Methods for dynamic secret key storing and stored secret key reading and deleting
A dynamic storage and key storage technology, applied in the field of information security, can solve problems such as storage capacity limitations, achieve fast reading and storage, enhance security, and meet market demand.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] In order to make the present invention more comprehensible, preferred embodiments are described in detail below with accompanying drawings.
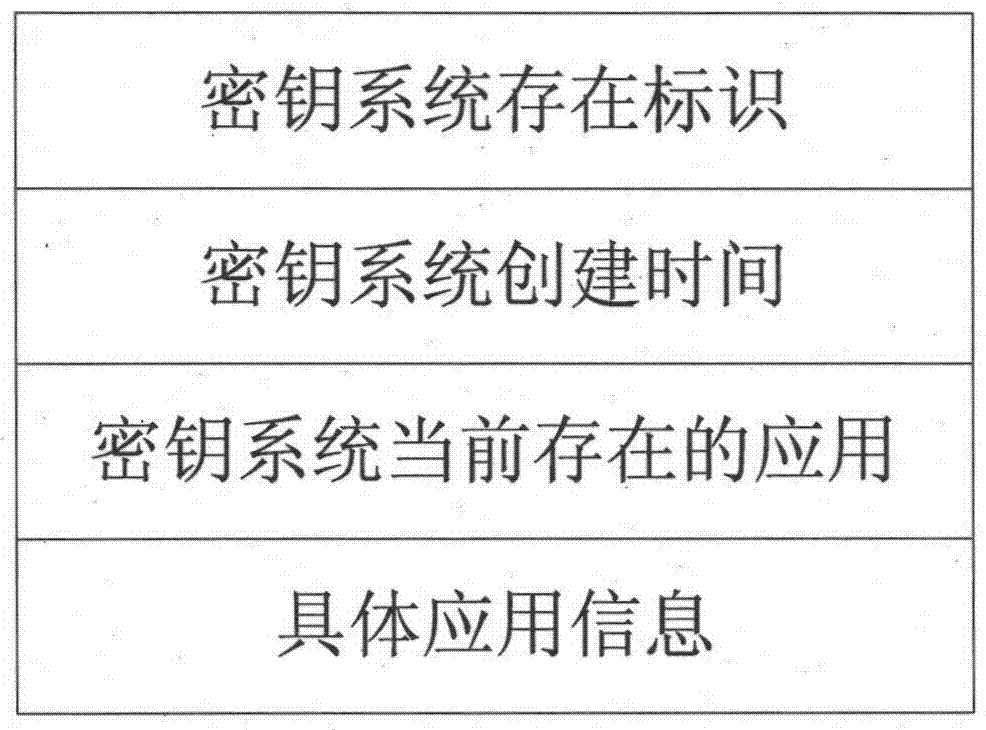
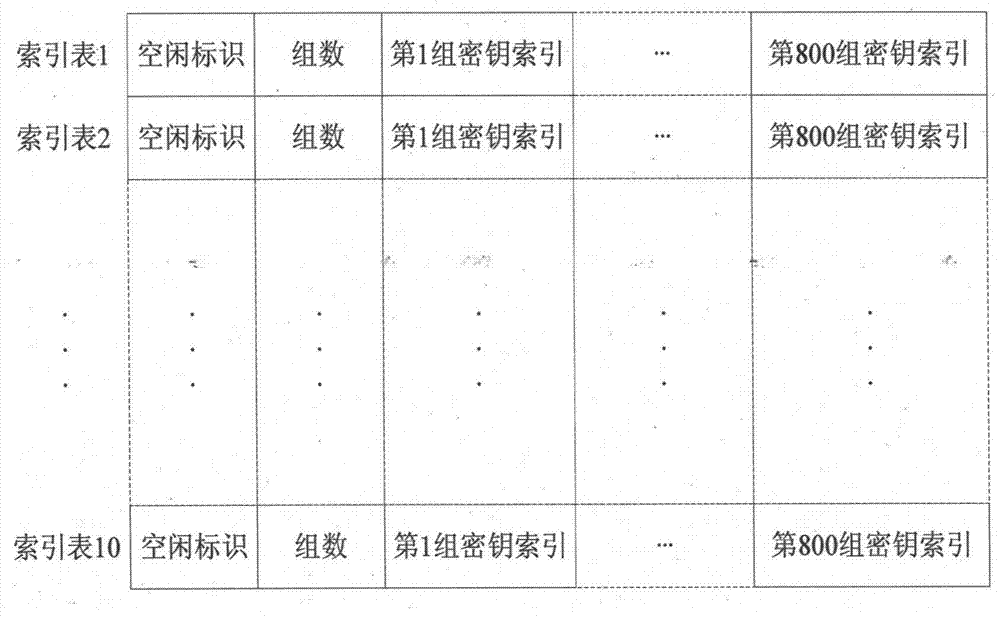
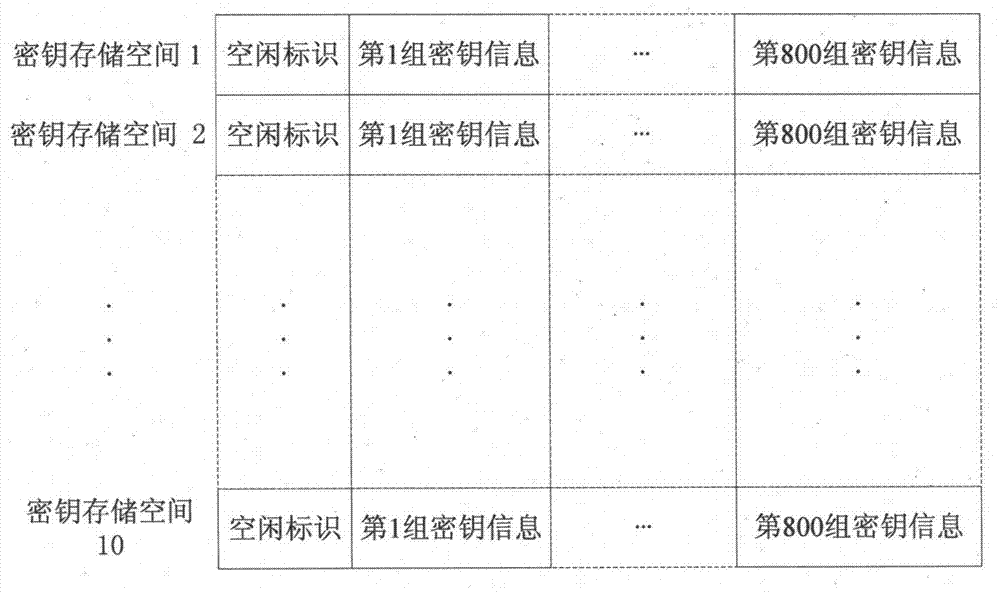
[0074] The present invention is realized by selecting an independent main control chip with on-chip non-volatile large-capacity memory and a dedicated security chip for encryption and decryption, wherein the storage space of the key system is divided into three parts: the first The part is to record the basic information of the key system, such as figure 1 As shown, the basic information of the key system includes the existence identifier of the key system, the creation time of the key system, the applications currently existing in the key system (currently existing application keys), specific application information (the application number corresponding to the key), etc. ;The second part is the key index information, which adopts the sorting method of dichotomy. Different application numbers correspond to a group of independent s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com