Activity measurement-based hardware trojan detection method
A hardware Trojan detection and activity technology, applied in the field of hardware Trojan detection and hardware Trojan detection based on activity measurement, can solve the problems of strong destructiveness, no quantitative measurement method, hardware Trojan is not easy to be activated, etc., and achieves strong flexibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
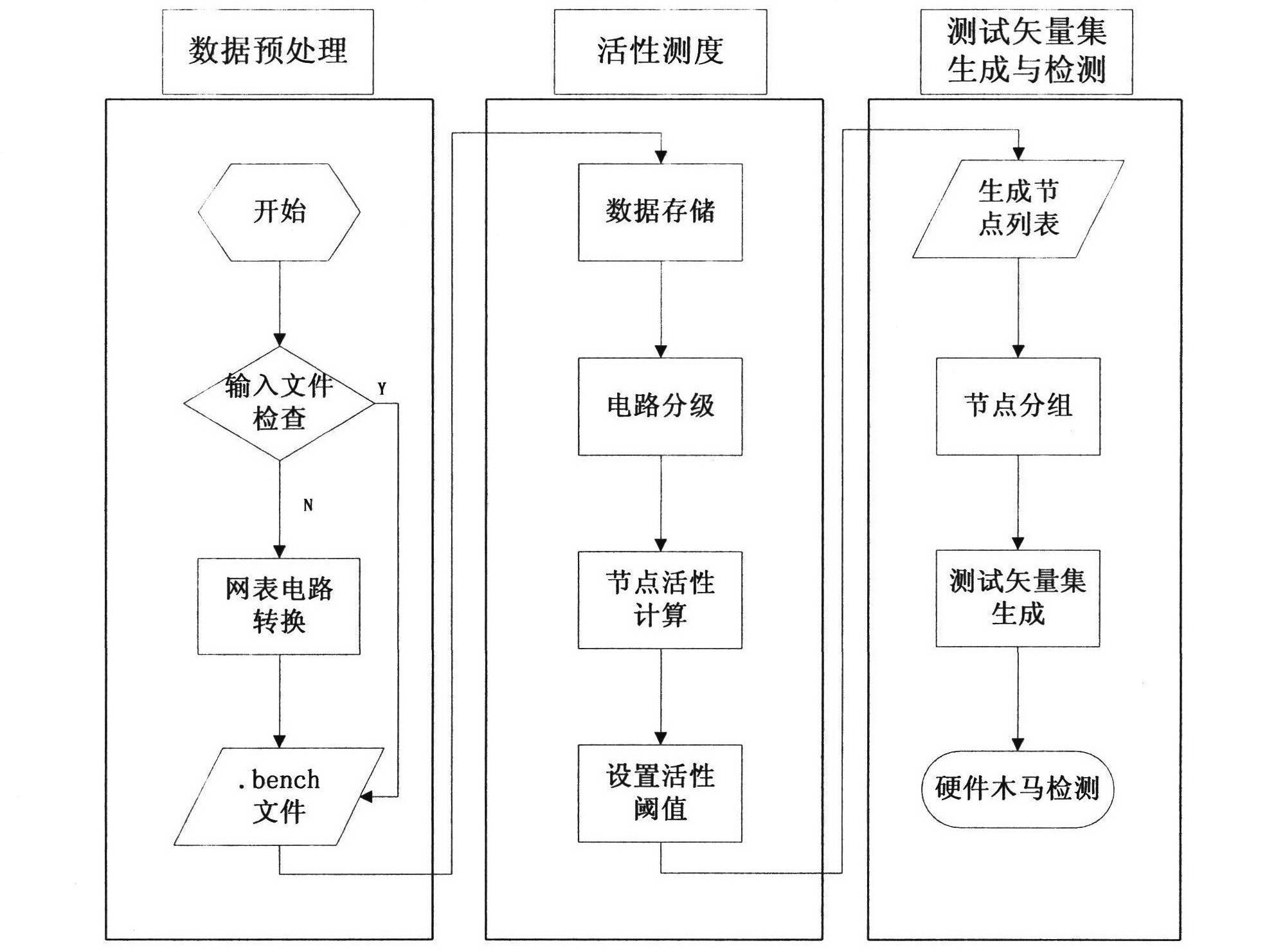
[0028] A kind of hardware Trojan detection method based on activity measurement of the present invention, its step comprises:
[0029] Phase 1: Data Preprocessing
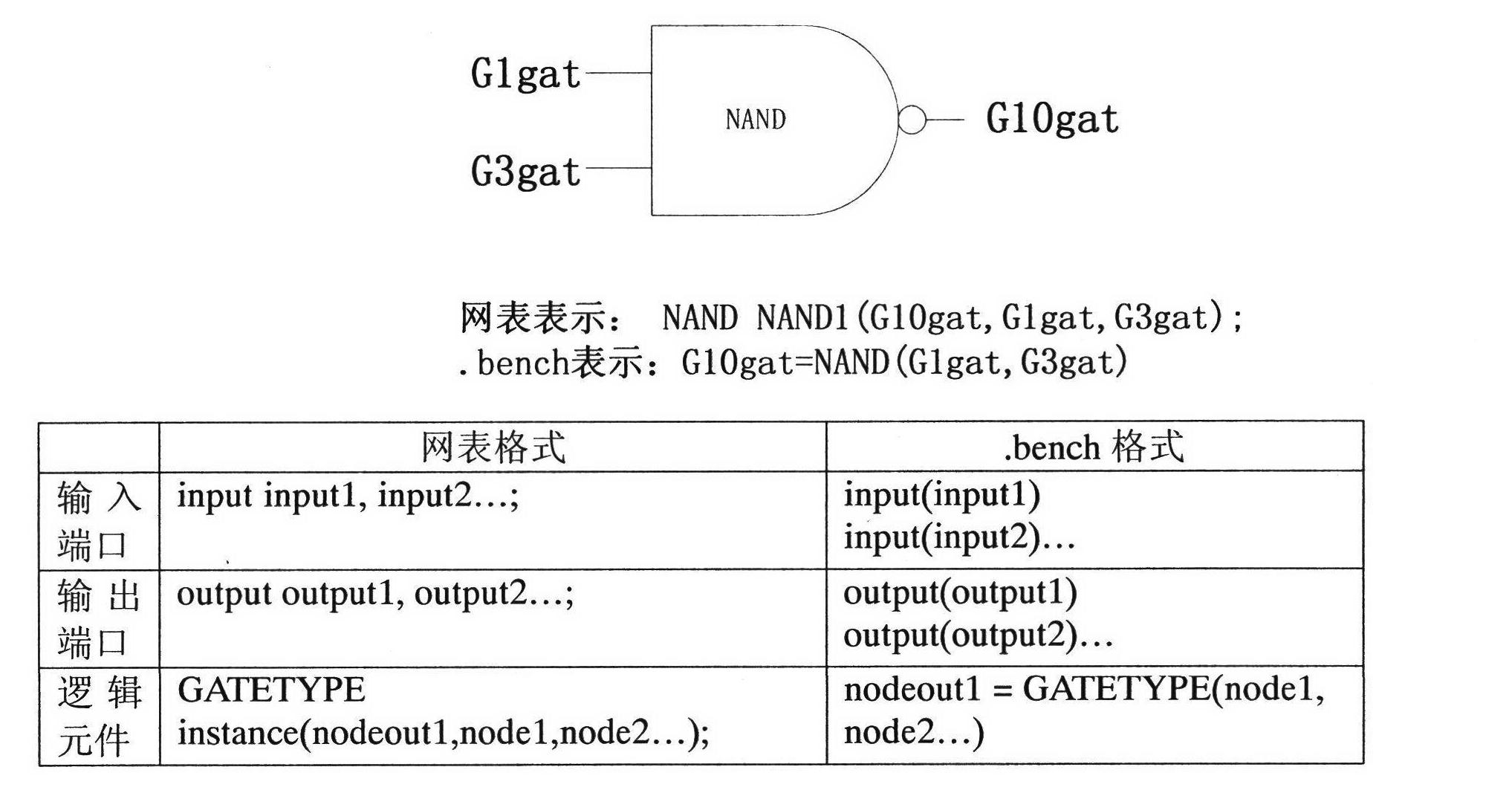
[0030] 1. Check the input file format, if the circuit format conforms to the proposed .bench file format, such as image 3 , proceed to the next stage.
[0031] 2. Use perl language, according to image 3 The conversion principle shown converts the gate-level netlist structure of the target circuit into the .bench file format. This conversion simplifies the expression form of the circuit, and is beneficial to restore the topology of the circuit using a programming language.
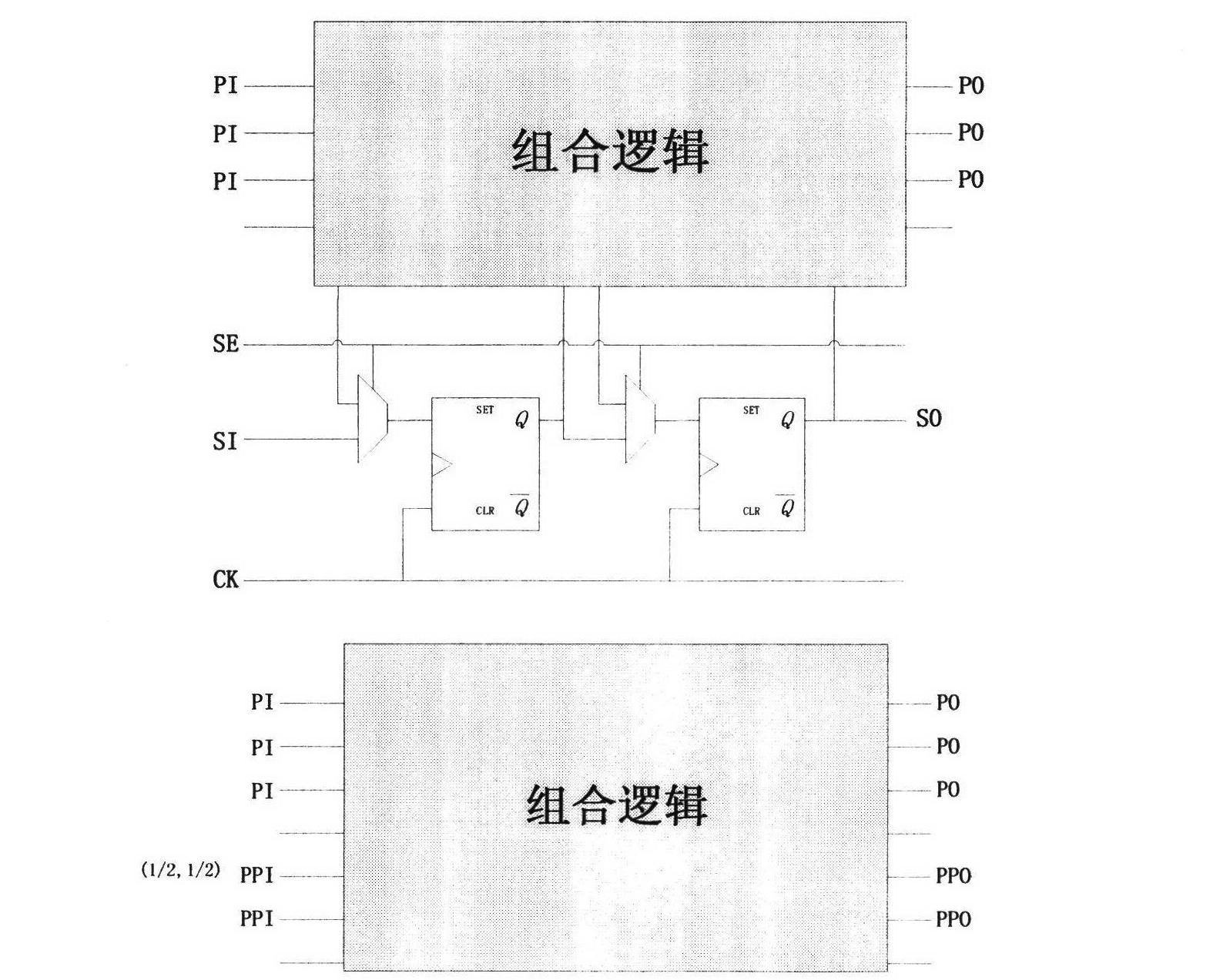
[0032] For sequential circuits, due to the existence of sequential devices, when the circuit works normally, the node logic ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com