Webpage watermark generation and authentication method capable of positioning and tampering positions on a browser
An authentication method and browser technology, applied in the fields of instruments, image data processing, special data processing applications, etc., can solve the problems of unable to locate the tampered position of the web page, loss, reducing the efficiency of website information transmission and real-time interactivity, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
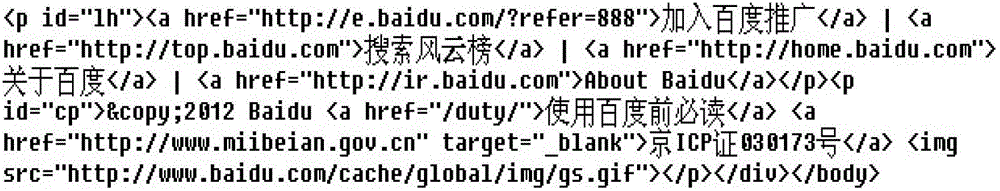
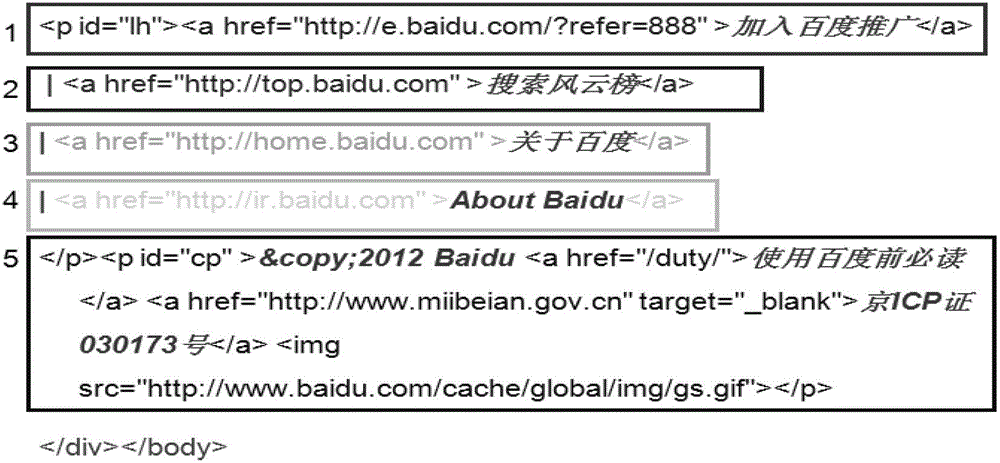
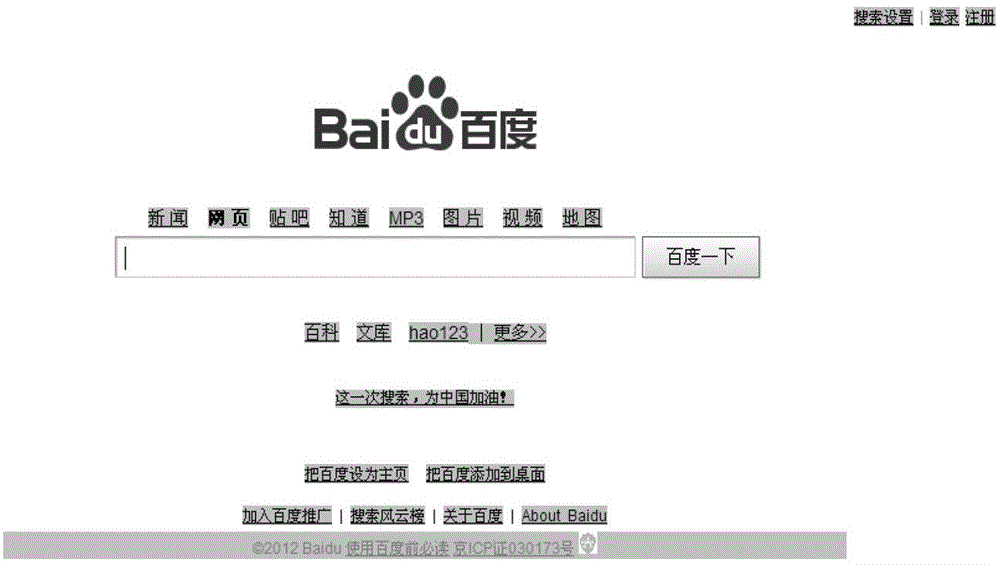
[0061] A specific embodiment of the present invention is a webpage watermark generation and authentication method capable of locating tampered positions on a browser, comprising the following steps:
[0062] A. Web page segmentation
[0063] The original webpage source file F, F={f r |r=1, 2, ..., N}, divide the original web page source file F into M text blocks F connected end to end according to the character blocks displayed by the browser i , that is, F={F i |i=1,2,...,M}; F i ={f r | r = d i +1, d i +2,...,d i +s i}, where f r Indicates the rth character in the original web page source file F, N is the number of characters contained in the original web page source file F, F i Indicates the i-th text block, M is the number of text blocks contained in the original webpage source file F, s i for text block F i the number of characters contained, d i for text block F i The position of the prefix of the first character, ie d i = d i-1 +s i-1 ;
[0064] B. Wate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com