Network access control method and device
A network access control and network access technology, which is applied in the field of network access control methods and devices, can solve the problems of poor monitoring of user Internet access time, inability to control user Internet access time, and access to mobile Internet access time restrictions, etc., and achieve flexible control. , Effective and comprehensive effect of network access control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
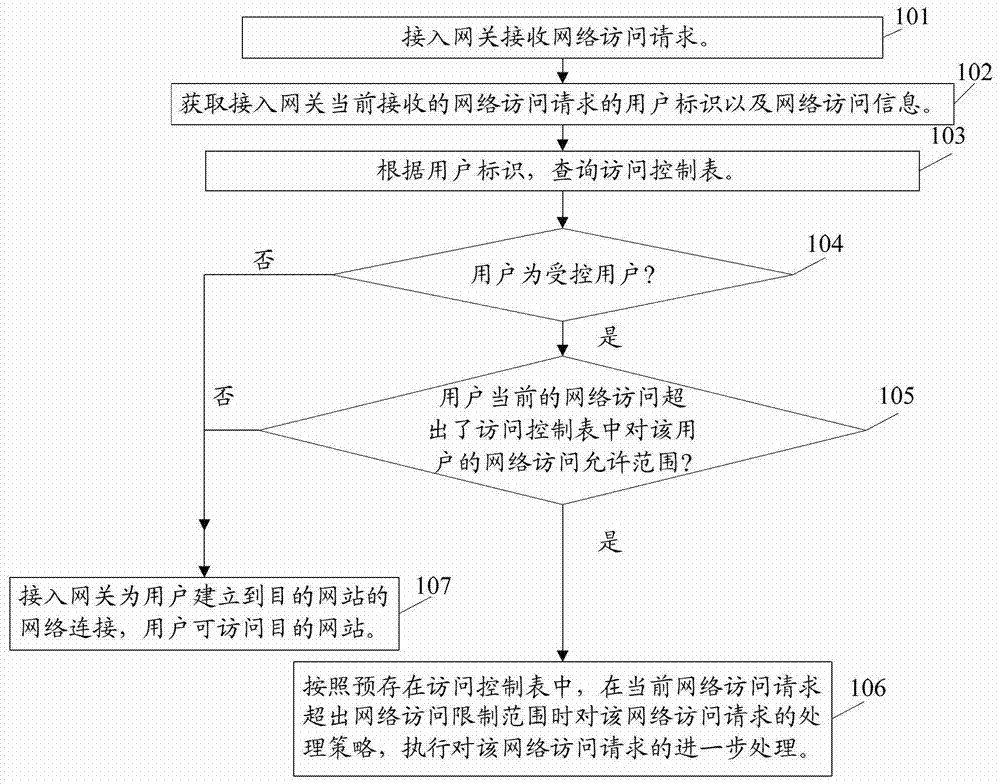
[0034] This embodiment discloses a network access control method, which can be applied at the communication network end to control the user's network access, see figure 1 As shown, it mainly includes the following steps:
[0035] Step 101: the access gateway receives a network access request.
[0036] All users access the network through the access gateway and use network services.
[0037] Step 102: Obtain the user identification and network access information of the network access request currently received by the access gateway.
[0038] In this embodiment, the user ID uniquely identifies the user in the network, for example:
[0039] In the broadband network, the user's broadband account, or an identification composed of the user's broadband account and the user's login password may be used as the user's user identification in the network, but not limited to.
[0040] In the mobile communication network, the mobile phone number of the user may be used as the identificat...
Embodiment 2
[0080] As an implementation example of the technical solution of this implementation, the access control table set in the mobile communication network may be shown in Table 1 below.
[0081] Table 1: Network access control strategy for network controlled users in the mobile Internet
[0082]
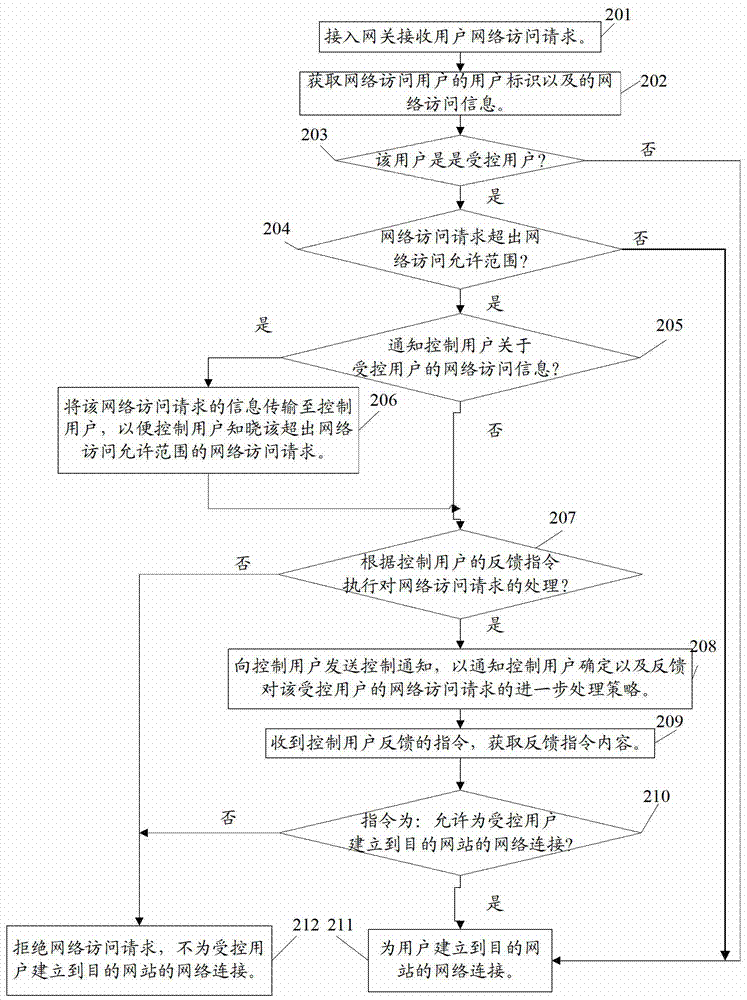
[0083] Step 201: the access gateway receives a user network access request.
[0084] The downlink gateway interface of the access gateway receives the user's network access request. In this mobile communication network, the access gateway is a mobile communication access gateway.
[0085] Step 202: Obtain the user ID and network access information of the network access user.
[0086] The user ID is the user's mobile phone number, which is the unique identification of the user in the network.
[0087] The network access information includes at least the address of the destination website, the time spent online on the day, the time spent online on the destination website, and the lik...
Embodiment 3
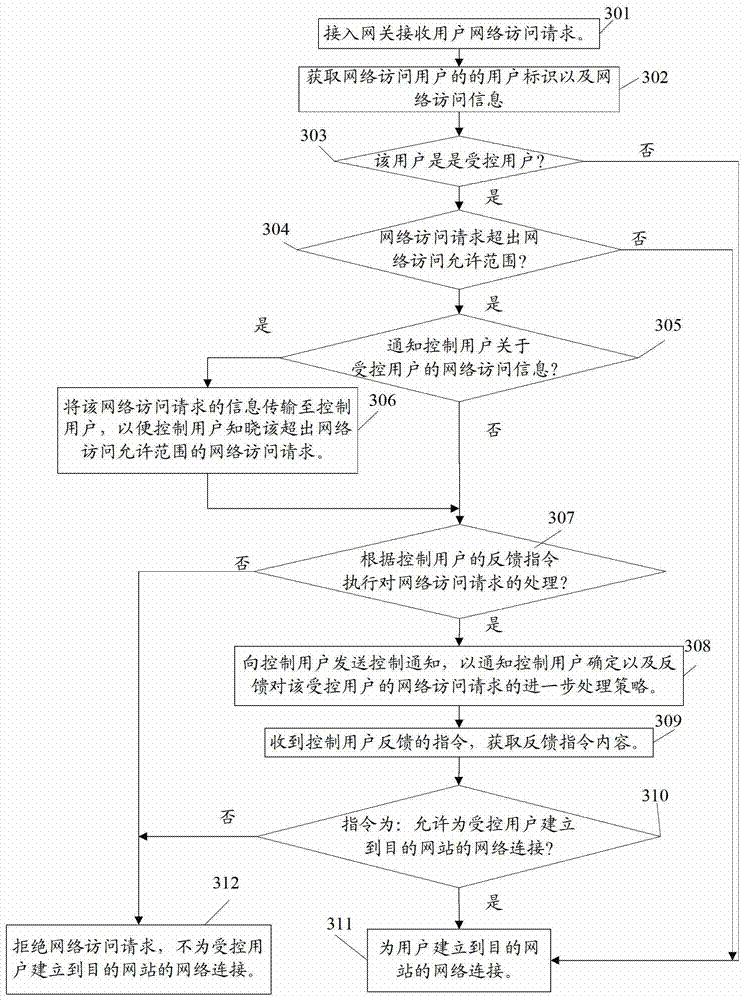
[0114] As an implementation example of the technical solution of this implementation, the access control table set in the broadband may be shown in Table 2 below.
[0115] Table 2: Schematic representation of network access control policies for network controlled users in broadband Internet
[0116]
[0117]
[0118] Generally, each family shares a unique Internet account, so the control user can directly use the broadband account and password to log in to the operator's website, set and store the Internet access control strategy on the interface provided by the website. In order to prevent other family members from modifying the access control list, it is also possible to set the user ID of the control user in the access control list, so that when anyone makes changes to the access control list, the network will send a control notification to the control user. The information notification can be SMS, MMS, Wap push and so on.
[0119] The network access control method o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com