Password encryption method for social website
An encryption method and technology for social networking sites, applied in the field of password encryption, can solve problems such as the reduction of user password security, and achieve the effects of increasing difficulty, reducing logic, and increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
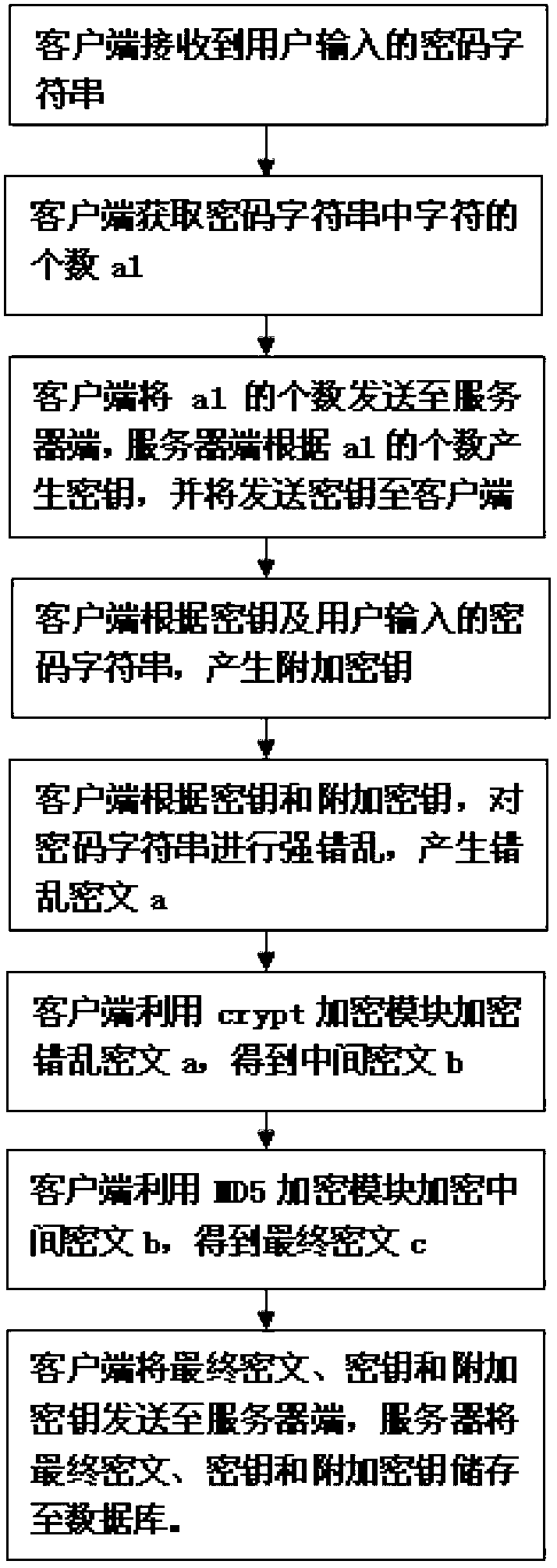
[0036] A password encryption method used by social networking sites, such as figure 1 shown, including the following steps:
[0037] A. The client communicates with the server to generate a key X, and then the client uses the key X and the password entered by the user to generate an additional key Y, and uses the key X and the additional key Y to scramble the password entered by the user to generate Confused ciphertext a;
[0038] B. The client performs nonlinear and irreversible encryption on the disordered ciphertext a for the first time to generate intermediate ciphertext b;
[0039] C. The client performs a second non-linear and irreversible encryption on the intermediate ciphertext b to generate the final ciphertext c;
[0040] D. The client sends the key X, the additional key Y and the final ciphertext c to the server, and the server stores the key X, the additional key Y and the final ciphertext c.
[0041] Step A is specifically:
[0042] After the client receives ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com