Signature realization method and signature realization device
A technology for signing data and signing keys, applied in the field of information security, which can solve the problems of high memory space occupation, low recognizability, and large amount of computation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0085] Embodiment 1 provides a signature implementation method, including the following steps:
[0086] Step A: receiving the signature request command sent by the host, and analyzing the signature request command according to preset rules, and determining the header preset length data, data field length value and data field;
[0087] In this embodiment, before parsing, it also includes: judging whether the signature request command can be parsed according to the second preset format, and if so, parsing the signature request command according to the preset rules, otherwise returning an error to the host Prompt information.
[0088] Step B: judging whether the header preset length data matches the first preset character string, if yes, execute step C, otherwise, judge whether the header preset length data matches the second preset character string, if yes, execute step B E, if the first preset length data does not match the first preset character string and the second preset c...
Embodiment 2
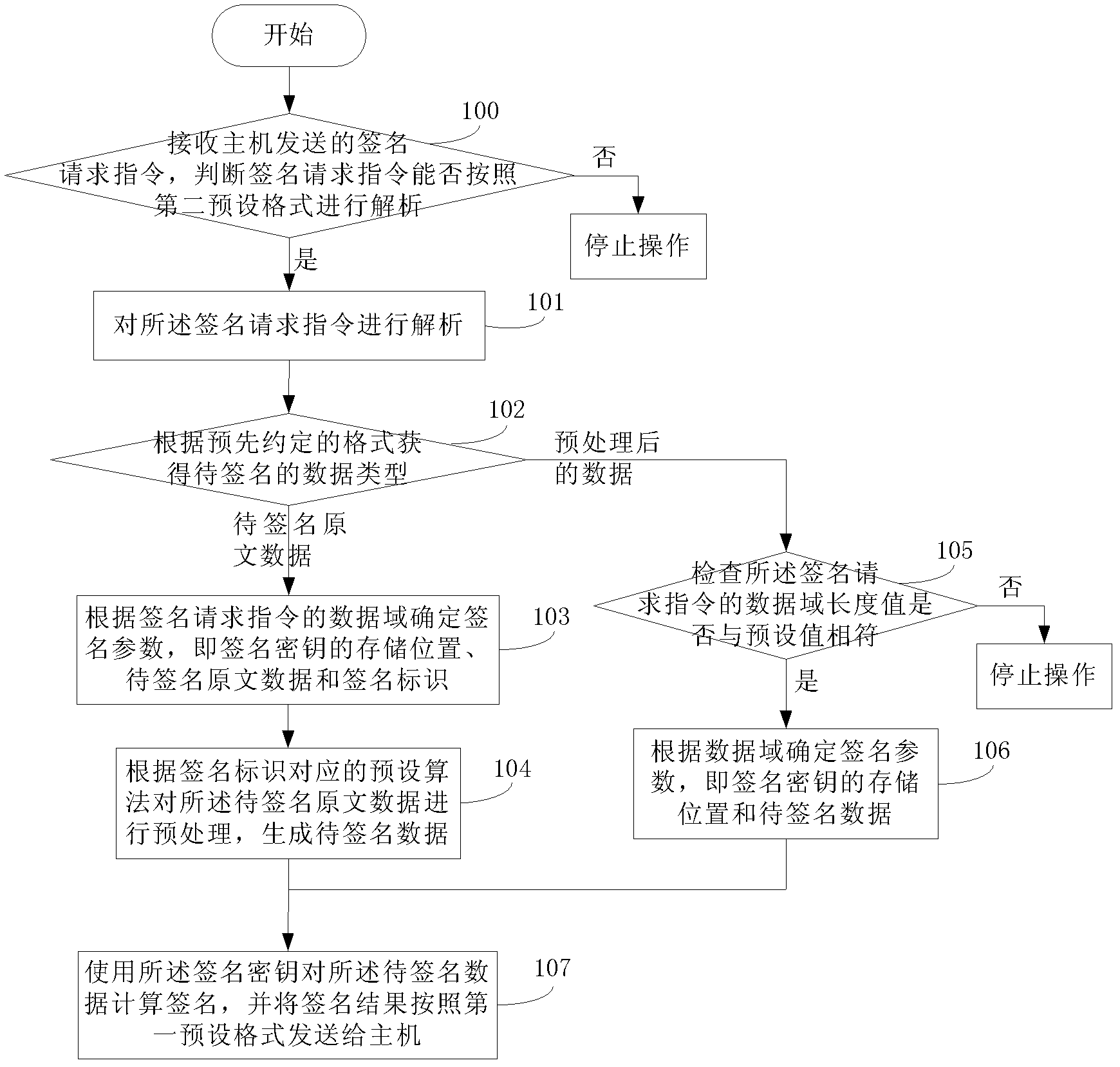
[0099] see figure 1 , which is a flow chart of a method for implementing a signature provided in Embodiment 2; specifically includes the following steps:
[0100] Step 100: Receive the signature request instruction sent by the host, and judge whether the signature request instruction can be parsed according to the second preset format, if yes, perform step 101, otherwise stop the operation;
[0101] Preferably, in this embodiment, the stop operation specifically includes: sending a pre-agreed error code to the host, and returning error prompt information to the host.
[0102] After stopping the operation, if a new command is received from the host, it will continue to be operated accordingly.
[0103] The method for judging whether the signature request instruction can be parsed according to the second preset format is specifically:
[0104] Step 2'-1: judging whether the data length of the signature request instruction reaches the preset length; if yes, proceed to the next ...
Embodiment 3
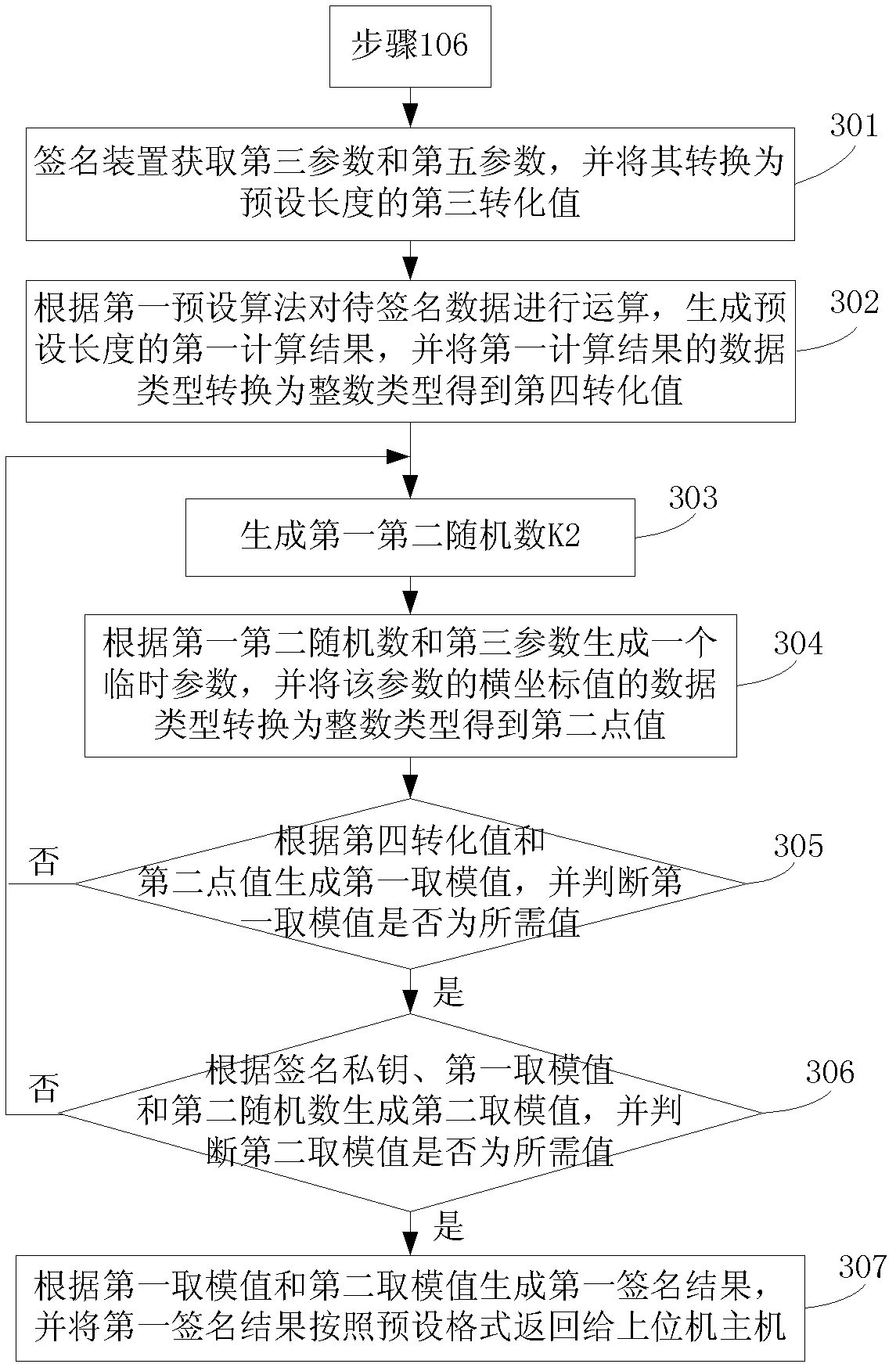
[0152] Embodiment 3 of the present invention is based on Embodiment 2, taking the data type to be signed as the original text data to be signed as an example, and introduces the implementation process of preprocessing and signing in detail, as figure 2 shown, including:
[0153] This embodiment will be described in detail by taking the signature request instruction data sent by the analyzed host as the following specific data as an example: 80740100 00001C 0001 0002 00000006 313233343536 6D657373 61676520 64696765 7374 000000;
[0154] Step 201: Obtain the first parameter, the second parameter, the third parameter, and the fourth parameter, and at the same time obtain the signature public key according to the container object, and convert the above values into byte type data of a preset length;
[0155] Wherein, the first parameter, the second parameter and the fourth parameter are respectively one-dimensional arrays; the third parameters are respectively two-dimensional ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com