Anonymous digital certificate system and verification method of trustable computing environment
A digital certificate and trusted computing technology, which is applied in the field of communication security, can solve performance problems, platform user privacy violations, complexity and other problems, and achieve the effects of enhanced scalability, good cross-platform characteristics, and privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
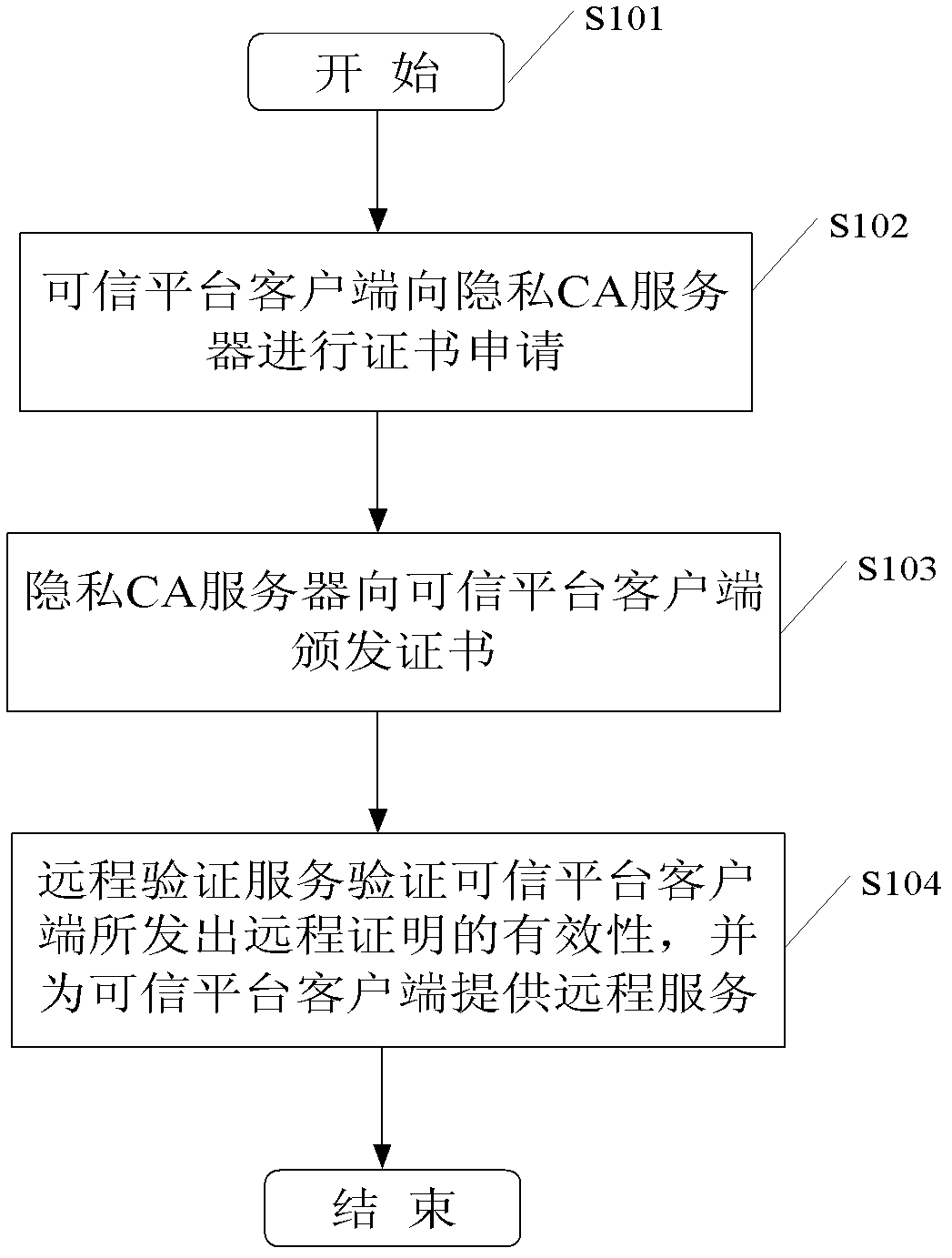
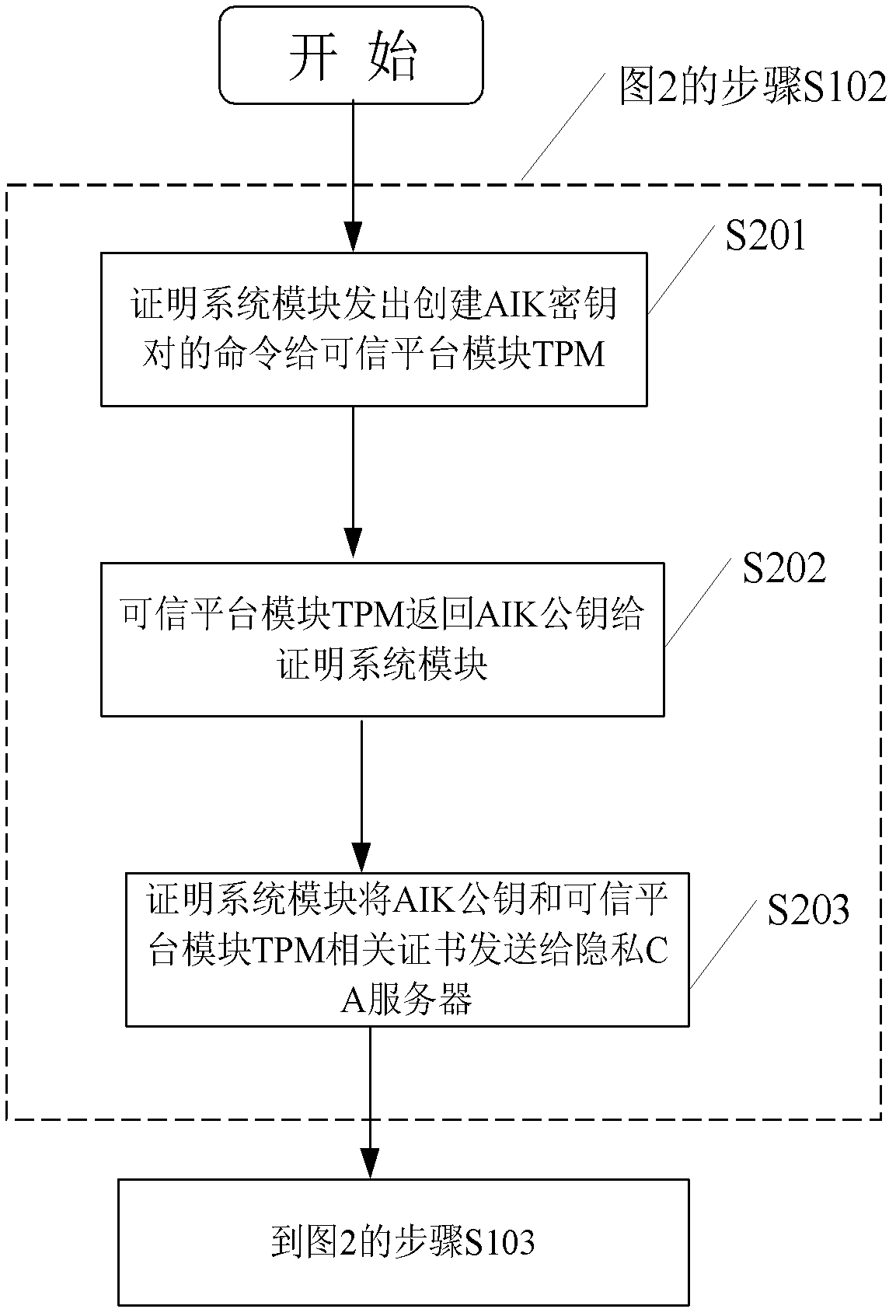
[0048] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
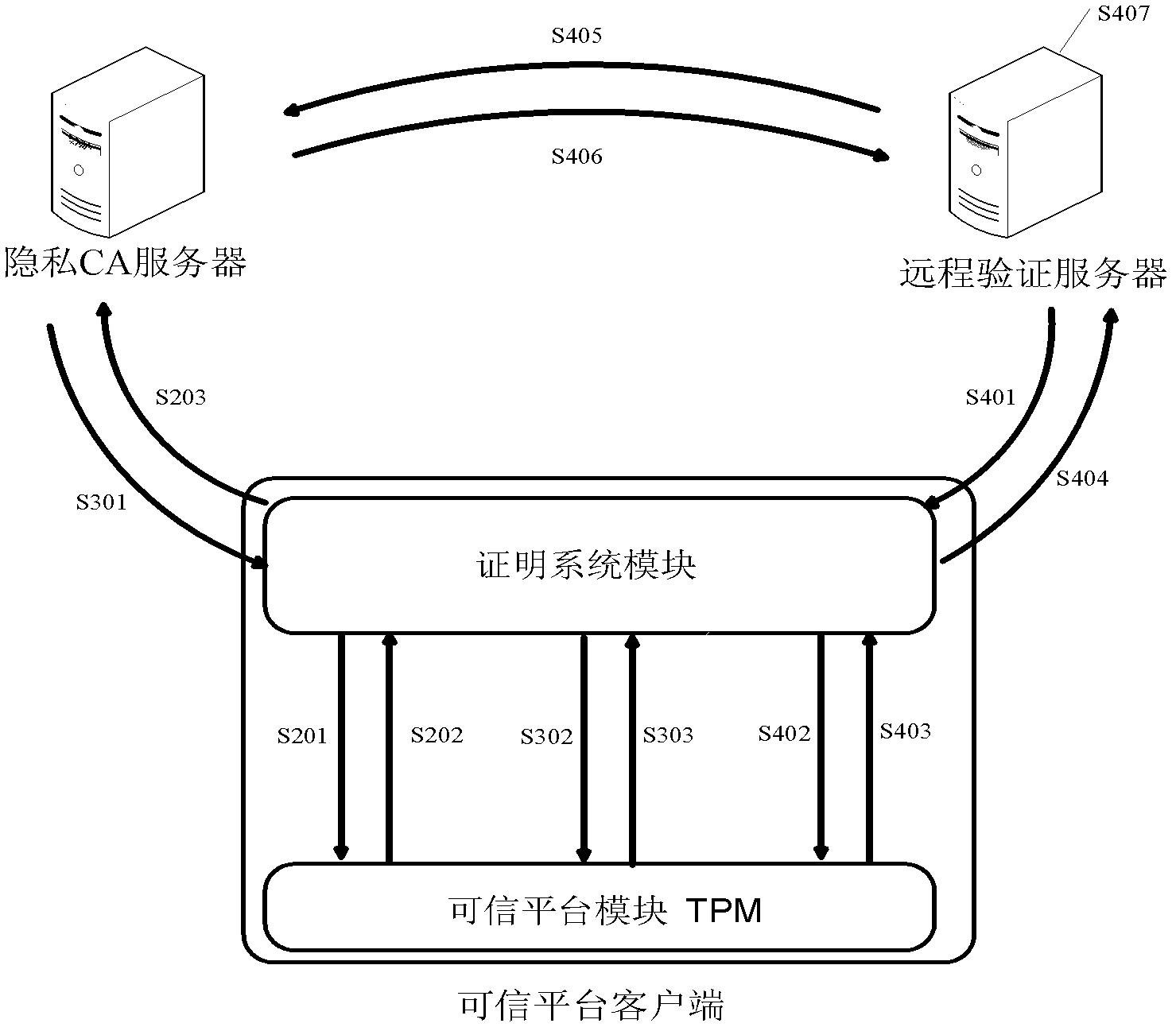
[0049] The anonymous digital certificate system of the trusted computing environment of this embodiment, such as figure 1 As shown, it includes: including a trusted platform client, a remote verification server and a privacy CA server. In this embodiment, the trusted platform client host model is Lenovo ThinkCentre M55p Tower, and the TPM model equipped with a trusted platform module is Infineon1.2. The models of the remote authentication server and the privacy CA server are both Dell OptiPlex360Mini Tower, and the network environment is a campus-level network environment.
[0050] The trusted platform client, the remote verification server and the privacy CA server are connected to each other through the campus LAN network;
[0051] The communication between the trusted platform client and the remote verification server, and the communicatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com