Virtualization network boundary data flow gathering method and apparatus
A technology for virtualizing networks and network boundaries, applied in the field of network data flow monitoring, it can solve problems such as infeasibility and high computing load, and achieve the effects of improving flexibility, improving platform adaptability, and improving detection efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
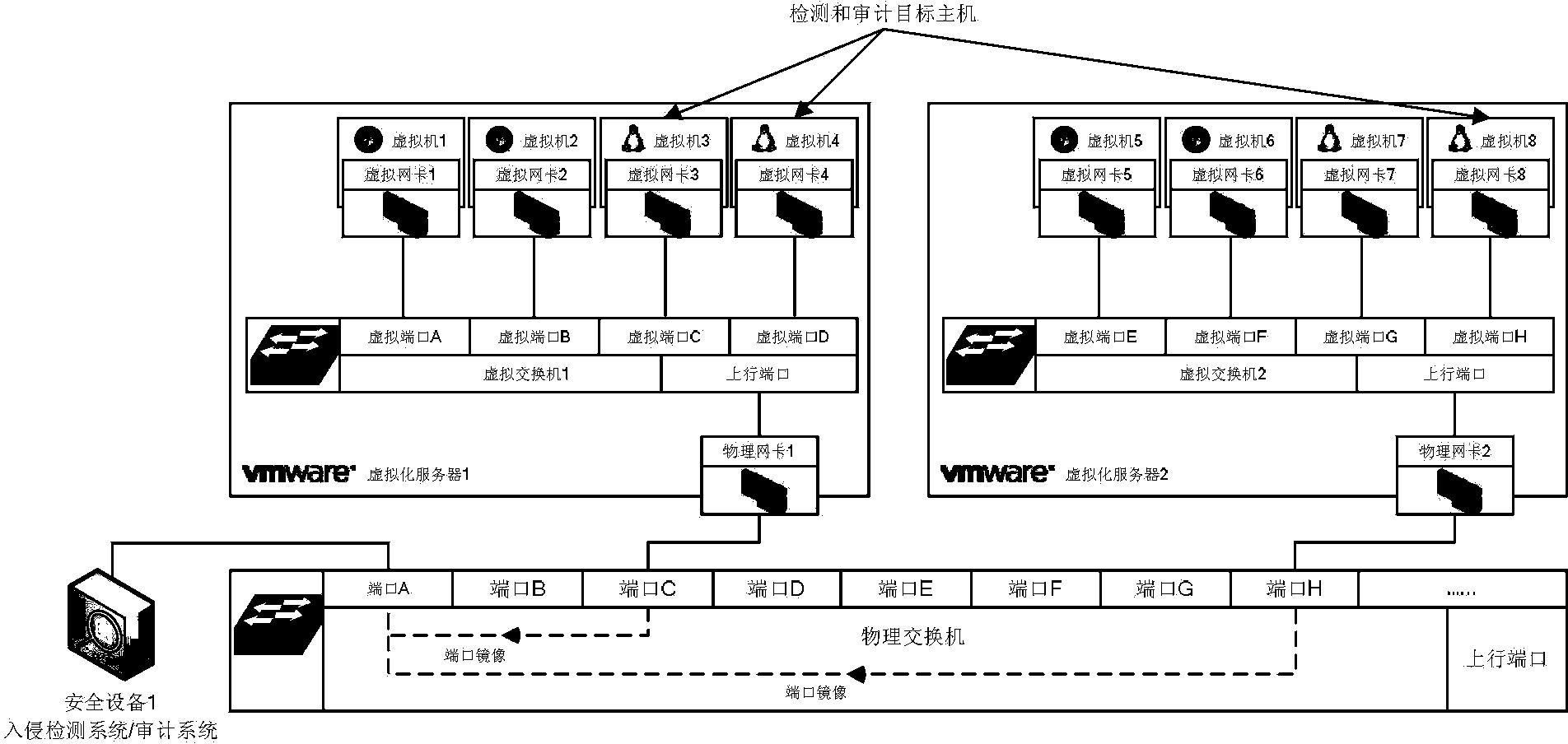
[0035] In a virtualized network, due to the disappearance of network physical boundaries, a physical server connected by a single link is virtualized into a group of virtual machine servers distributed on different physical hosts. Because the communication between two virtual machines on the same physical machine may not forward the data to the physical switch, but directly forwards the data internally by the virtual switch, which makes it impossible for the IDS connected to the physical server to monitor the data sent by the virtual switch. Internally forwarded traffic, in order to solve this problem, it is necessary to deploy a virtual IDS on each virtual switch, monitor the traffic on the virtual switch through the virtual network card on it, and ensure that all traffic of the monitored virtual machine can be monitored, but if There are multiple monitoring objects of different tenants and different security levels on a physical machine, and multiple virtual IDSs need to be d...
Embodiment 2
[0046] This embodiment provides a virtualized network boundary data flow aggregation method, including the following operations:
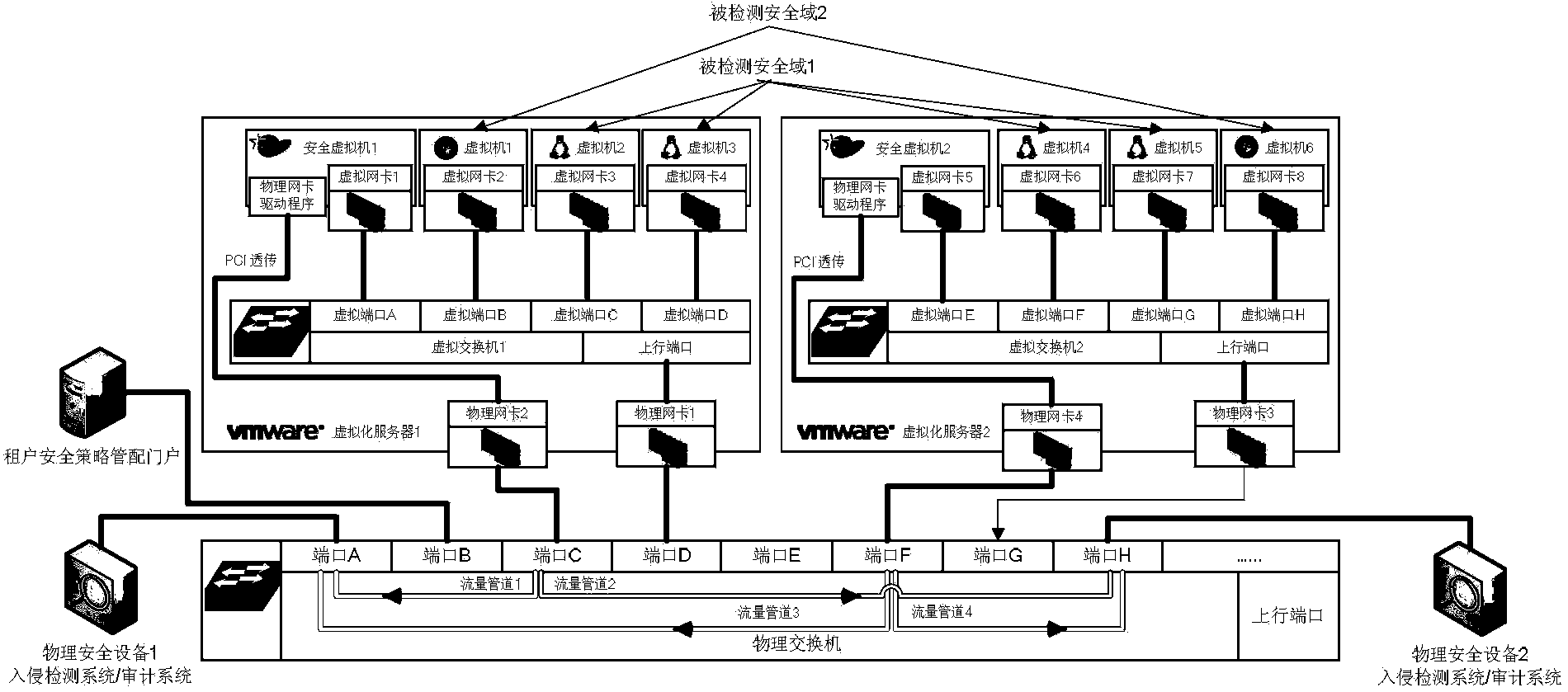
[0047] The virtualized network boundary data flow convergence device listens to the network data flow on the virtual switch according to the network boundary security policies of different tenants, captures the data packets of the network interface specified by the network boundary security policy, and passes the captured data packets through the pre-established The data packet is filtered according to the tenant's filter, and the filtered network data flow belonging to the security domain boundary of the corresponding tenant is encapsulated, and sent to the network security product corresponding to the corresponding tenant for detection and analysis.
[0048] In the above method, the network border security policy includes at least a virtual network security domain border network data flow aggregation policy and a virtual machine network data flow ...
Embodiment 3
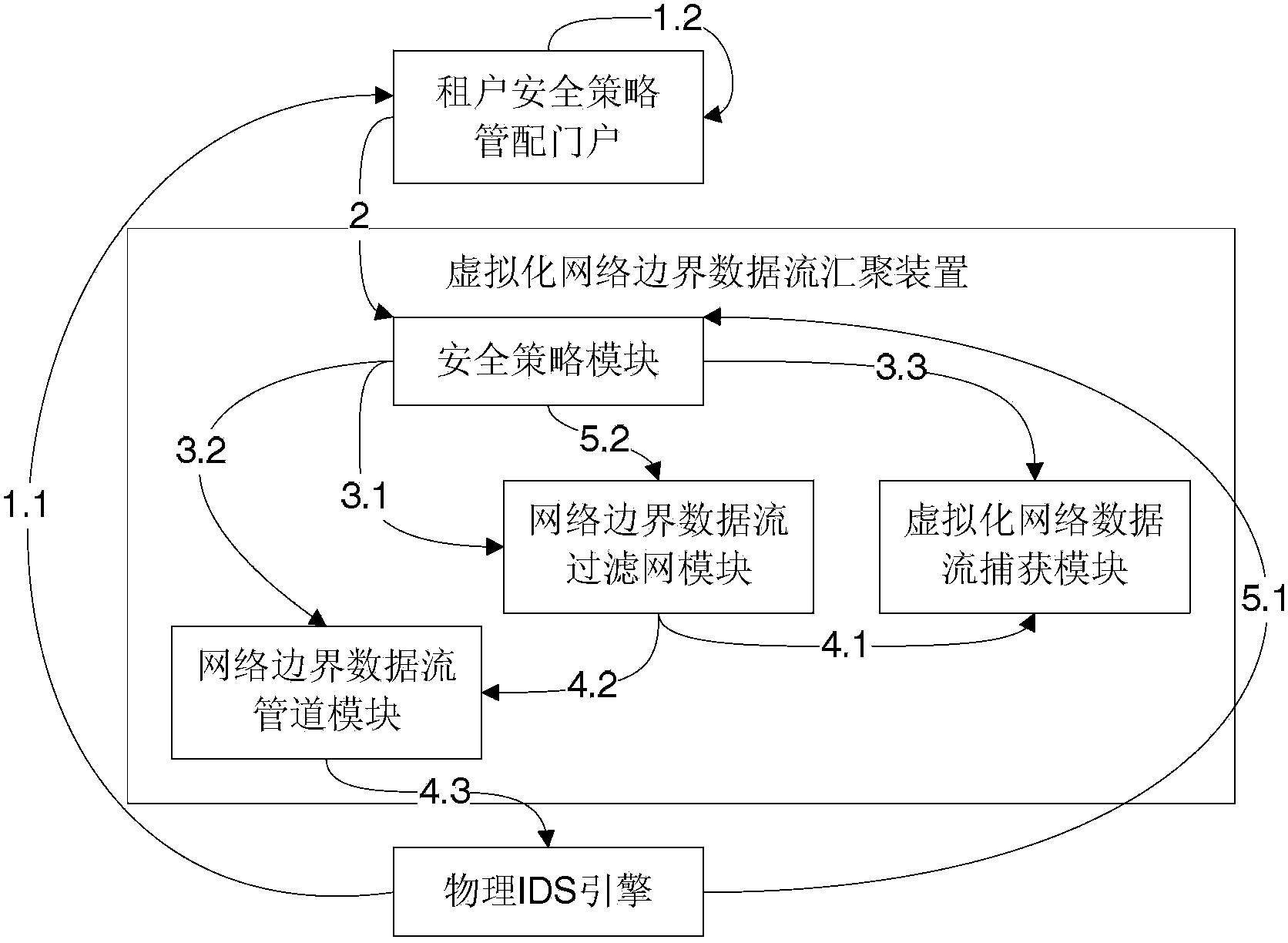
[0055] In this embodiment, as figure 2 The system architecture shown is taken as an example to introduce the working principle of a virtualized network border data flow aggregation device.
[0056] First introduce the working process of the whole system.
[0057] First, the physical IDS engine registers with the tenant security policy management portal
[0058]Then, through the tenant security policy management portal, according to the actual virtual network security domain information of the tenant, the administrator configures the security domain information managed by the IDS and the detection and audit policies of the security domain.
[0059] Next, issue a network border security policy (here, a global policy) to the virtualized network border data flow convergence device on all virtualized servers, and update the network border security policy in the virtualized network border data flow convergence device.
[0060] The working process of the device for converging data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com