Tree structure-based cryptographic algorithm logical expression identification method
A technology of logical expressions and cryptographic algorithms, which is applied in the field of logical expression recognition of cryptographic algorithms based on tree structure, and can solve the problems of not being able to deal with deformation algorithms that do not use constant feature algorithms, not being able to label algorithm names, and misjudging cryptographic functions. Achieve the effect of shortening the analysis cycle, accurately identifying, and solving poor generality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
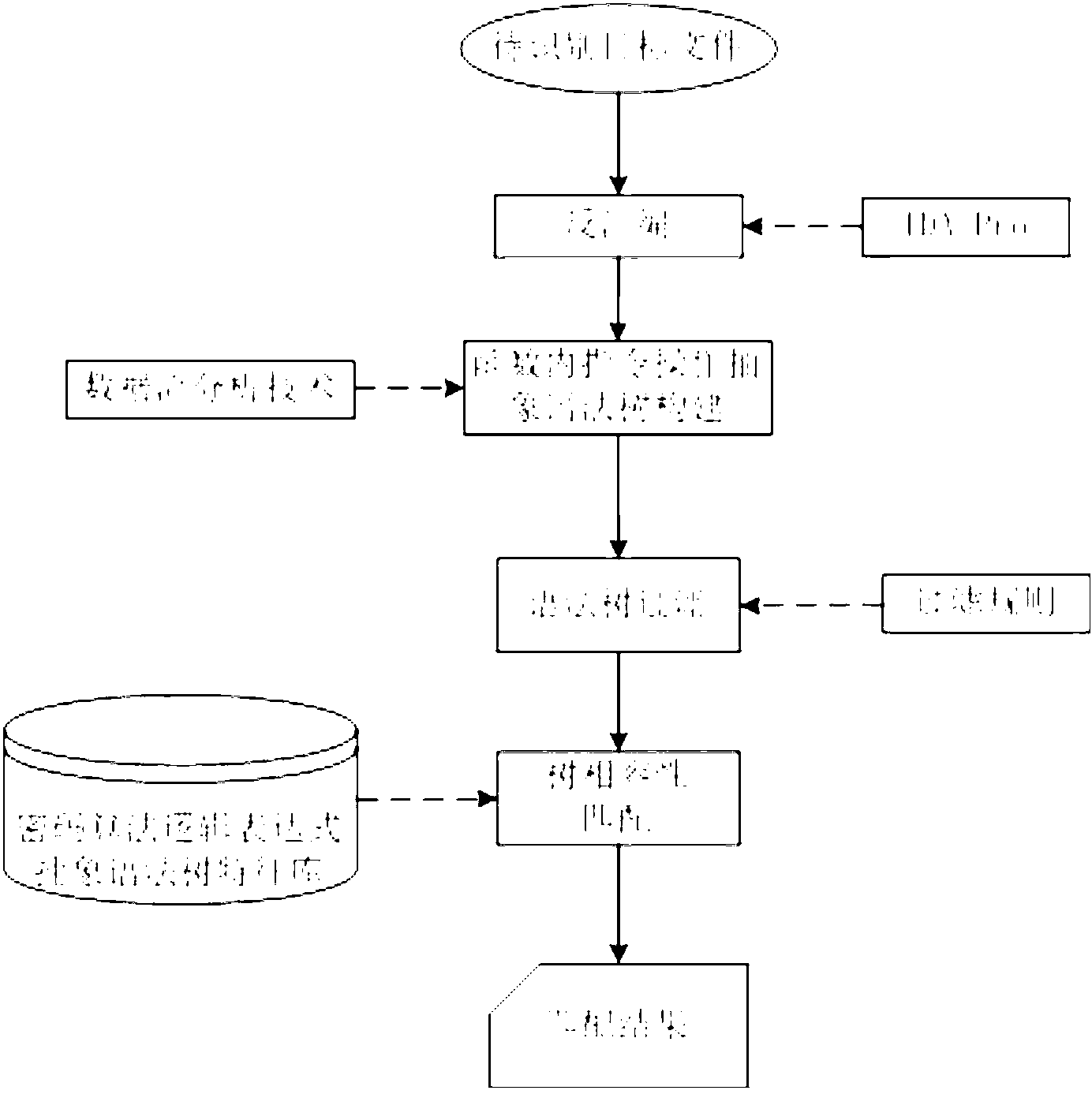
[0040] Embodiment one: see figure 1 , the present invention is based on the cryptographic algorithm logical expression identification method of tree structure, and the cryptographic algorithm and cryptographic function are identified through the following steps:
[0041] 1) By studying the implementation principles of different cryptographic algorithms, extract the logical expression LE (Logic Expression) used in the cryptographic algorithm implementation, and store it in the cryptographic algorithm logical expression feature database T in a tree structure character middle;
[0042] 2) Perform disassembly analysis on the target program to be identified, and obtain the function sequence P1 , F 2 …F n >, for the function F i Perform local (basic block) data flow analysis and construct an abstract syntax tree set F containing only logical operations i 1 , T 2 …T m >, that is, the target pattern tree; where m is the number of abstract syntax trees, and n is the number of fu...
Embodiment 2
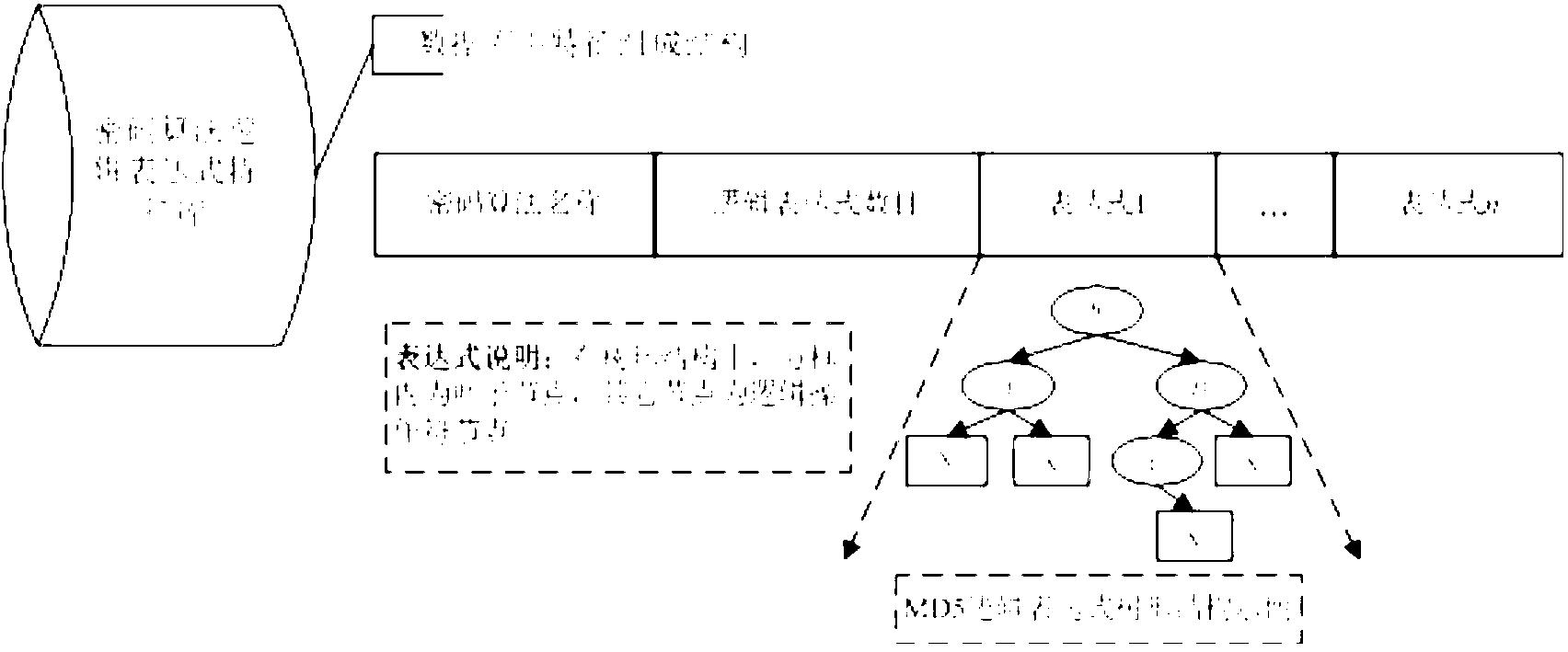
[0046] Embodiment two: see figure 1 , figure 2 , this embodiment is based on a tree-structured method for identifying logical expressions of cryptographic algorithms. The difference from Embodiment 1 is that the pattern tree construction algorithm PTCA (Pattern Tree Create Algorithm) is used to construct a cryptographic algorithm logical expression feature database T character , the specific process is as follows:
[0047] Step 1: Scan the logical expression LE, and record the operator OP with the lowest operation priority min , create an internal node of the feature tree (the internal node created for the first time is the root node), and mount it at the corresponding position of its parent node (except the created root node), and put the OP min saved in internal nodes, OP min Divide LP into left and right parts;
[0048] Step 2: If the left part is an operand, mount it at the corresponding position of the parent node; if it is LE, call the PTCA algorithm for processing...
Embodiment 3
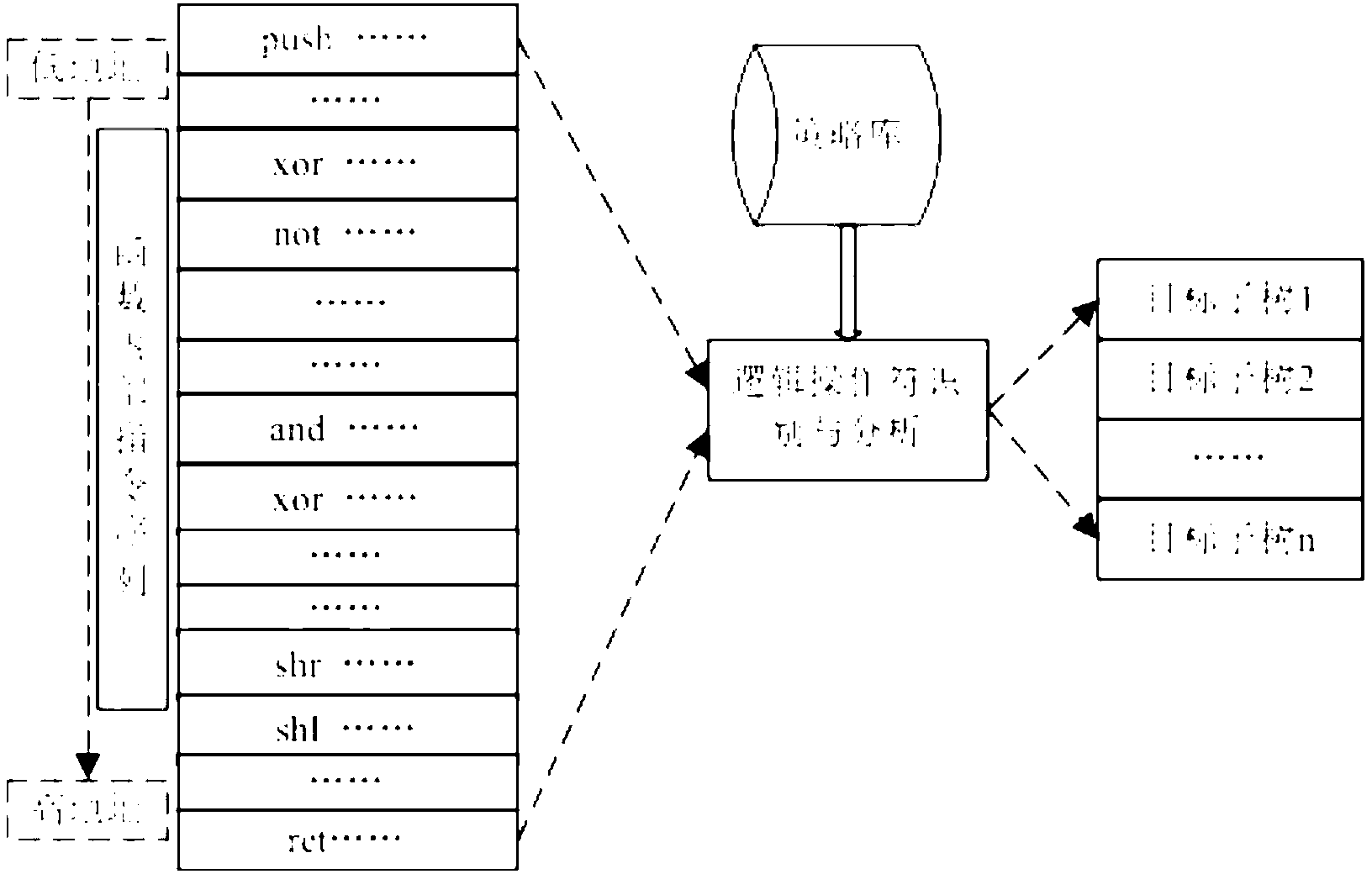
[0052] Embodiment three: see figure 1 , figure 2 , image 3 , this embodiment is based on a tree-structured cryptographic algorithm logic expression recognition method. The difference from Embodiment 1 and Embodiment 2 is that on the basis of object code disassembly, local data flow analysis is performed with functions as the basic granularity, and the construction Target schema tree.
[0053] Object schema tree construction framework such as image 3 As shown, the specific process is as follows:
[0054] Step 1: Disassemble the object code, and the result is recorded as P=(f 1 , f 2 … f n );
[0055] Step 2: In the function f i Inner-scan logical operators, operations with direct logical relations are aggregated into a pattern tree, the function f i The set of pattern subtrees within is T i =(t 1 ,t 2 ...t m );
[0056] Step 3: Repeat step 2 until all functions are processed once, and record the pattern tree set T=(T 1 , T 2 …T m ), the algorithm ends. Where...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com