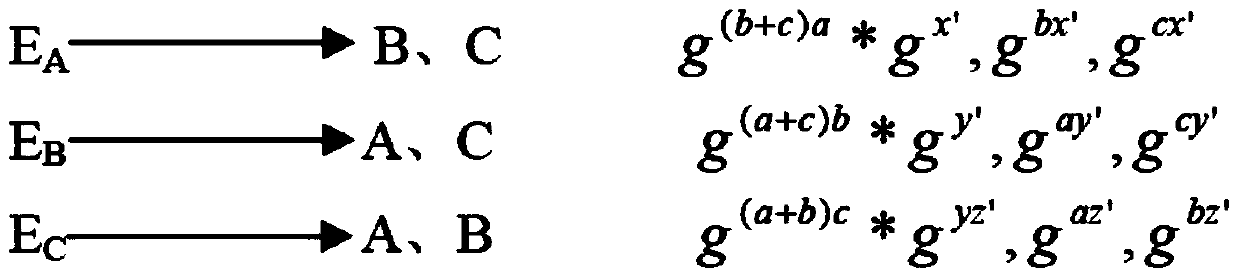Three-party authentication key agreement protocol generating method based on certificates
A technology of key agreement and three-party authentication, which is applied in the field of three-party secure communication in wireless networks, and can solve problems such as inapplicability to wireless networks and low computing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
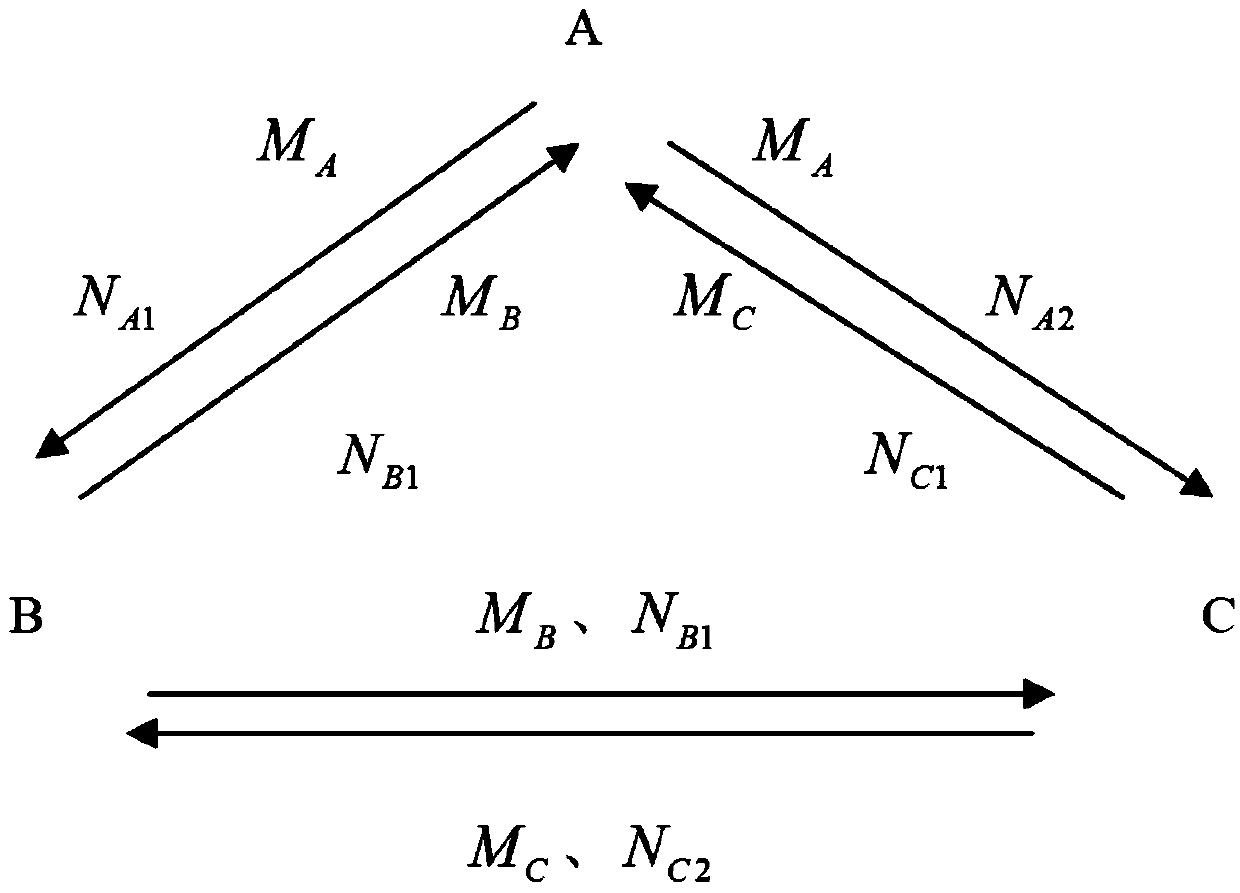
[0041] The present invention is described in further detail now in conjunction with accompanying drawing. These drawings are all simplified schematic diagrams, which only illustrate the basic structure of the present invention in a schematic manner, so they only show the configurations related to the present invention.
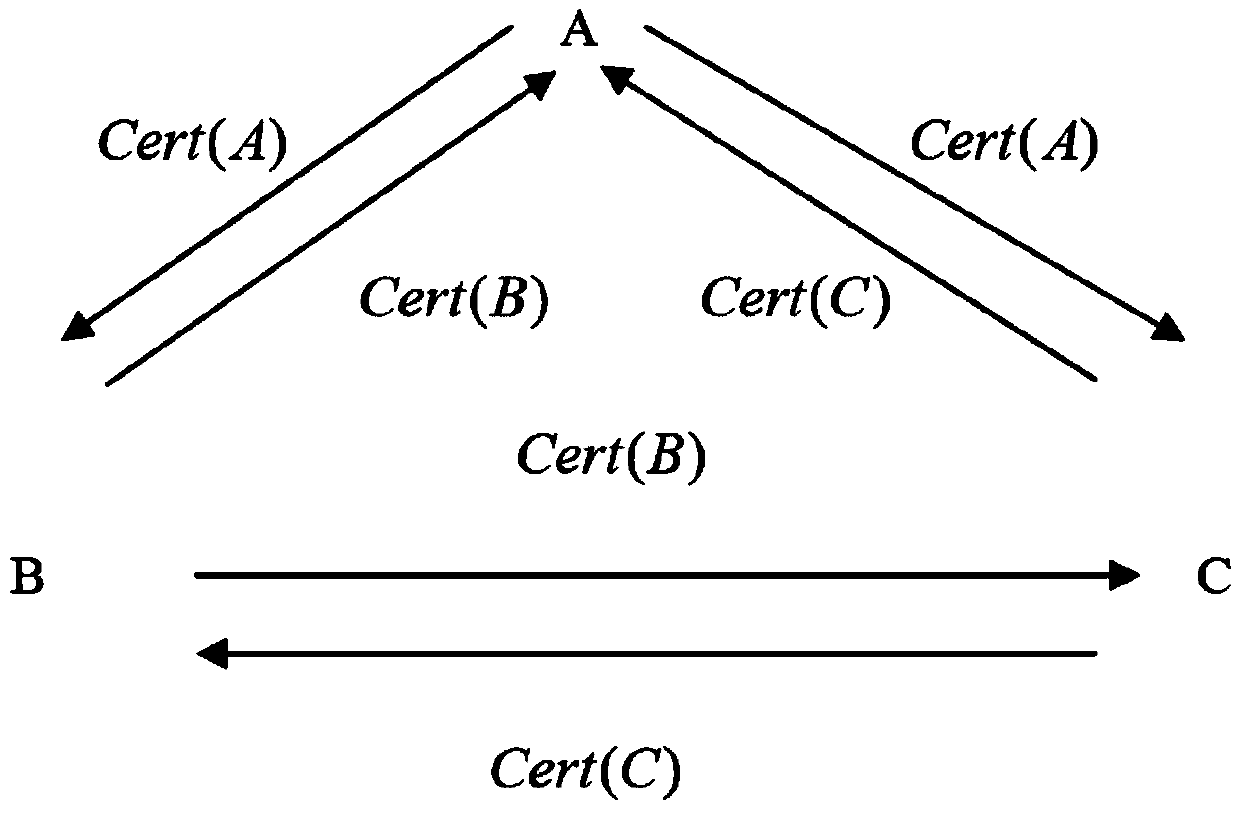
[0042]In the certificate-based three-party authentication key agreement generation method of the present invention, each of the three communication parties A, B, and C has a pair of keys (PK A ,SK A ), (PK B ,SK B ) and (PK C ,SK C ), where PK A 、PK B 、PK C is the public key of A, B, C, SK A 、SK B 、SK C are the private keys of A, B, and C. The authenticity of the key is attested by a certificate issued by a certificate authority. The forms of certificates of parties A, B, and C are as follows:
[0043] Cert(A)=A ,g,p,q,g a ,{ID A ,g,p,q,g a} sigCA >
[0044] Cert(B)=B ,g,p,q,g b ,{ID B ,g,p,q,g b} sigCB >
[0045] Cert(C)=C ,g,p,q,g c ,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com