Method for transmitting paired master cryptography keys in wireless local area network (WLAN) access network and system
A technology of paired master key and access key, which is applied in network topology, security devices, electrical components, etc., and can solve problems such as poor networking compatibility and complex interfaces
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
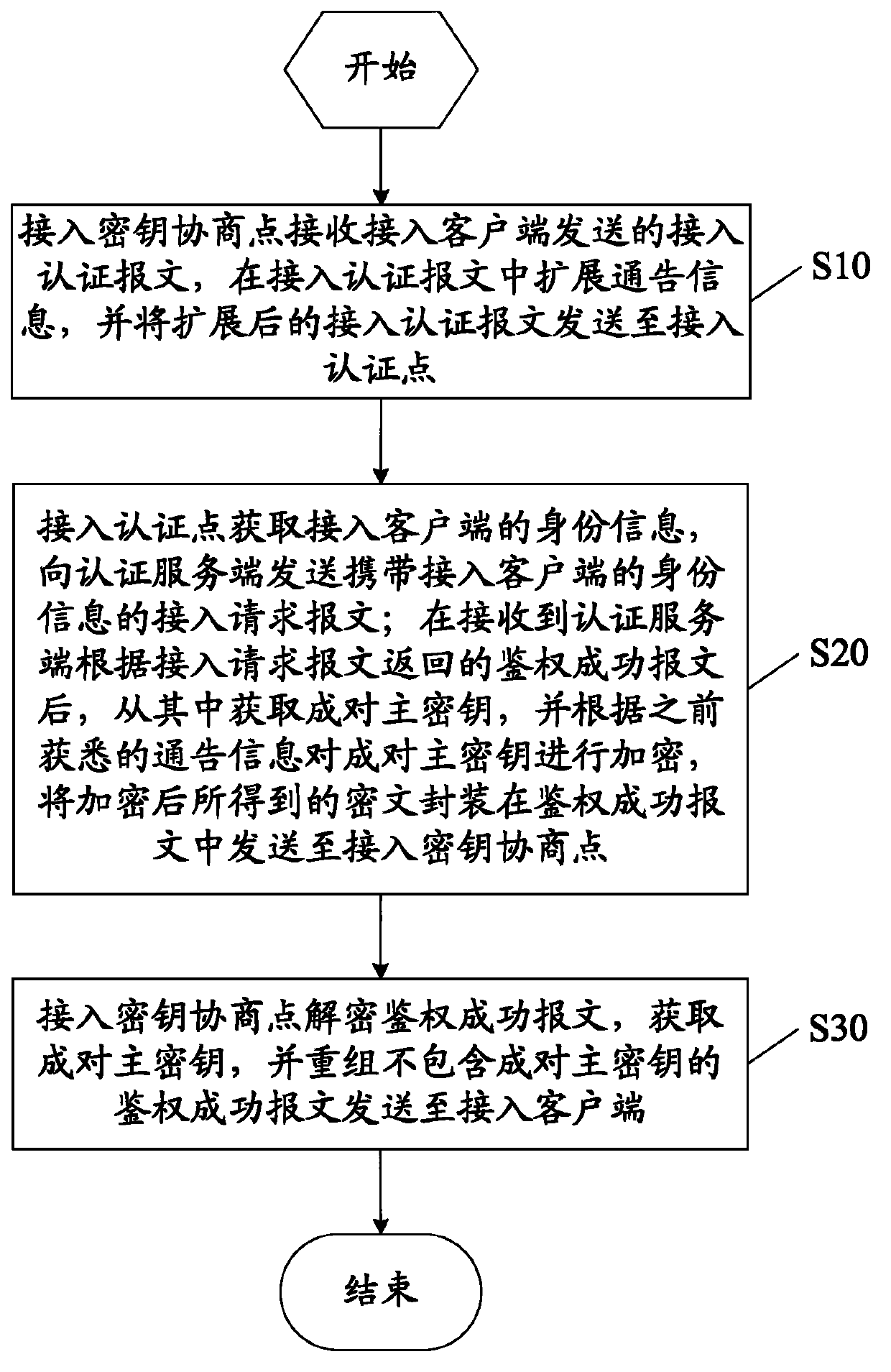
[0074] In fat AP deployment scenarios, APs perform local forwarding. The AP is located between the STA and the BNG. In this networking scenario, the AC does not need to participate. The specific implementation method is as follows:
[0075] Step 1: After connecting to the client STA and associating with the AP, it sends an EAPol-Start message to trigger EAP authentication.
[0076] Step 2: After the AP receives the STA's EAPol-Start message, it expands the notification information supported by the EAPoL V3 version in the EAPol-Start message, that is, carries information such as the AP's public key and encryption algorithm through the TLV option, and sends the expanded The message is sent to BNG.
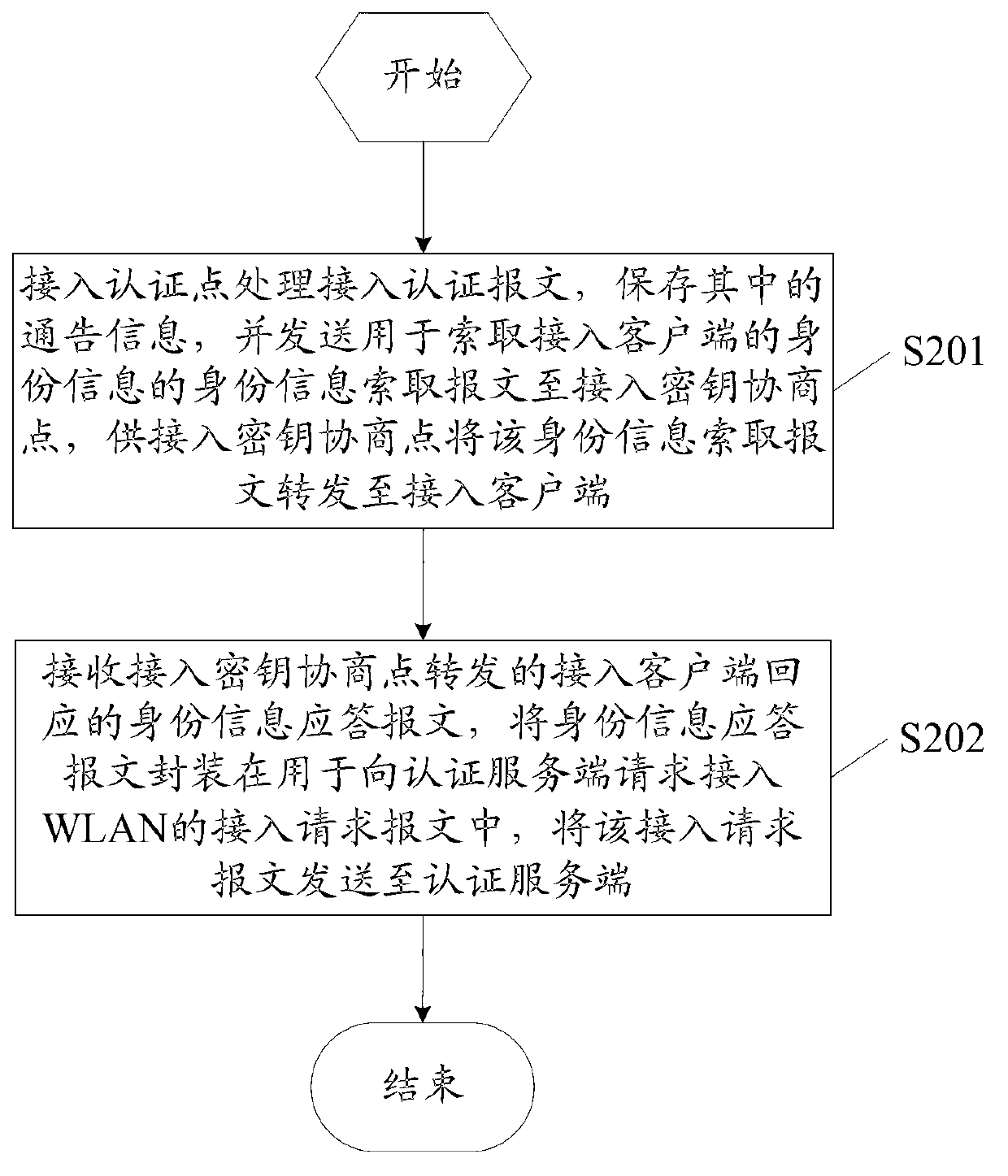
[0077] Step 3: The BNG processes the EAPol-Start message, saves the relationship between the STA and the AP, and the AP's public key and encryption algorithm, and requests identity information from the STA by sending the EAPol / Eap-Req / Identity message.
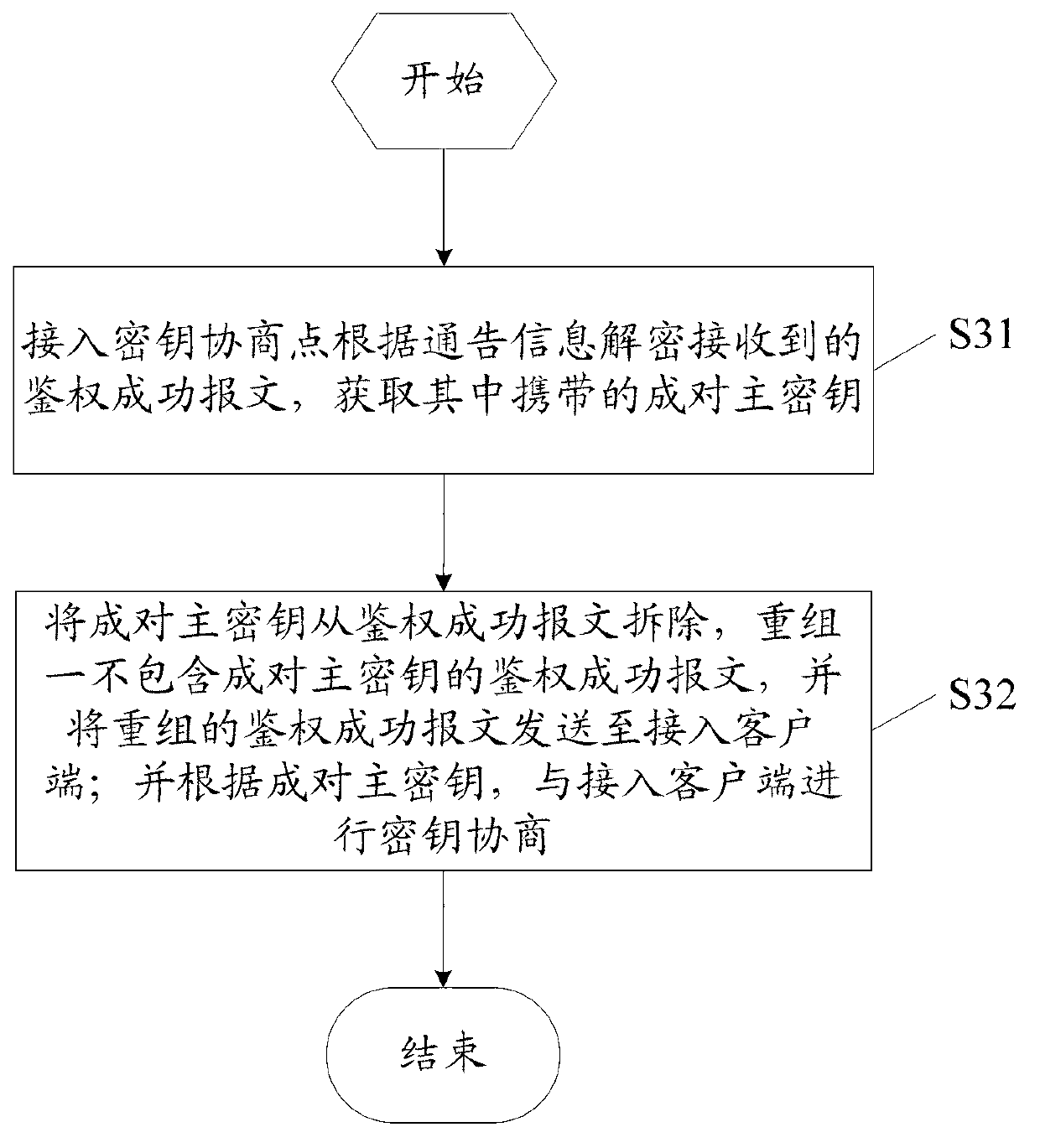
[0078] Step 4: The AP forw...
Embodiment approach 2
[0089] In thin AP deployment scenarios, APs perform centralized forwarding. The wireless access controller AC and BNG can be integrated or separated. No matter in the network where the AC is separated or the network where the AC and BNG are integrated, the PMK carried by EAP-SUCCES can be Analyze the PMK on the AP side. This embodiment adopts a networking mode in which the AC and the BNG are separated. The AP goes online through steps such as discovering the AC request / response, AP joining the AC request / response, AP status change request / response, and configuration update request / response, and establishes a CAPWAP control tunnel with the AC.
[0090] Step 1: After the access client STA establishes an association with the AP, it sends an EAPol-Start message to trigger EAP authentication.
[0091] Step 2: After the AP receives the EAPol-Start message sent by the STA, it expands the notification information supported by the EAPoL V3 version in the EAPol-Start message, that is,...
Embodiment approach 3
[0108] Thin AP deployment scenario, AP local forwarding mode. This embodiment adopts a networking mode in which the AC and the BNG are separated, and the AC, the AP, and the BNG are connected through the SW. The AP goes online through steps such as discovering the AC request / response, AP joining the AC request / response, AP status change request / response, and configuration update request / response, and establishes a CAPWAP control tunnel with the AC.
[0109] Step 1: After the access client STA establishes an association with the AP, it sends an EAPol-Start message to trigger EAP authentication.
[0110] Step 2: After the AP receives the EAPol-Start message sent by the STA, it expands the notification information supported by the EAPoL V3 version in the EAPol-Start message, that is, the public key and encryption algorithm of the AP are carried in the TLV option, and the expanded The EAPol-Start message sent to the BNG.
[0111] Step 3: The BNG processes the received EAPol-Star...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com