Method and system for establishing a protection path in a network protected by a shared grid
A technology for protecting paths and networks, applied in the field of network communication, can solve the problems of increasing the processing complexity of intermediate nodes, slowing down the speed of protection paths, and blocking the protection paths, so as to shorten the time of path switching, reduce the processing time, and reduce the number of processing times. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
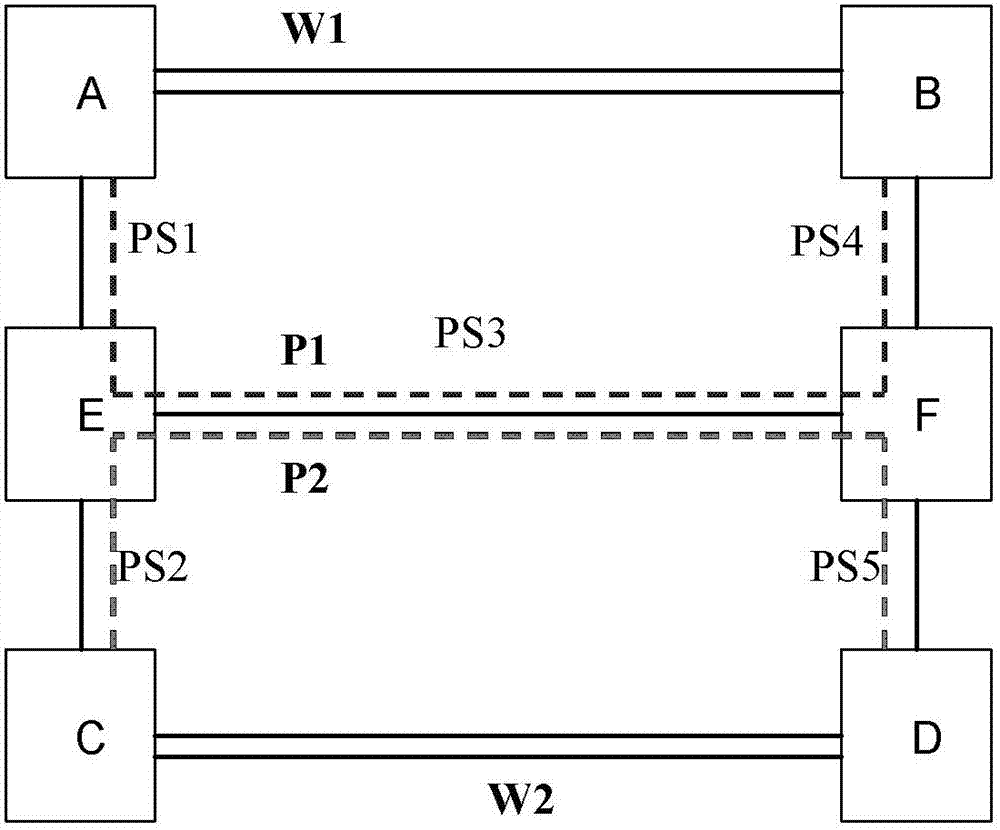
[0101] image 3 It is a schematic diagram of implementing a shared grid protection. Such as image 3 As shown, W1 is the working path, P1 is the protection path of W1, W2 is the working path, and P2 is the protection path of W2. The path passed by P1 is A-E-F-B, which is composed of three sections PS1-PS3-PS4, and the path passed by P2 is C-E-F-D, which is composed of PS2-PS3-PS5. P1 and P2 share resources of the PS3 segment. PS1, PS2, PS3, PS4, and PS5 are all OTU (Optical Transform Unit, optical transformation unit) type 2 links. ODU2 can carry 8 ODUs (Optical channel Data Unit, optical channel data unit) 0, that is, a protection group of 8 ODU0s can be established. In this example, one of the ODU0 protection groups is taken as an example. In this shared protection group , there are two members, P1 and P2, sharing the resources of ODU0. Deploy a TCM on each section of the protection path, and the TCM occupies the overhead of ODU0.
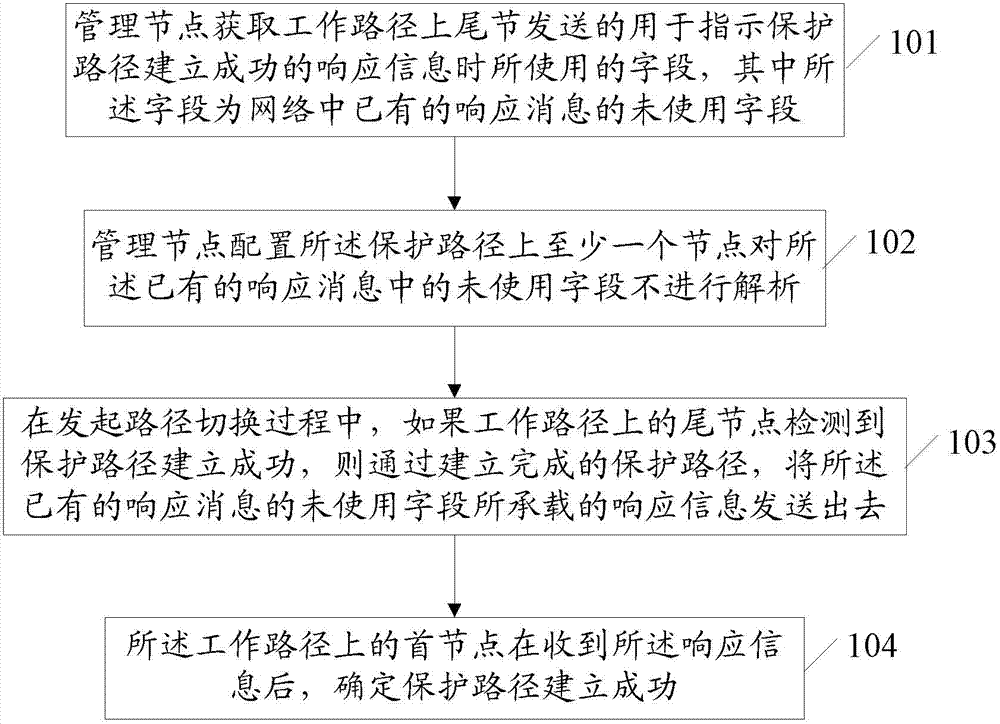
[0102] The starting node on a ...
Embodiment 2
[0113] After the working path is restored, the traffic needs to be switched back to the working path, and the occupied shared resources on the protection path need to be released.
[0114] The release of resources needs to be realized through TCM, such as image 3 As shown, TCM needs to be deployed between each segment, that is, TCM is deployed on PS1, PS2, PS3, PS4, and PS5. In this topology, a single-layer TCM is deployed.
[0115] The first and last endpoints send revert messages to each other, indicating that traffic needs to be switched back. The head and tail endpoints wait for the recovery timer locally; when the recovery timer expires, the head and tail endpoints switch the traffic from the protection path to the working path; and then initiate the resource release of the protection path.
[0116] Figure 5 It is a sequence diagram of resource release of the protection path in the second embodiment. Figure 5 Timing diagram shown, including:
[0117] S...
Embodiment 3
[0124] In shared protection, because the resources of the protection path are shared by two protection paths, when the working path of the shared resource fails at the same time, resource preemption will occur. During resource preemption, the resource with the highest priority occupies the resource, and the priority is divided into fault priority, service priority, and so on. The priority is processed according to the policy configured locally, and the one with the higher priority occupies resources.
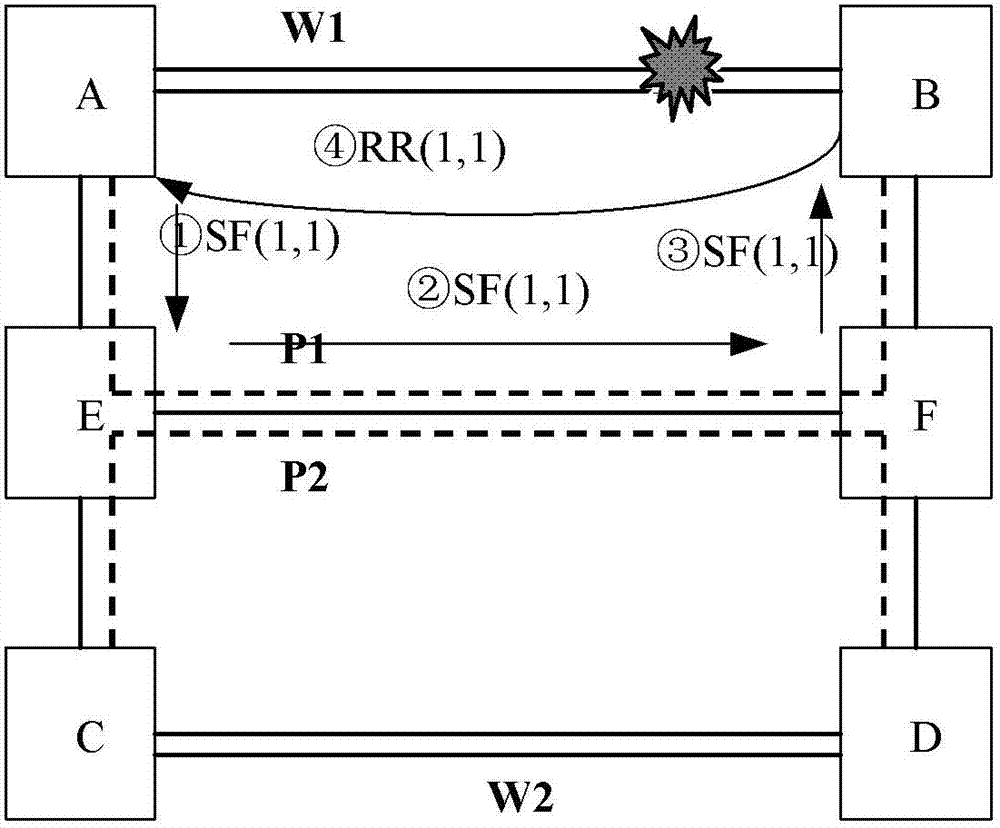
[0125] Figure 6 It is a schematic diagram of the shared grid protection in the third embodiment. Such as Figure 6 As shown, when W1 fails, P1 has already occupied the resource of the shared path. During the period of W1 failure, W2 also fails. At this time, resource preemption processing is required. In this example, it is assumed that P2 has a higher priority than P1.
[0126] Figure 7 It is a sequence diagram of resource release of the protection path in the th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com