Key management system and method for a train protection system
A security system and key technology, applied in the field of key management, can solve problems such as troublesome, error-prone, inefficiency, etc., and achieve the effect of simplifying definition, less error-prone, and accelerating generation and distribution.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
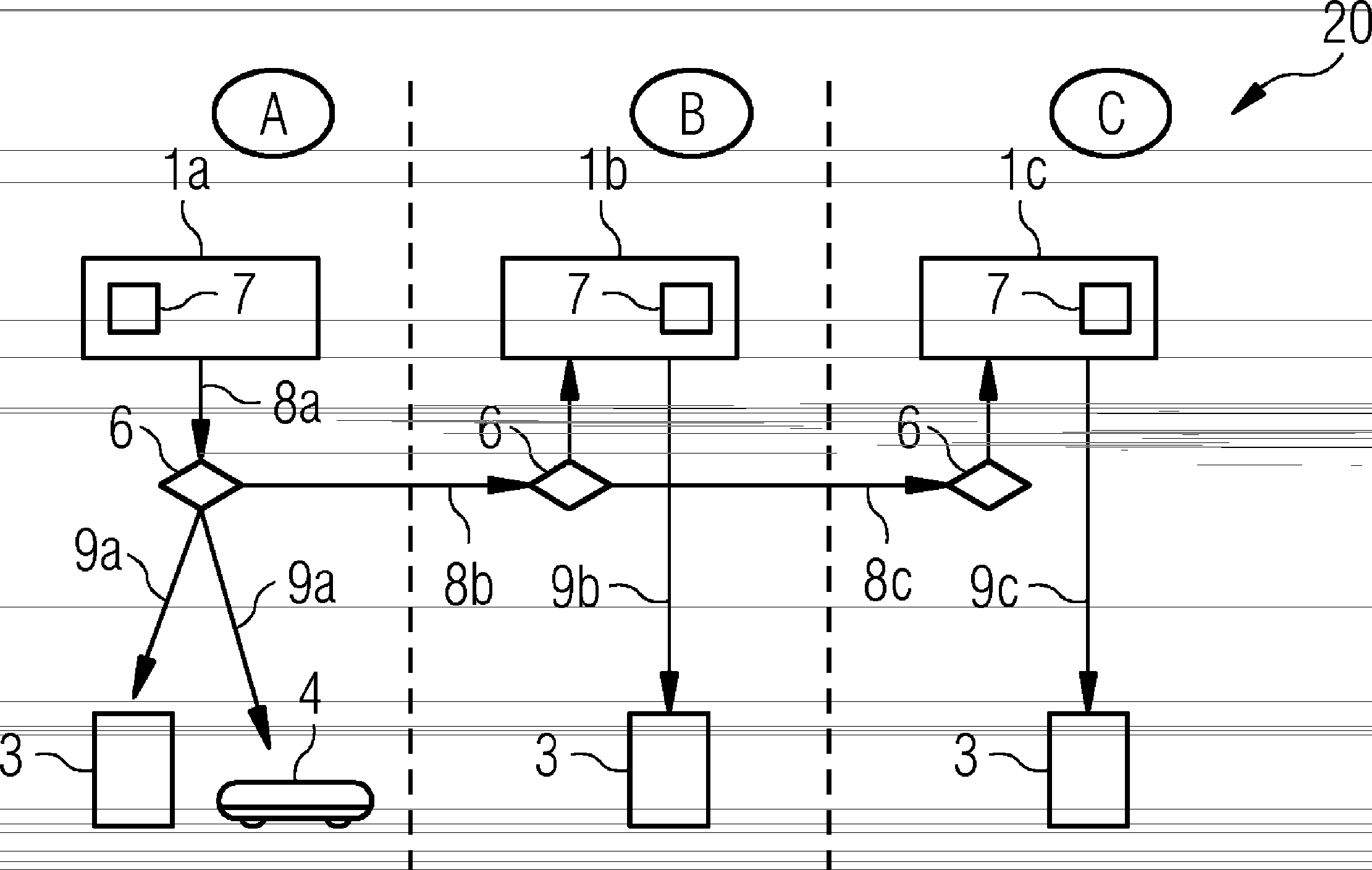
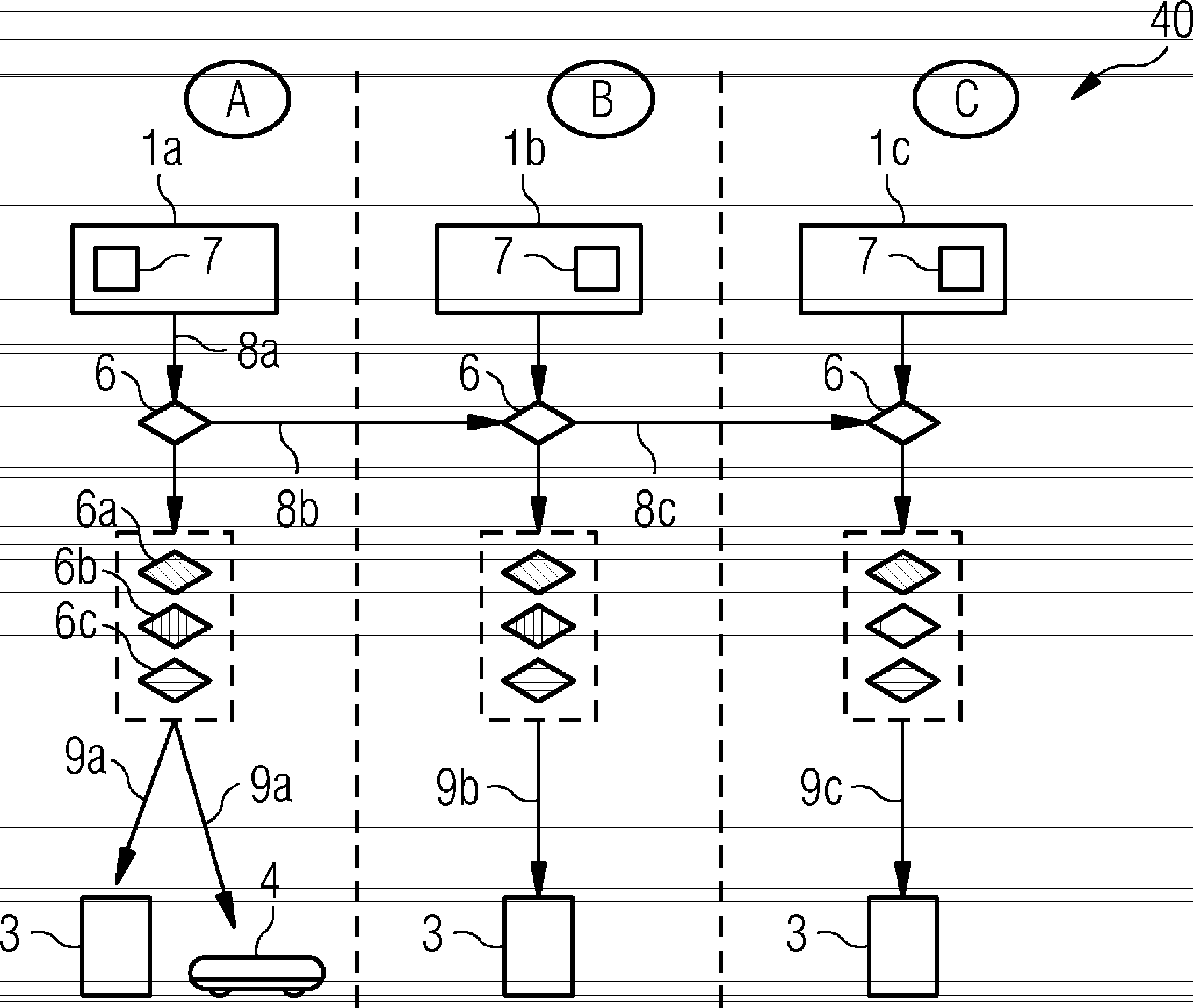
[0033] In the sense explained below, a communication key includes all encrypted information and data units, which are suitable for encrypting data in plaintext format and thereby generating data in eavesdropping and / or reading-proof ciphertext format, or which are suitable for It is suitable for protecting the integrity of data in plaintext format and implementing encrypted checksums (Prüfsumme), and it is also suitable for recovering data in plaintext format from data in ciphertext format in the identification of encrypted information or verifying that said data is transmitted period has not been processed. A communication key in the sense of the invention can include, for example, a symmetric key pair, an asymmetric key pair or similar encryption methods. For example, communication keys can be used via methods such as AES, DES, KDF, IPsec, SSL / TLS, MACsec, L2TP, PPTP, PGP, S / MIME or via associated key management such as IKE, EAP or other method uses a similar technique.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com