminal device will negotiate different keys to encrypt the content license, and the terminal device must be restarted repeatedly through the interval negotiation to allow the application. Content licenses, decrypted to watch shows. Legitimate end users will report this phenomenon of not being able to watch programs normally to the operator at the first time, and the operator will take effective measures to solve the cloning problem in a timely manner. And the interference of not being able to watch programs normally makes cloning terminal equipment meaningless.
[0036] "After-the-fact monitoring" means that when th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com