Implementation method and system of wireless information safety device
A technology of information security and implementation method, applied in the field of information security, can solve the problems of inconvenience, high cost, and inability to control and manage multiple encryption locks, so as to avoid frequent plugging and unplugging, save costs, and reduce the risk of information leakage. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
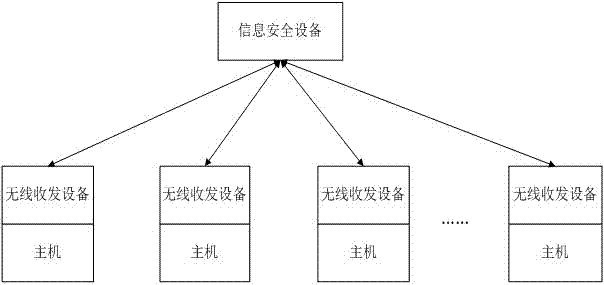
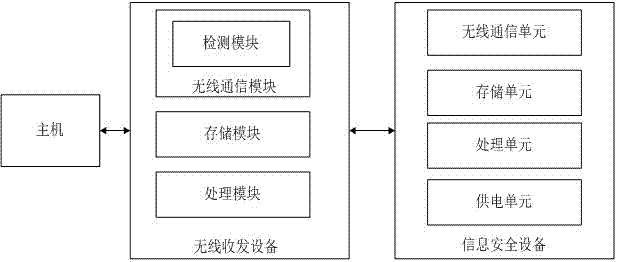
[0118] For example, an IT company and a research and development team use the product in the present invention. According to an embodiment of the present invention, a certain number of wireless transceiver devices are customized according to the needs of the research and development team. Assuming that there are 10 project personnel (including the project manager), then 1 1 information security equipment and 10 wireless transceivers supporting the information security equipment. In this embodiment, the information security device is a dongle, the dongle is carried and kept by the project manager, the wireless communication method is bluetooth, and the wireless transceiver device adopts a USB connector (the wireless transceiver device is hereinafter referred to as a USB transceiver). The wireless transmission range is 10 meters.
[0119] In this embodiment, the 10 USB transceivers are assumed to be named U1, U2...U10 for easy identification; the dongle ID is assumed to be USB_B...
Embodiment 2
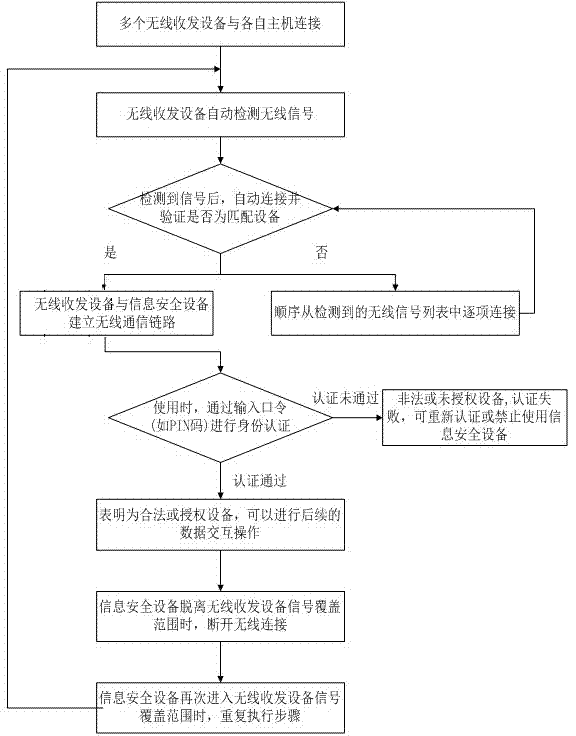
[0132] This embodiment is partly the same as Embodiment 1. The difference in this embodiment is that a list of identification information of 10 matching USB transceivers is stored inside the dongle. Such as Figure 5 Shown, the concrete implementation mode of this embodiment is:
[0133] 1. Project participants connect the USB transceiver to the host through the host interface;
[0134] 2. The USB transceiver automatically detects other wireless signals within the signal coverage area (when the project manager carrying the dongle enters the signal coverage area, the USB transceiver will detect the wireless signal of the dongle);
[0135] 3. After the USB transceiver detects the wireless signal, it automatically sequentially connects with the wireless signals in the detected wireless signal list, and sends a verification request, and the verification request includes the identification information of the USB transceiver;
[0136] 4. If the wireless signal device does not resp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com