Color image encryption method based on chaos sequence and hyper-chaos system
A technology of chaotic sequence and encryption method, which is applied in image data processing, image data processing, instruments, etc., and can solve problems such as ignoring mutual influence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0075] Embodiment 1: in the present embodiment, the programming software that adopts is Matlab7.0, selects attached image 3 The Lena standard color image with a size of 256×256 (M×N) shown in (a) is the experimental object. The specific process of encrypting the Lena color image is as follows:
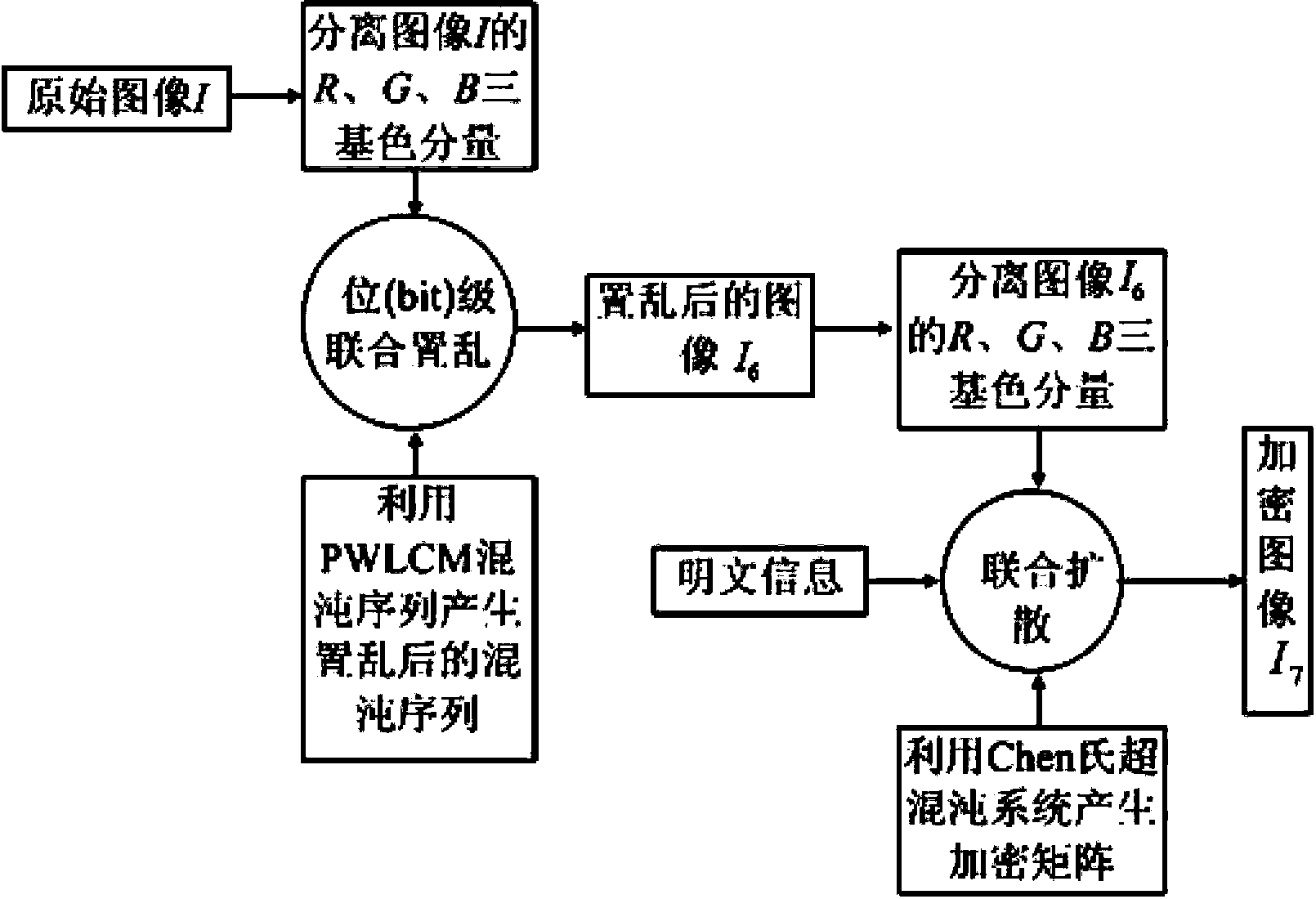
[0076] 1. Input the original Lena color image, and use I=imread('Lena.bmp') to read the image information. Separate the R, G, and B three primary color components of the color image I to obtain three image matrices I_R MN =I(1:256,1:256,1), I_G MN =I(1:256,1:256,2) and I_B MN =I(1:256,1:256,3).
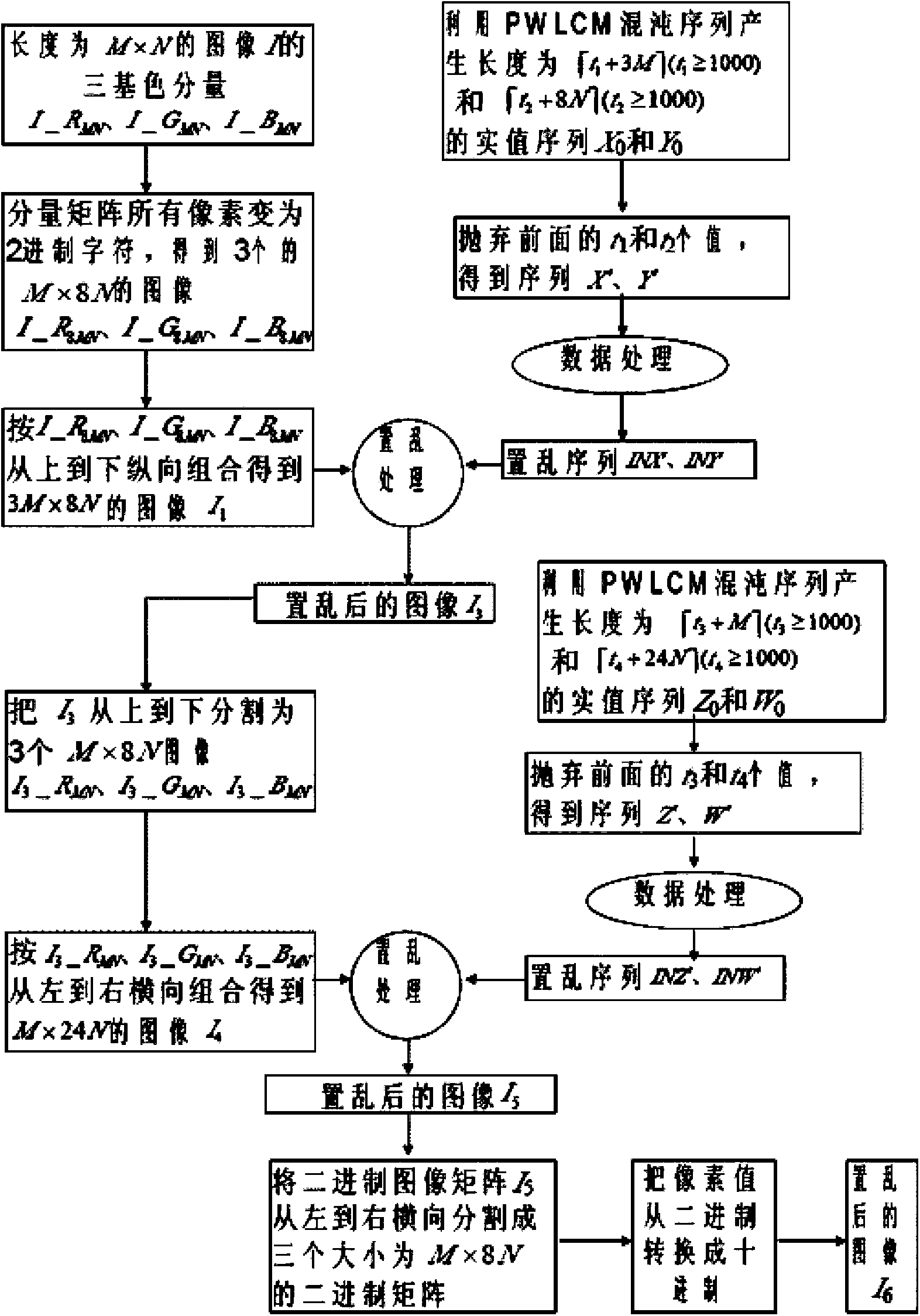
[0077] 2. Change each pixel in the above-mentioned three-primary color component matrix into an 8-bit binary string to obtain three binary matrices I_R with a size of 256×2048 8MN , I_G 8MN and I_B 8MN , then put the I_R 8MN , I_G 8MN and I_B 8MN , according to I_R 8MN , I_G 8MN and I_B 8MN The sequence is arranged vertically from top to bottom, and a new binary image matrix I wit...
Embodiment 2
[0152] Embodiment 2: in the present embodiment, the programming software that adopts is Matlab7.0, selects attached Figure 7 The Peppers standard color image shown in (a) with a size of 512×512 (M×N) is the experimental object, and the basic process of encrypting the Peppers color image is:
[0153] 1) Input the original color image I with the size of 512×512, separate the R, G, B three primary color components I_R of the image I MN , I_G MN and I_B MN , the size of each component matrix is 512×512, and the pixel value is between 0 and 255;
[0154] 2) Use the one-dimensional chaotic system to generate a chaotic sequence for scrambling, perform bit-level joint scrambling on the original color image I, and obtain an image I with a size of 512×512 after scrambling 6 , see attached Figure 7 (b);
[0155] 3) The scrambled image I 6 Decomposed into R, G, B three primary color components I 6 _R MN , I 6 _G MN and I 6 _B MN , and converted into three sequences of leng...
Embodiment 3
[0178] Embodiment 3: in the present embodiment, the programming software that adopts is Matlab7.0 equally, selects attached Figure 11 The color image shown in (a) with a size of 500×377 (M×N) is the experimental object, and the basic process of encrypting the color image is as follows:
[0179] 1) Input the original color image I with an image size of 500×377, separate the R, G, and B three primary color components I_R of the image I MN , I_G MN and I_B MN , the size of each component matrix is 500×377, and the pixel value is between 0 and 255;
[0180] 2) Use the one-dimensional chaotic system to generate a chaotic sequence for scrambling, perform bit-level joint scrambling on the original color image I, and obtain an image I with a size of 500×377 after scrambling 6 , see attached Figure 11 (b);
[0181] 3) The scrambled image I 6 Decomposed into R, G, B three primary color components I 6 _R MN , I 6 _G MN and I 6 _B MN , and converted into three sequences of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com