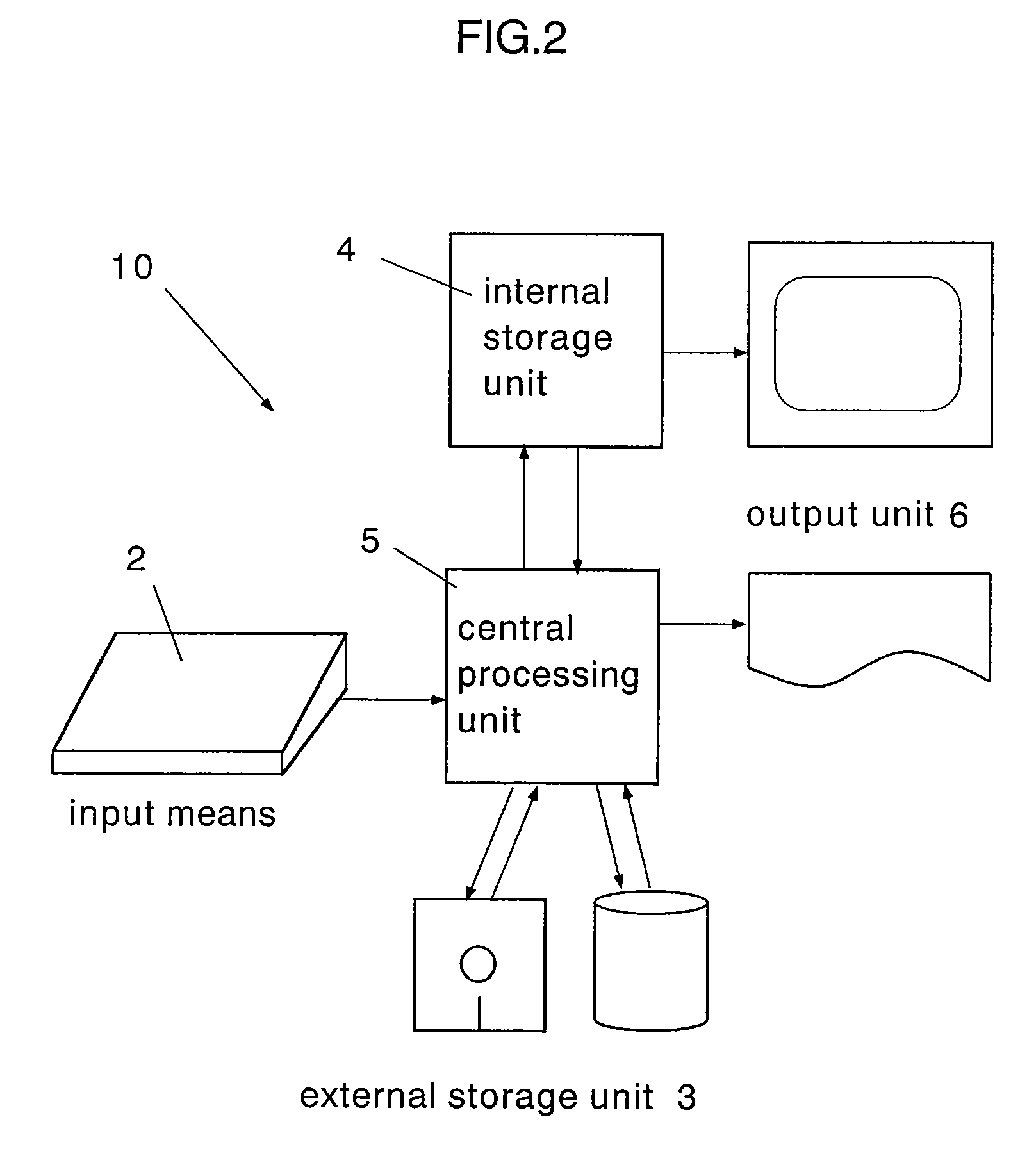
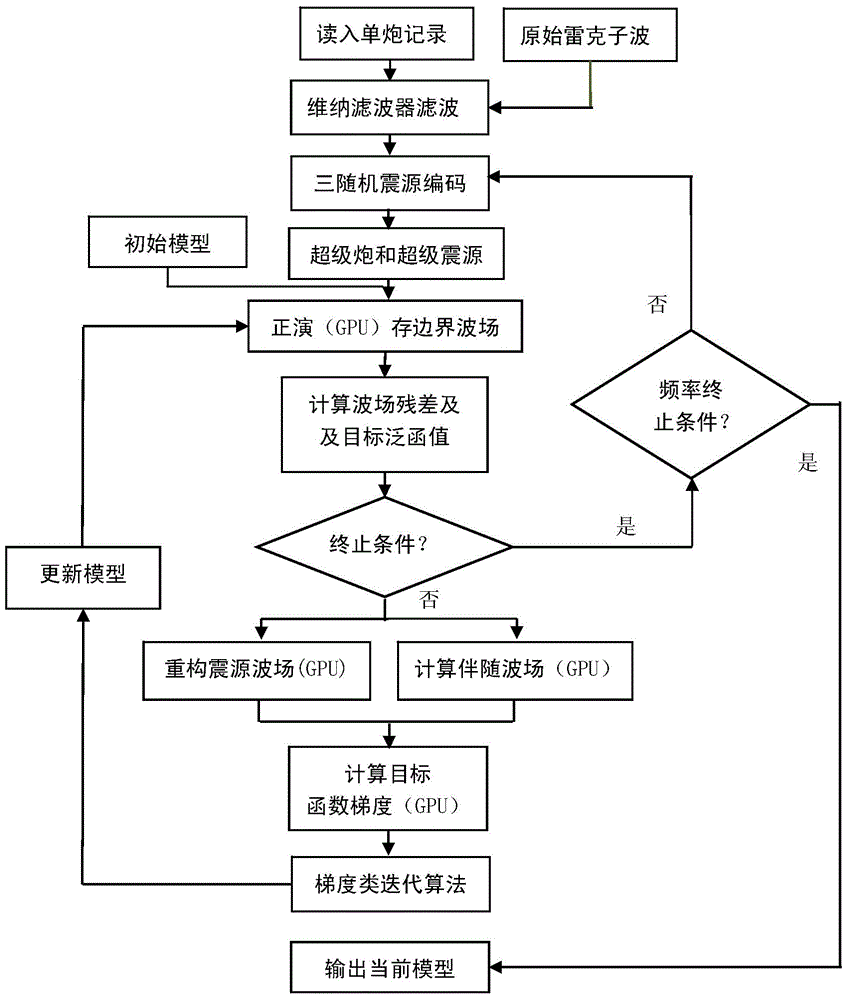
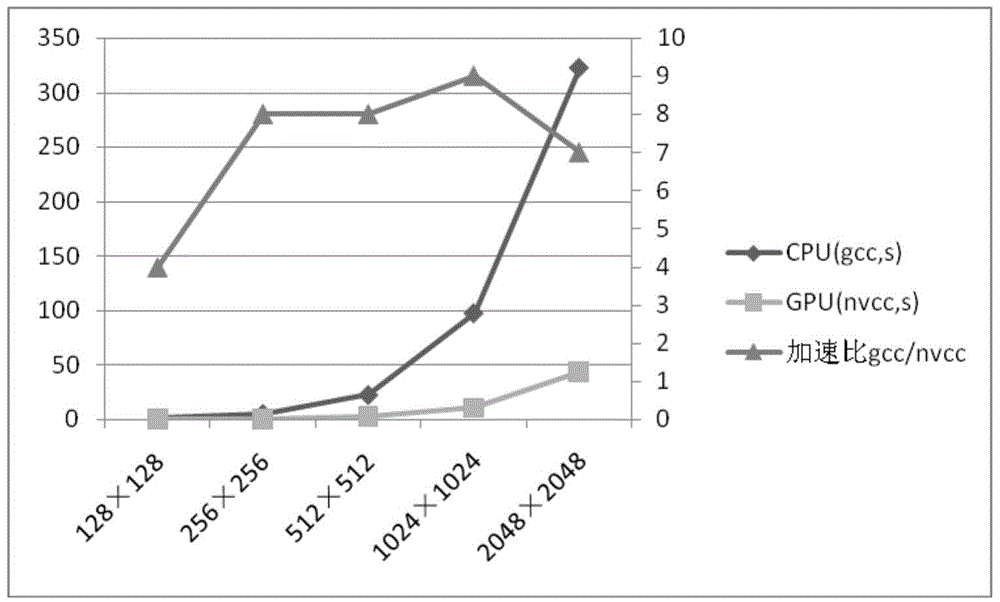
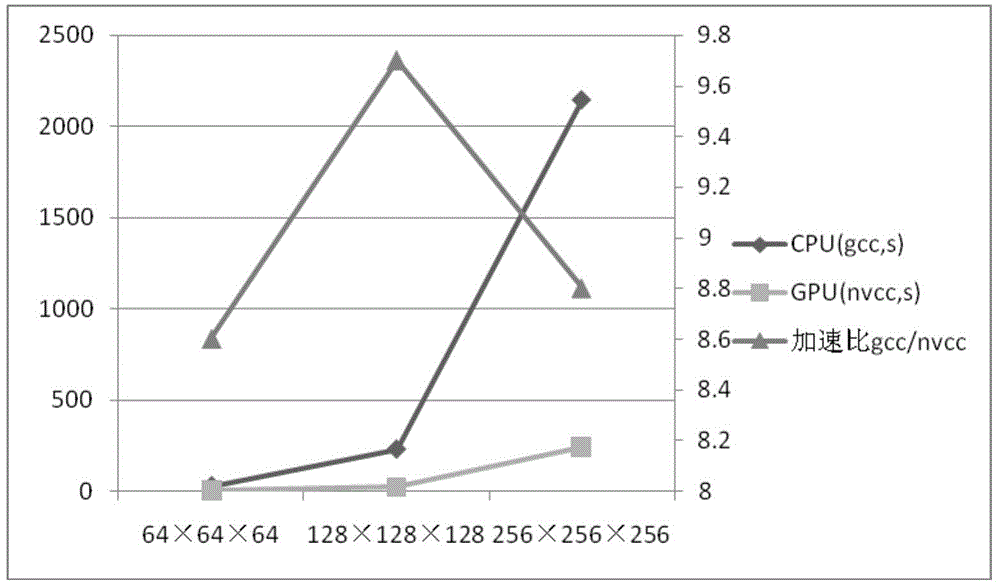
Patents
Literature
408 results about "Boundary data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Cleaning robot and cleaning method thereby
ActiveCN102138769AImprove cleaning efficiencyFloor sweeping machinesCleaning methodsComputer science
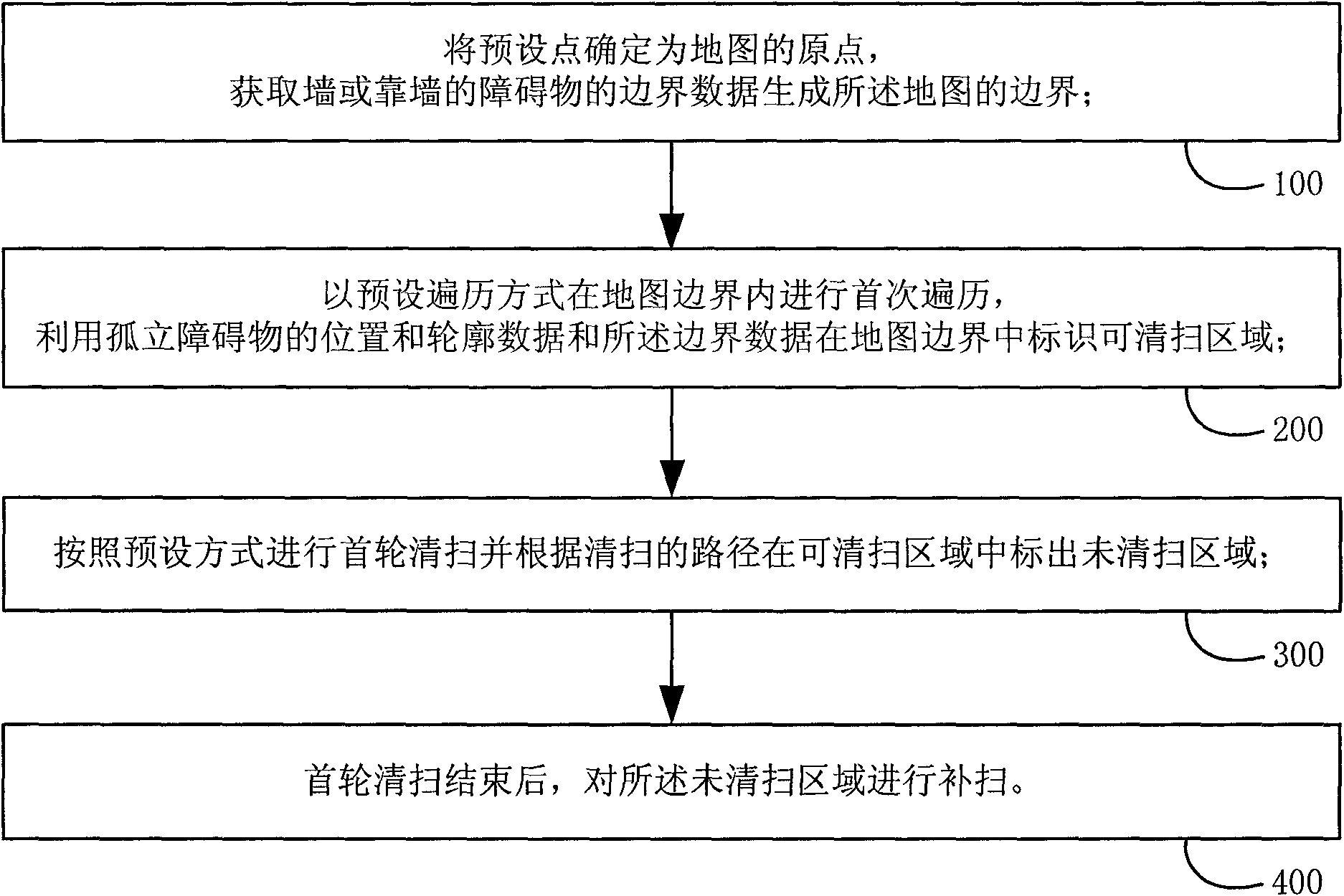
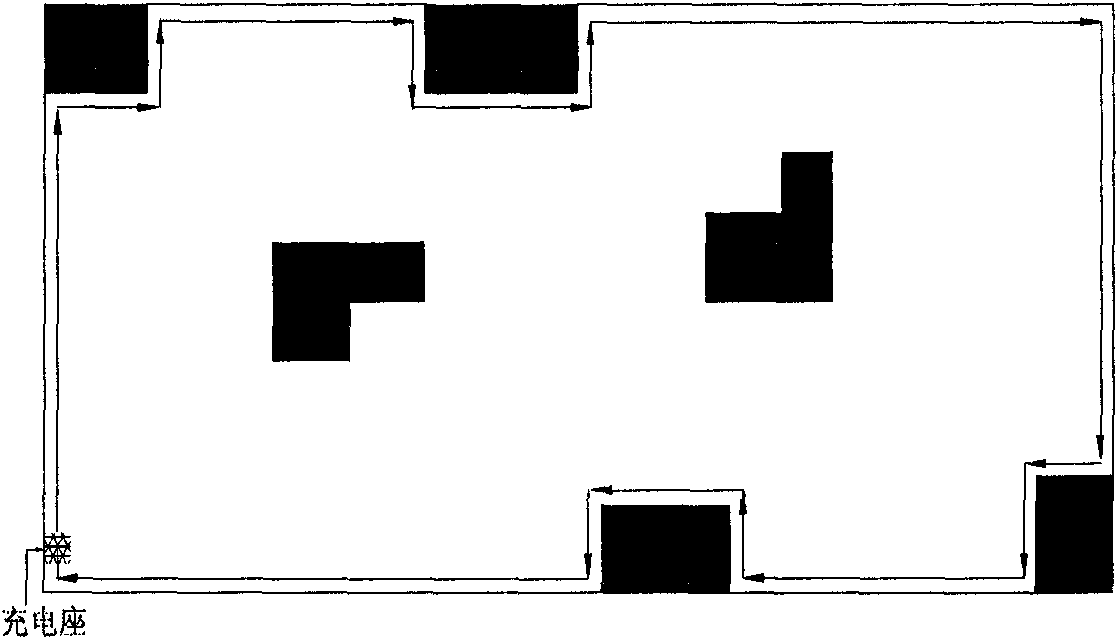
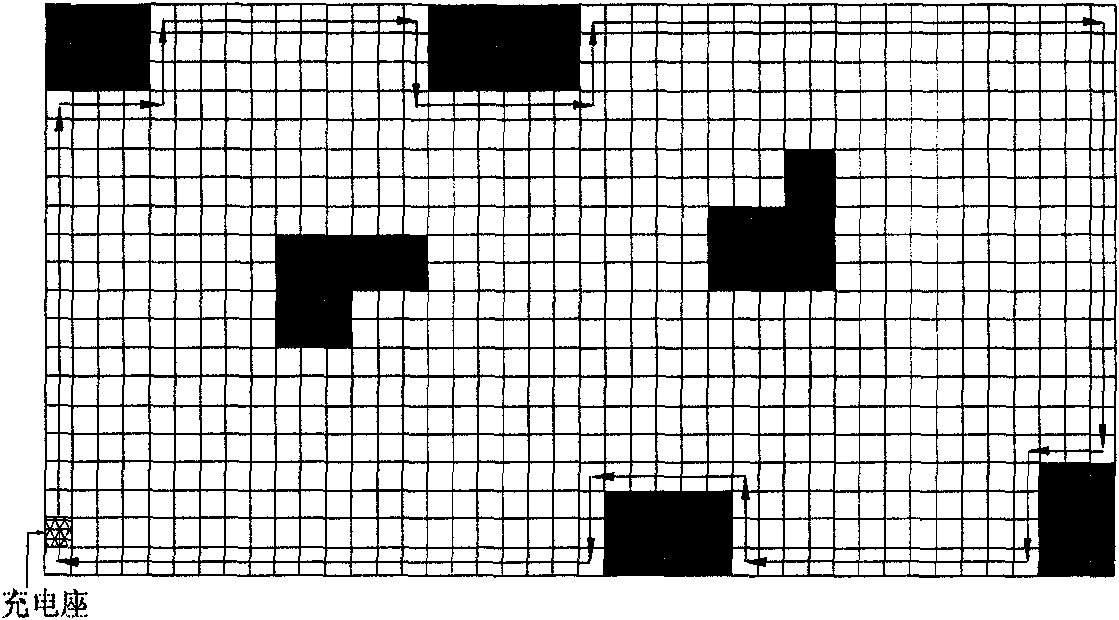
The invention provides a cleaning robot and a cleaning method thereby. On the basis of acquired detection data and the current position and gesture data, the method comprises the following steps of: determining a preset point as the original point of a map; acquiring boundary data of a wall or an obstacle near the wall to generate the boundary of the map; performing first ergodic operation in the boundary of the map in a preset ergodic mode; if encountering an isolated obstacle, acquiring position and outline data by surrounding the isolated obstacle; identifying regions which can be cleaned in the map boundary according to the position and outline data and the boundary data; at the same time of or after the first ergodic operation, cleaning according to the preset cleaning mode; identifying the non-cleaning regions in the cleaning regions according to the cleaning route; and then cleaning the non-cleaning regions. Compared with the conventional blind cleaning methods, the cleaning method has the advantage of greatly improving cleaning efficiency.
Owner:SHENZHEN INST OF ADVANCED TECH +1
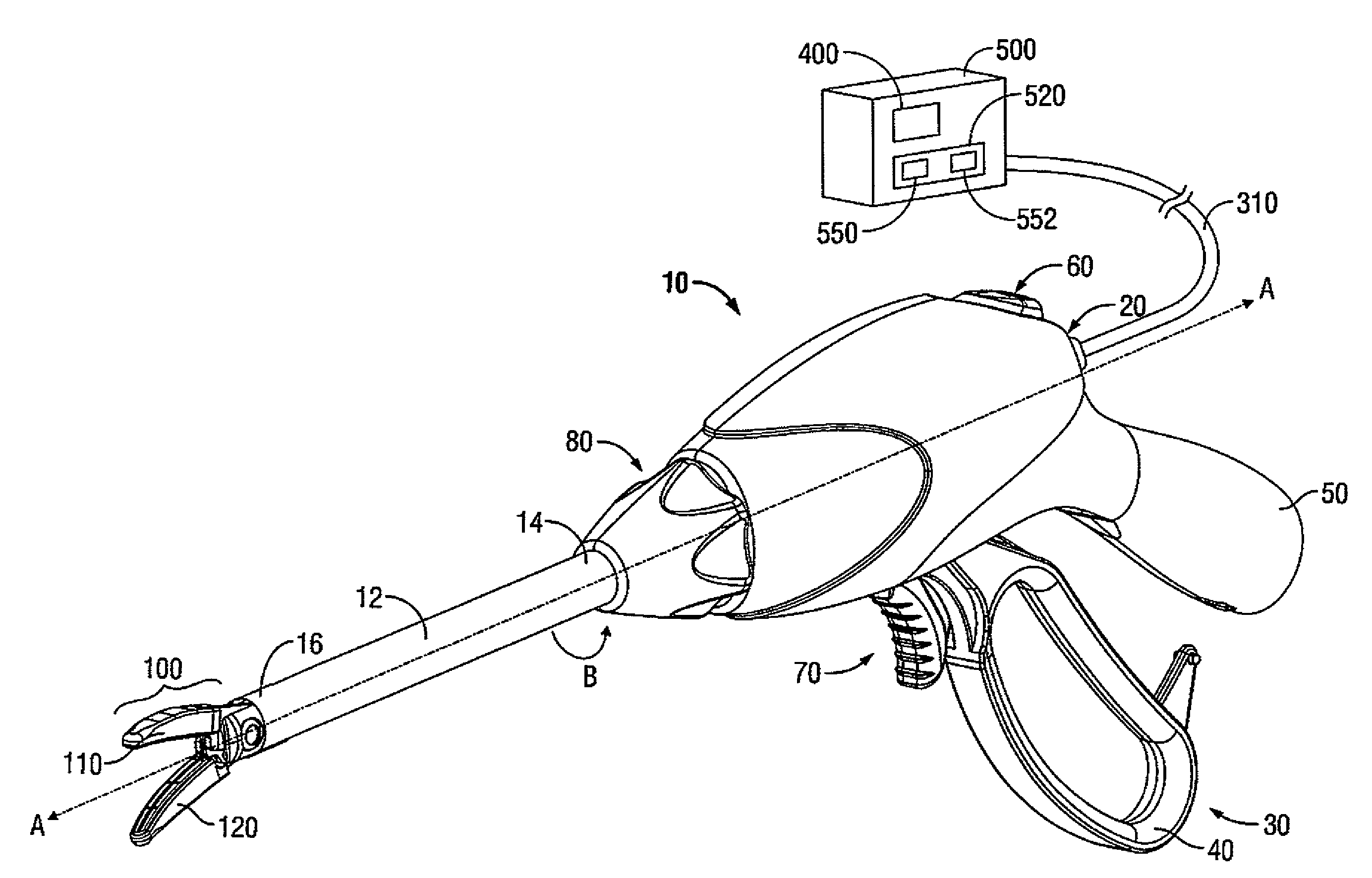
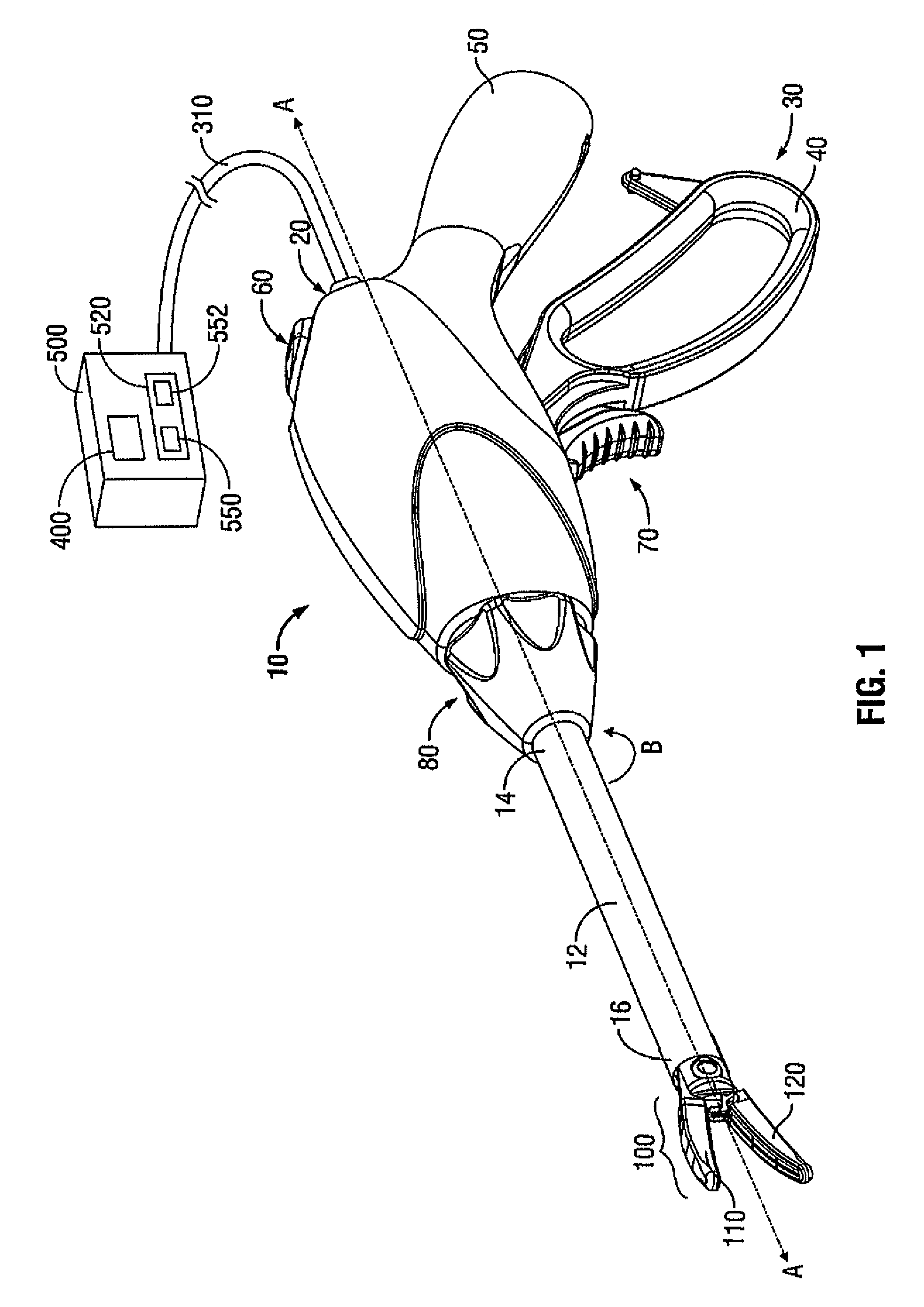
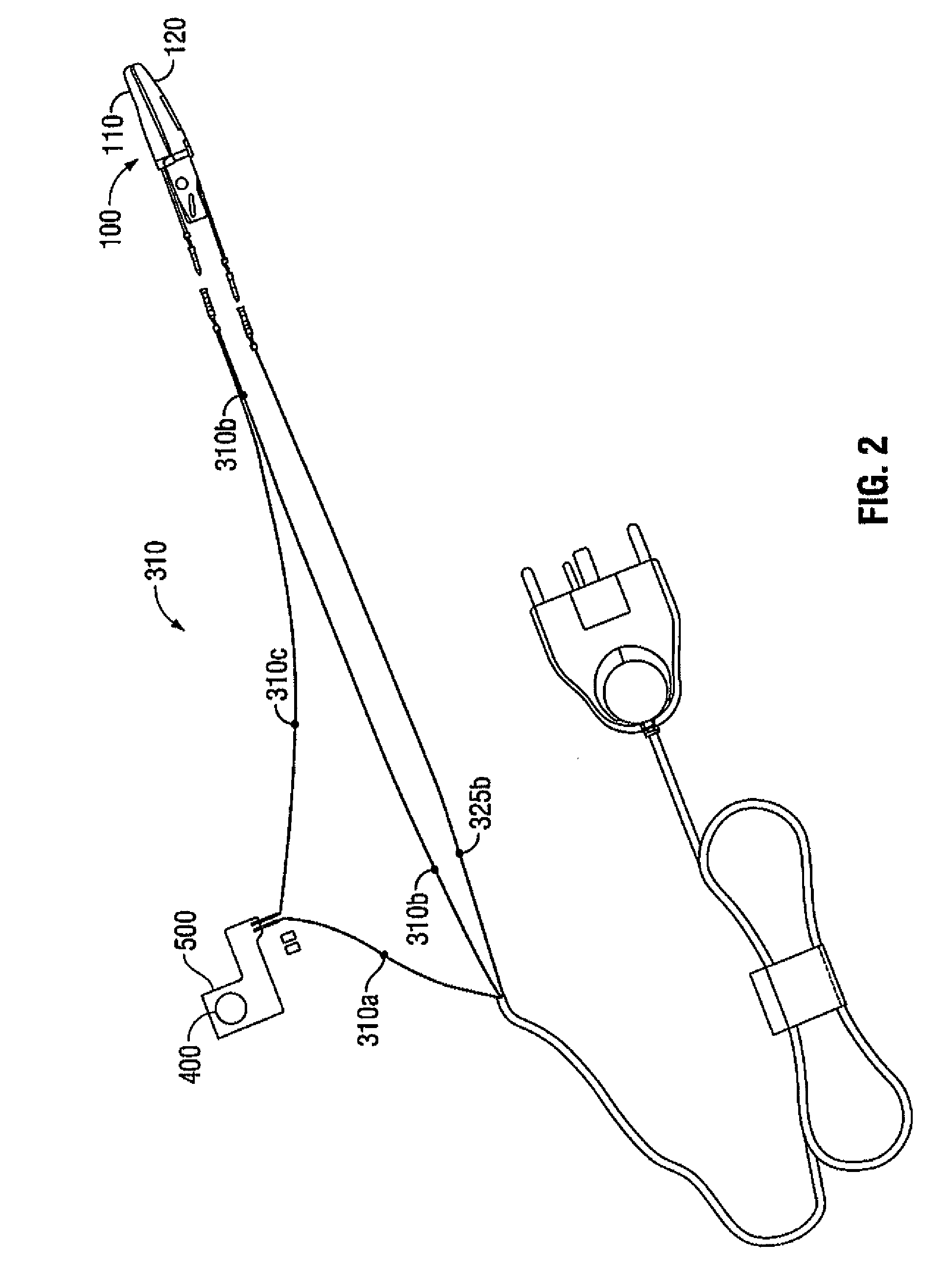
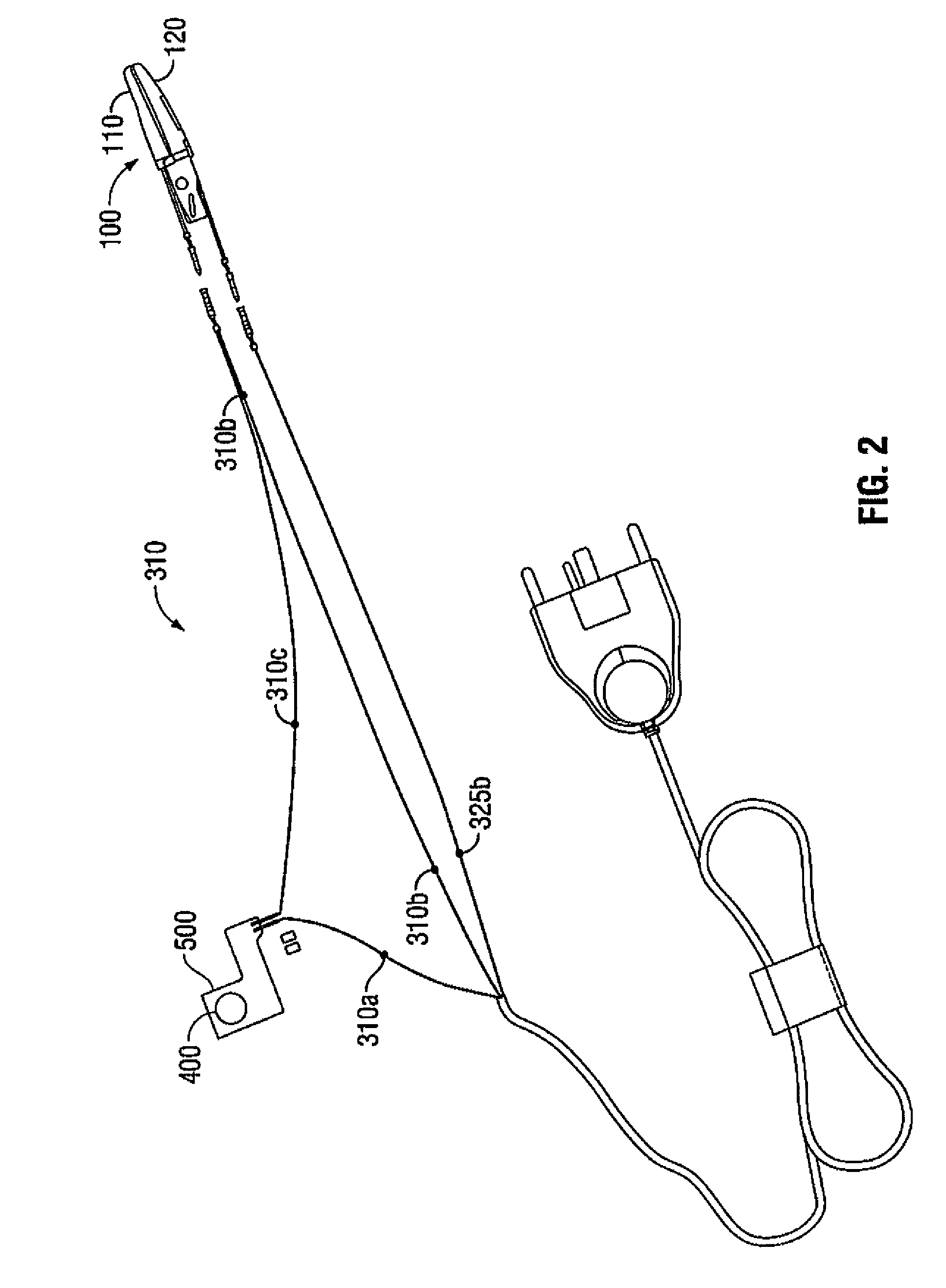
Apparatus, System and Method for Monitoring Tissue During an Electrosurgical Procedure
A system for monitoring and / or controlling tissue modification during an electrosurgical procedure is provided. The system includes an electrosurgical apparatus adapted to connect to an electrosurgical generator. The electrosurgical apparatus configured to transmit energy to tissue. The system also includes a control system having one or more electromagnetic wave sources configured to generate the interrogator wave of one or more frequencies adjacent tissue. One or more sensors are configured to transmit and sense a reflected portion of the interrogator wave of at least one frequency to determine dielectric boundary data. A processor operatively coupled to the control system and to the electrosurgical generator configured to control the delivery of electrosurgical energy from the electrosurgical generator to tissue based on dielectric boundary data provided by the one or more sensors.
Owner:TYCO HEALTHCARE GRP LP
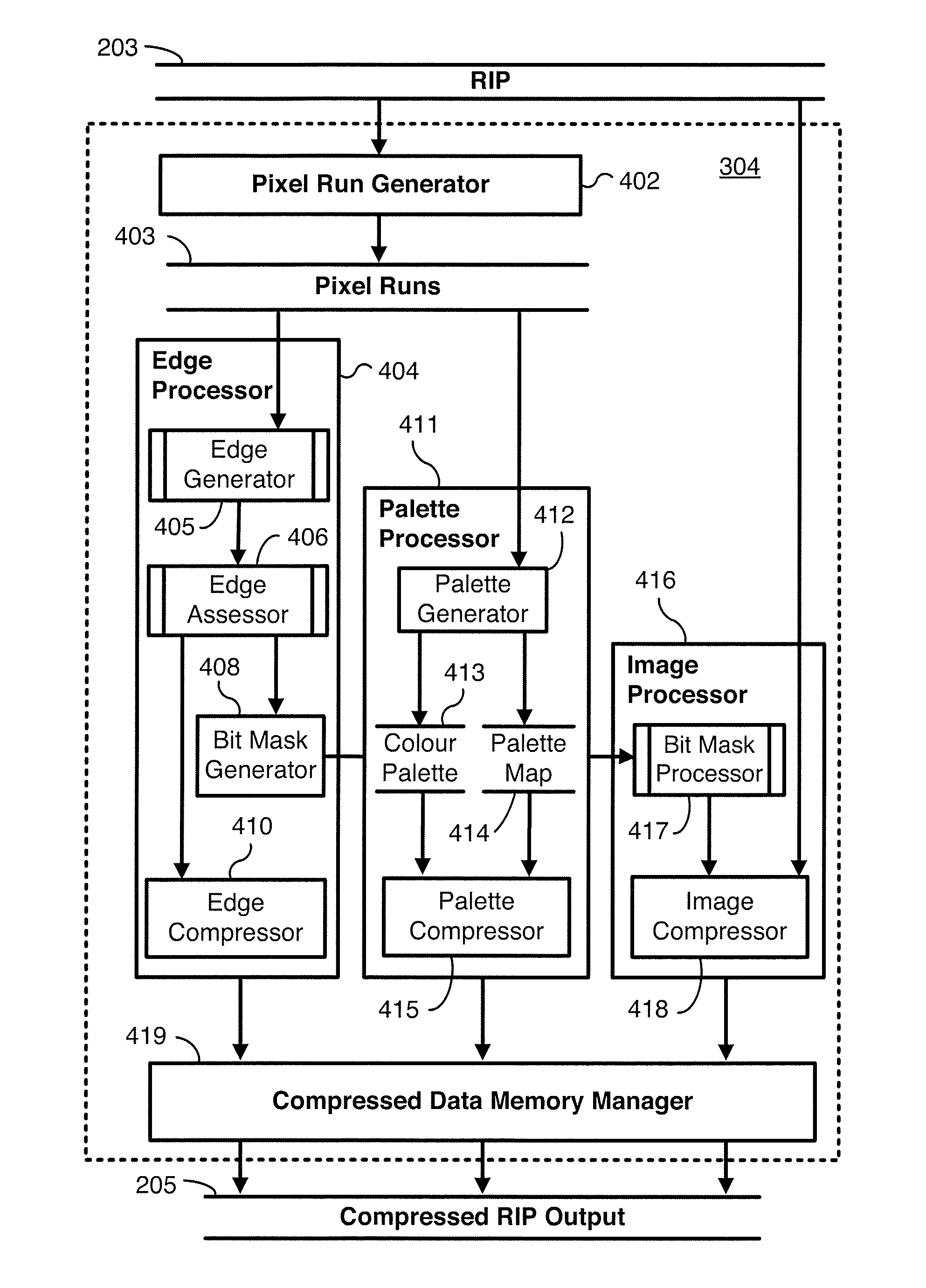
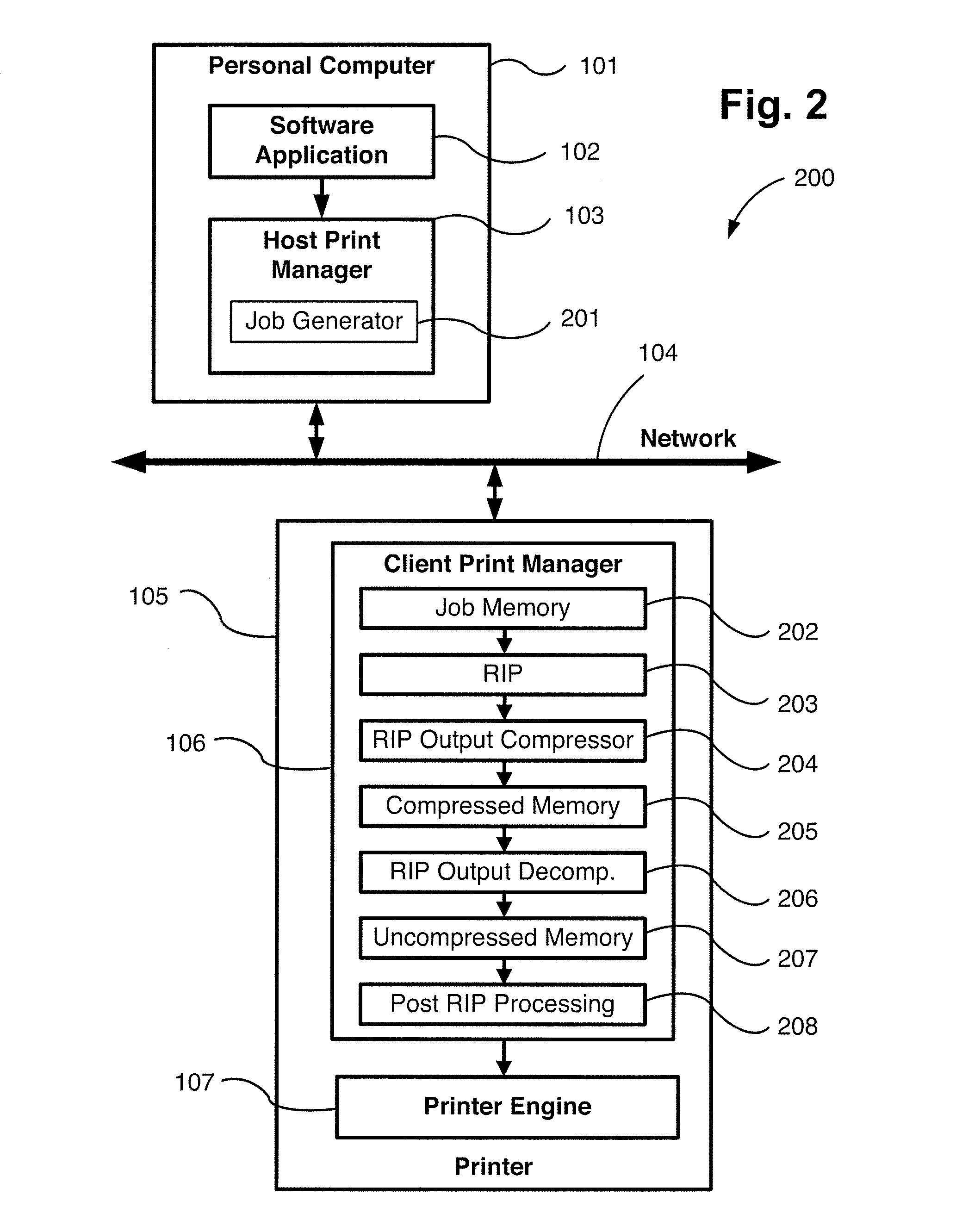
Method and Apparatus For Hybrid Image Compression
ActiveUS20080144952A1More disadvantageCharacter and pattern recognitionImage codingHybrid imageImage processor
A Hybrid Compressor (304) and method (500) of compressing a tile (2200) of pixels within an image are disclosed. An Edge Processor (404) of the Hybrid Compressor (304) analyses pixel runs (403) of the tile (2200) and generates boundary data defining one or more regions comprising pixels of substantially identical colour. A Palette Processor (411) of the Hybrid Compressor (304) generates data defining a colour value for each region. An Image Processor (416) of the Hybrid Compressor (304) generates a representation of pixels not included in the one or more regions.
Owner:CANON KK
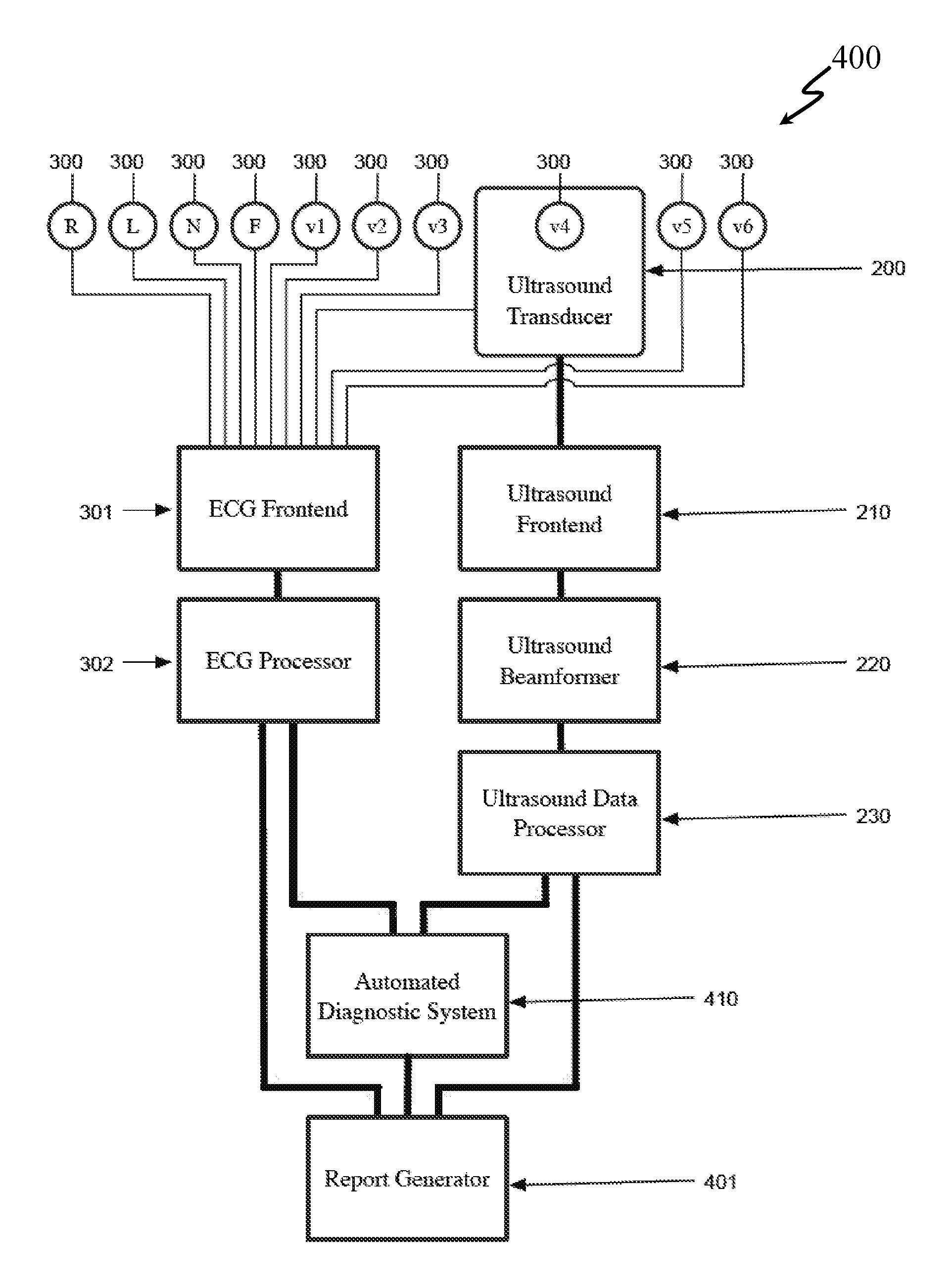
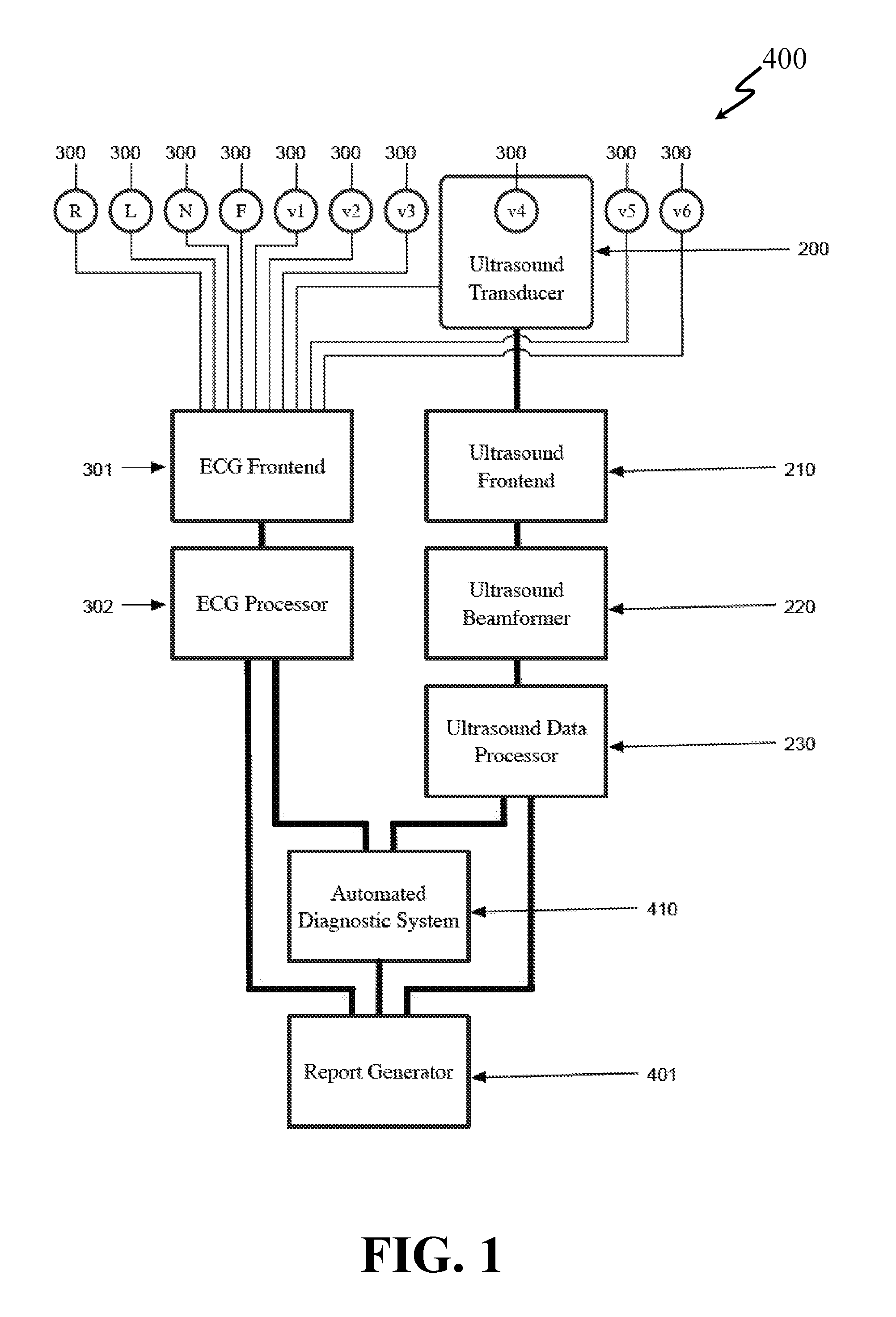
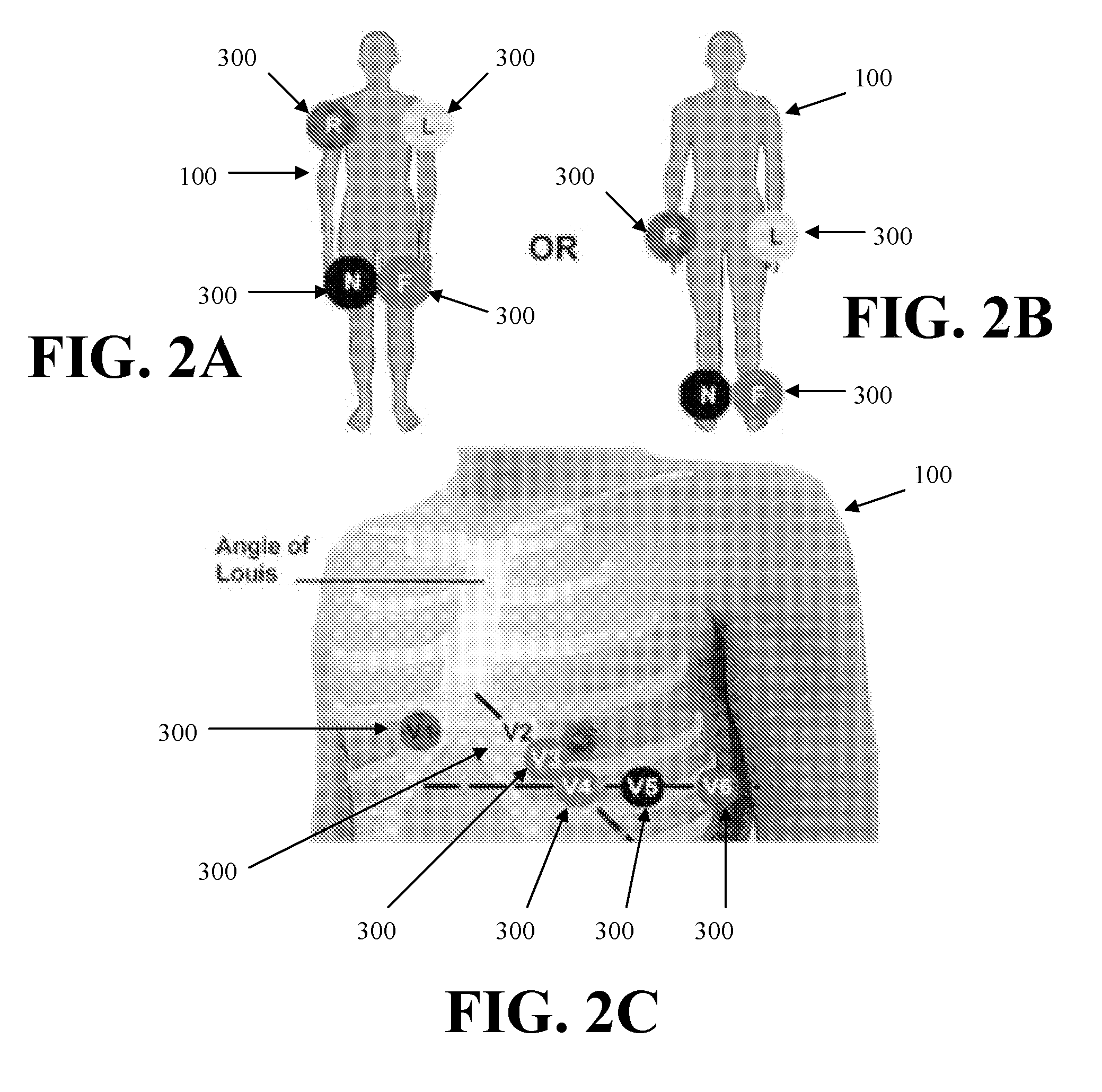
System and Method for Combined ECG-Echo for Cardiac Diagnosis
InactiveUS20100168578A1Low costSmall sizeUltrasonic/sonic/infrasonic diagnosticsDiagnostic recording/measuringSonificationCardiac muscle
A system and related method for obtaining volumetric cardiac data of a subject. The data is generated by forming a plurality of focused ultrasound images corresponding to a series of ranges, generating myocardial boundary data for each of the plurality of ultrasound images, calculating the area of the region defined by said myocardial boundary data for each of the plurality of ultrasound images, multiplying the area for each of the plurality of ultrasound images by a slice depth corresponding to said ultrasound image to obtain the slice volume of each slice, and summing the slice volumes to obtain a total volume. In an alternative embodiment the system and related method combine an automated volumetric ultrasound system for finding chamber volumes and myocardial thicknesses, with a diagnostic electrocardiogram system to enable simultaneous diagnosis of mechanical and electrical cardiac problems.
Owner:UNIV OF VIRGINIA ALUMNI PATENTS FOUND
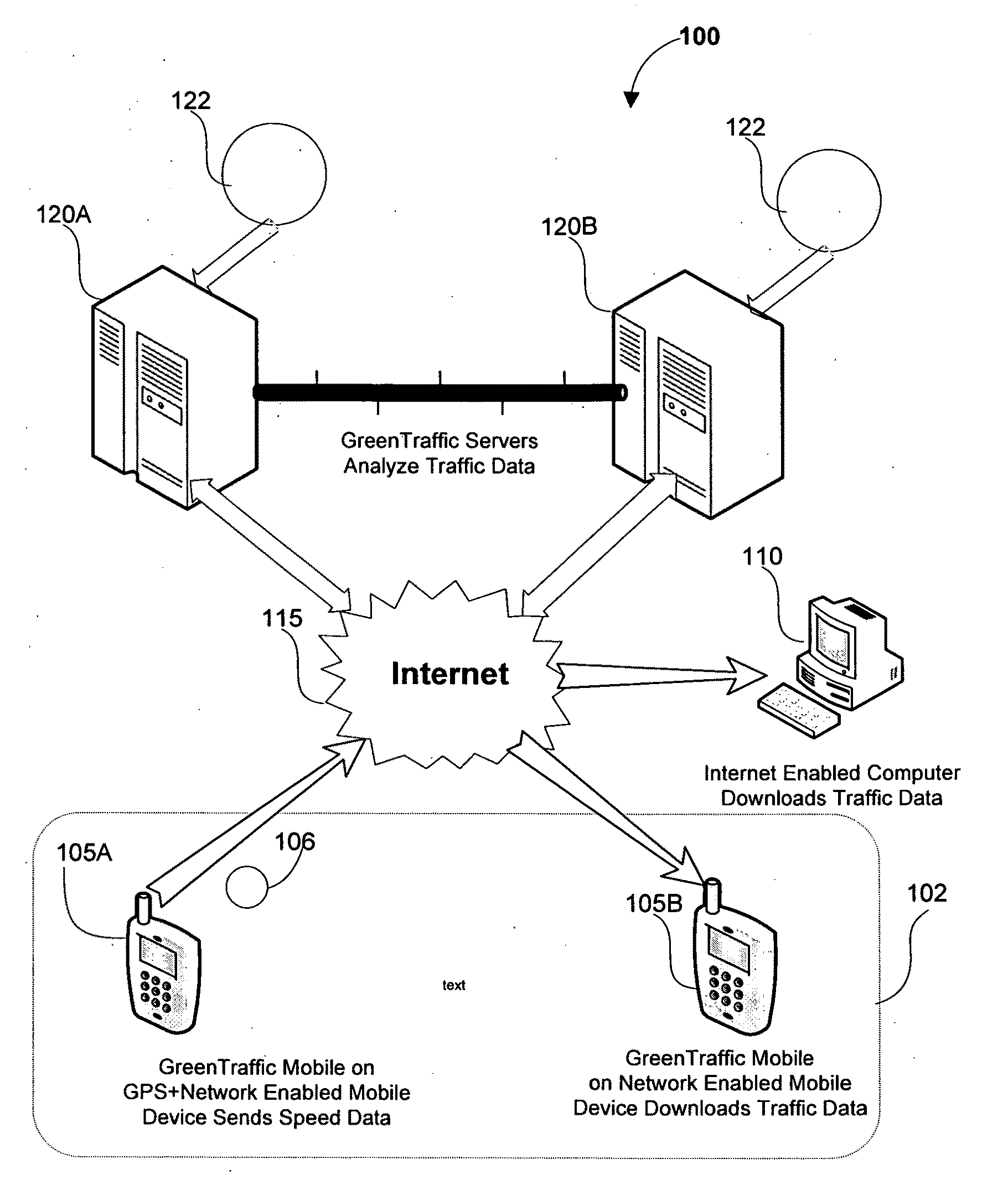
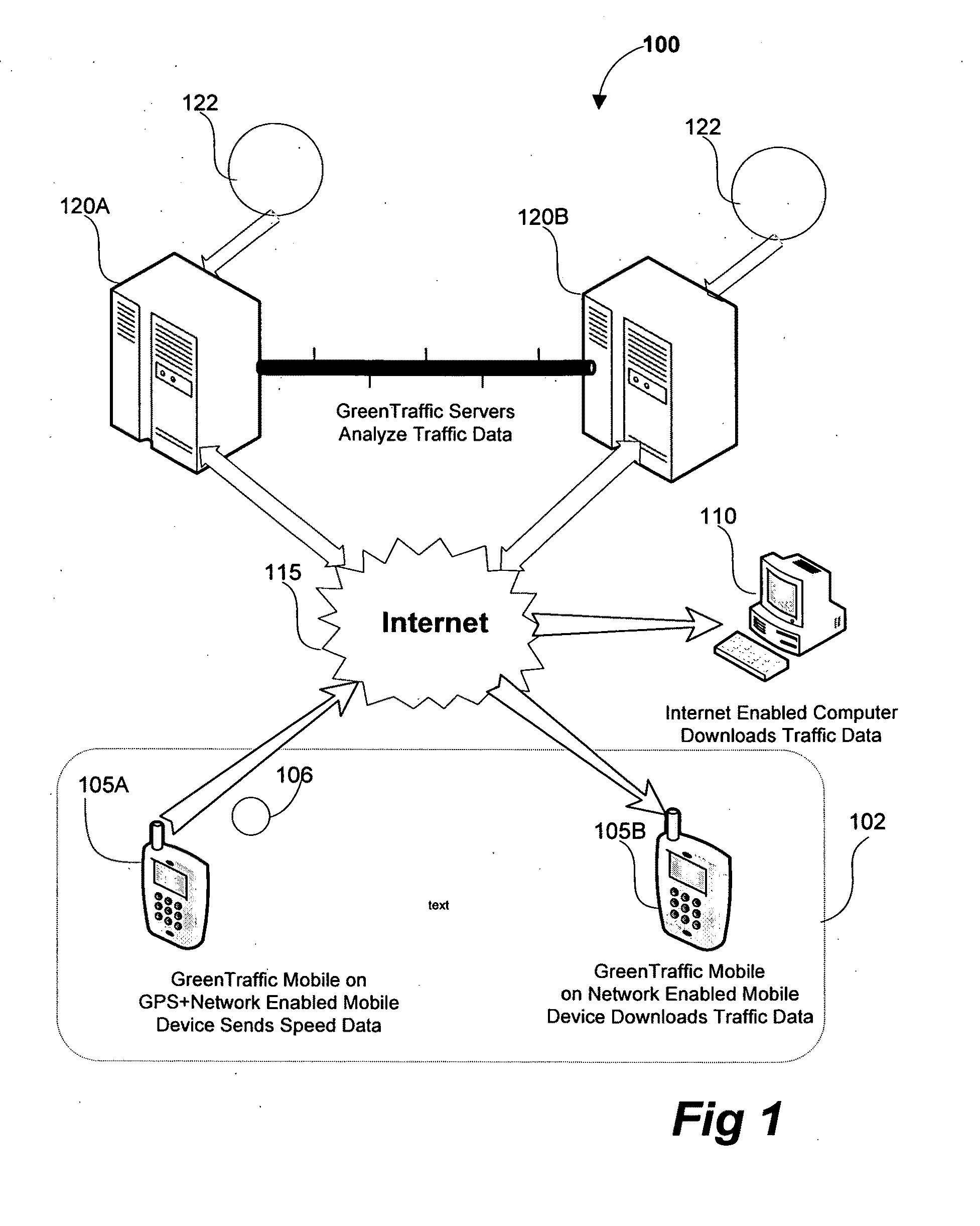
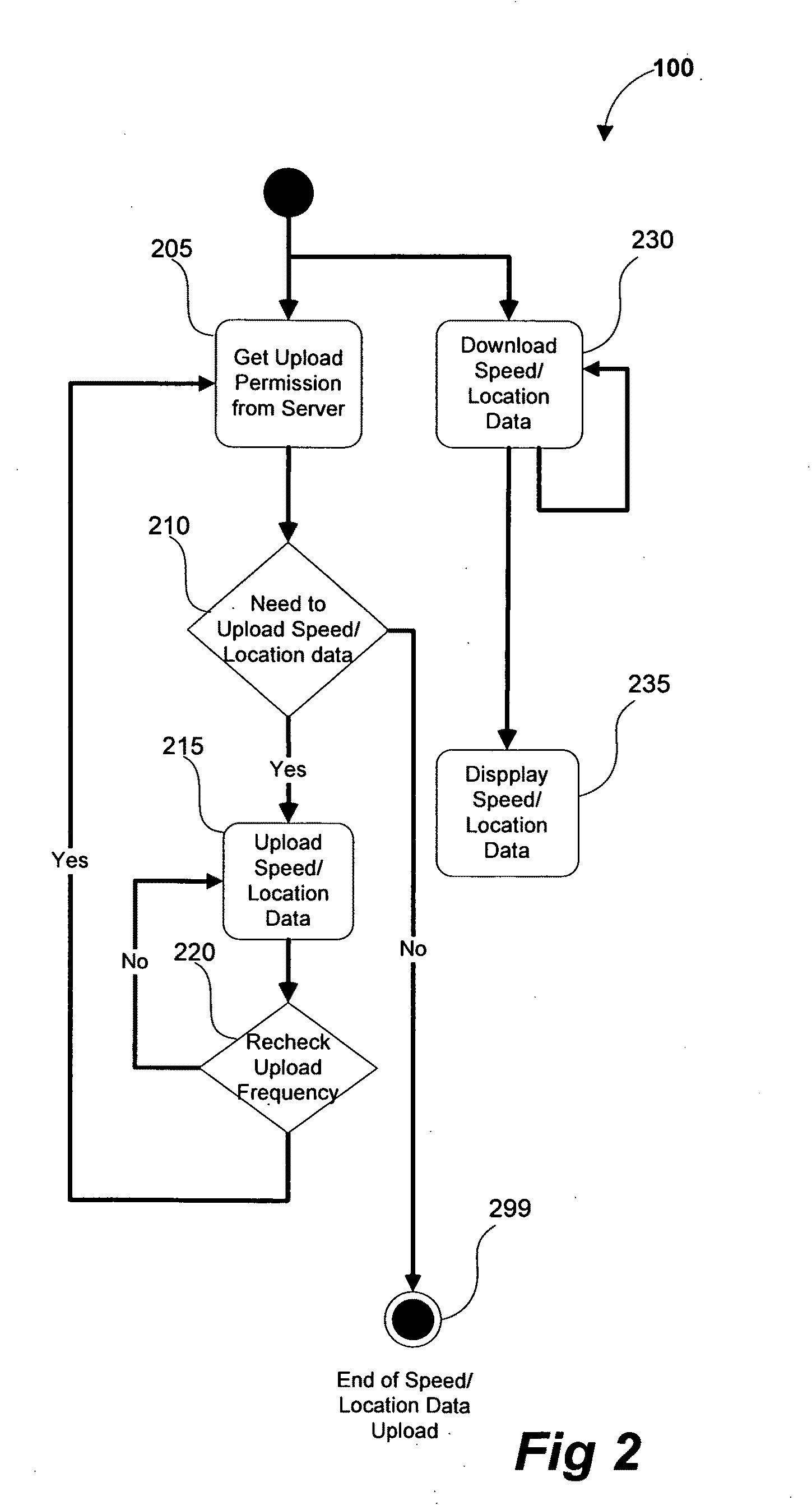
Universal GPS Traffic Monitoring System
InactiveUS20100100307A1Reduce loadReduce power consumptionAnalogue computers for vehiclesDirection finders using radio wavesData storeProcess information
A traffic data collection process and monitoring system that uses a plurality of GPS enabled mobile devices to transmit near at real-time traffic direction and speed information to a server and or / at real-time (sub 10 second latency). The sever processes the information thereby reducing the computational load and power consumption of the mobile devices. The system uses a Traffic Pattern Recognition software program that accurately recognizes only valid traffic data while filtering out unwanted traffic data. The system creates a Distributed Traffic Data Store database containing the average speeds for designated traffic monitoring points created for the region. During use, a request for traffic data containing the boundary data and the zoom level is sent from the mobile device to the server. The server then reviews the requests and determines with specific Distributed Traffic Data Store database contains the information. The server then creates a compressed file containing the traffic information relevant to the TMPs in the request and sends it to the mobile device.
Owner:KIM JIN HONG
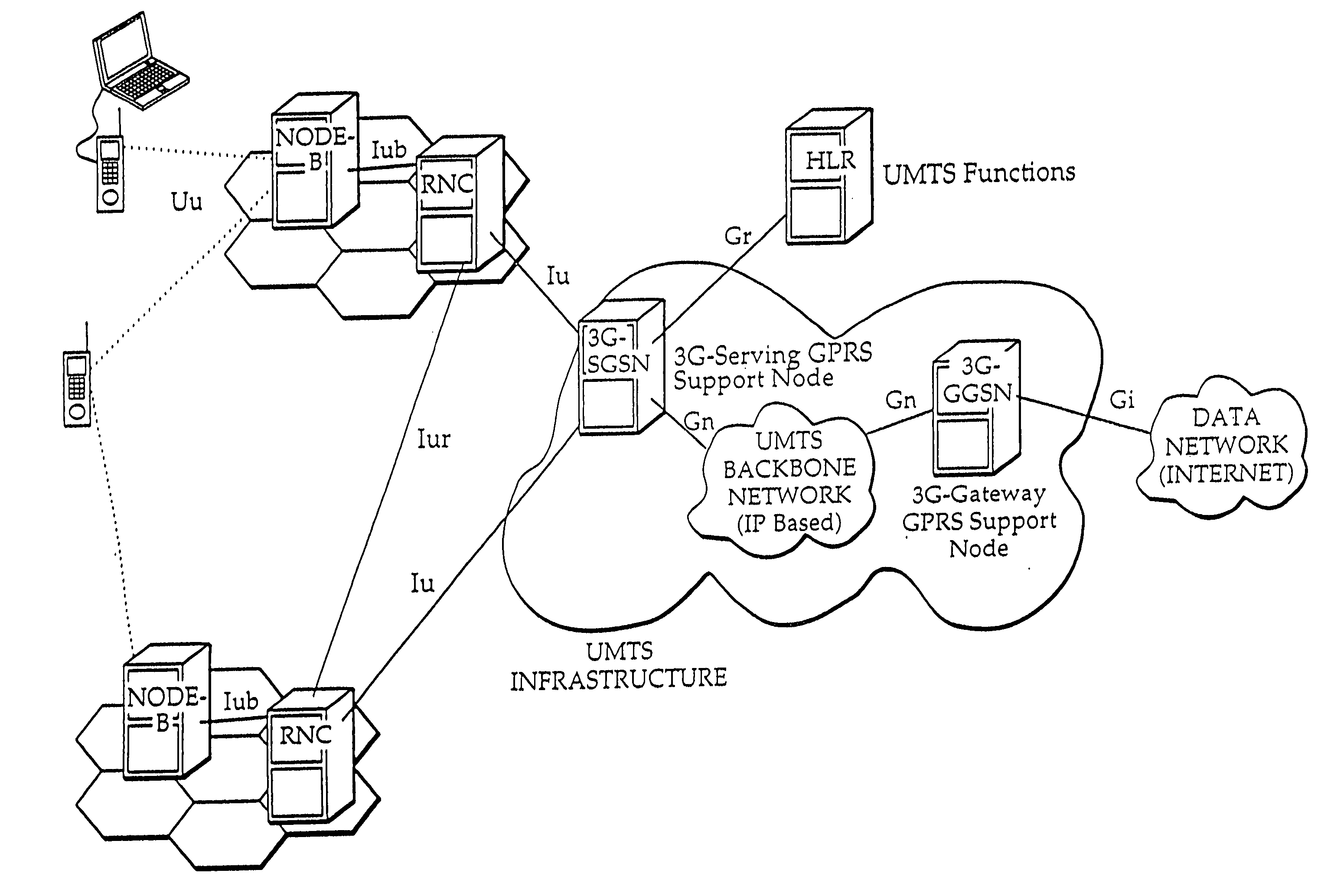
Method, apparatus, data structure, computer program, and system for providing appropriate QoS end-to-end for data crossing network boundaries
InactiveUS20050185651A1Network traffic/resource managementData switching by path configurationQuality of serviceComputer science
Data is structured with information indicative of time-related, bandwidth-related, or class-related quality-of-service (QoS) required for sending the data so that a receiving terminal or any network element processing the data in transit over a network is able to determine whether the required quality-of-service has actually been uniformly experienced by the data and, in case the quality-of-service is degraded in any section of the network, the receiving terminal or the network element is able to cause the network to either uniformly accord to the data a degraded quality-of-service corresponding to that actually experienced or to actually uniformly provide the required quality-of-service between the sending and receiving terminals by improving the processing of the data by the network element or elements. A corresponding method, apparatus, system and computer programs are shown.
Owner:NOKIA CORP
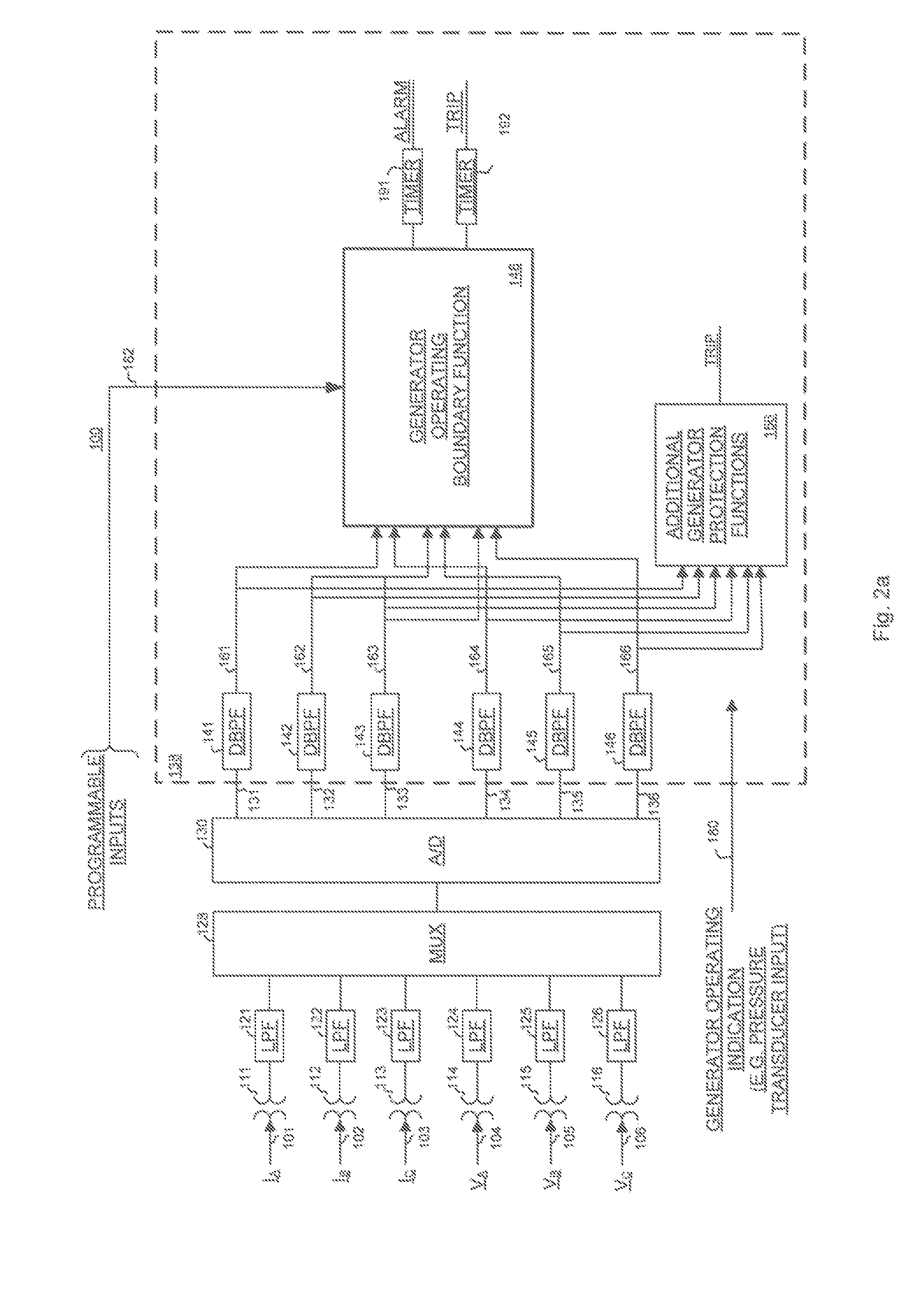
Apparatus and method for providing protection for a synchronous electrical generator in a power system
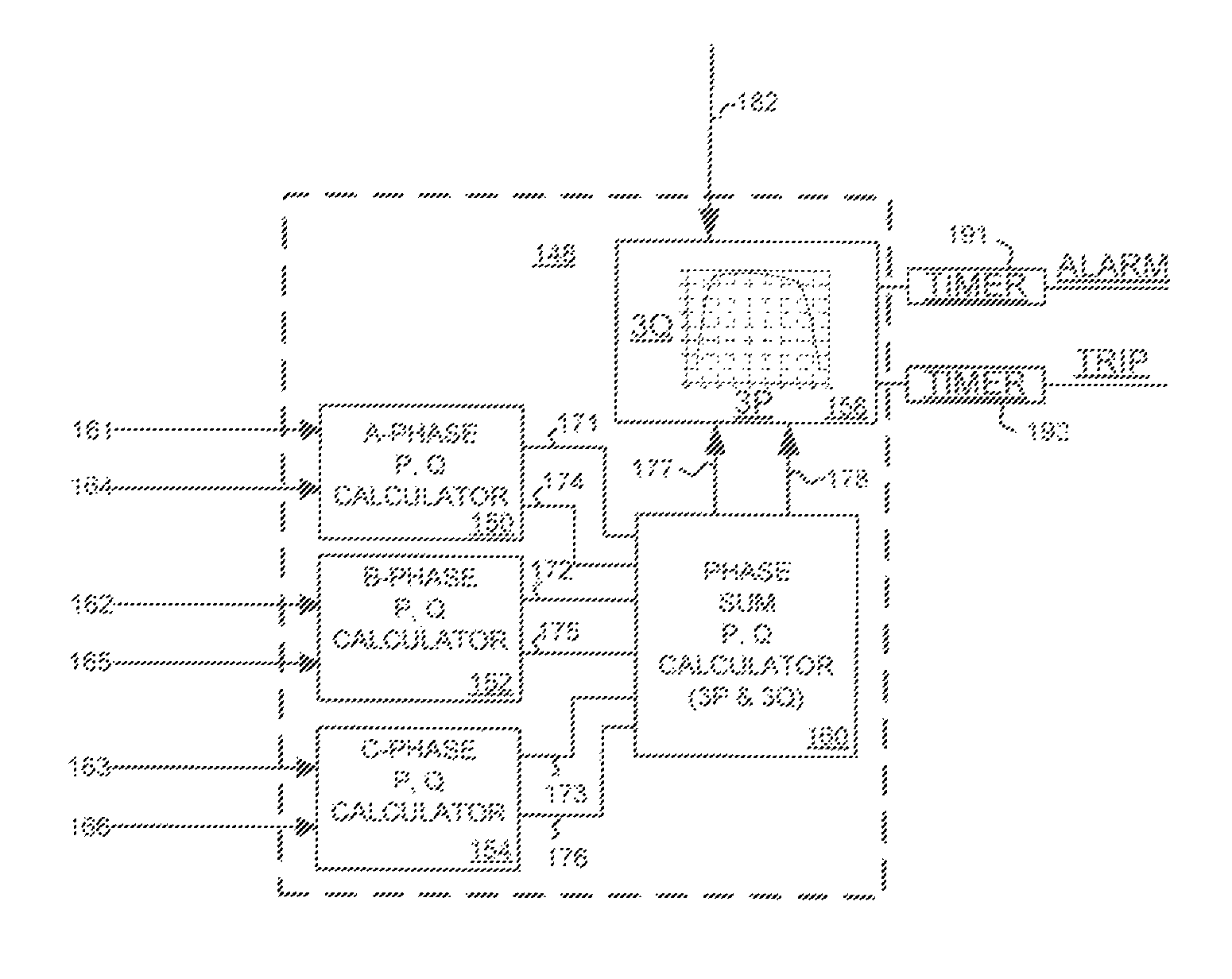
ActiveUS7710693B2Provide protectionGeneration protection through controlDynamo-electric converter controlSteady state stabilityThree-phase
An apparatus and method provide protection for a synchronous generator in a power system. The method includes deriving a plurality of generator safe operating boundary data expressions from power system data and / or user-defined inputs. The power system data may include a plurality of generator data supplied by a manufacturer of the generator and / or power system parameters such as power system equivalent impedance. Each generator safe operating boundary data expression may relate to a generator capability curve, a steady-state stability limit curve, a minimum excitation limiter curve, an over excitation limiter curve, or an user-defined curve. The method also includes calculating an active power value sum and a reactive power value sum based on generator three-phase currents and voltages, comparing these sums to at least one of the plurality of generator safe operating boundary data expressions, and to provide protection and / or alarming functions for the generator based on this comparison.
Owner:SCHWEITZER ENGINEERING LABORATORIES
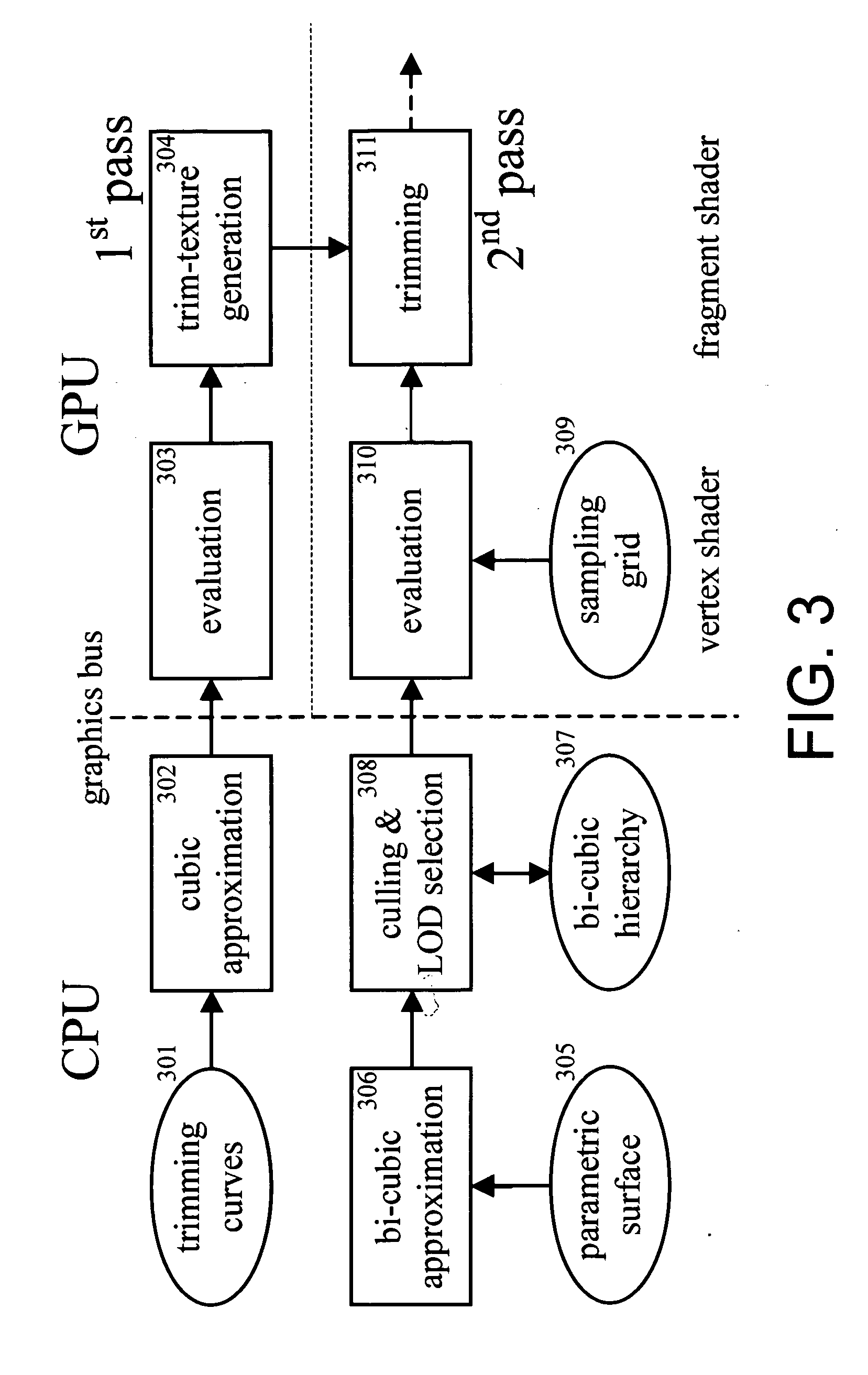
Method and applications for rasterization of non-simple polygons and curved boundary representations
A hardware-accelerated method for the rasterization of non-simple polygons is used to generate a trim-texture that is dynamically adapted to the required resolution. This method is combined with a GPU-based tessellation of parametric surfaces and a method to generate non-simple polygons with the required resolution from the parametric trimming curves on the GPU. This way trimming and tessellation of parametric surfaces like rational Bézier and Spline surfaces can be performed on the GPU. The method can also be used for the visualization of 2D boundary data on arbitrary parametric surfaces.
Owner:GUTHE MICHAEL
Robot map establishing and storing method
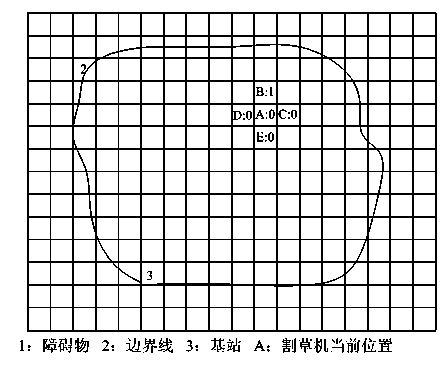
ActiveCN104035444AImplement the buildImplement storagePosition/course control in two dimensionsComputer scienceX-Coordinate
The invention discloses a robot map establishing and storing method. The method comprises the steps that an electronic compass and a speedometer are used for achieving positioning and coordinate calculation of a robot combined with a GPS, before map data are established, the robot operates a circle around a working area along a boundary first, map boundary data are established, the mapping relation of the map data and the address of a storage unit is calculated, then the robot operates in the area, and then internal map data are established. The format of the map data is {X coordinate, Y coordinate and map grid attributes}, and in order to facilitate data storage, the data are mapped into storage space according to a certain rule.
Owner:SOUTHEAST UNIV
Method and device for numberical analysis of flow field of non-compressive viscous fluid, directly using v-cad data
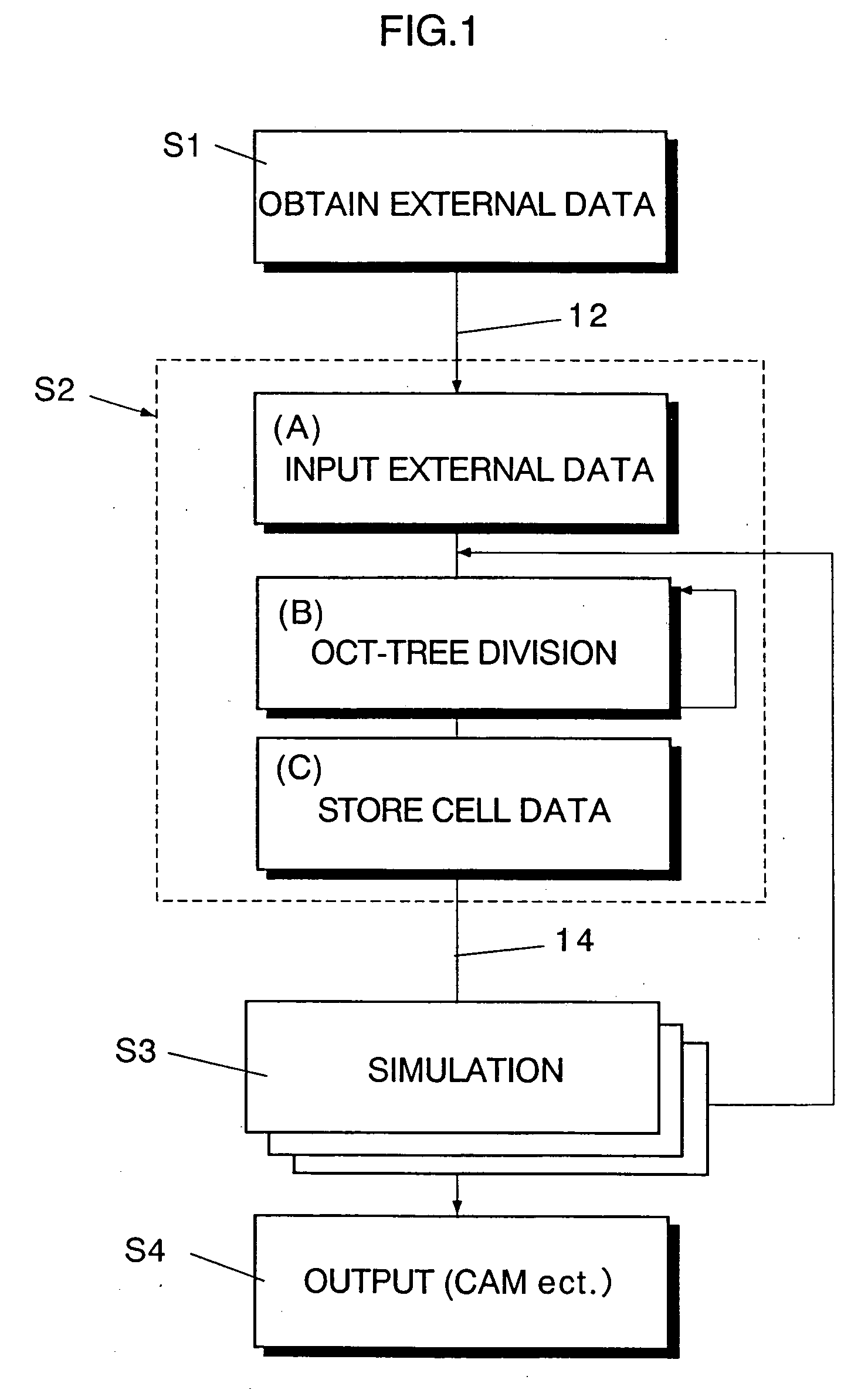
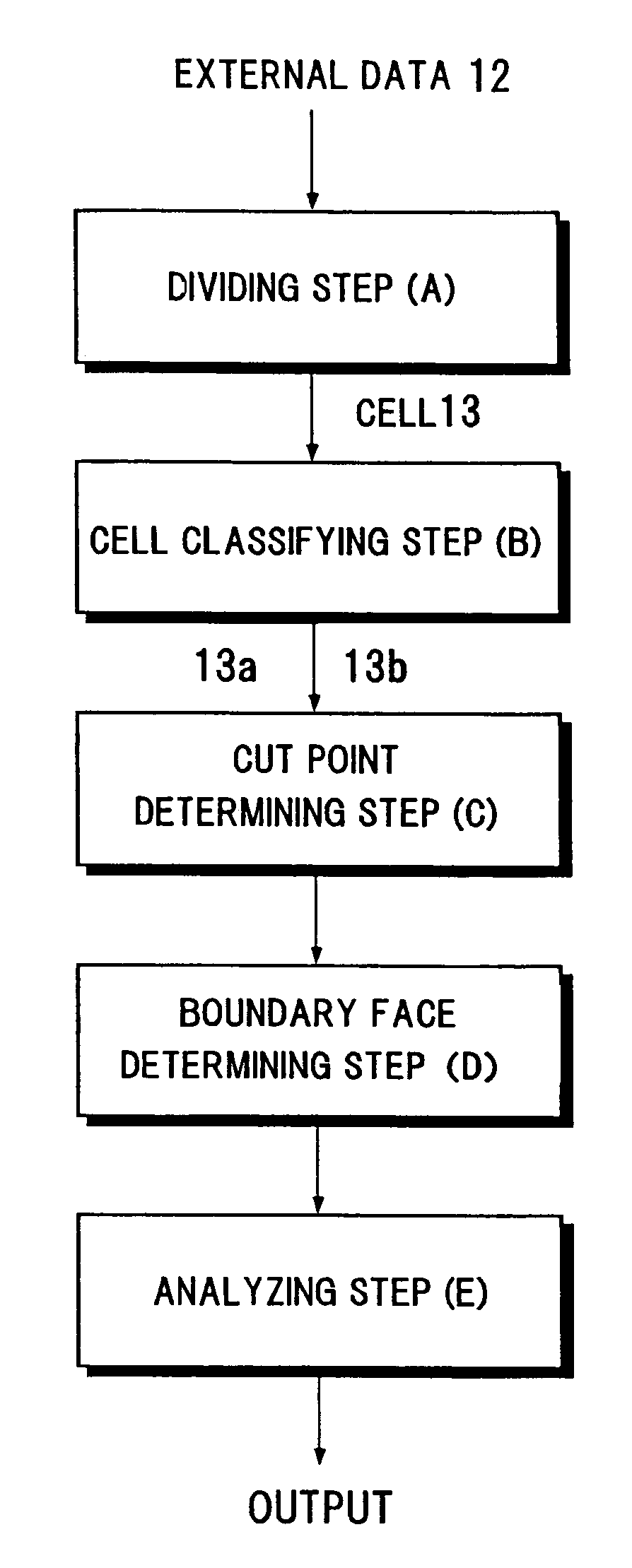
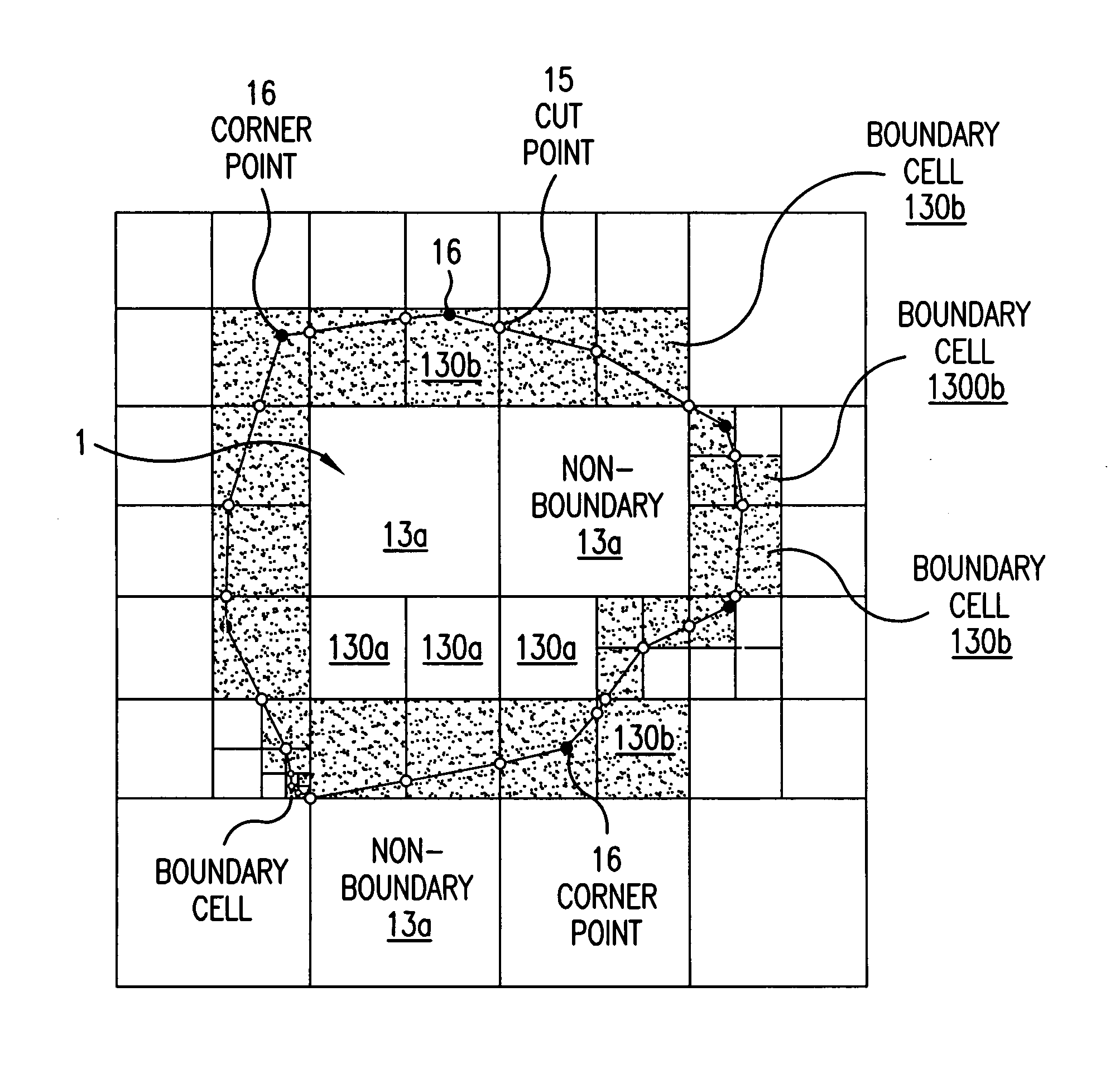
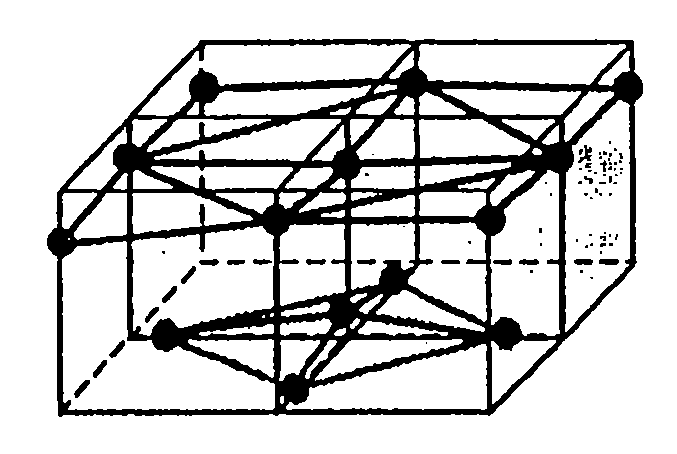
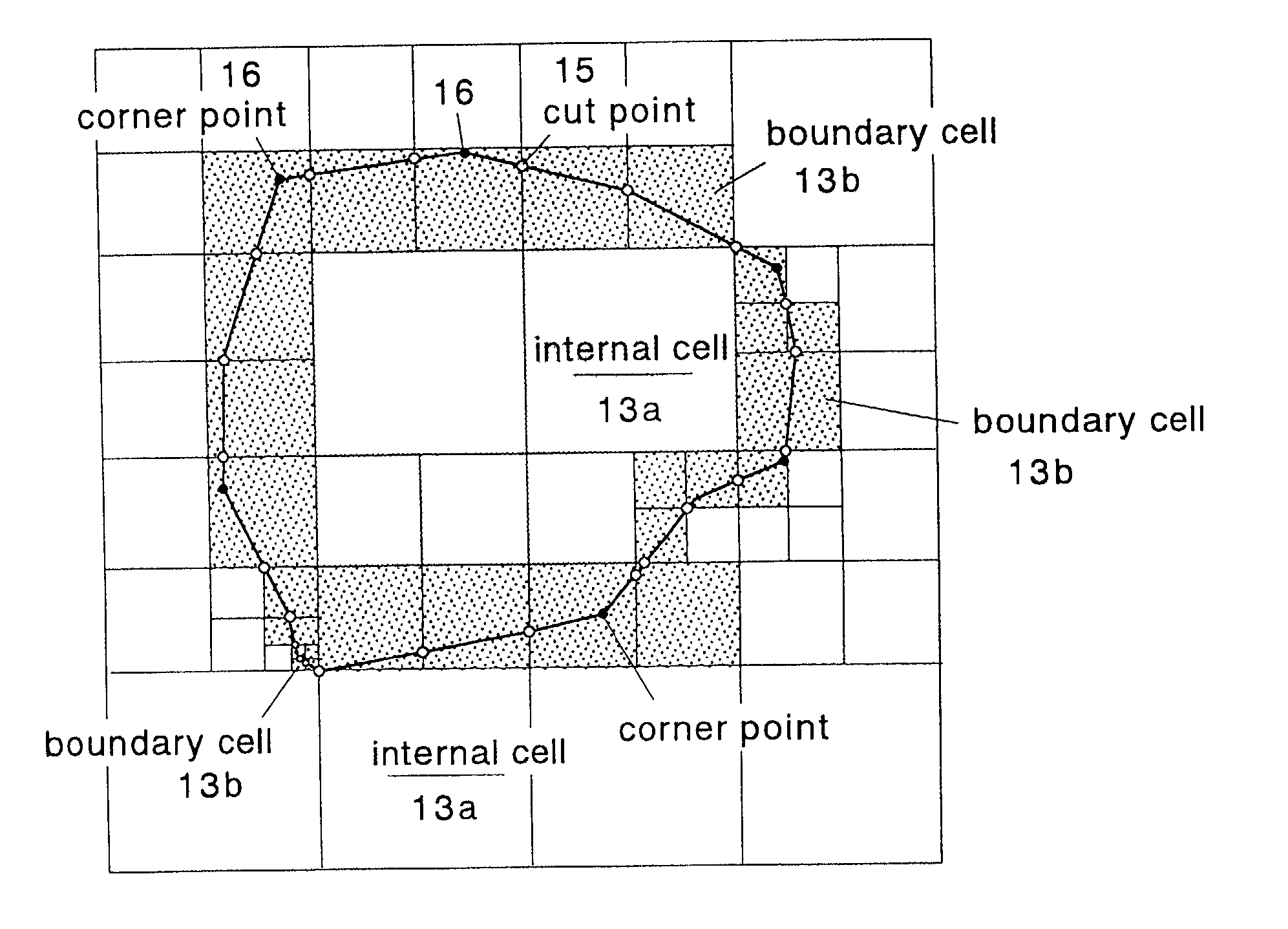
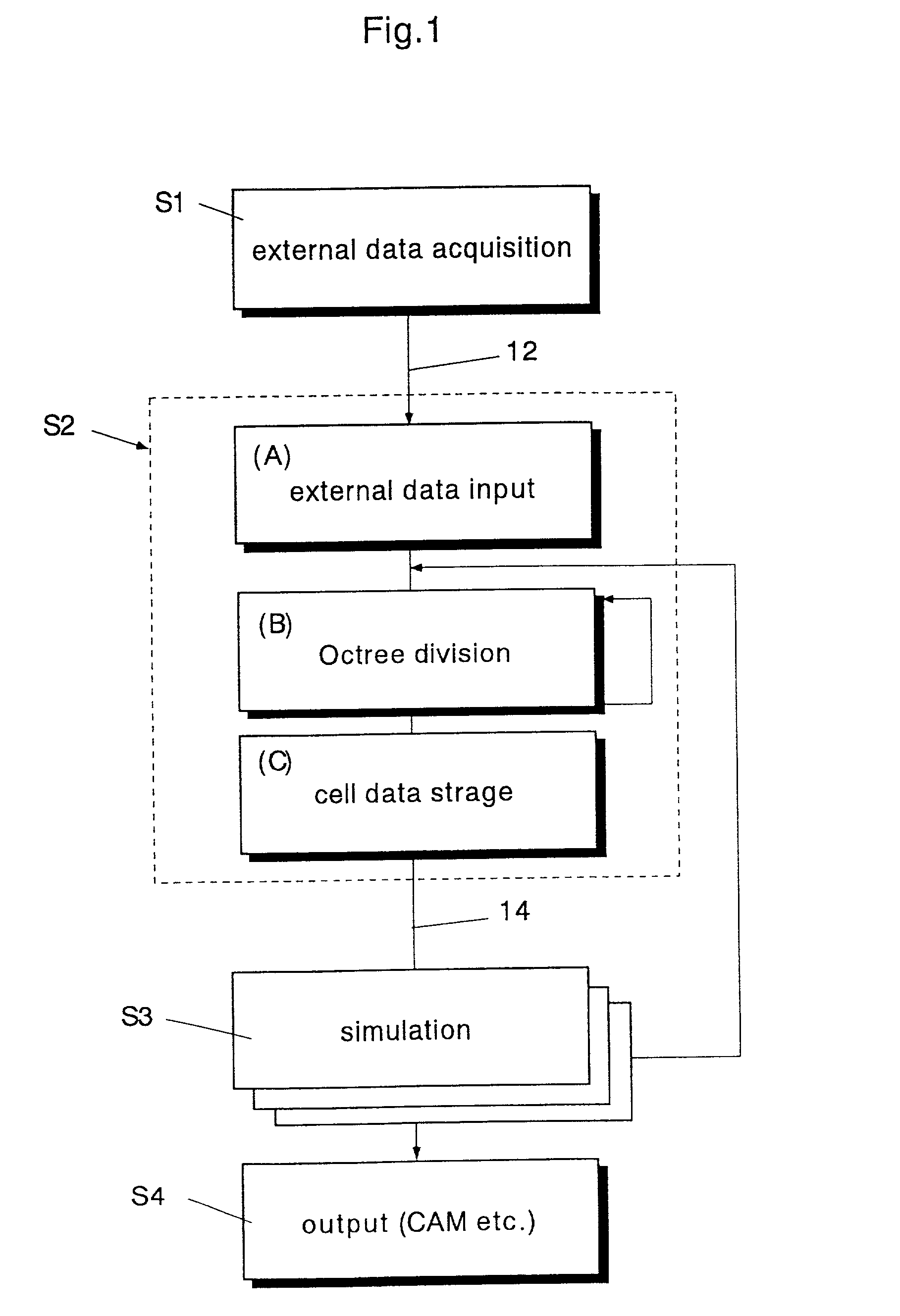
InactiveUS20060089803A1High expressionEnsure correct executionTesting/calibration apparatusVolume/mass flow measurementExternal dataDividing cell
A method including: a dividing step (A) of dividing external data into a plurality of cells (13) having boundaries orthogonal to each other, the external data including boundary data of an object which contacts incompressible viscous fluid; a cell classifying step (B) of classifying the divided cells into an internal cell (13a) positioned inside or outside the object and a boundary cell (13b) including the boundary data; a cut point determining step (C) of determining cut points in ridges of the boundary cell on the basis of the boundary data; a boundary face determining step (D) of determining a polygon connecting the cut points to be cell internal data for the boundary face; and a analyzing step (E) of applying a cut cell finite volume method combined with a VOF method to a boundary of a flow field to analyze the flow field.
Owner:RIKEN
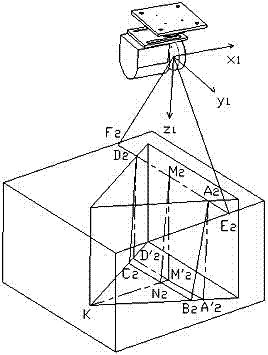
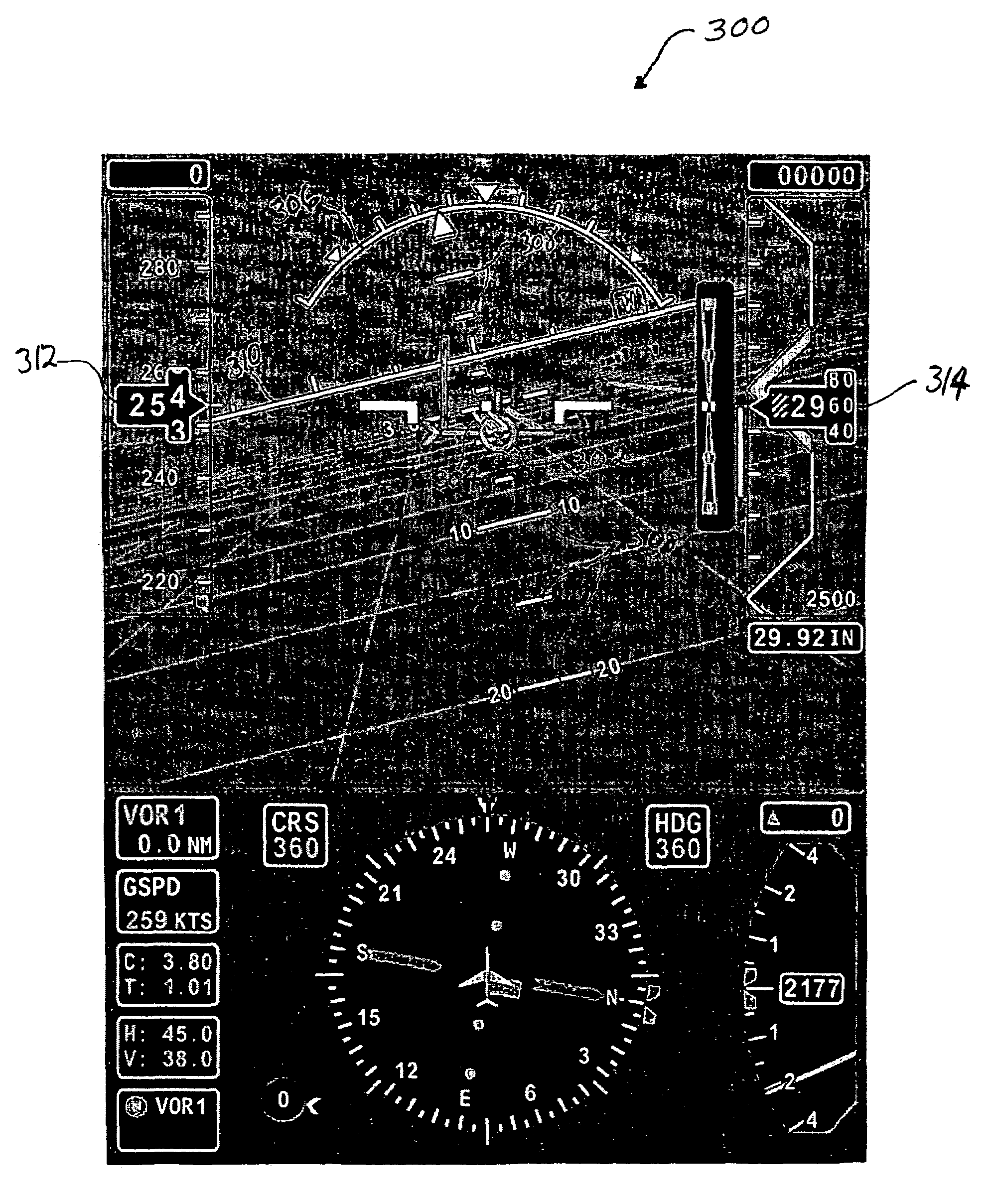
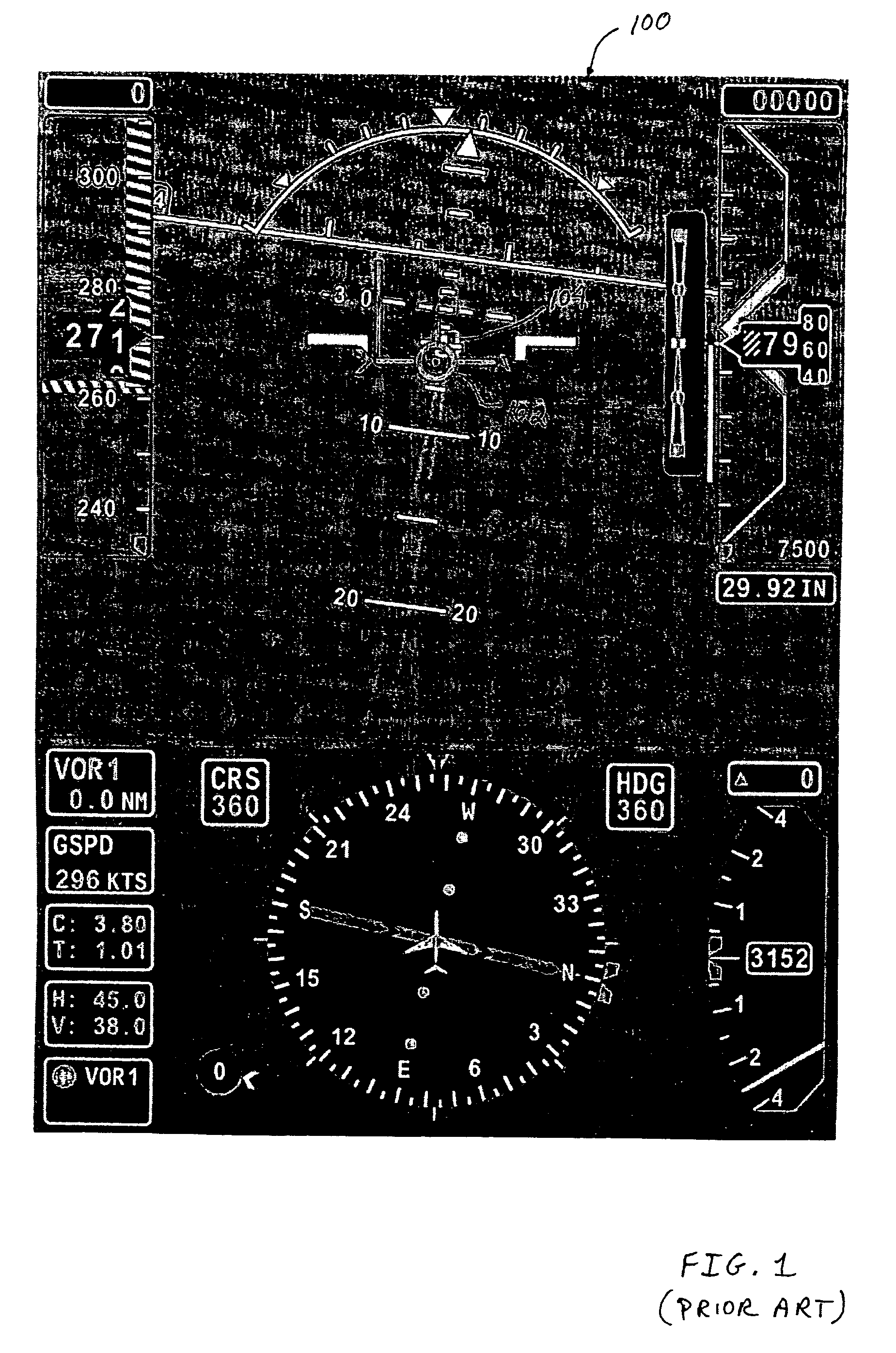
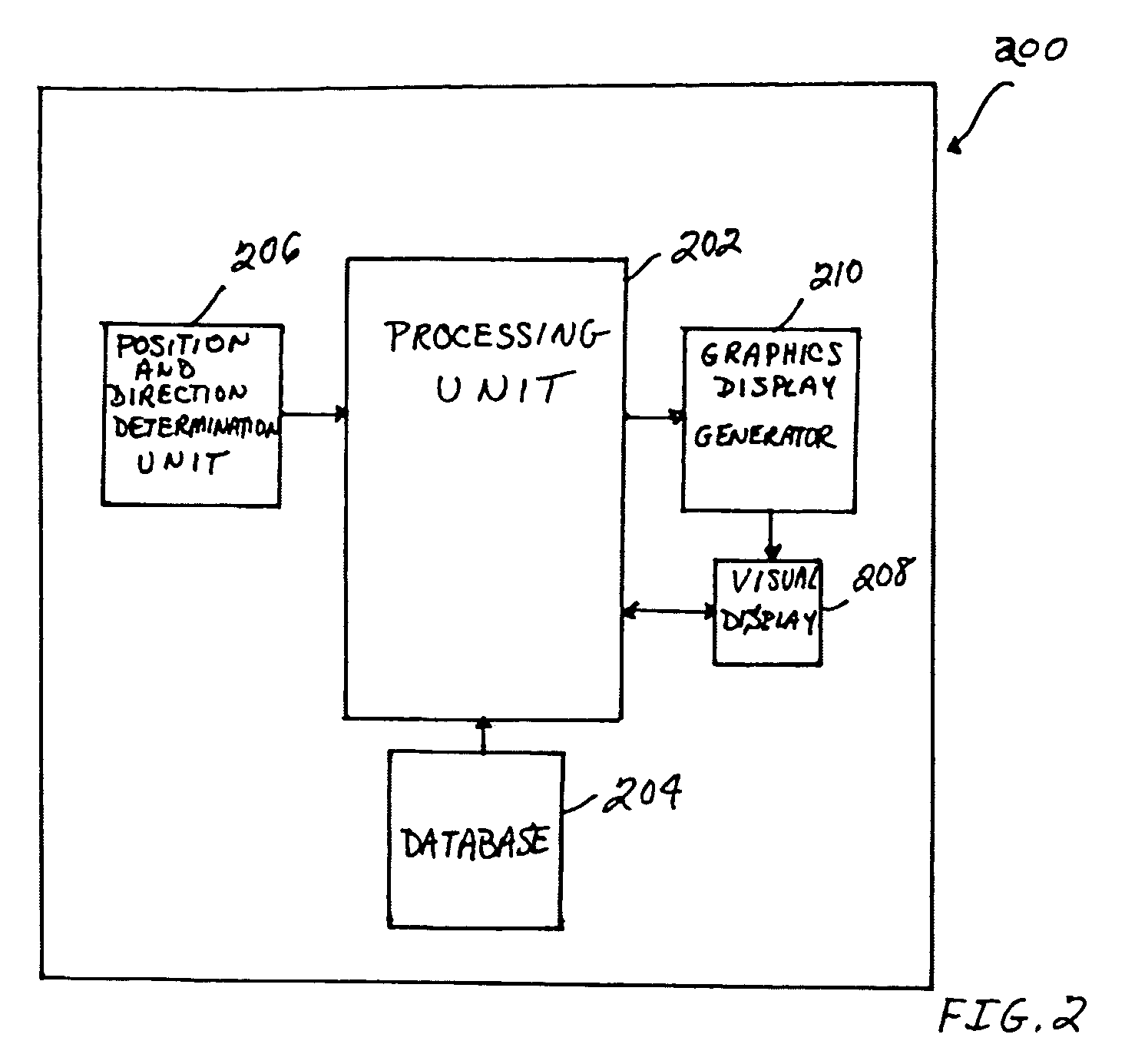
System and method for facilitating target aiming and aircraft control using aircraft displays
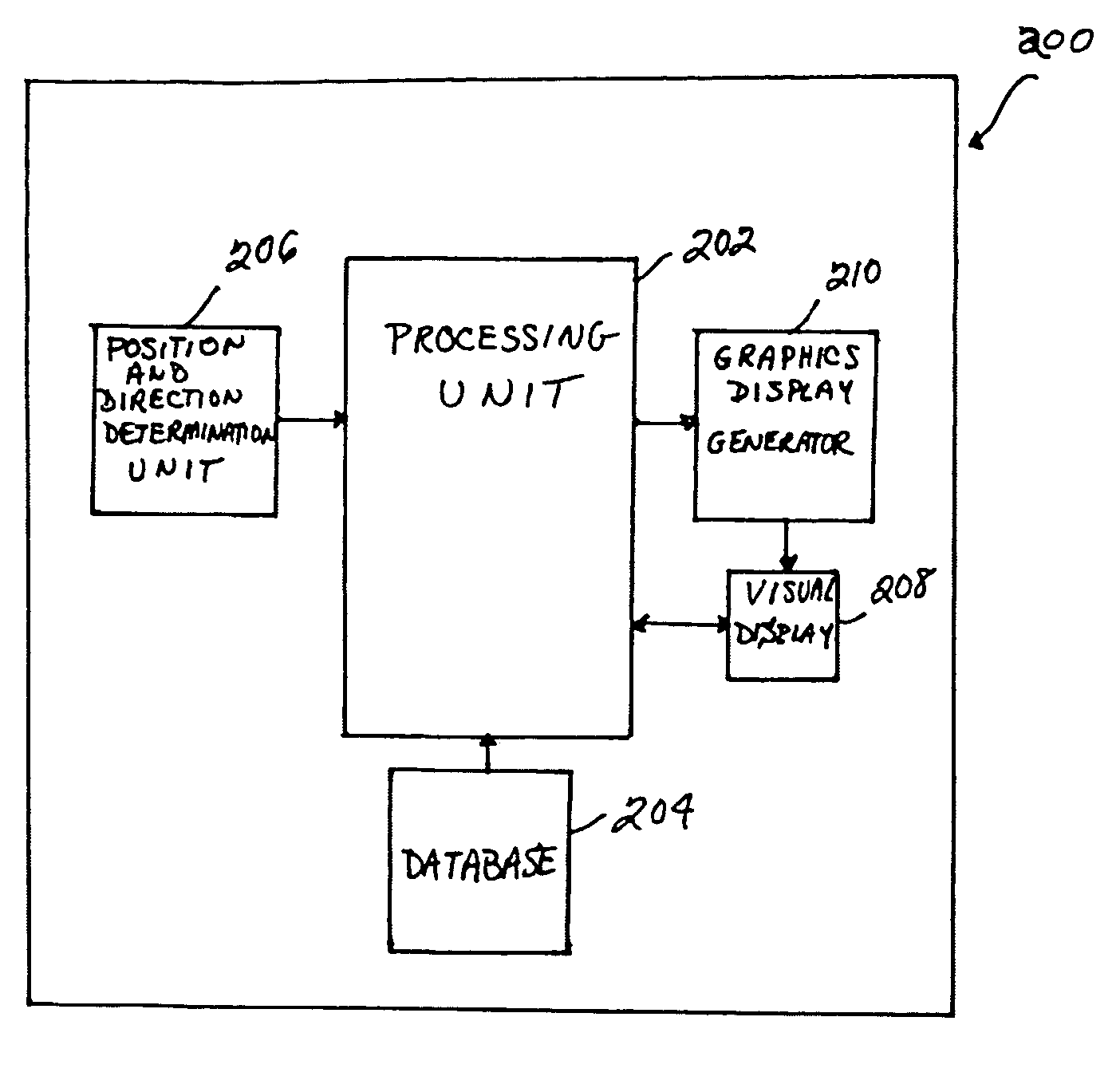
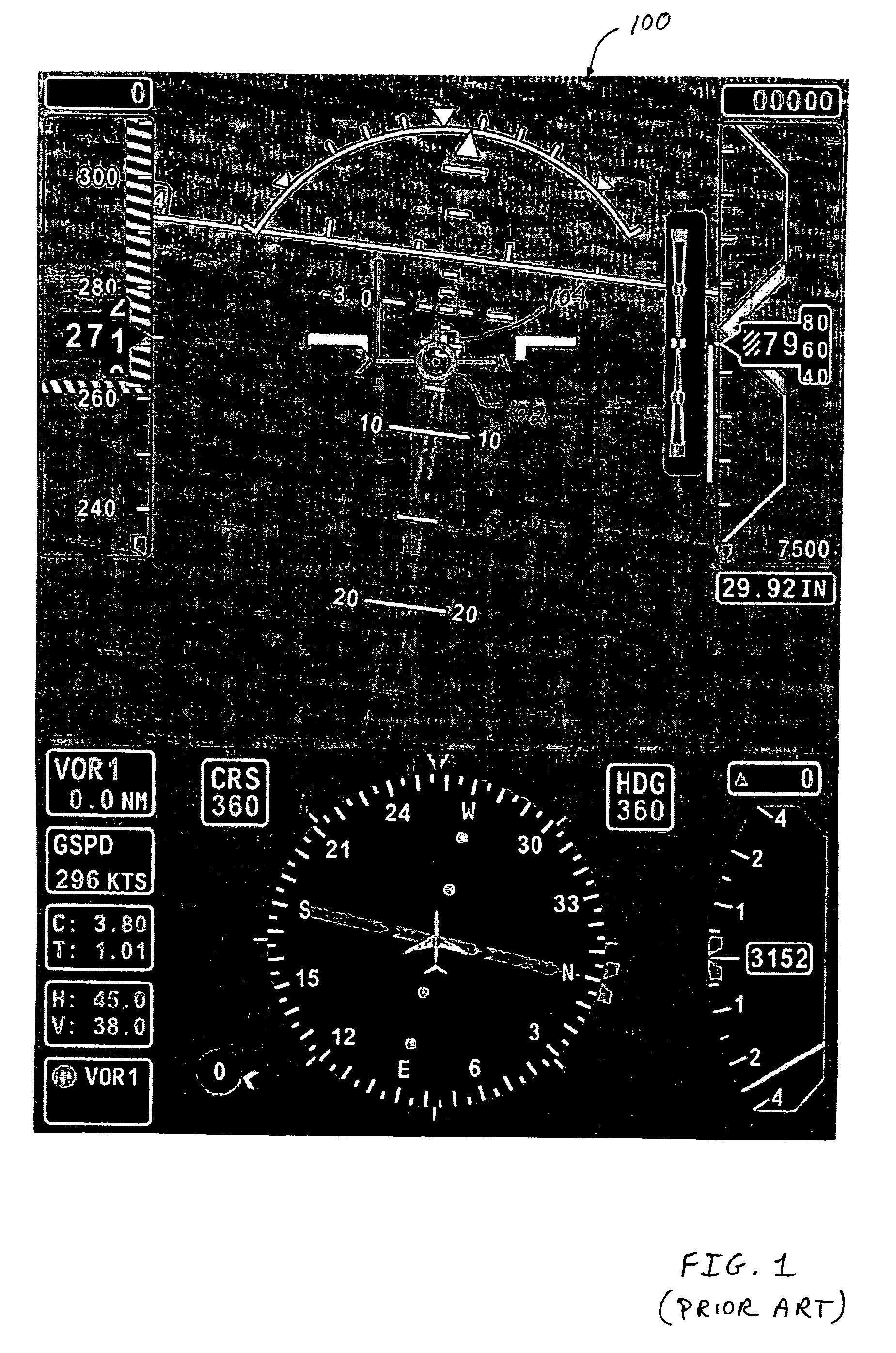
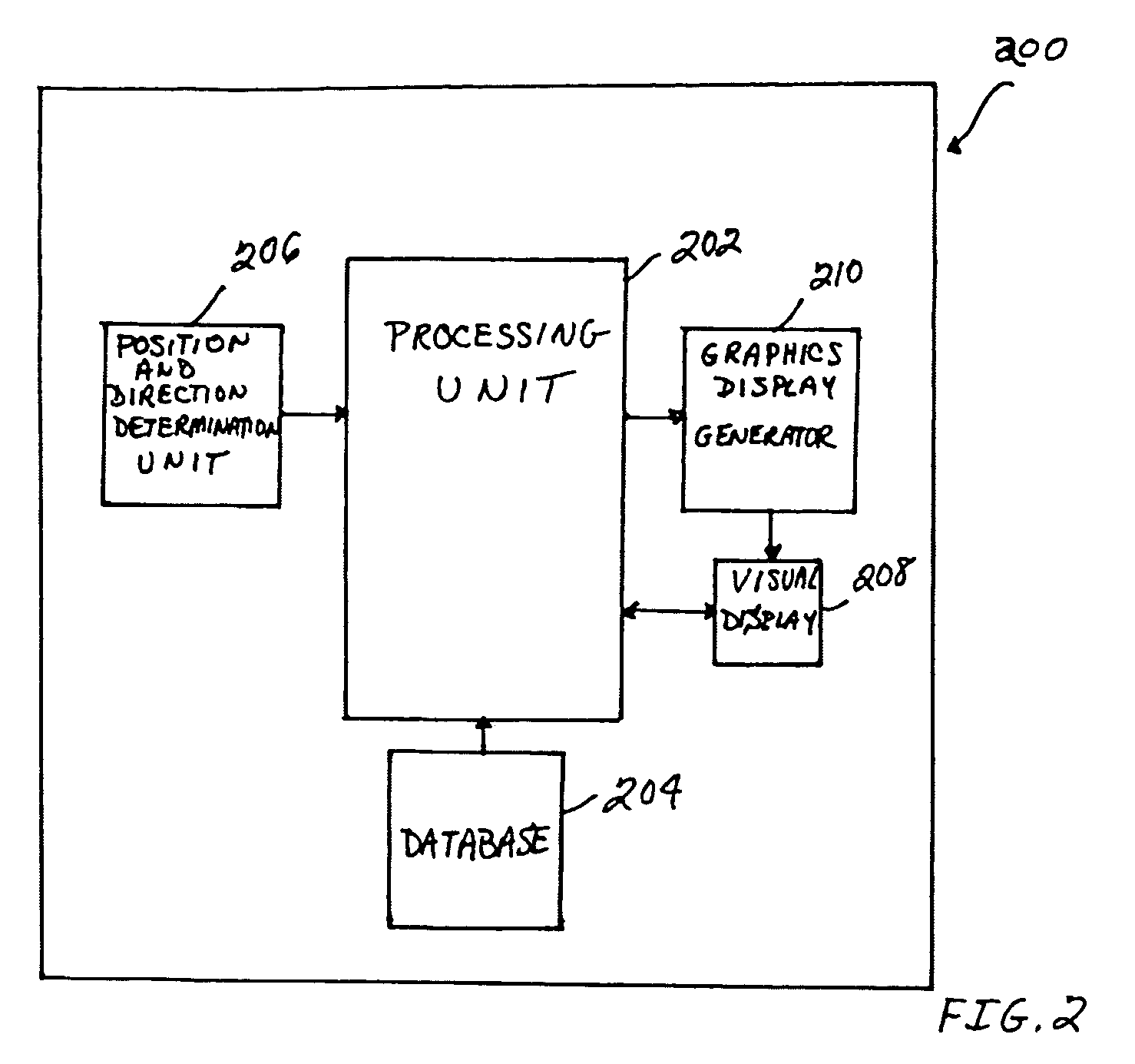
ActiveUS20060227012A1Facilitating target aimingFacilitating aircraft controlAnalogue computers for trafficNavigation instrumentsControl signalDisplay device
An improved system and method are disclosed for facilitating target aiming and aircraft control by flight crews using electronic displays. For example, an aircraft display system is disclosed that includes a database for storing target location and boundary data, a processing unit, a position and direction determination unit for use in determining the position of an aiming symbol on a display, a graphics display generator, and a visual display. The processing unit determines whether or not a selected target to be displayed is obscured or covered by the aiming symbol to be displayed. If any portion of the target is obscured or covered by the aiming symbol, then the processing unit directs the graphics display generator to generate graphic control signals for the visual display, which increase the transparency of the portions of the aiming symbol that obscure or cover the target. Notably, the transparency of any symbol (or portion of a symbol) can be increased if that symbol obscures or covers a target being displayed or viewed. Thus, the visibility of targets viewed using onboard visual displays is significantly enhanced, whereby the targets are obscured by the symbols used to aim and control the aircraft. Advantageously, target aiming and aircraft control are facilitated, which reduces pilot workload and navigation errors, and thus results in increased aircraft safety.
Owner:HONEYWELL INT INC
Method and device for numerical analysis of flow field of incompressible viscous fluid, directly using V-CAD data
InactiveUS7430500B2High expressionEnsure correct executionTesting/calibration apparatusVolume/mass flow measurementExternal dataDividing cell
A method including: a dividing step (A) of dividing external data into a plurality of cells (13) having boundaries orthogonal to each other, the external data including boundary data of an object which contacts incompressible viscous fluid; a cell classifying step (B) of classifying the divided cells into an internal cell (13a) positioned inside or outside the object and a boundary cell (13b) including the boundary data; a cut point determining step (C) of determining cut points in ridges of the boundary cell on the basis of the boundary data; a boundary face determining step (D) of determining a polygon connecting the cut points to be cell internal data for the boundary face; and a analyzing step (E) of applying a cut cell finite volume method combined with a VOF method to a boundary of a flow field to analyze the flow field.
Owner:RIKEN
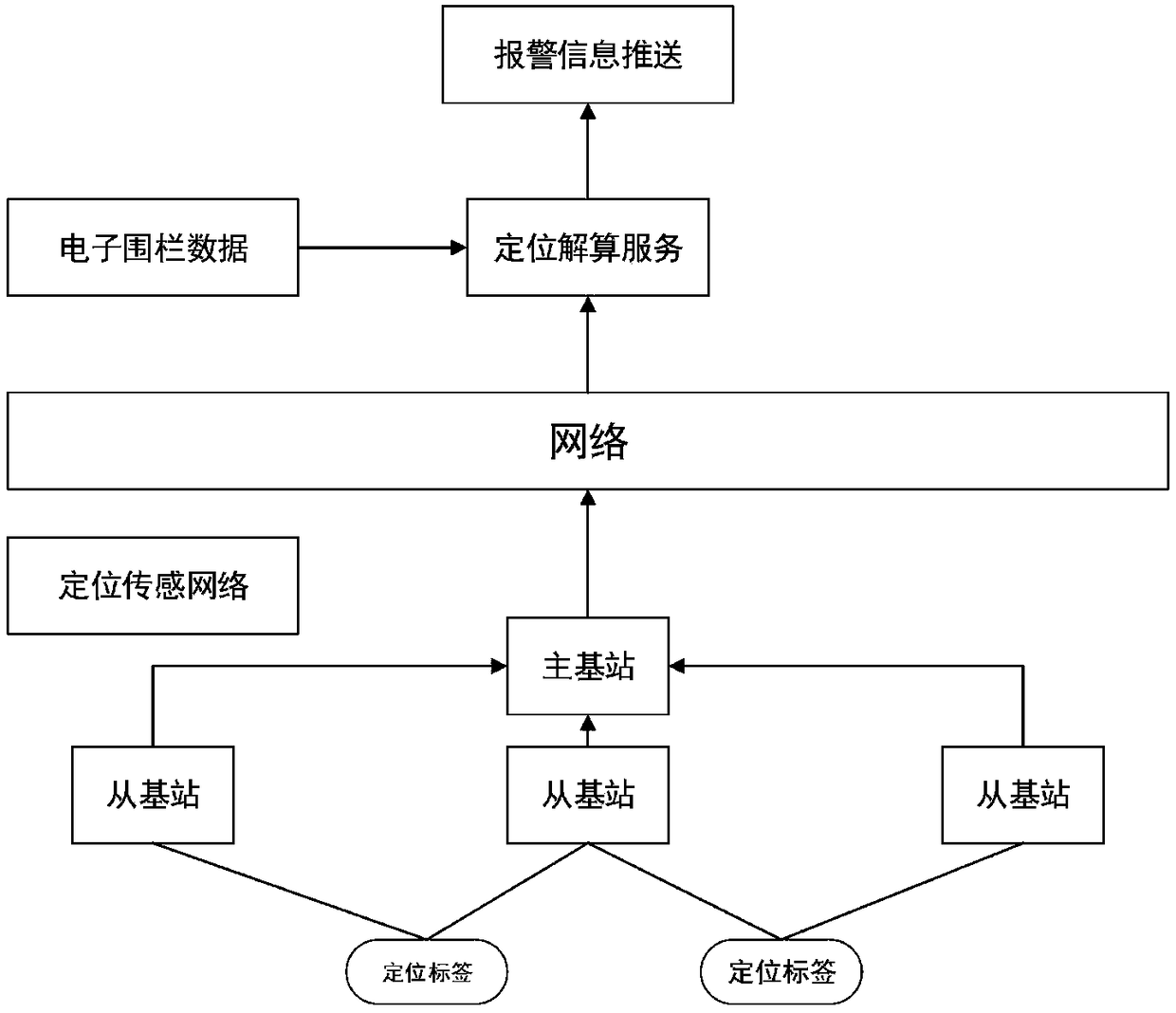
Substation illegal line-crossing prompting method based on ultra-wideband (UWB) positioning
InactiveCN109147272AEarly warning of crossing the lineReduce accident rateAlarmsUltra-widebandSpatial positioning
The invention relates to a substation illegal line-crossing prompting method based on ultra-wideband (UWB) positioning. The method comprises: a safe area of a device is drawn in a substation three-dimensional model and a visual three-dimensional electronic fence is formed; UWB positioning system deployment is carried out in the substation; according to a content of a work ticket, a corresponding working area is drawn; a staff member in the substation wears a spatial positioning device; a background carries out calculation to obtain the real-time position of the staff member; the background carries out comparison with safety fence boundary data to calculate whether someone approaches or crosses a safety distance and a corresponding working range; if any early-warning or line-crossing behavior is made, the information is sent to a smart watch worn by the staff member; the information is sent to an administrator background; and the background records data including the person doing alarming, lasting time, and a walking path of the alarm event. Therefore, the staff member and the administrator are prompted effectively; and the background records the line-crossing behavior so as to carry out follow-up work and analysis conveniently.
Owner:STATE GRID TIANJIN ELECTRIC POWER +1
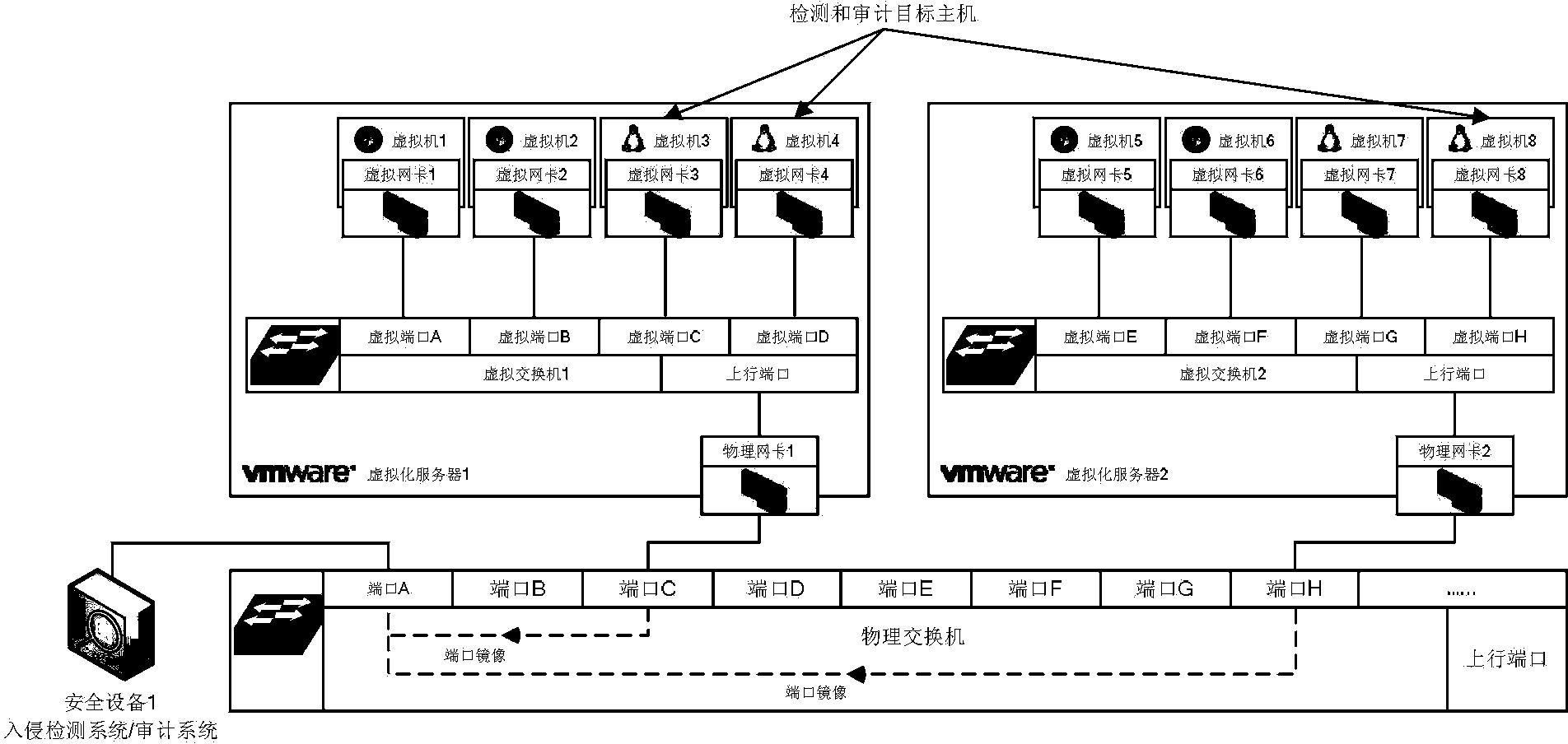
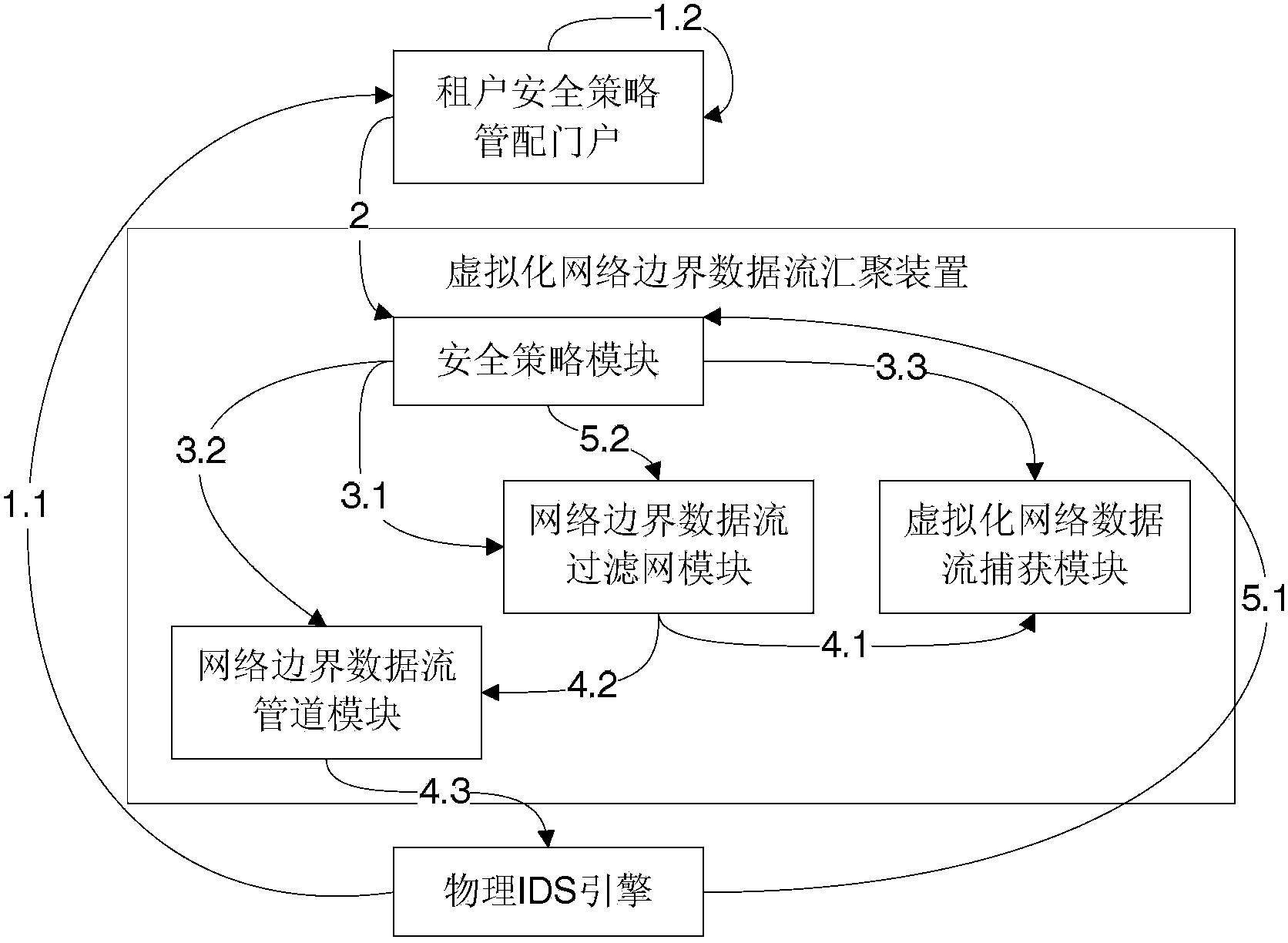
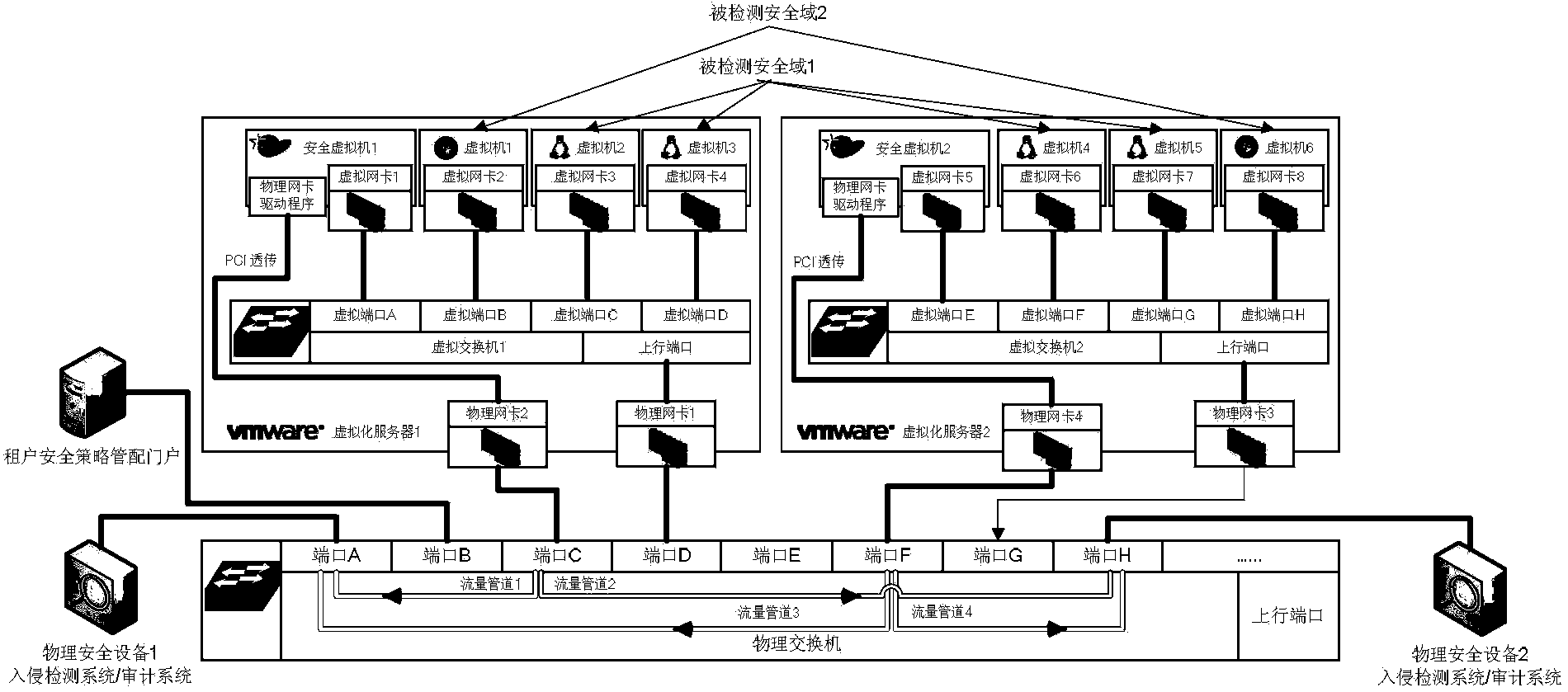
Virtualization network boundary data flow gathering method and apparatus
ActiveCN103354530AImprove detection efficiencyIncrease flexibilityNetworks interconnectionVirtualizationData stream
The invention discloses a virtualization network boundary data flow gathering method and apparatus and relates to the technical field of information safety. The apparatus disclosed by the invention comprises: a safety strategy module for maintaining and managing network boundary safety strategies of different tenants, a virtualization network data flow capturing module for monitoring a network data flow on a virtual switch and capturing the data packets of network interfaces specified by the safety strategies, and a network boundary data flow filter screen module for establishing, according to the network boundary safety strategies of the different tenants, filter screens based on network data flow filtering for the tenants respectively, filtering the captured network data packets through the filter screens of the corresponding tenants, encapsulating the network data flows which are obtained after filtering and belong to the safety domain boundaries of the tenants, and sending corresponding network safety products to the tenants. The invention also discloses the virtualization network boundary data flow gathering method. The technical scheme of the application effectively solves problems of gathering virtualization network safety domain boundary network data flows in a multi-tenant environment.
Owner:BEIJING VENUS INFORMATION TECH +1
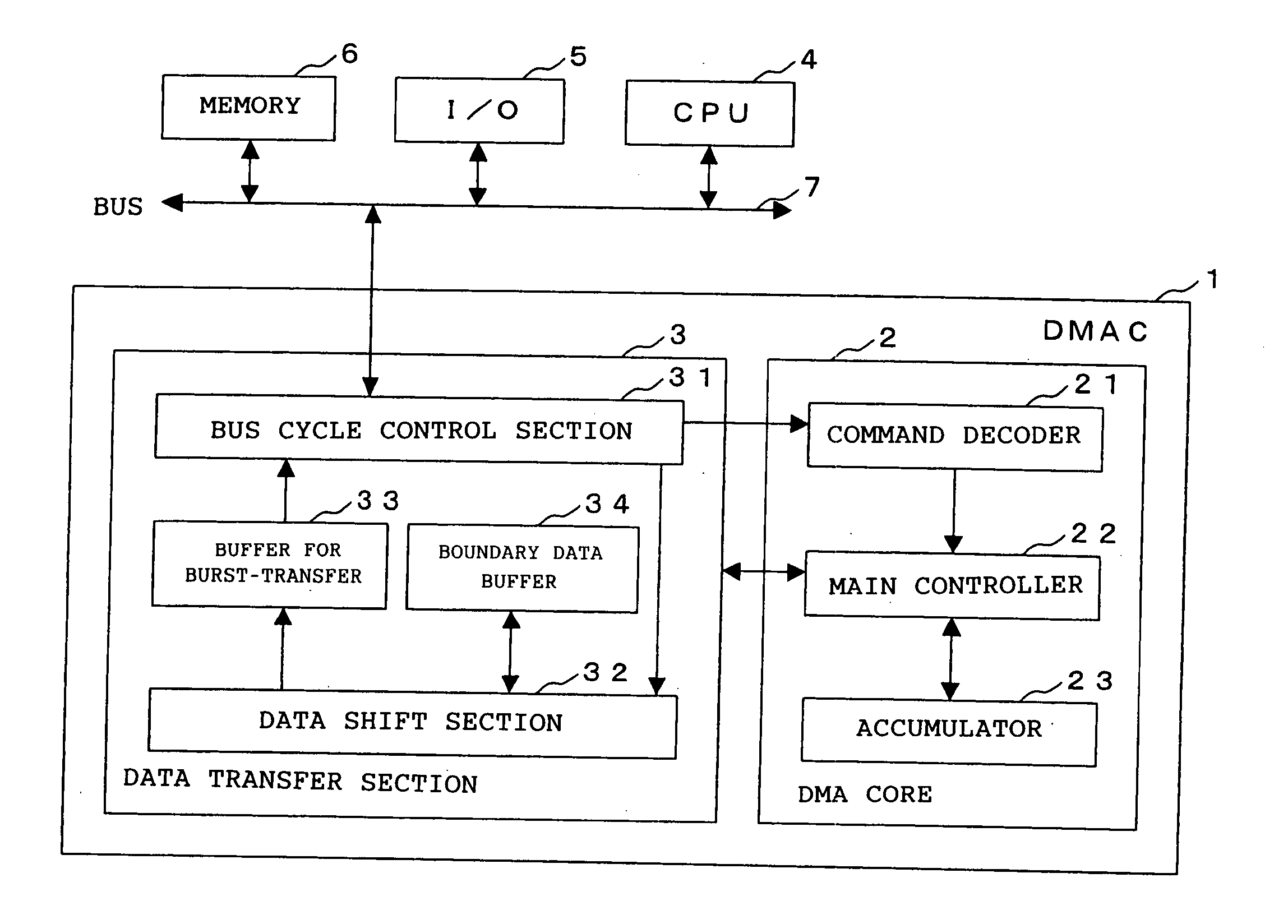
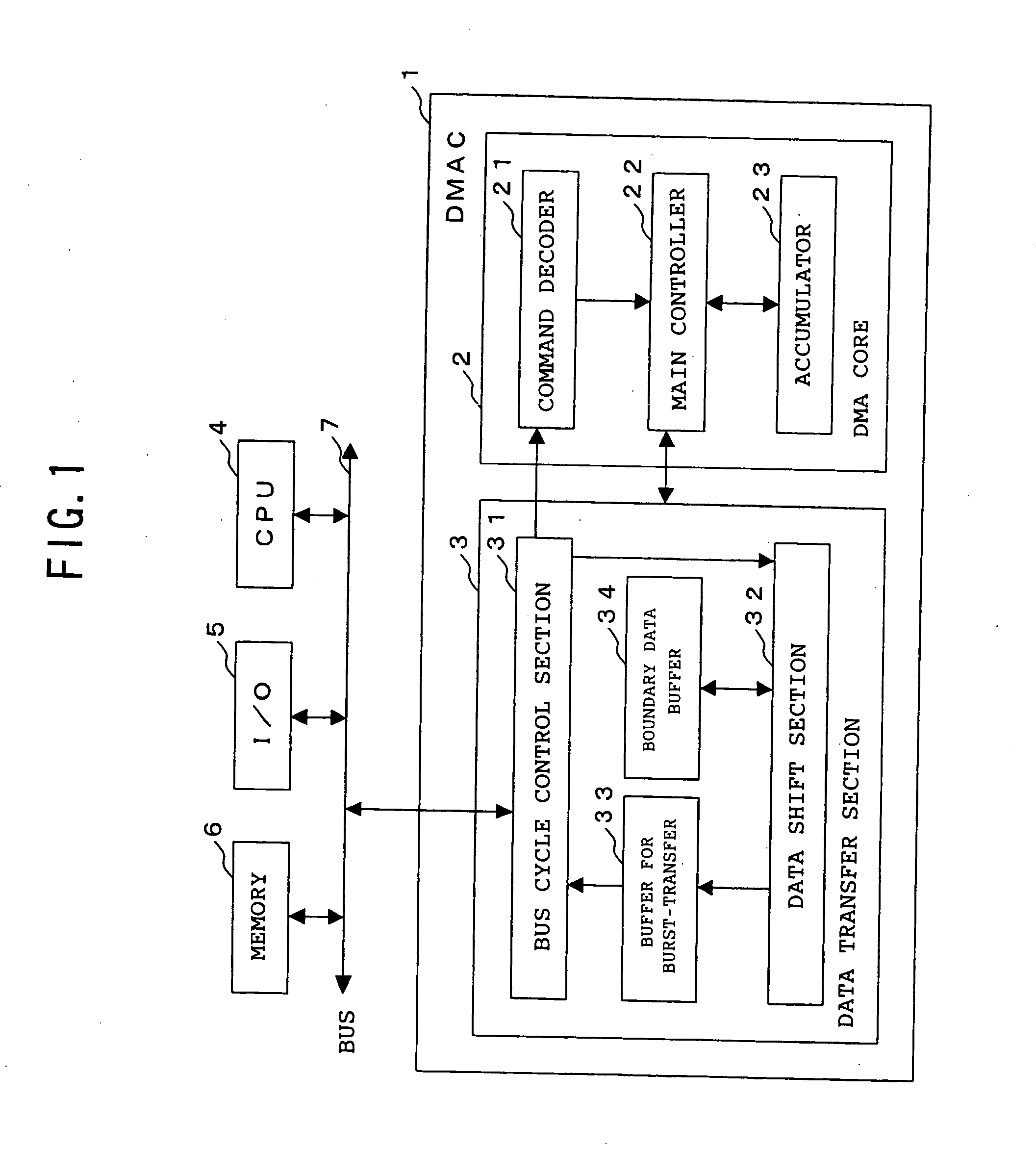
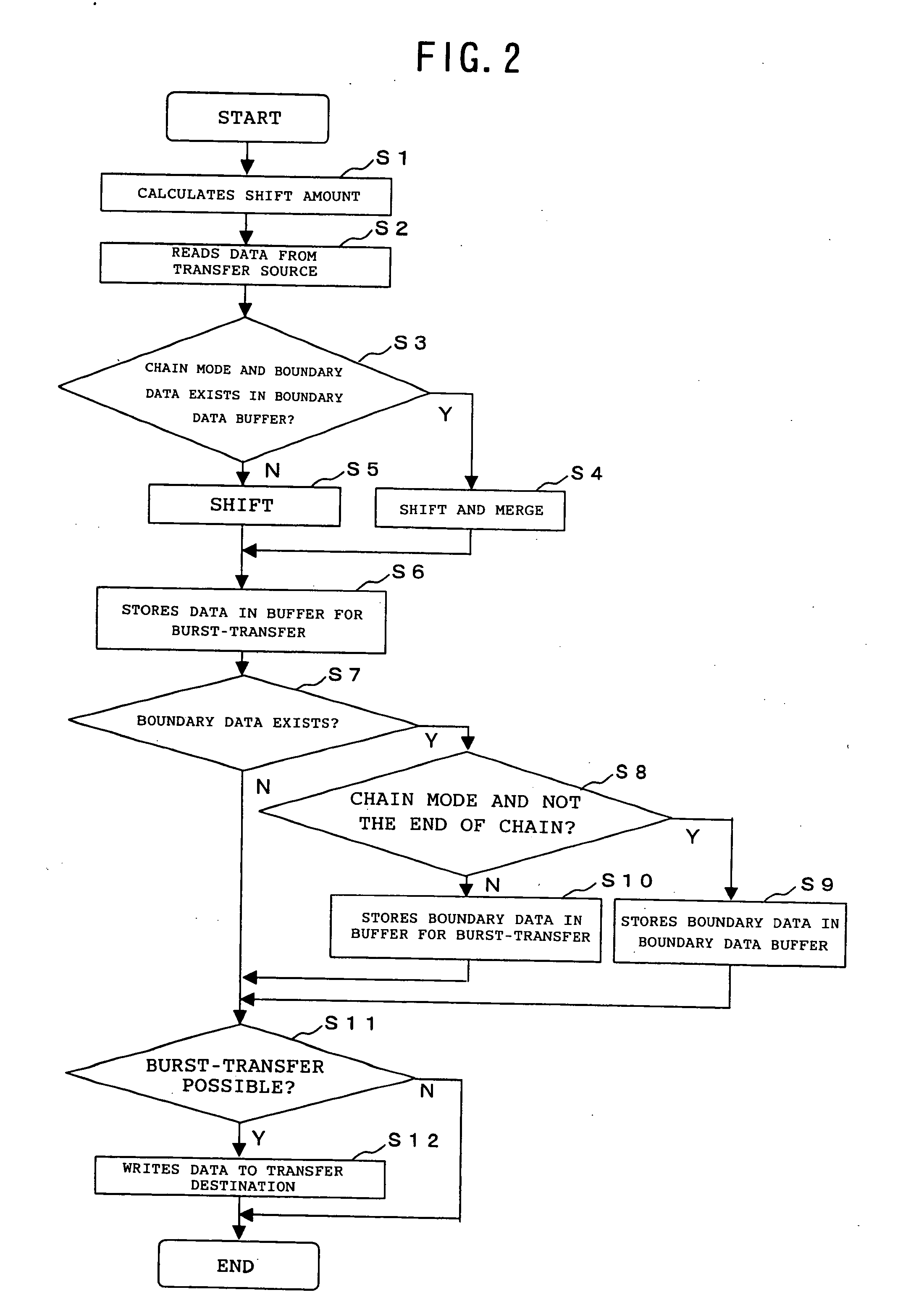
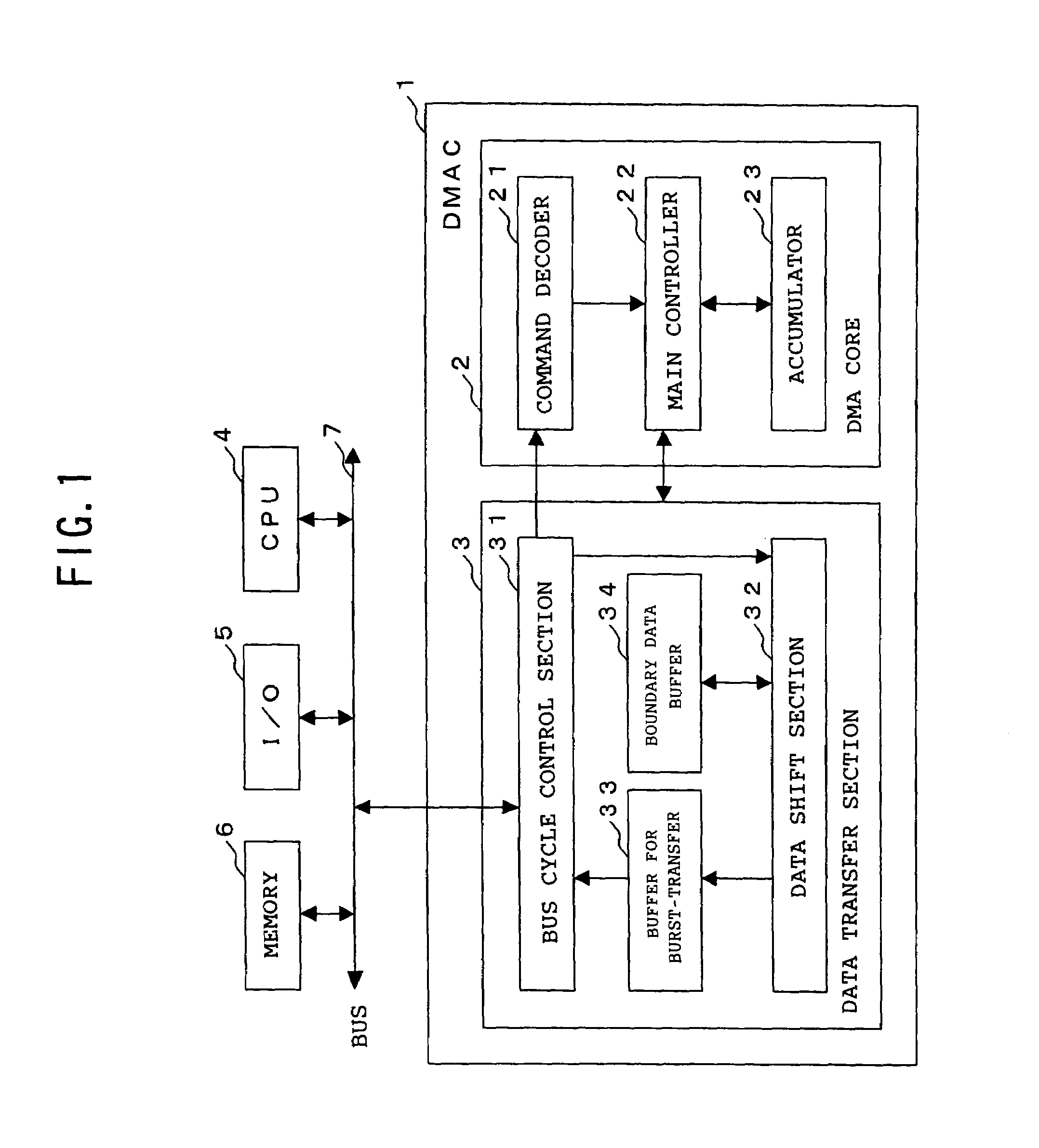
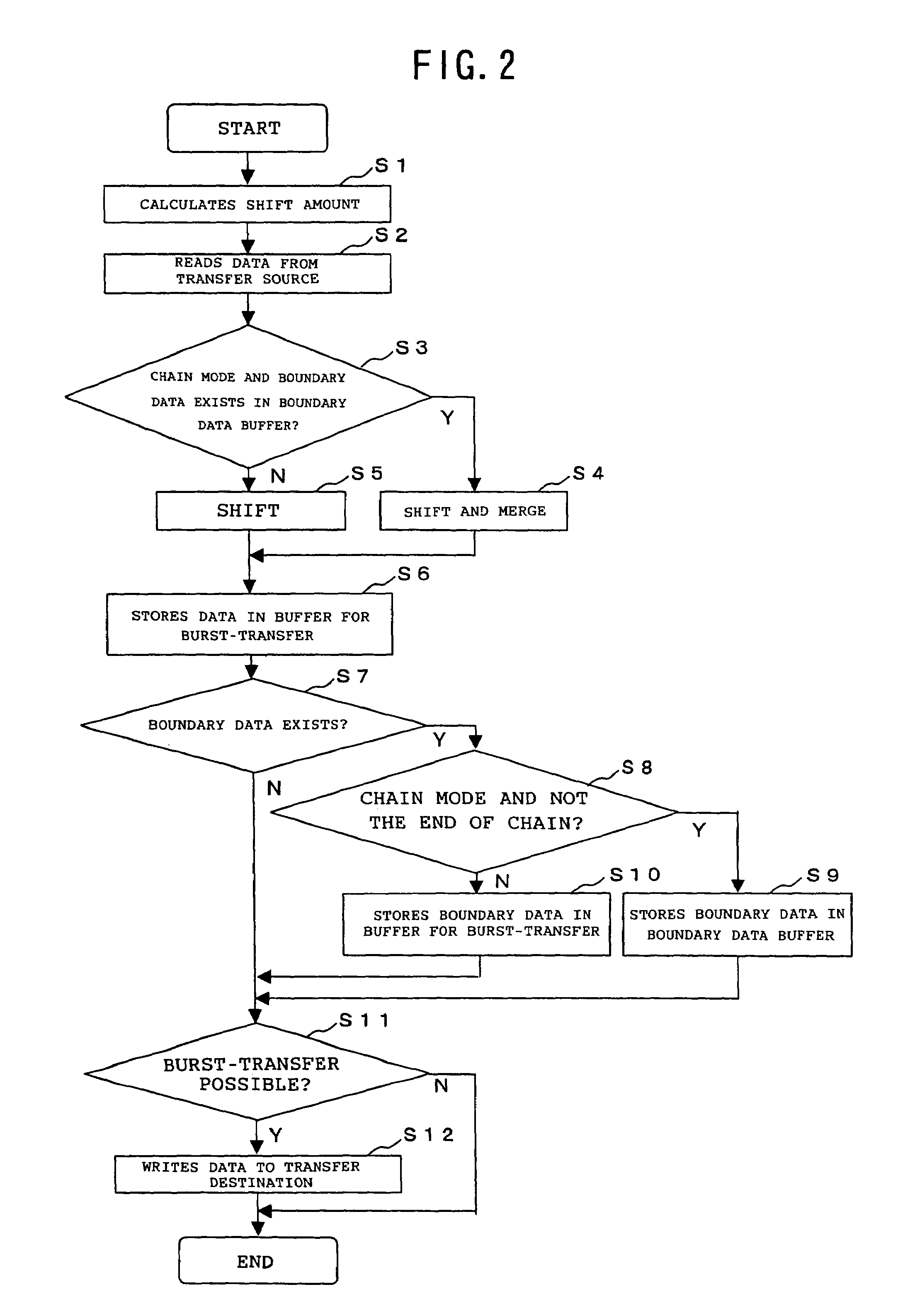
DMA controller, DMA control method and DMA control program
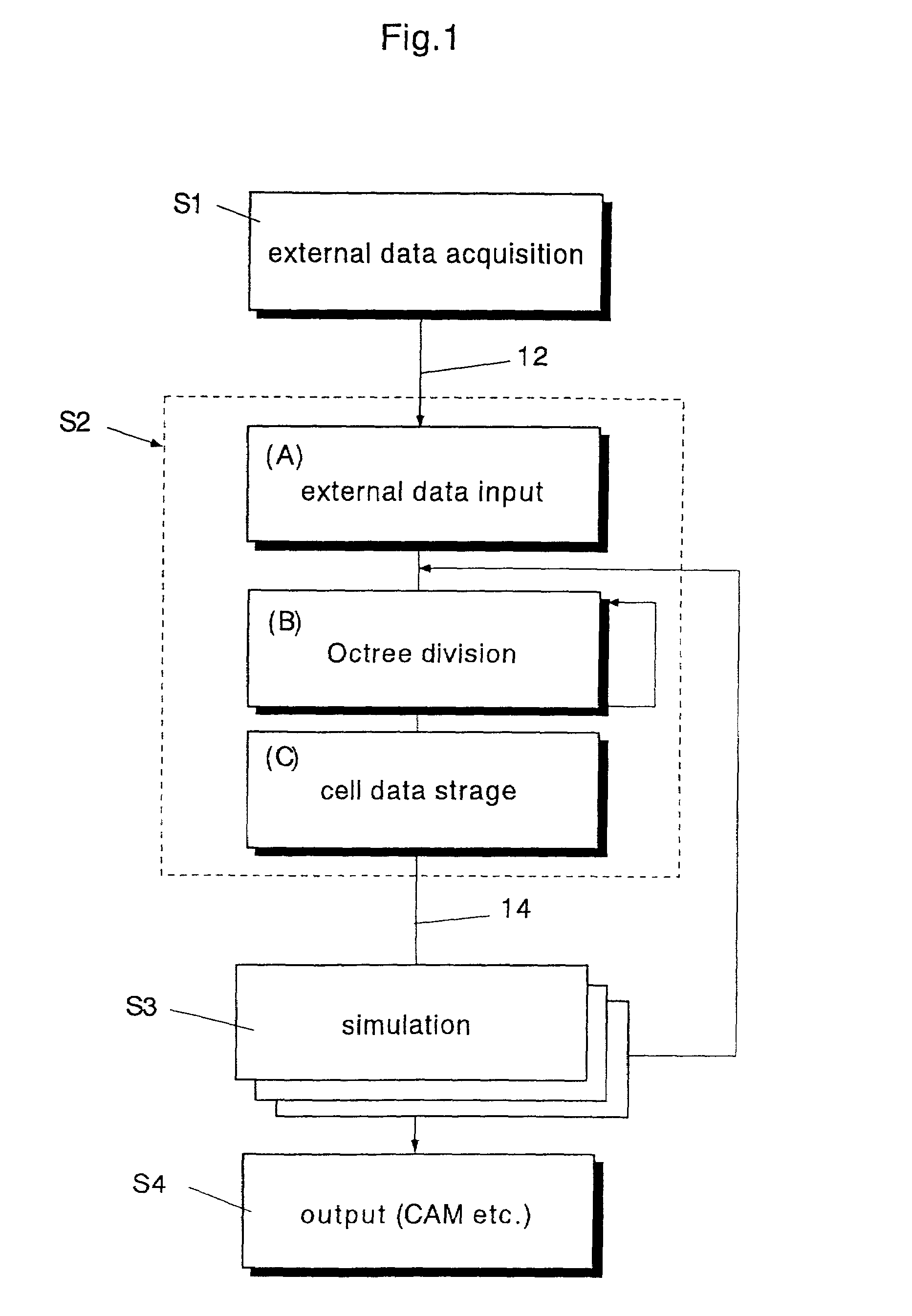
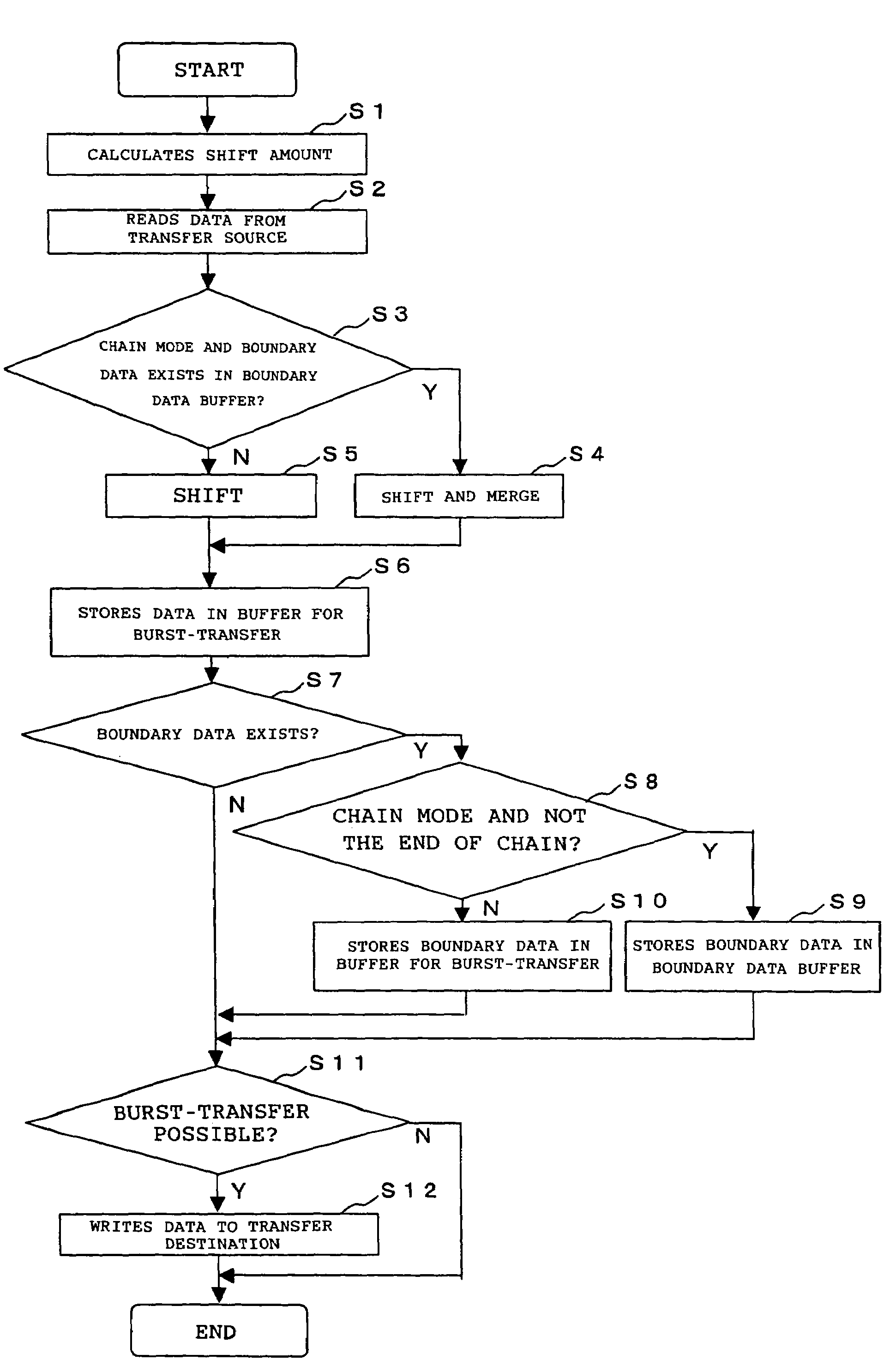
InactiveUS20050108446A1Increase profitImprove utilization efficiencyMemory adressing/allocation/relocationInput/output processes for data processingData segmentBurst transmission
The present invention is a DMA controller that accesses a transfer source and a transfer destination of a DMA transfer via a bus, that chains a plurality of data segments in the transfer source according to an instruction by an external initiator, and that performs burst-transfer to the transfer destination, and when a boundary data, that is a remaining data after dividing in the bus width units and data less than the bus width, is generated, the boundary data is stored in a boundary data buffer in the DMA controller, the data to be read from the transfer source by the next DMA command and the previously stored boundary data are merged, and the data is burst-transferred to the transfer destination.
Owner:FUJITSU LTD
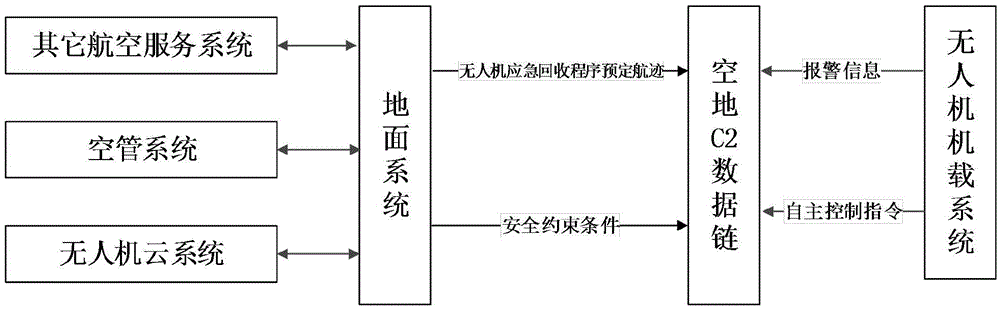
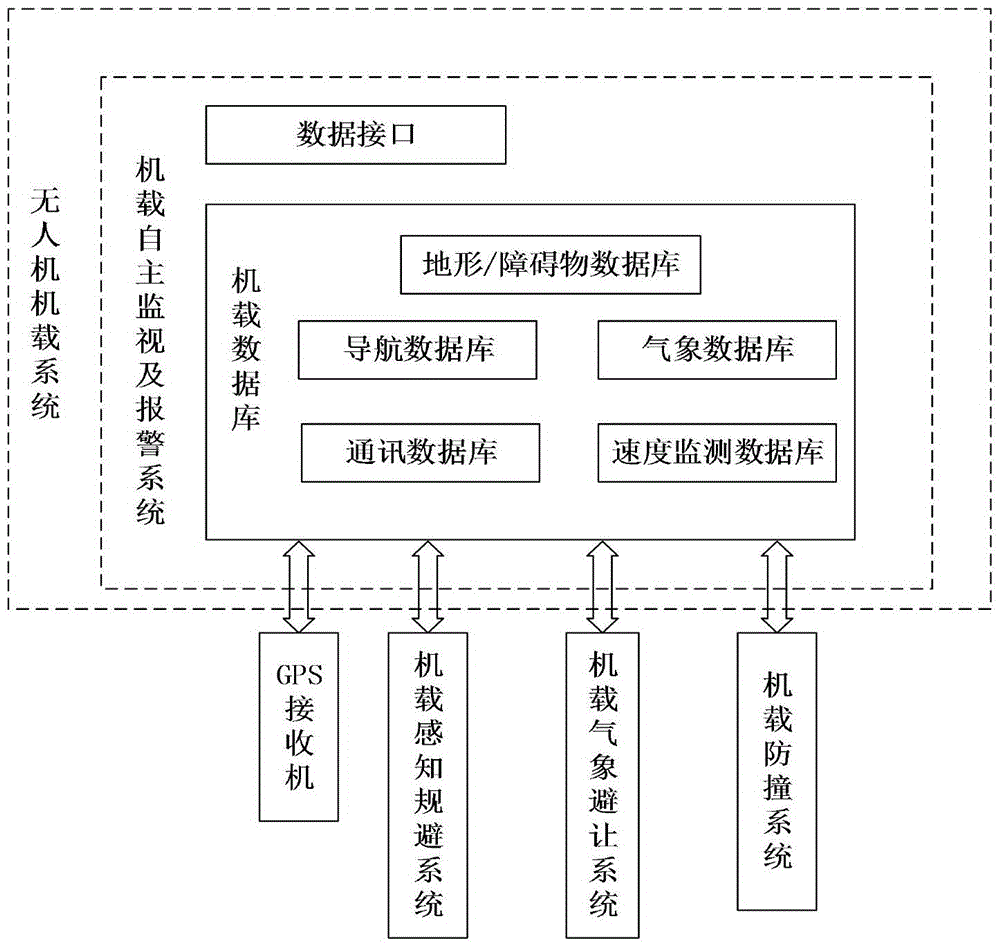
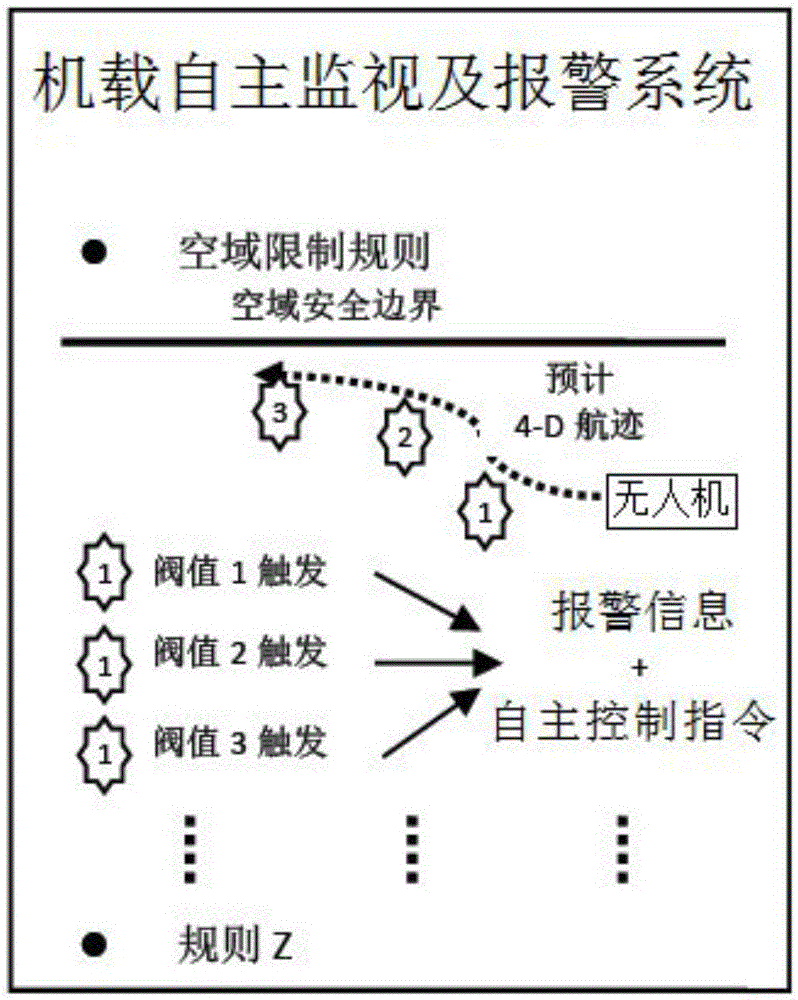
Airborne autonomous monitoring and alarming system and method for safe operation of unmanned aerial vehicle
ActiveCN105575188AEnsure operationAvoid instruction transfer delaysAircraft traffic controlReal-time computingBoundary data
The invention relates to an airborne autonomous monitoring and alarming system and method for safe operation of an unmanned aerial vehicle. The system comprises a ground system. The ground system is communicated with the unmanned aerial vehicle through a space-ground C2 data chain. The system is provided with an airborne database. The airborne database constructs a security boundary of the unmanned aerial vehicle. The system also comprises a data interface, wherein the data interface uploads updated real-time security constraint conditions and preset flight path of an emergency recovery program updated therewith through the space-ground C2 data chain. The unmanned aerial vehicle, through the security boundary data stored in the airborne database, triggers different levels of alarm information and an autonomous control instruction according to the ganger level, and sends the alarm information and the autonomous control instruction to the ground system and operation personnel through the space-ground C2 data chain in real time. The system constructs a multidimensional virtual fence according to the security constraint conditions and rules to carry out real-time monitoring on the flight state and give a corresponding alarm when the dangerous state is triggered, thereby ensuring the unmanned aerial vehicle flies within the security boundary.
Owner:丁元沅
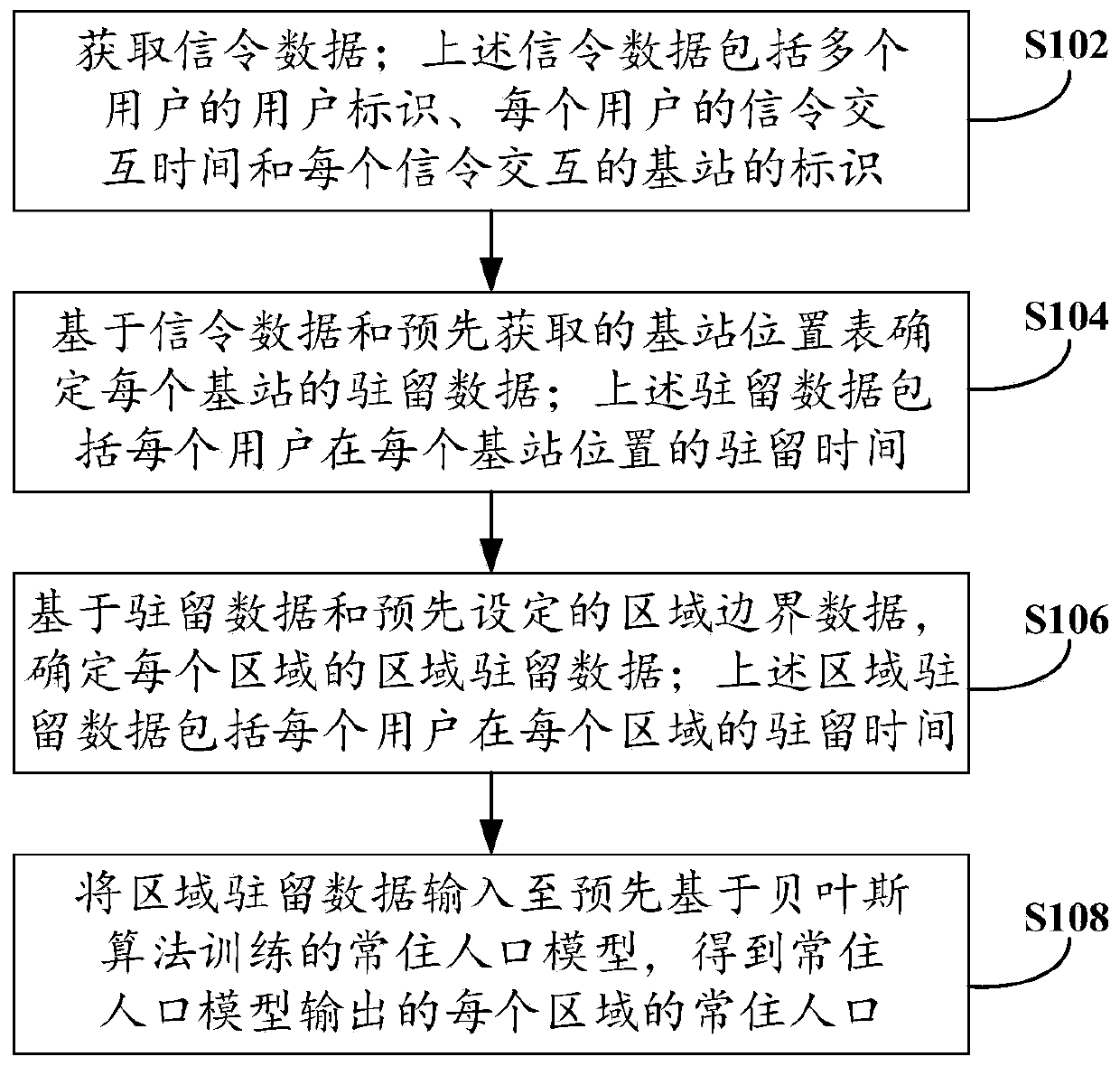
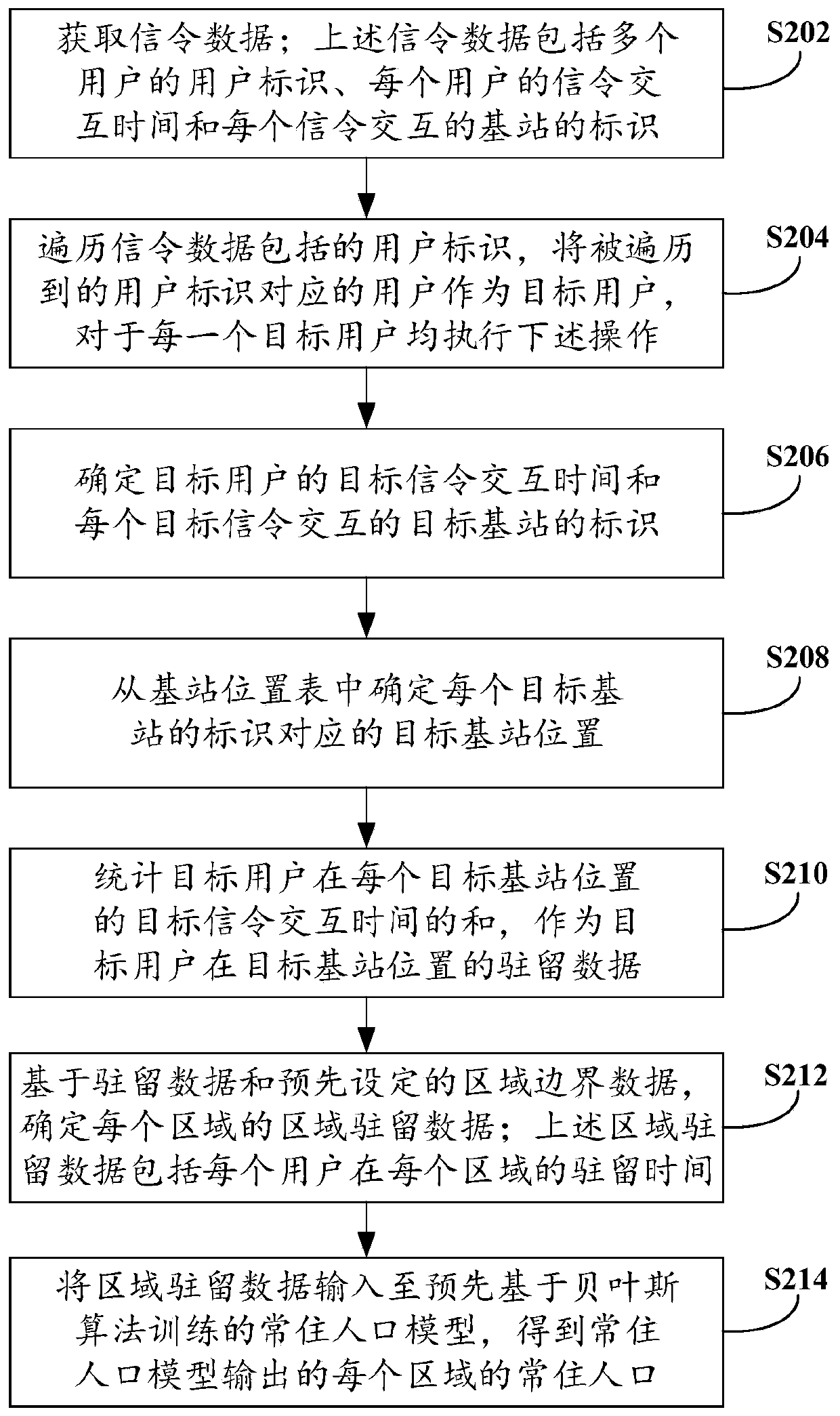
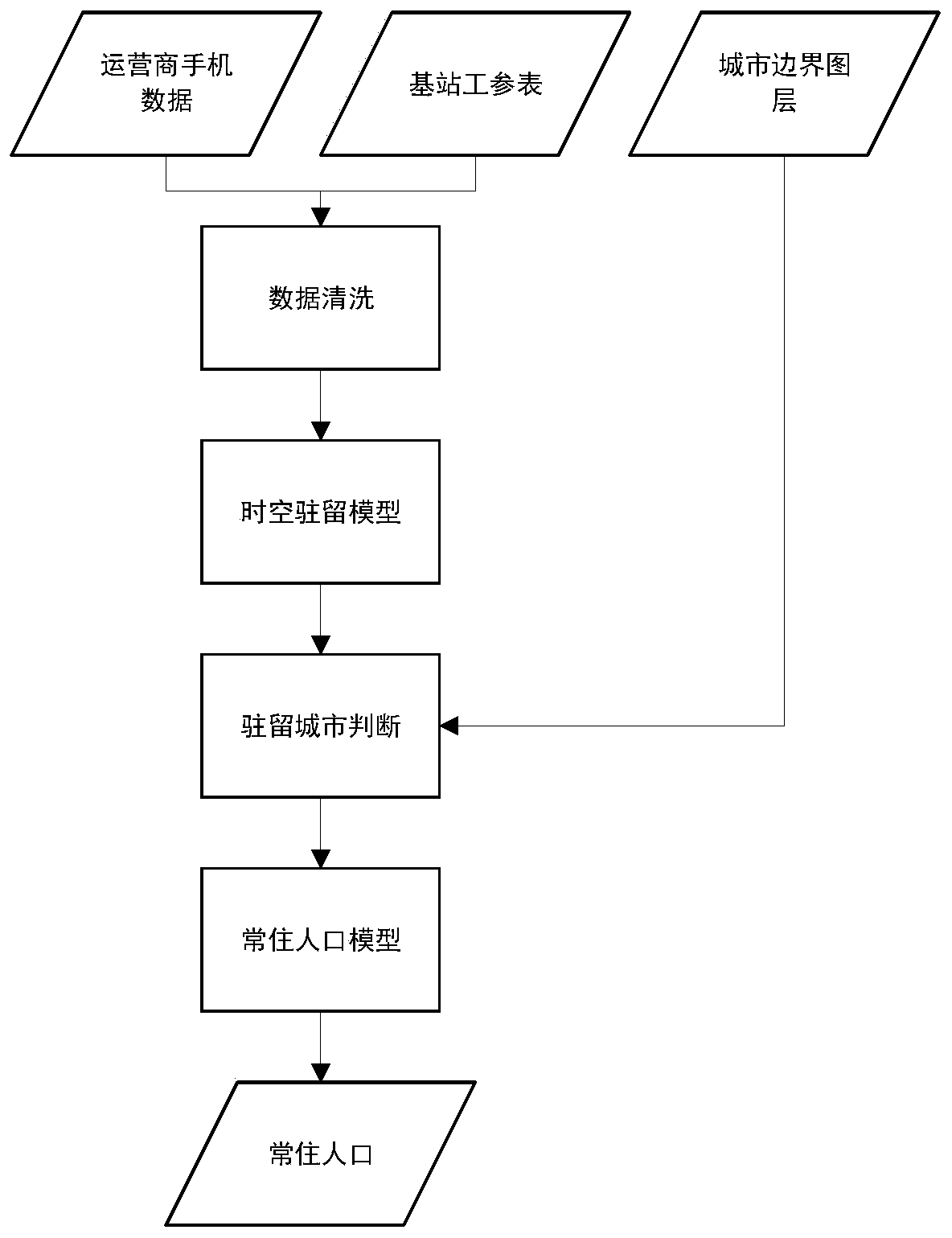
Method and device for determining permanent resident population and electronic equipment
ActiveCN110868689AAvoid time costReduce labor costsServices signallingLocation information based serviceData packUser identifier
The invention provides a permanent resident population determination method and device and electronic equipment. The method comprises the following steps: acquiring signaling data; wherein the signaling data comprises user identifiers of a plurality of users, signaling interaction time of each user and identifiers of base stations for signaling interaction; determining residence data of each basestation based on the signaling data and a pre-acquired base station position table; determining area residence data of each area based on the residence data and preset area boundary data; and inputting the regional resident data into a permanent resident population model trained in advance based on a Bayesian algorithm to obtain permanent resident population of each region output by the permanentresident population model. In the mode, only a small amount of signaling data is needed for reckoning permanent resident population, a large amount of manpower does not need to be consumed to use a large amount of time for investigation and statistics, time cost and labor cost can be reduced, the implementation period can be shortened, dynamic change characteristics can be obtained, and the methodcan be used for cities with large population cardinal numbers and high floating population proportions.
Owner:智慧足迹数据科技有限公司
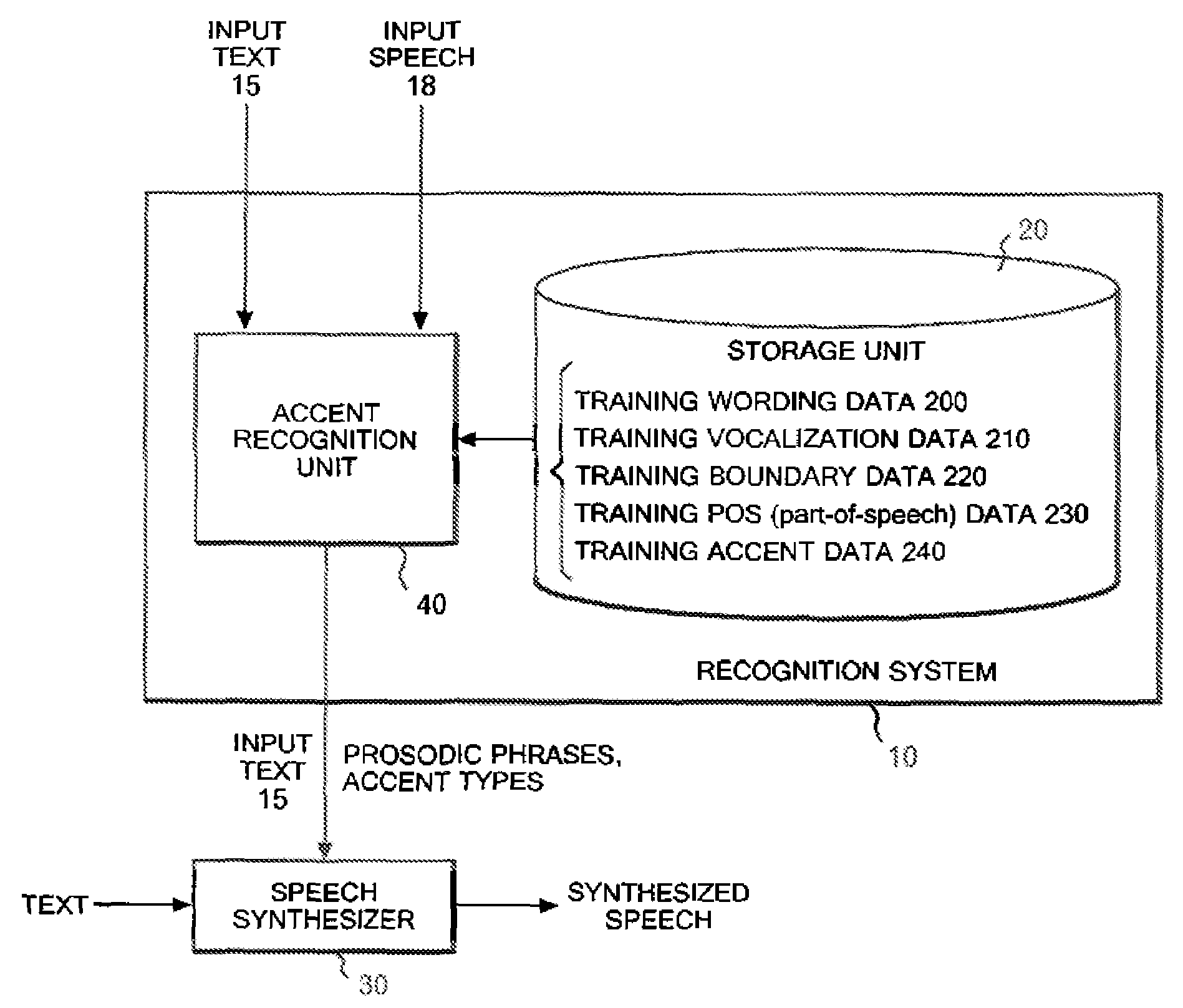
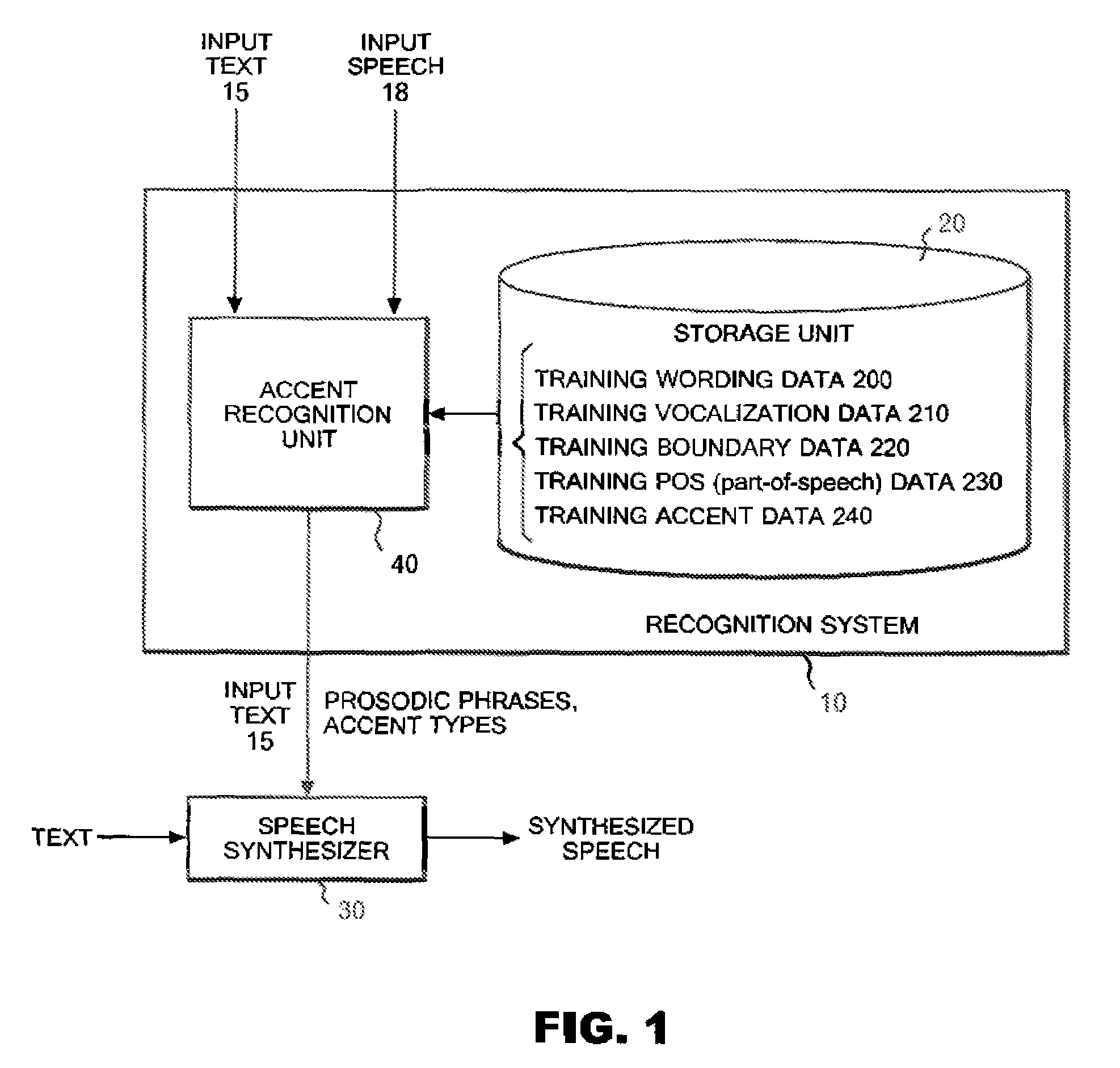
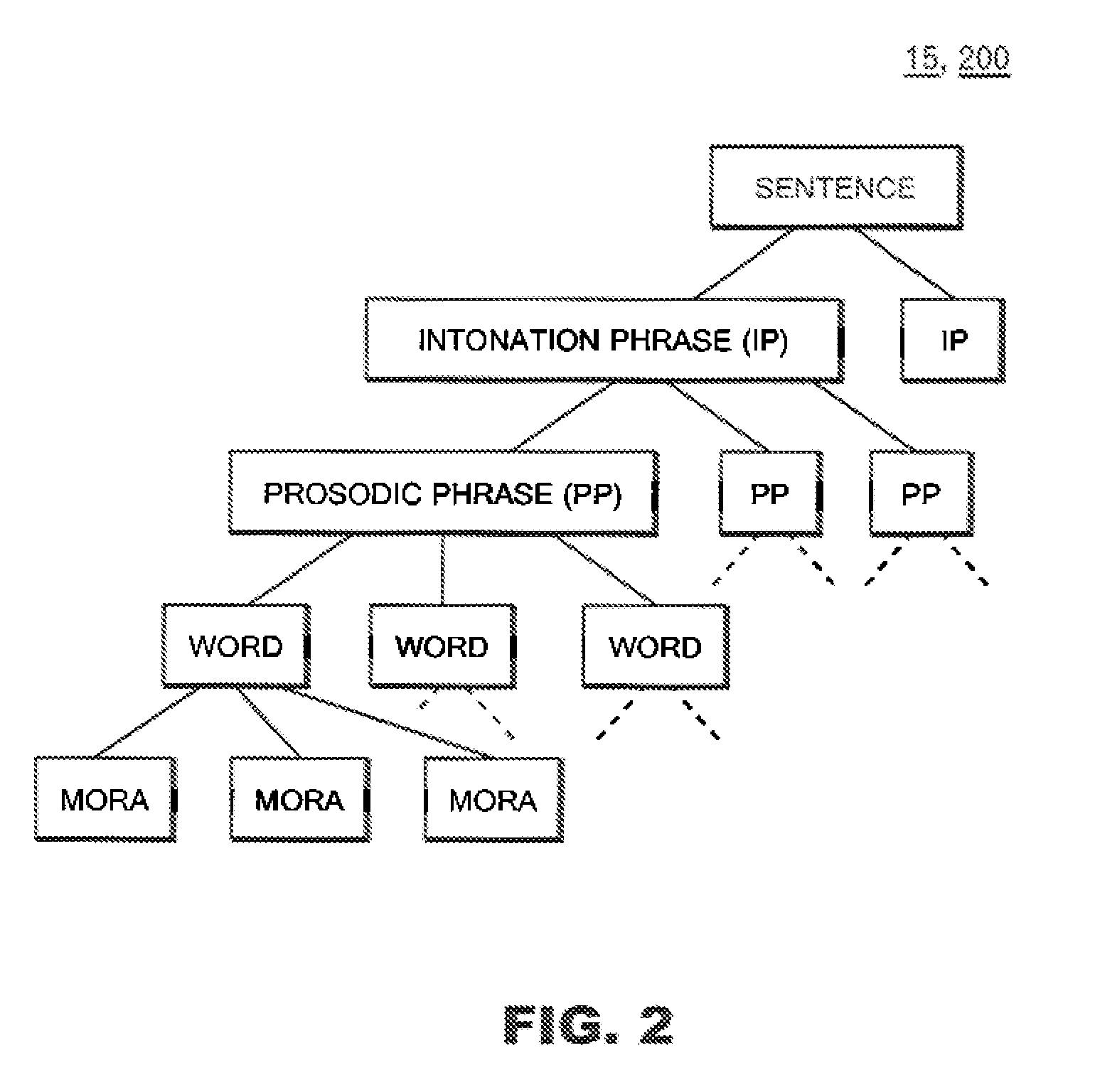
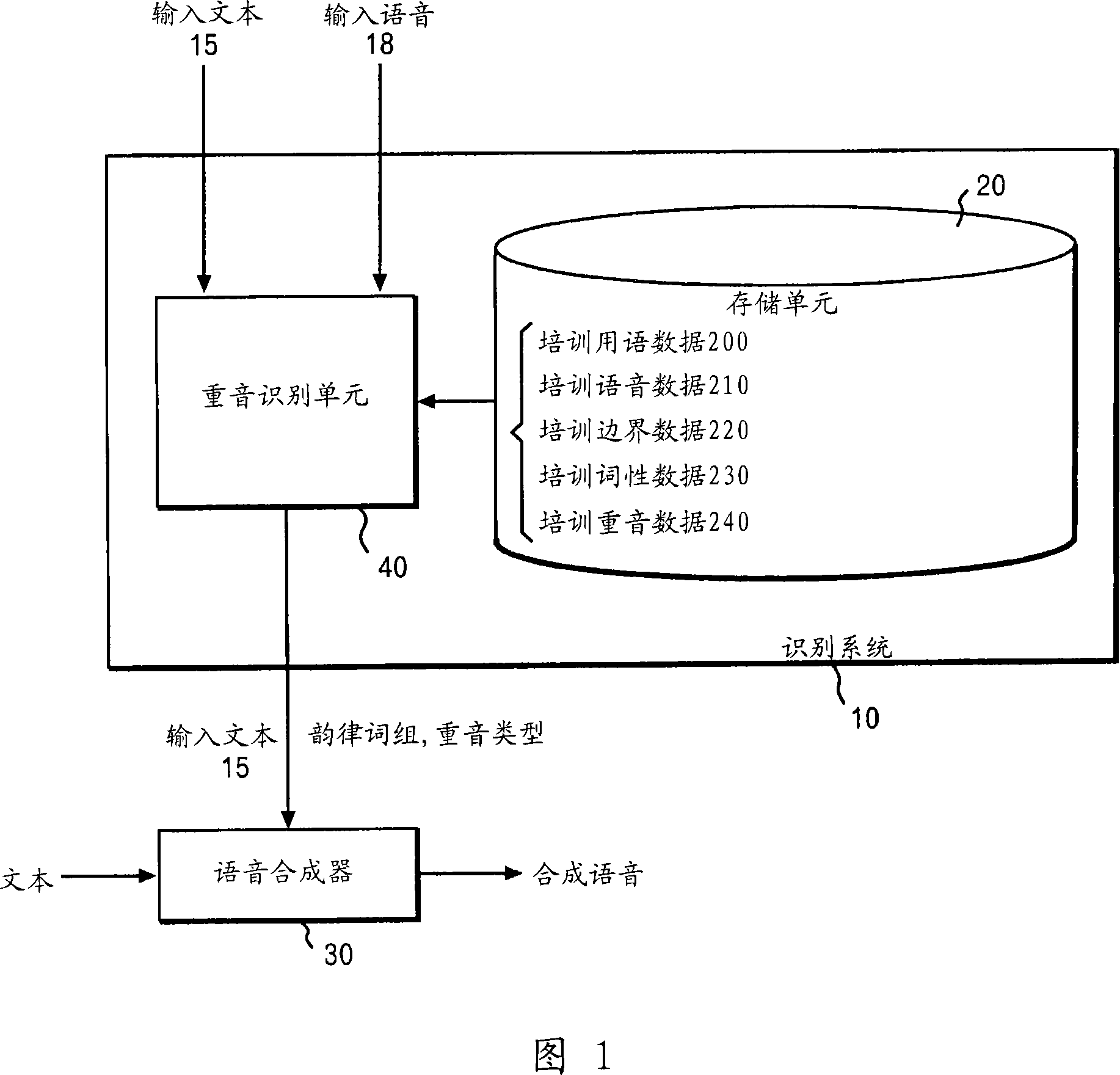
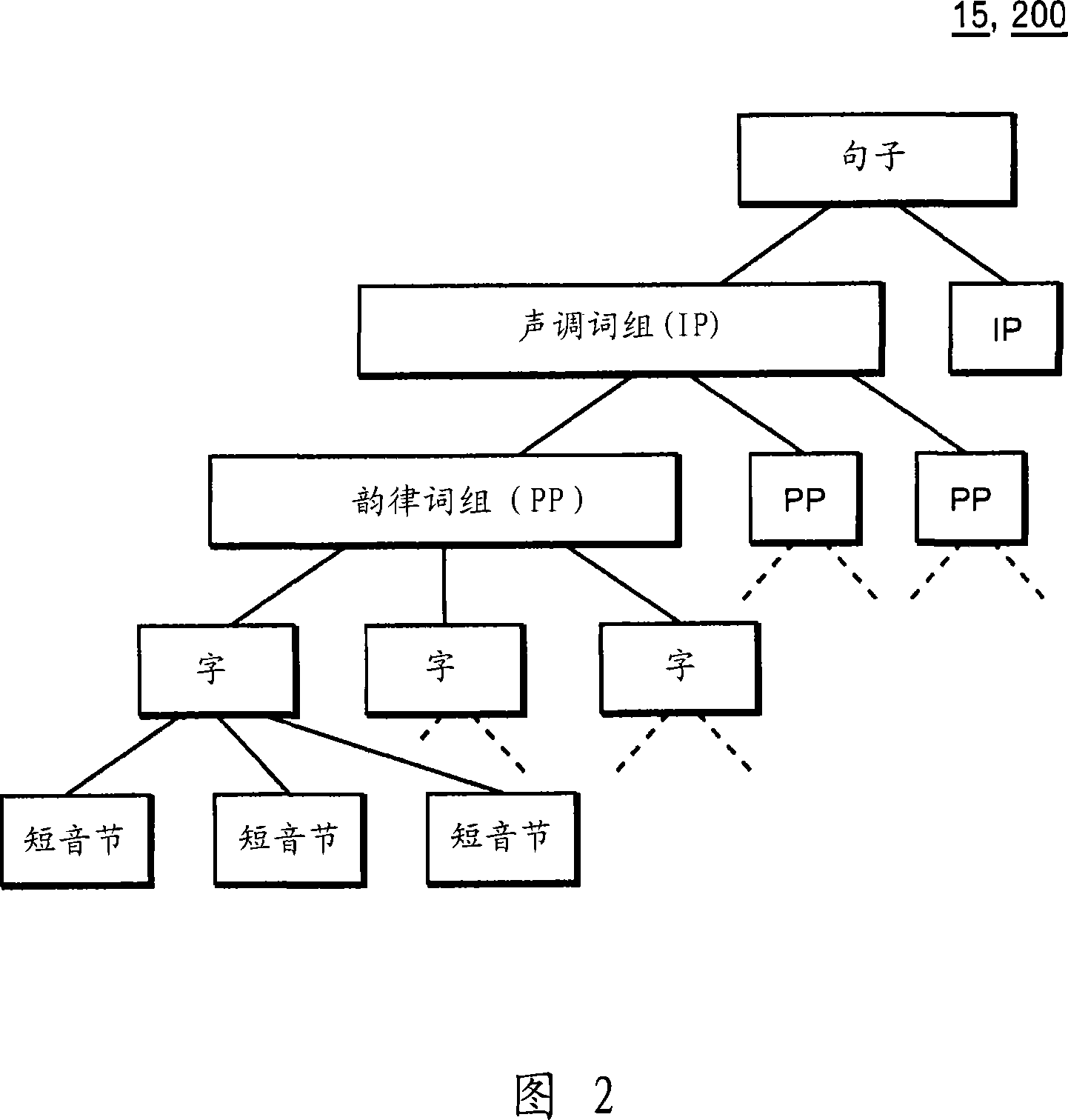
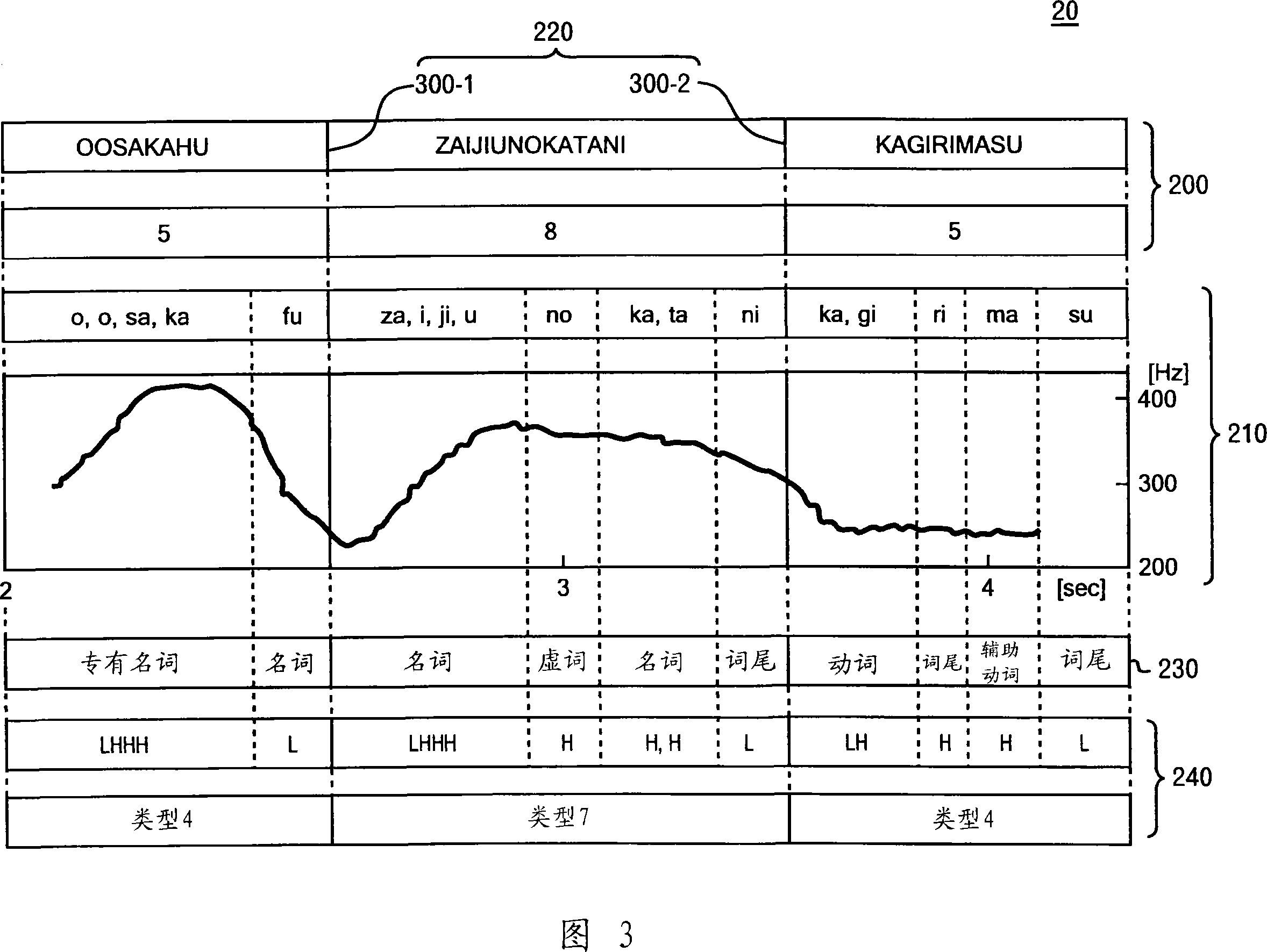
Stochastic Syllable Accent Recognition
Training wording data indicating the wording of each of the words in training text, training speech data indicating characteristics of speech of each of the words, and training boundary data indicating whether each word in training speech is a boundary of a prosodic phrase are stored. After inputting candidates for boundary data, a first likelihood that each of the a boundary of a prosodic phrase of the words in the inputted text would agree with one of the inputted boundary data candidates is calculated and a second likelihood is calculated. Thereafter, one boundary data candidate maximizing a product of the first and second likelihoods is searched out from among the inputted boundary data candidates, and then a result of the searching is outputted.
Owner:NUANCE COMM INC
Storage method of substantial data integrating shape and physical properties
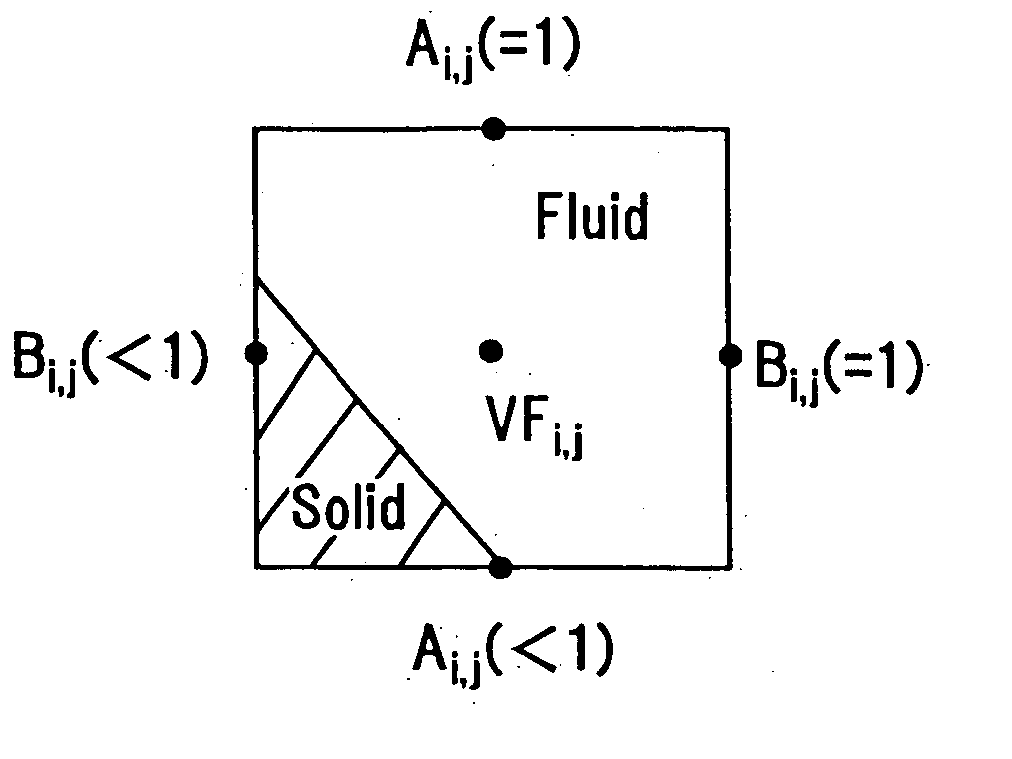
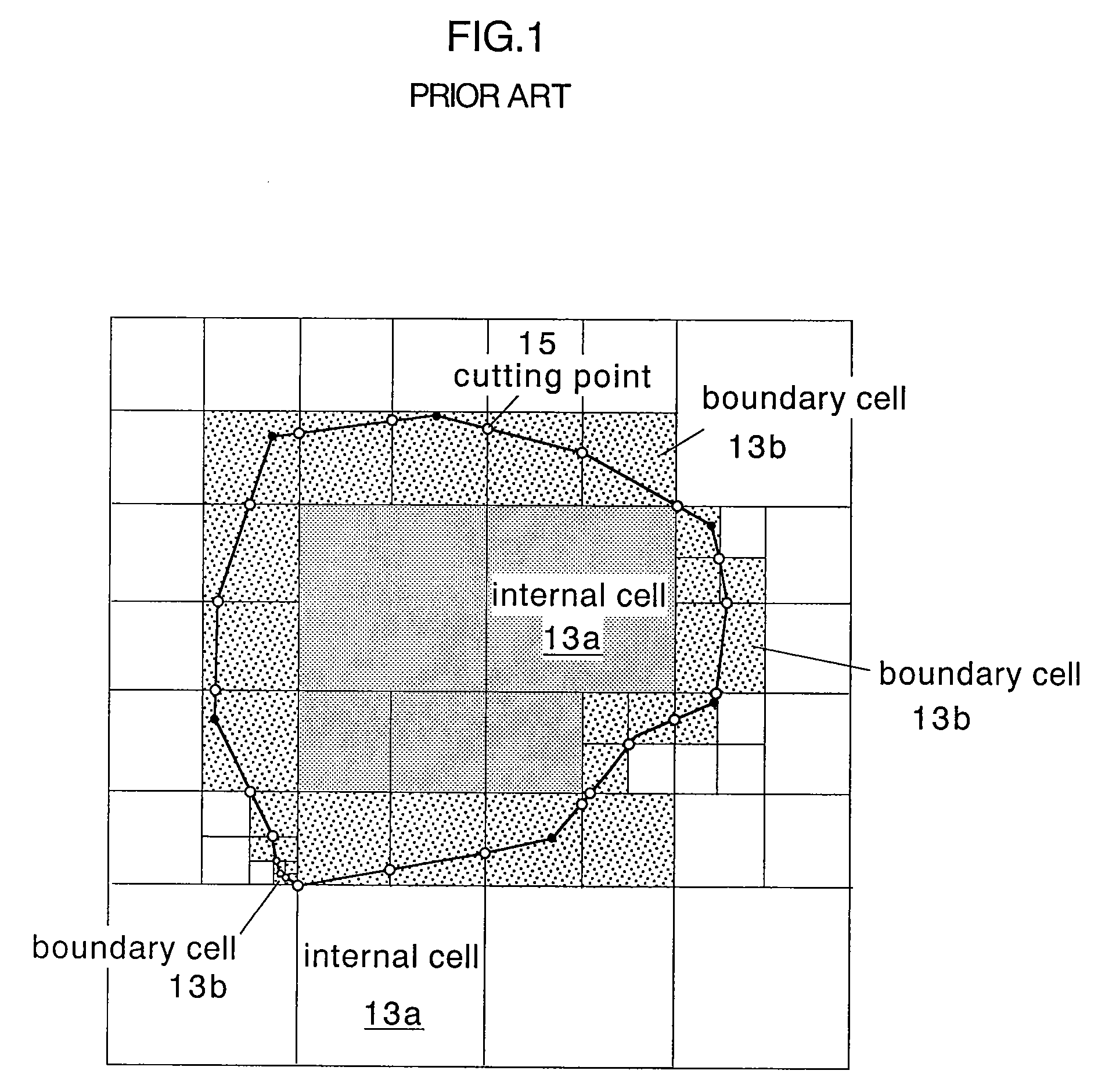
InactiveUS7088363B2Design optimisation/simulationSpecial data processing applicationsComputer graphics (images)External data
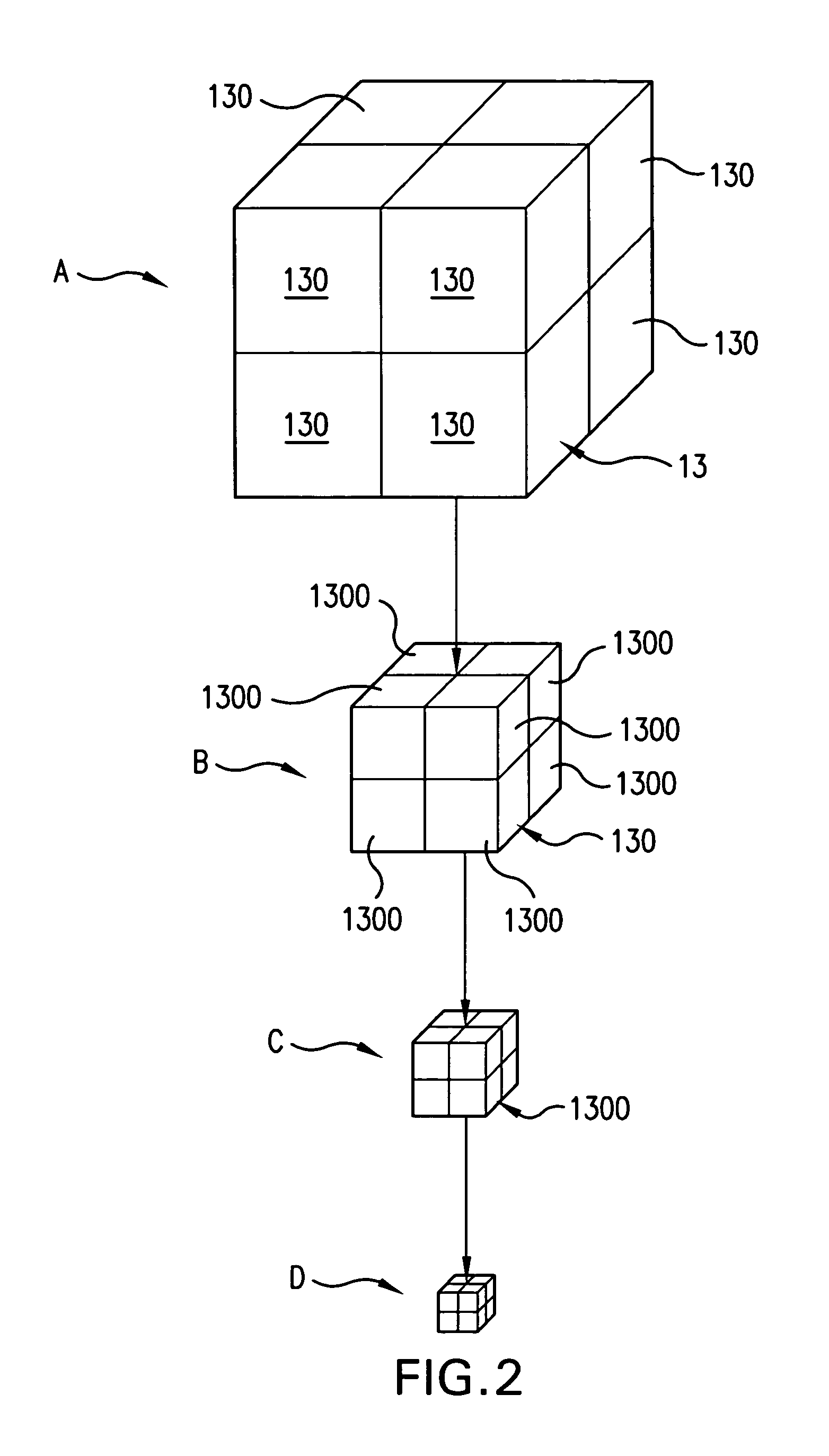
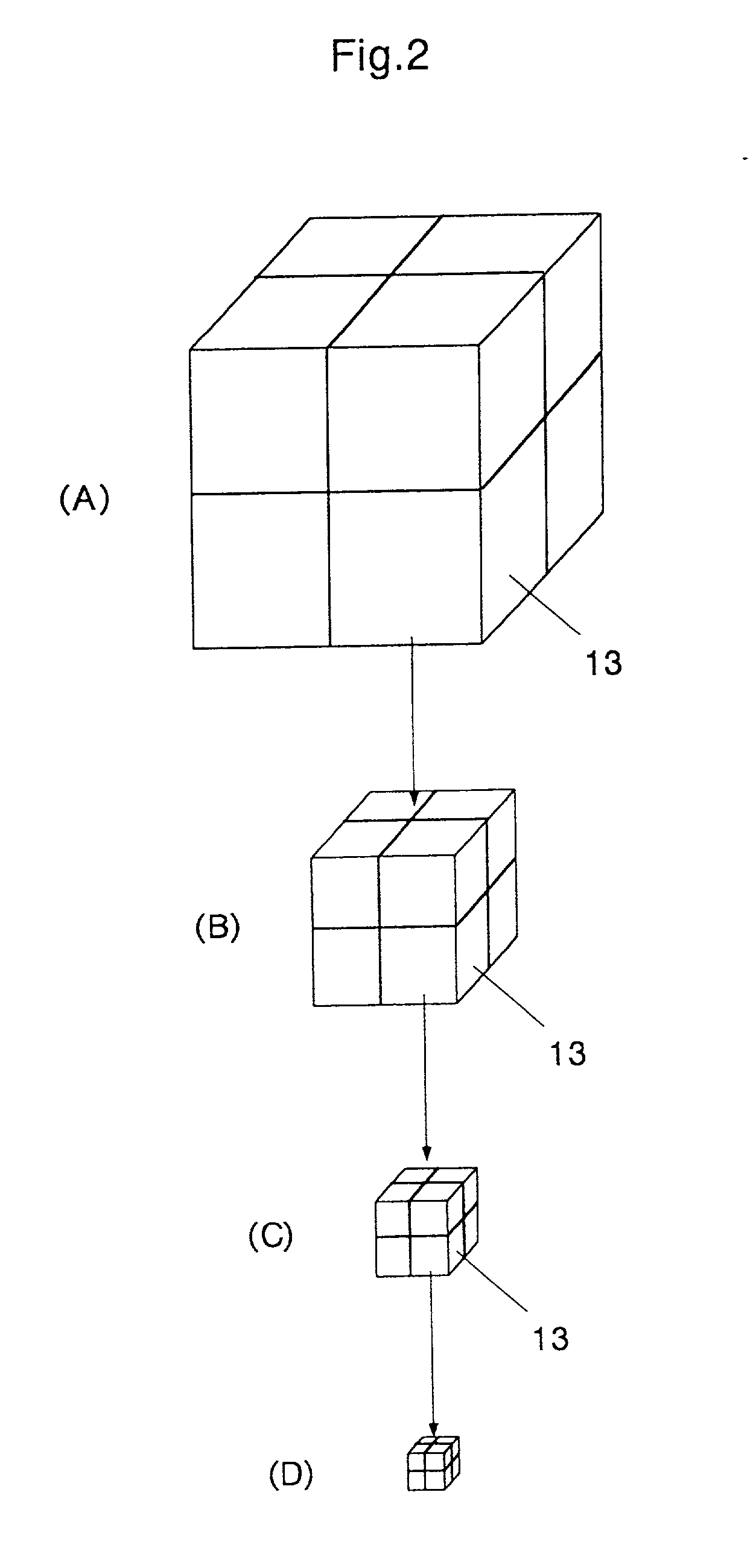
A method of storing substantial data integrating shape and physical properties comprising (A) inputting external data 12 consisting of boundary data of an object 1, (B) dividing, by modified Octree division, the external data into cubical cells 13 which boundary surfaces are orthogonal to each other, and (C) storing the values of various physical properties for each of the cells. Furthermore, in step (B), each of the divided cells 13 is classified to non-boundary cells 13a located in the interior of the object or in a region outside of the object, and boundary cells 13b including boundary surfaces. Thereby, substantial data integrating shape and physical properties can be stored in small storage capacity, thus enabling the integration of CAD and simulation.
Owner:RIKEN
DMA controller, DMA control method and DMA control program
InactiveUS7330914B2Increase profitImprove utilization efficiencyMemory adressing/allocation/relocationInput/output processes for data processingData segmentBurst transmission
The present invention is a DMA controller that accesses a transfer source and a transfer destination of a DMA transfer via a bus, that chains a plurality of data segments in the transfer source according to an instruction by an external initiator, and that performs burst-transfer to the transfer destination, and when a boundary data, that is a remaining data after dividing in the bus width units and data less than the bus width, is generated, the boundary data is stored in a boundary data buffer in the DMA controller, the data to be read from the transfer source by the next DMA command and the previously stored boundary data are merged, and the data is burst-transferred to the transfer destination.
Owner:FUJITSU LTD
Method and program for generating volume data from boundary representation data
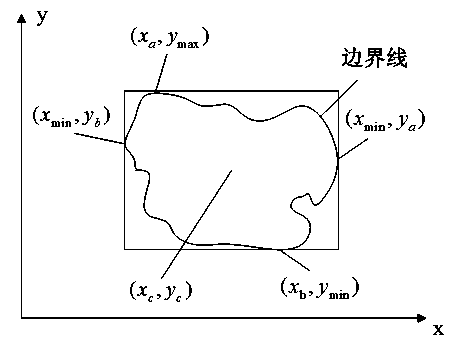
InactiveUS20070057938A1Easy to shapeDesign optimisation/simulationImage data processing detailsComputational scienceBoundary plane
A data input means inputs boundary data of an object to a computer, a data converting means converts the boundary data into a triangle patch having a phase, an associating means divides a space into rectangular parallelepiped cells having boundary planes intersecting perpendicularly and associates the cell with a triangle to be included in the cell, a dividing / arranging means divides a triangle patch having a phase and floating in the space at cell faces and keeps all triangles arranged within and on the boundaries of cells, a ridge line integrating means integrates ridges that do not alter the phase, a cell assigning means assigns each triangle and its vertex to a cell with reference to index data of the vertex, and a labeling means sets an attribute value of each cell.
Owner:RIKEN
Efficient time domain full waveform inversion method
ActiveCN105319581AReduce the number of simulationsReduce input and outputSeismic signal processingWave equationWave field
The present invention provides an efficient time domain full waveform inversion method, belonging to the field of efficient, low storage, high precision and high speed modeling of petroleum seismography data. The efficient time domain full waveform inversion method comprises the following steps: (1) employing original seismic observation records to randomly form supper-shot gathers with different frequency bands through adoption of a source polarity randomizing scheme, a source position randomizing scheme and a source number randomizing scheme; (2) accelerating the forward modeling of high order staggered mesh finite differences of a sound wave equation system and an elastic wave system of the one-form basis of the time domain through adoption of a multi-GPU parallel computing technique on the basis of CUDA, and obtaining a supper-shot gather with the ifreq frequency band simulated by the GPU; and (3) simulating propagations with different seismic sources through multi-GPU nucleus and through adoption of the collaborative technology of the CPU and the GPU at the forward modeling, and storing boundary data of a seismic source wave field and all the wave fields at the last moment to a computer memory.
Owner:CHINA PETROLEUM & CHEM CORP +1
Pointer based binary search engine and method for use in network devices
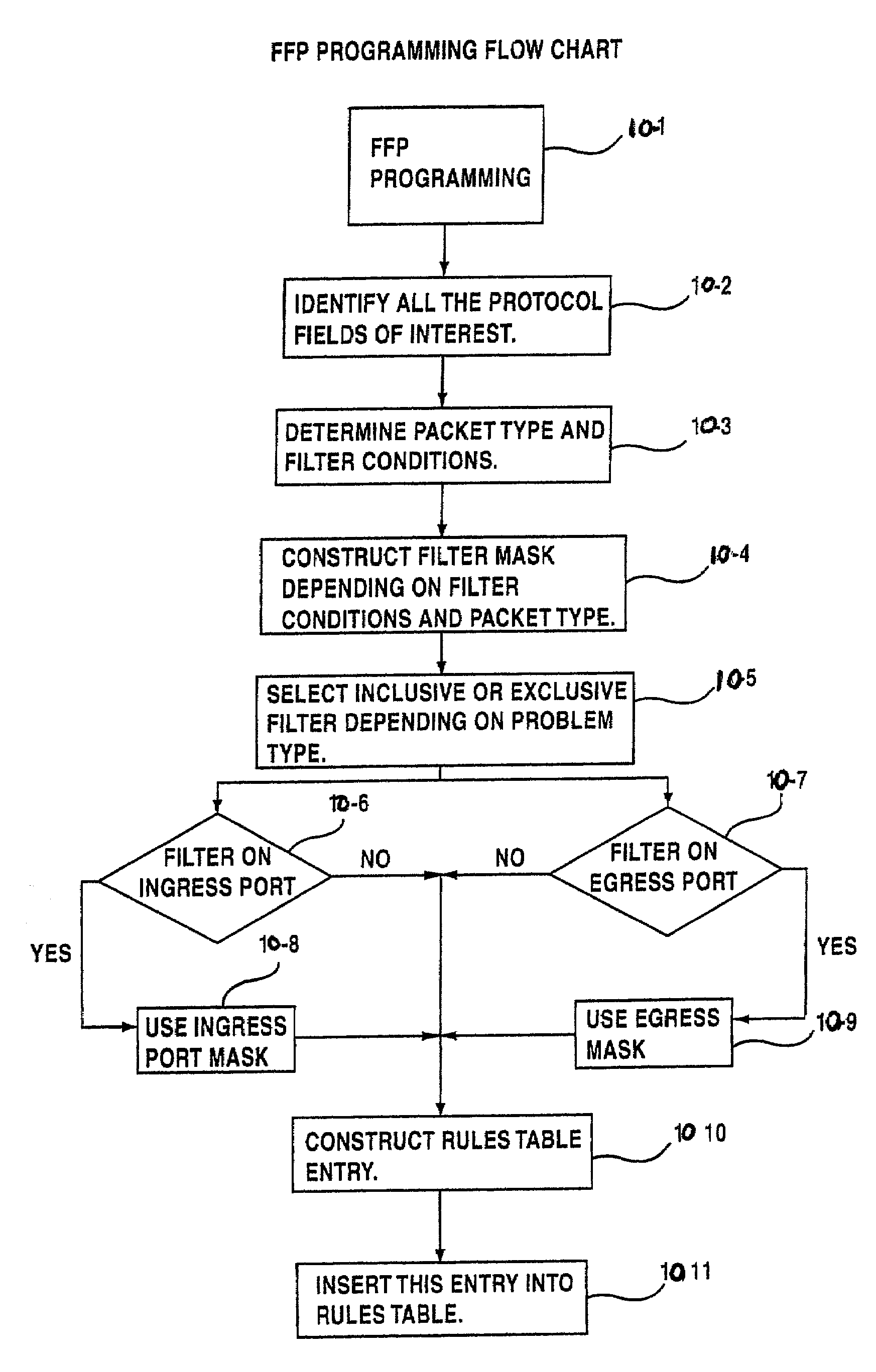
InactiveUS7068652B2Fast filter processingFrequency-division multiplex detailsDigital computer detailsData miningBoundary data
A network device includes at least one network port, a masks table, a rules table, a pointers table, and a fast filter processor. The masks table contains filter information and a mask key. The rules table contains corresponding rules to the filter information and is related to the mask table by the mask key. The pointers table contains boundary data related to the rules for corresponding filter information. The fast filter processor is coupled to the mask table, the rules table and the pointers table, and configured to perform at least one binary search for at least one rule related to a data packet received by the network device at the at least one network port, the binary search being limited based on the boundary data in the pointers table.
Owner:AVAGO TECH INT SALES PTE LTD
Bit clock with embedded word clock boundary
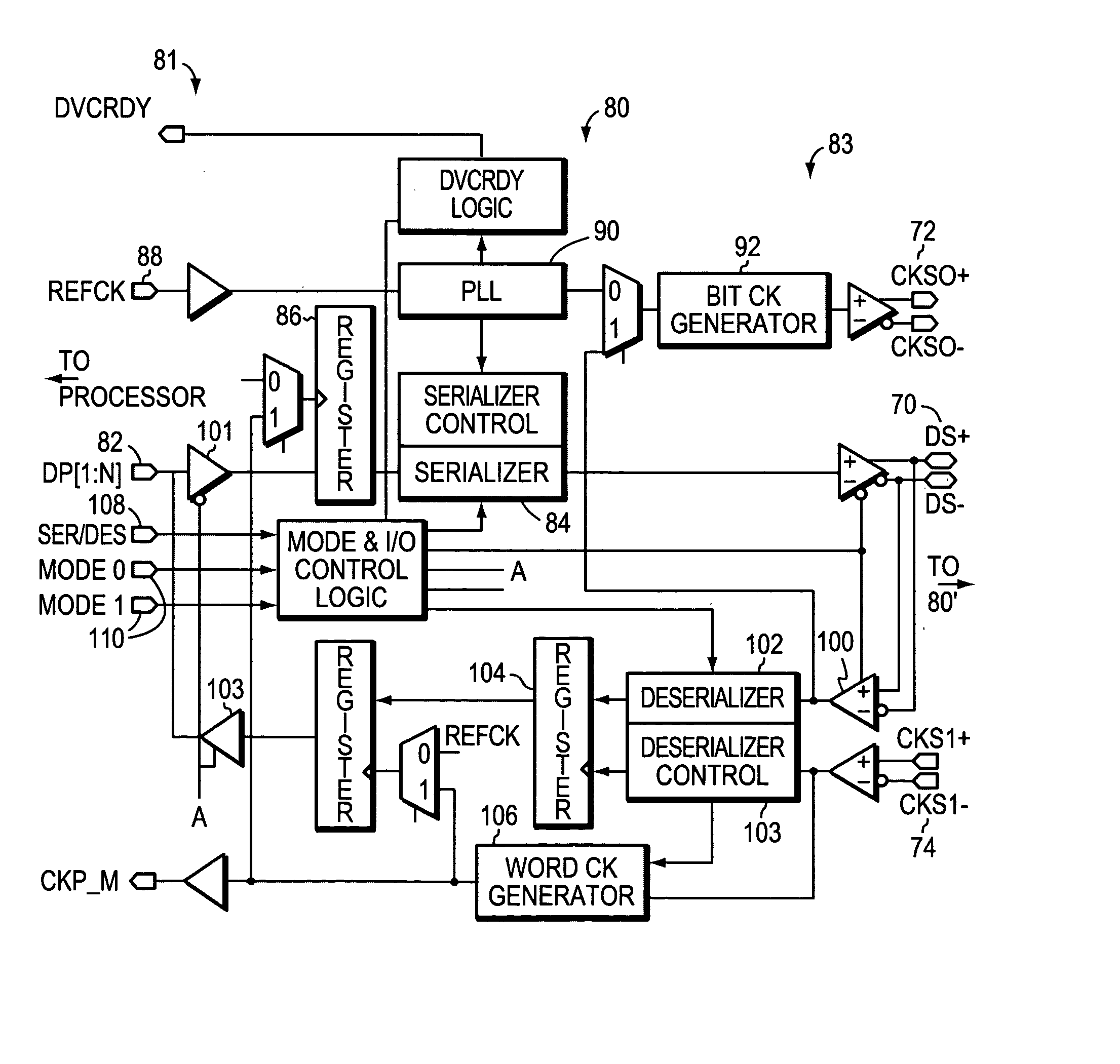
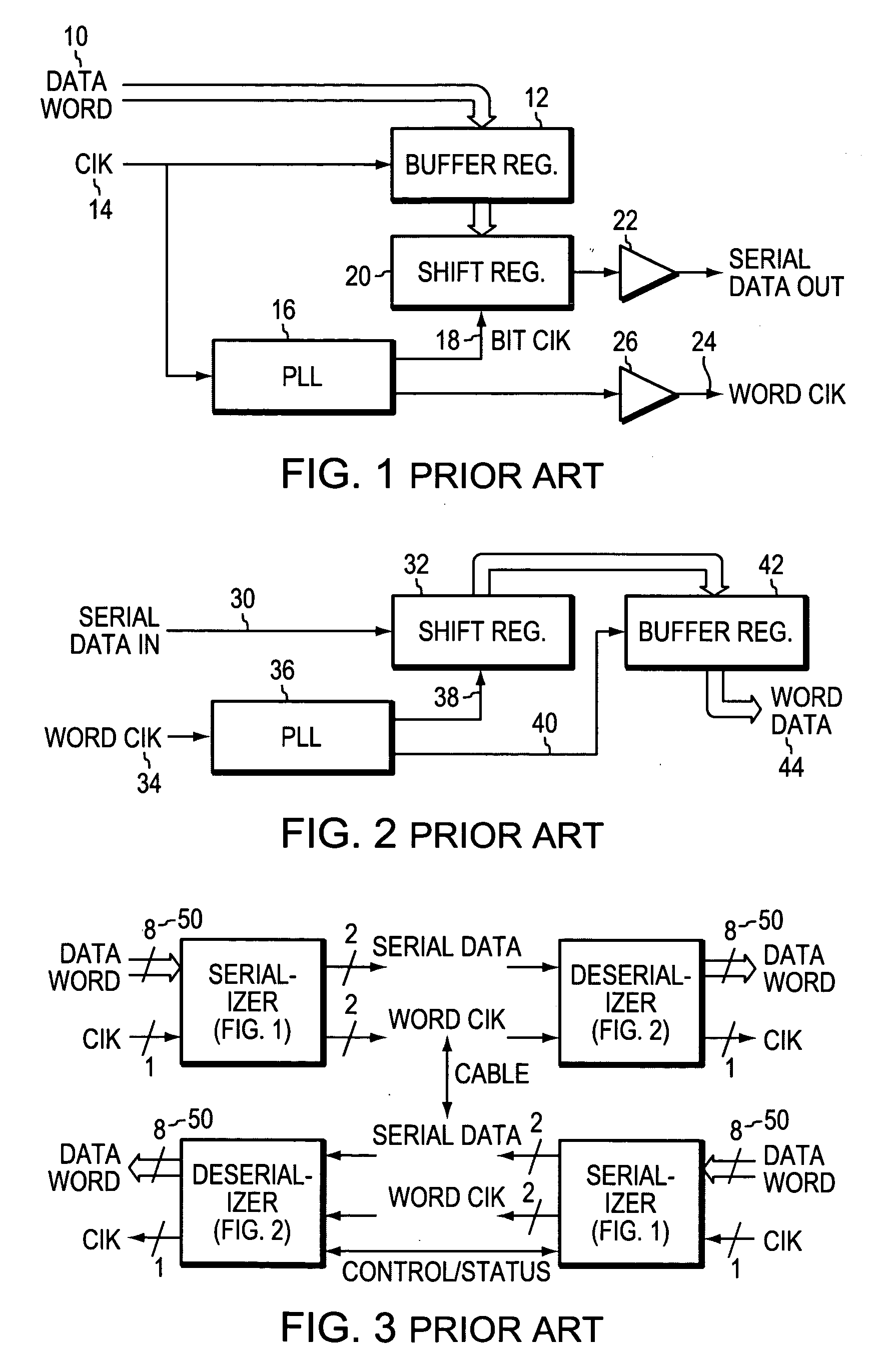
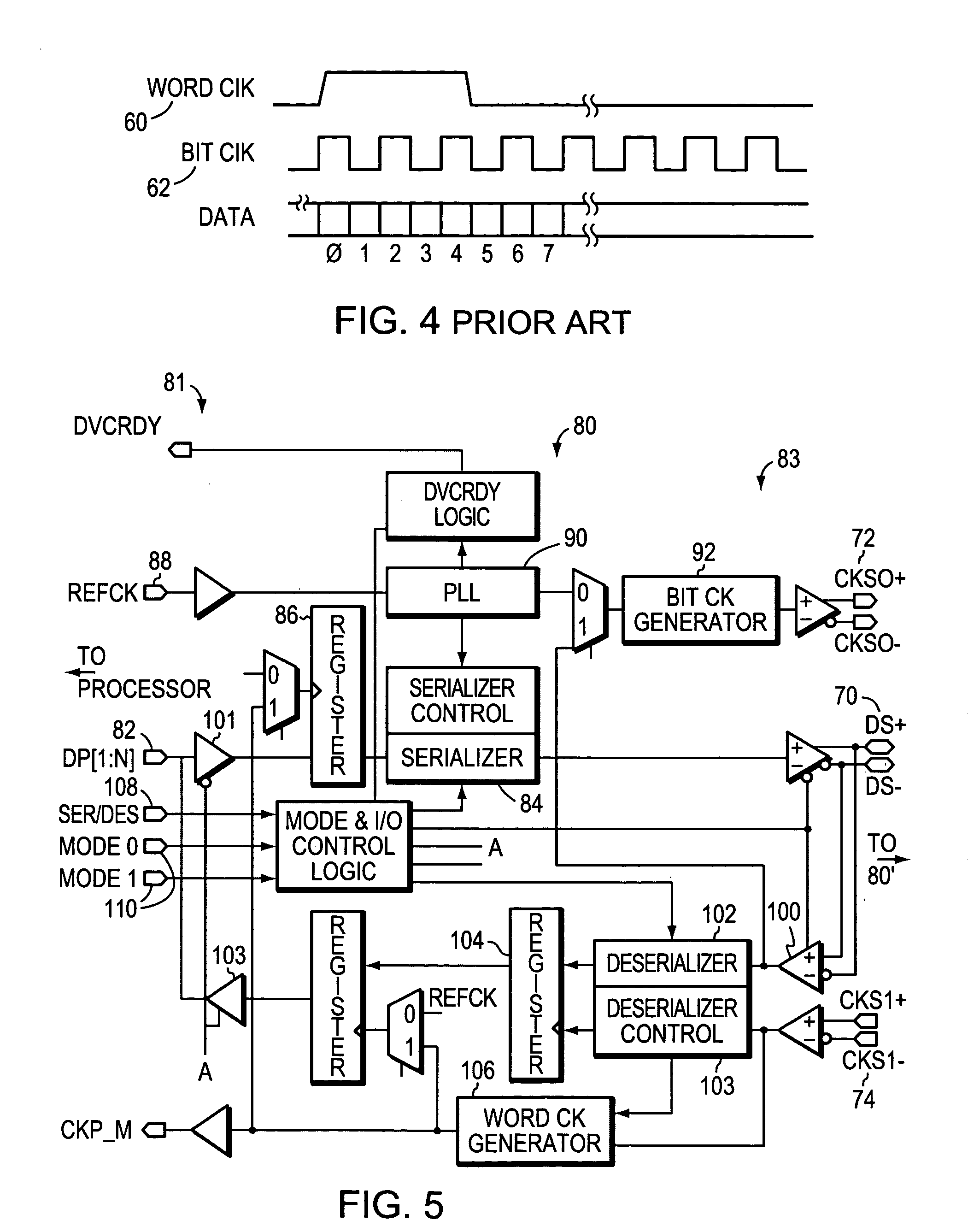
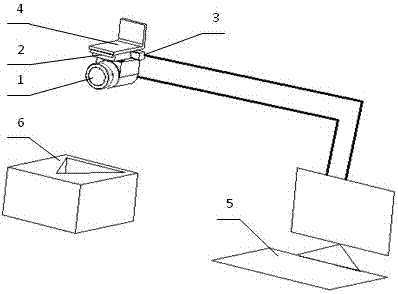
InactiveUS20050207280A1Easy to controlParallel/series conversionSynchronisation information channelsShift registerSensing data
A bi-directional serializer / deserializer is disclosed using a single bi-directional data line and a single bi-directional clock line. Gated buffers are controlled to operate either sending or receiving data, and a phase locked loop provides a clock to shift data out from a shift register. A reference clock is supplied to the PLL and the PLL generates a synchronous bit clock. The bit clock is sent over the clock line in parallel with the serial data bits, and the PLL bit clock is synchronized to the data bits. Two data boundary bits are inserted between the word data bits, the boundary data bits are arranged with a logic level transition between the two data boundary bits. Also, at the boundary of the words during the sending of the two boundary data bits, the synchronous bit clock is arranged to have no logic level transition. The receiving system will use the bit clock to serial load the received word and boundary data bits into a shift register. A word boundary is detected by sensing a data bit transition while there is no bit clock.
Owner:SEMICON COMPONENTS IND LLC
Two-dimensional-laser-radar-based method for measuring three-dimensional scanning system of hopper-shaped container
The invention relates to a two-dimensional-laser-radar-based method for measuring a three-dimensional scanning system of a hopper-shaped container. The method comprises: a measuring system is calibrated; a calibration element is moved away and a hopper-shaped container is arranged right below a two-dimensional laser radar; a computer equipped with point cloud data storage and processing programs sends a rotation instruction to motor and sends a scanning instruction to the two-dimensional laser radar simultaneously, so that the motor drives a workbench to make rotation and the two-dimensional laser radar installed on the work bench to scan a measured object; data obtained by scanning are stored into the computer with the point cloud data storage and processing programs, the computer carries out simplification processing on the data to transform the simplified data into ones in a three-dimensional point cloud manner, and the three-dimensional point cloud is drawn at a computer screen; and triangular mesh construction is carried out on the three-dimensional point cloud to restore a three-dimensional mesh model of the hopper-shaped container, and extraction of boundary data of the hopper-shaped container is carried out and thus appearance dimensions like the length, width, and depth of the hopper-shaped container are calculated.
Owner:HEBEI UNIVERSITY OF SCIENCE AND TECHNOLOGY
System and method for facilitating target aiming and aircraft control using aircraft displays
ActiveUS7283064B2Facilitating target aiming and aircraft controlHigh transparencyAnalogue computers for trafficNavigation instrumentsControl signalDisplay device
Owner:HONEYWELL INT INC
System and method for identifying accent of input sound
Disclosed are a method and a system of input speech stress recognition, with a training vocabulary, training speech data and training boundary data stored. Hereafter, after the candidates of boundary data are input, the first probabilities are calculated based on the input vocabulary, speech and boundary data. The first probabilities are the corresponding probabilities between the words of input text, each prosodic word boundary and each boundary candidate. In addition, the second probabilities also can be calculated based on the input vocabulary, speech and boundary data when the input speech has boundary of the prosodic word assigned by one of the input boundary data candidates. The second probabilities are the corresponding probabilities between the word speech of input text and input speech data. Thereafter, the optimized the boundary candidate is searched out as the output result by maximizing the products of the first and the second probabilities.
Owner:NUANCE COMM INC
Storage method of substantial data integrating shape and physical properties
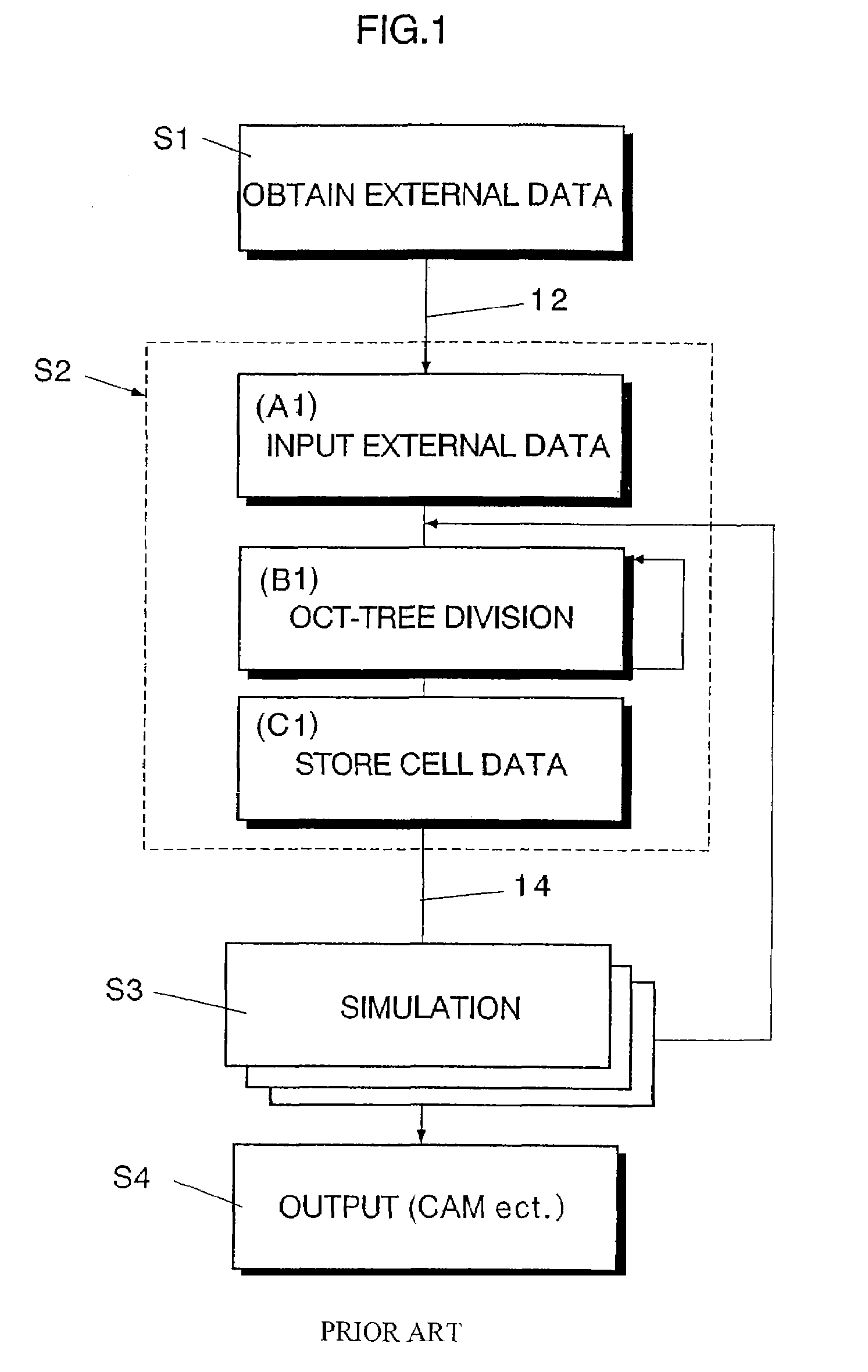
InactiveUS20020135577A1Solve large capacityDesign optimisation/simulationSpecial data processing applicationsDividing cellExternal data
There is disclosed a method of storing substantial data integrating shape and physical properties comprising an external data input step (A) for inputting external data 12 consisting of boundary data of an object 1, an Octree division step (B) for dividing, by Octree division, the external data into cubical cells 13 which boundary surfaces are orthogonal to each other, and a cell data storage step (C) for storing the values of various physical properties for each of the cells. Furthermore, in the Octree division step (B), each of the divided cells 13 is classified to internal cells 13a located in the interior of the object, external cells 13b in the exterior thereof and boundary cells 13c including boundary surfaces. Thereby, substantial data integrating shape and physical properties can be stored in small storage capacity, whereby it is possible to manage shape, structure, physical-property information, and history of matter in a unified way, and to manage data associated with a series of processes of from design to work, assembly, test and evaluation under the same data, thus enabling the integration of CAD and simulation.
Owner:RIKEN
Apparatus, system and method for monitoring tissue during an electrosurgical procedure
Owner:TYCO HEALTHCARE GRP LP
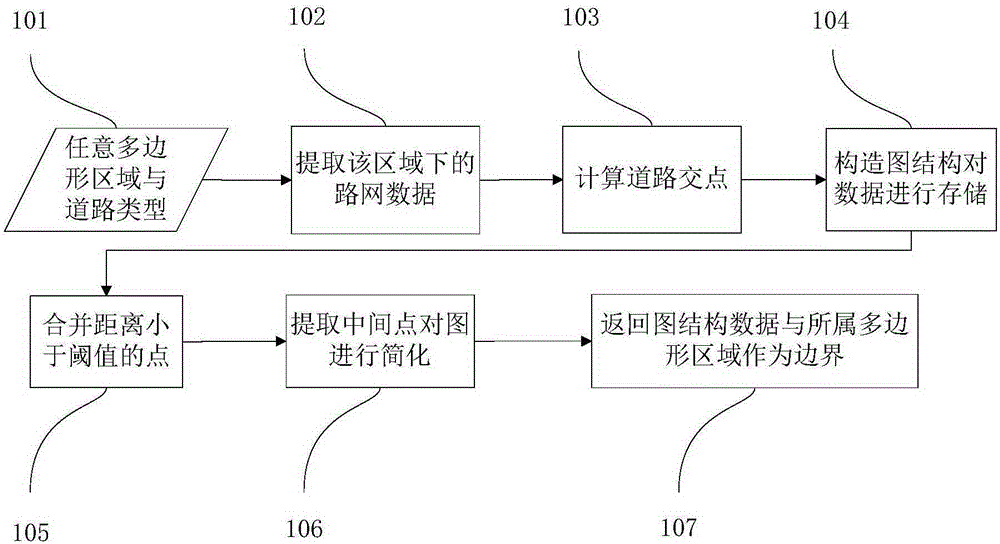
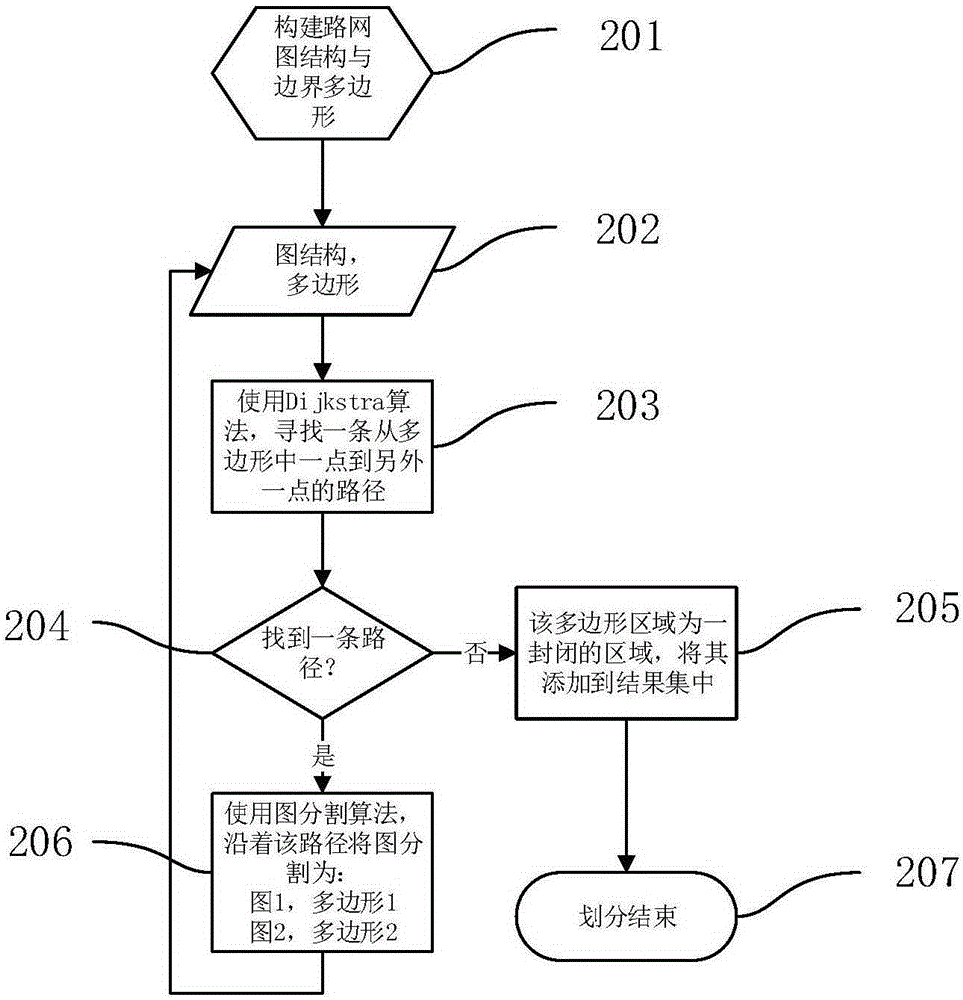
Urban hierarchical regional division method based on vector map data model
InactiveCN105222793AKeep original dataProcessing without distortionInstruments for road network navigationUrban regionOriginal data
The invention discloses an urban hierarchical regional division method based on a vector map data model. The method comprises the steps that a corresponding road network diagram structure and polygon boundary data are established for a region needing to be divided; a corresponding diagram structure and boundary polygon are established according to the road network diagram structure and the polygon boundary data, a path is searched to divide an original polygon into two parts, and paths are continuously searched in the newly generated polygons to conduct diagram division till all the polygons cannot be divided; a city is divided into primary regions according to primary road data, all the primary regions are traversed, secondary road data under the primary regions are extracted, and secondary regions under the regions are divided out by applying a regional division algorithm, so that a hierarchical structure of urban regions is formed. According to the urban hierarchical regional division method based on the vector map data model, a diagram structure is used for storing vector map data, operations are all based on the vector data, original data of a map can be completely reserved, and the data can be processed in an undistorted mode.
Owner:HUAZHONG UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com