An Asymmetric Encryption Method for Smart Electricity Interaction
An asymmetric encryption and encryption method technology, applied in the field of intelligent electricity interaction, can solve the problems of inapplicable smart grid deployment, etc., and achieve the effect of reducing decryption time, increasing the degree of deciphering, and facilitating communication channel transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
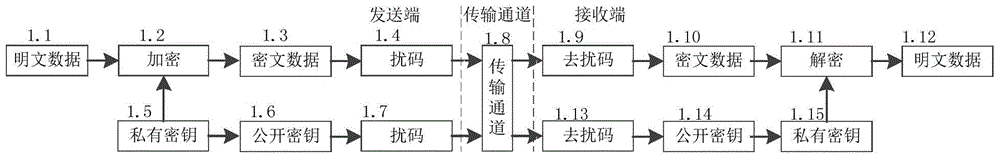
[0036] In Embodiment 1 of an asymmetric encryption method for intelligent electricity interaction provided by the present invention, as figure 1 A flow chart of this embodiment is shown. In this example:
[0037] 1.1 Plaintext data, intelligent electricity interaction information (corresponding to level 1), or national secret algorithm (SM1, SM2, SM3 or SM4) or international algorithm (DES, 3DES or RSA) key and corresponding encrypted plaintext data (corresponding level 3), or national secret algorithm (SM1, SM2, SM3 or SM4) or international algorithm (DES, 3DES or RSA) key encrypted plaintext data (corresponding to level 4), or national secret algorithm (SM1, SM2, SM3 or SM4) or international algorithm (DES, 3DES or RSA) key (corresponding to level 5);
[0038] 1.2 encryption, use the private key of "1.5 private key" to encrypt the data of "1.1 plaintext data";
[0039] 1.3 Ciphertext data, grouping the ciphertext data in groups of 8 bits;
[0040] 1.4 Add a scrambling co...
Embodiment 2
[0063] The remote communication channel of the power consumption information collection system of a rural comprehensive transformer user uses the electric power dedicated wireless network TD-LTE230MHz system as the transmission channel to solve the problem of fast and efficient encrypted transmission of the electric energy meter measurement information submitted remotely and automatically.
[0064] The SM1 (or RSA) key (corresponding to level 5) encrypted with the metering information of the electric energy meter automatically reported remotely is input into the system of the present invention as plaintext data. After encryption, scrambling, etc., use the electric power dedicated wireless network TD-LTE230MHz system as the transmission channel, and transmit it to the receiving end. After descrambling, decryption, etc., it will be restored to plaintext data: the metering of the electric energy meter submitted automatically remotely The SM1 (or RSA) key used to encrypt the messag...
Embodiment 3
[0066] The electricity consumption monitoring system of a 10kV special-purpose transformer industrial and commercial user, the remote communication channel adopts the leased public wireless network 3G system as the transmission channel, and solves the problem of fast and efficient encryption of information such as load control, abnormal monitoring and anti-theft alarm using the commercial key SM1 Encrypted transmission problem.
[0067] The commercial key SM1 and the corresponding encrypted plaintext data (corresponding to level 3) used for encryption of information such as load control, abnormal monitoring, and anti-theft alarm are input into the system of the present invention as plaintext data. After encryption, scrambling, etc., the leased public wireless network 3G system is used as the transmission channel, and it is transmitted to the receiving end. After descrambling, decryption, etc., it is restored to plaintext data: load control, abnormal monitoring and anti-theft al...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com