Transformer substation quantum communication model, quantum secret key distribution center and model achieving method
A quantum key distribution and quantum key distribution technology, applied in key distribution, can solve data encryption security risks and other issues, achieve the effect of unconditional key transmission, improve security and reliability, and prevent network monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
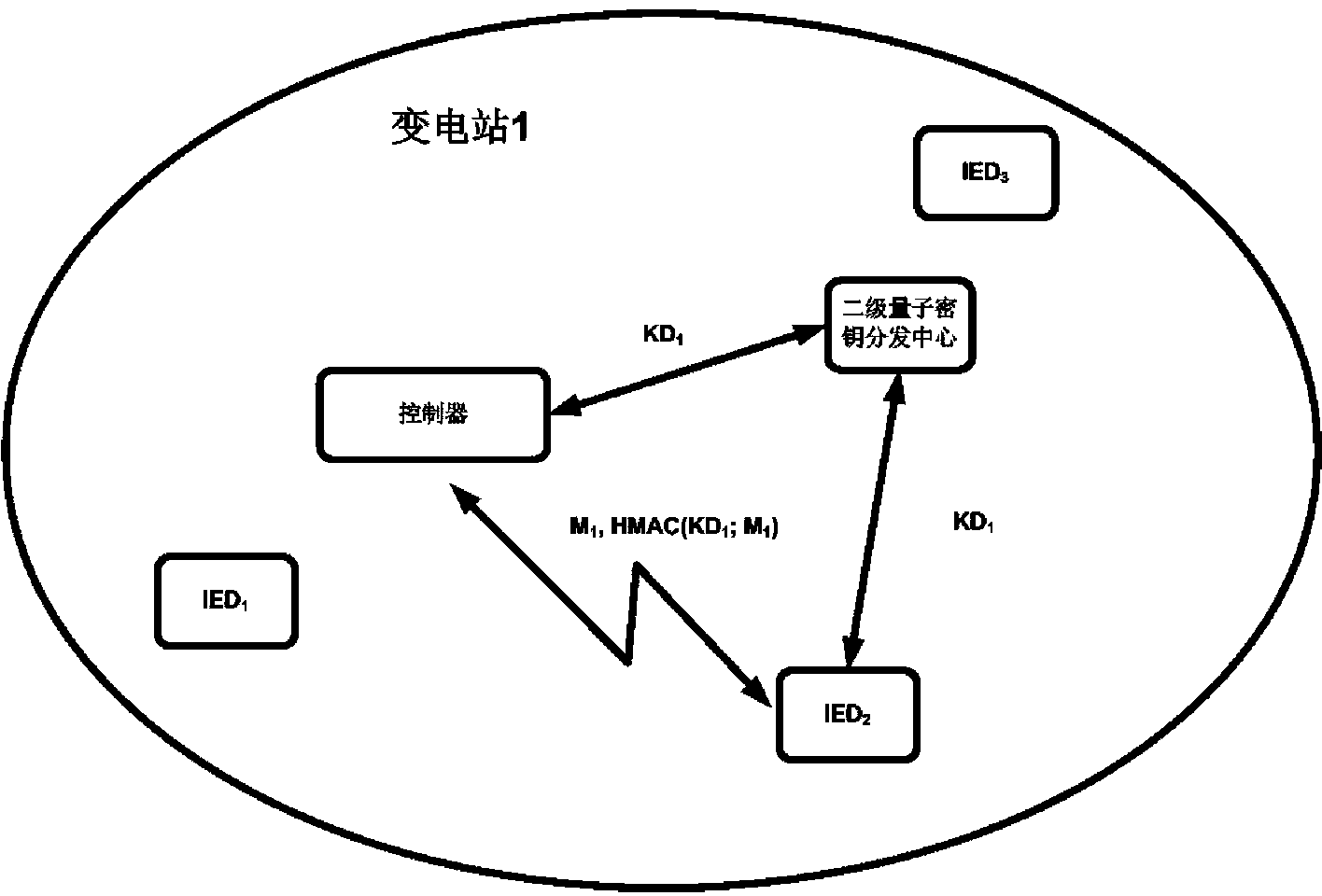
[0089] like image 3 As shown, it is a schematic diagram of scenario 1: the communication key distribution between the intelligent electronic device and the controller (protection or monitoring unit) in the substation.
[0090] Step 1. The secondary quantum key distribution center periodically sends the updated key KD to the intelligent electronic device and the controller at the same time through the classical channel 1 ;
[0091] Step 2. When an intelligent electronic device and the controller want to communicate, use the key KD between them 1 Hash values are calculated on the communication content to ensure message integrity, authentication, and anti-replay attacks.
Embodiment 2
[0093] like Figure 4 As shown, it is a schematic diagram of scenario 2: broadcast messages between different intelligent electronic devices in a substation.
[0094] Step 1. The secondary quantum key distribution center regularly distributes broadcast keys to all intelligent electronic devices through classical channels;
[0095] Step 2. During the lifetime of the key, the broadcast between intelligent electronic devices uses the key to calculate the hash value to ensure message integrity, identity authentication and anti-replay attack;
[0096] In the above two scenarios, SHA256 is used to calculate the hashed message verification code.
Embodiment 3
[0098] like Figure 5 As shown, it is a schematic diagram of scenario 3: key distribution for communication between a substation and a remote control center.
[0099] Step 1. When the remote monitoring system and the control system in the substation need to communicate, apply for a key to the sub-key distribution center;
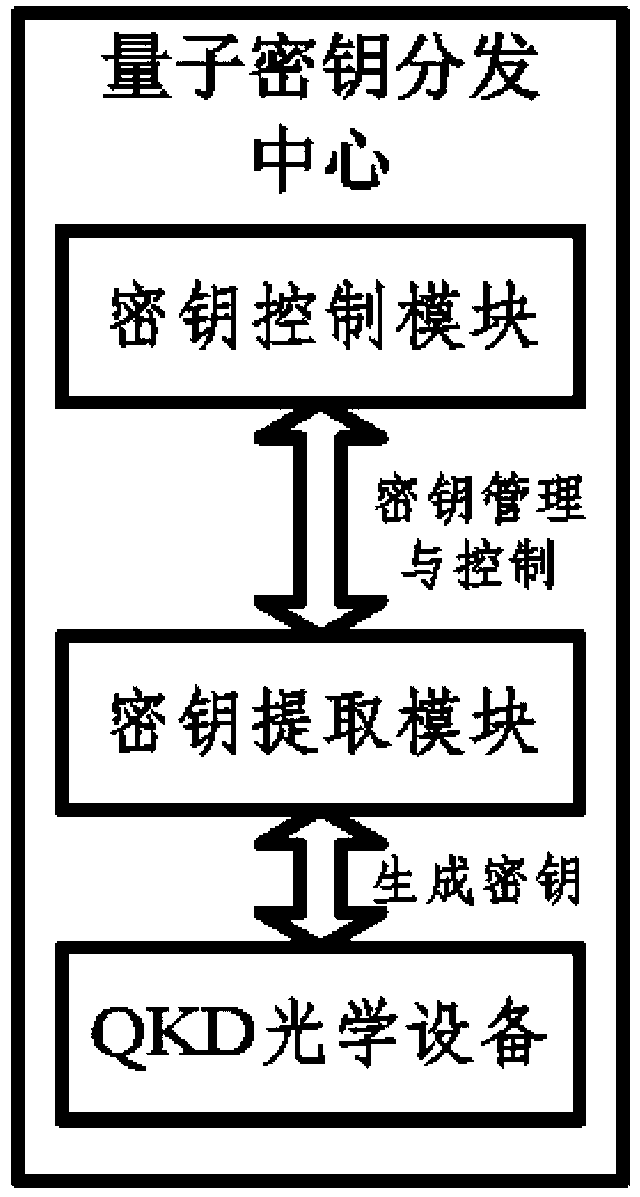
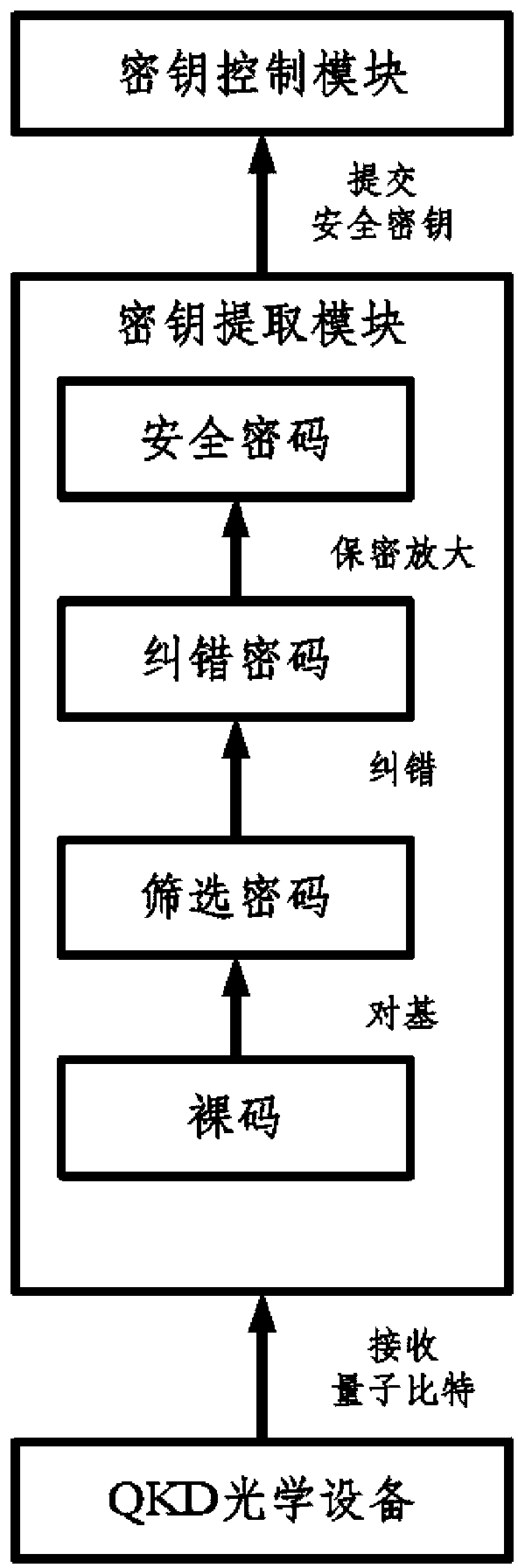
[0100] Step 2. Generate the bare code by the QKD optical device by the first-level quantum key distribution center and the second-level key distribution center where the substation is located;
[0101] Step 3. The first-level quantum key distribution center and the second-level key distribution center where the substation is located perform processes such as base alignment, error correction, and confidentiality amplification through the key extraction module to generate a security key and submit it to the key control module;
[0102] Step 4. The first-level quantum key distribution center and the second-level key distribution center where the substation is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com