File safe distribution method based on universal series bus (USB) flash disk
A technology for safe distribution and file, applied in the direction of digital data protection, digital data authentication, etc., can solve problems such as hindering the value of information, harming the due interests of information copyright owners and legitimate operators, security risks, etc., to strengthen protection and users. Authentication of identity, safe and reliable distribution and use, effect of enhancing reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
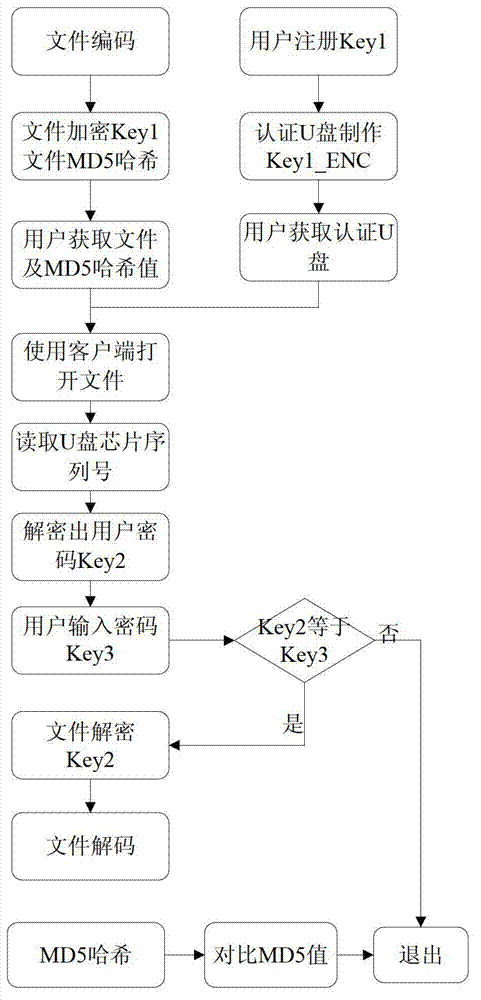
[0075] Example 1. After a registered user obtains an encrypted file in a special format, the process of using the client to open the file is as follows:
[0076] first part
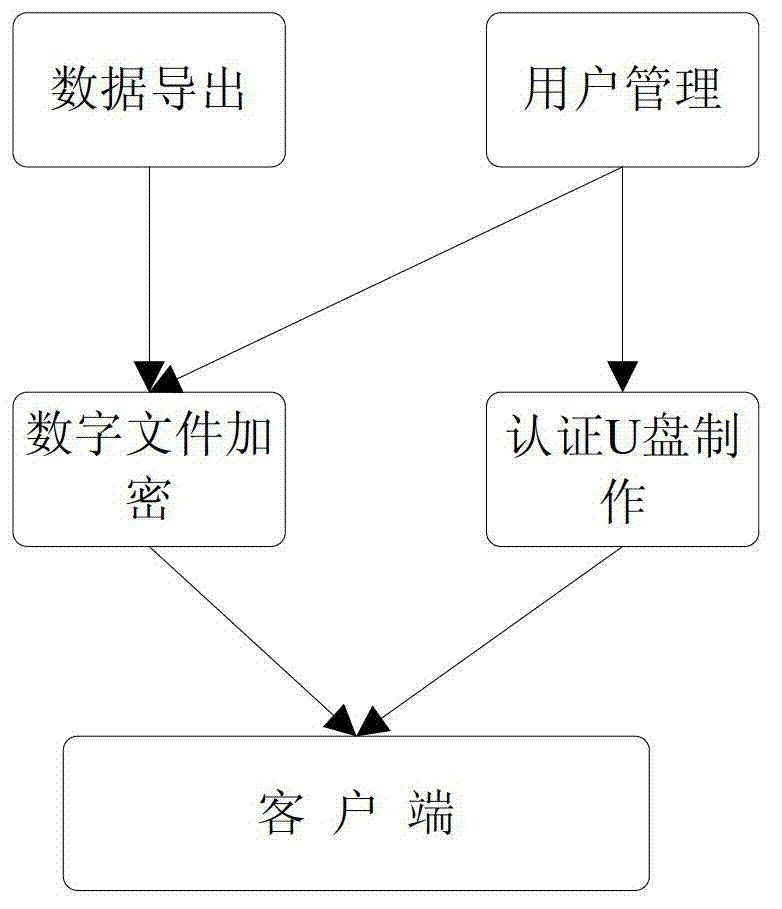
[0077] 1) User management. Manage user information, only registered users can use Excel files normally.
[0078] 2) Data export. Re-encode the original Excel file with a special encoding method to generate a file in a custom format.
[0079] 3) File encryption. Use the password of the registered user as the key to encrypt the content of the Excel file to generate a ciphertext file. Perform MD5 hash on the content of the Excel file and encrypt the obtained MD5 value.
[0080] 4) Certified U disk production. Use the serial number of the U disk chip as the key to re-encrypt the user password of the registered user, and store the obtained ciphertext in the system sector of the U disk to make an authenticated U disk.
[0081] The steps are:
[0082] Step 1: User registration, each user defines the use...
Embodiment 2
[0126] Example 2. The procedure for a registered user to modify the personal password and update the authentication U disk is as follows:
[0127] first part
[0128] 1) User management. Manage user information, only registered users can use Excel files normally.
[0129] 2) Data export. Re-encode the original Excel file with a special encoding method to generate a file in a custom format.
[0130] 3) File encryption. Use the password of the registered user as the key to encrypt the content of the Excel file to generate a ciphertext file. Perform MD5 hash on the content of the Excel file and encrypt the obtained MD5 value.
[0131] 4) Certified U disk production. Use the serial number of the U disk chip as the key to re-encrypt the user password of the registered user, and store the obtained ciphertext in the system sector of the U disk to make an authenticated U disk.
[0132] The steps are:
[0133] Step 1: User registration, each user defines the user password Key1; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com