Security management method for enterprise-level electronic documents
An electronic document and security management technology, applied in the field of information security, can solve problems such as stay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
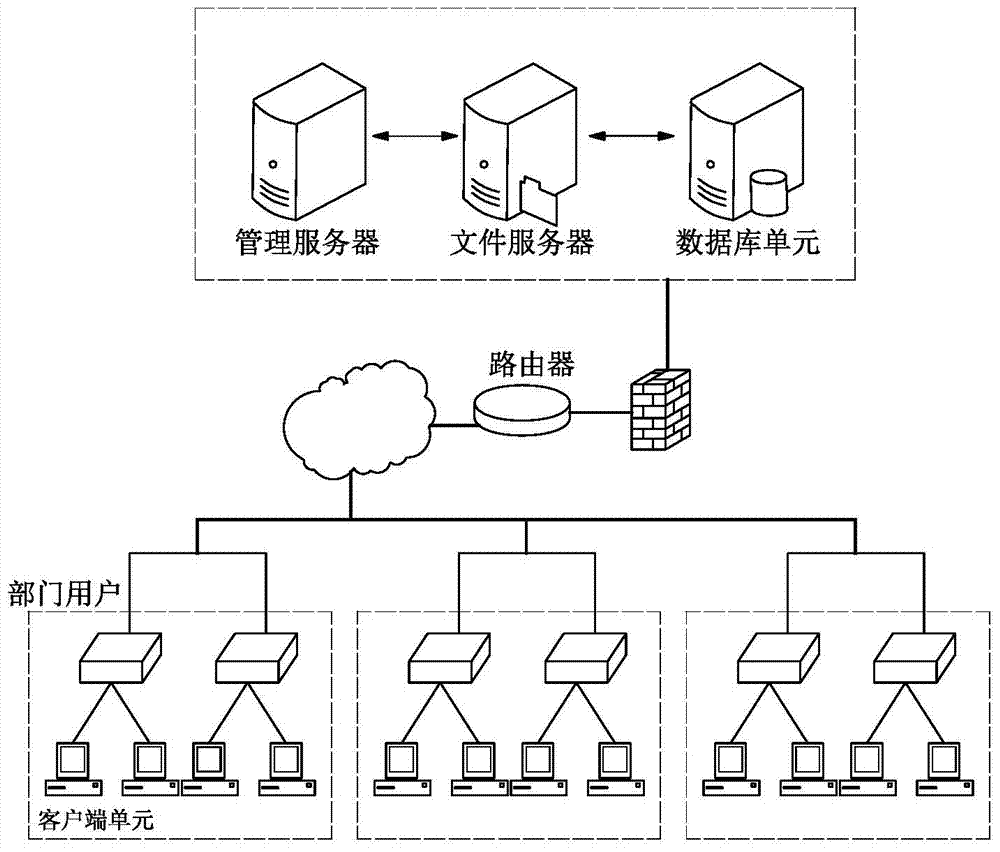
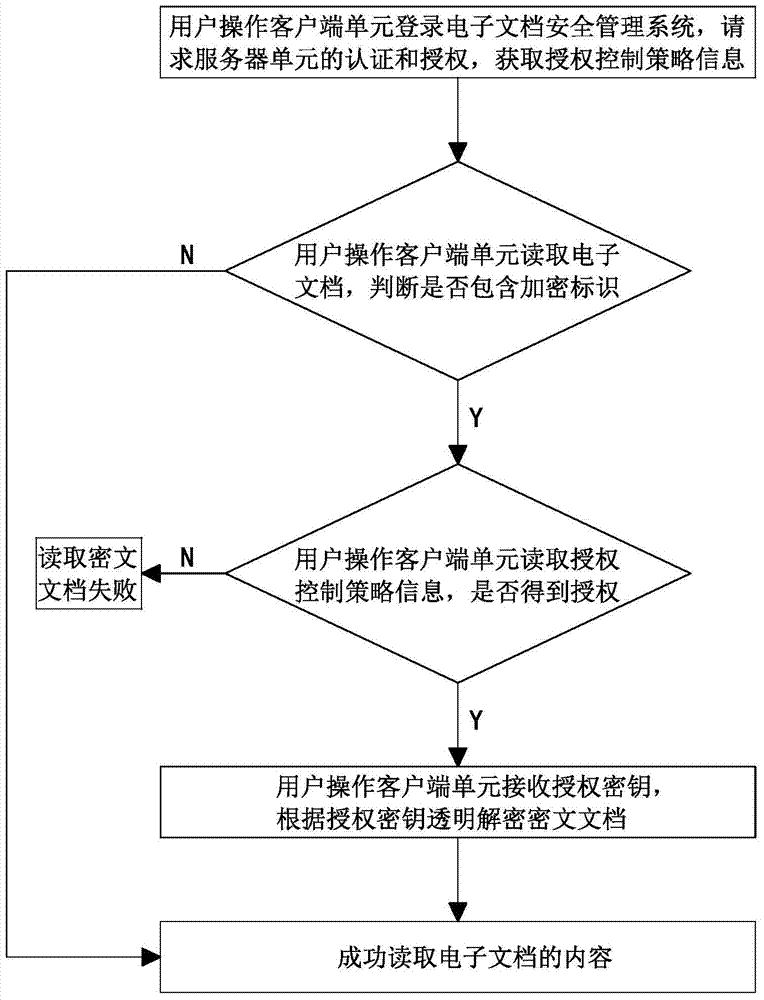
[0025] see figure 1 , figure 2 , a security management method for enterprise-level electronic documents, the security management method comprising the following steps:
[0026] (1) Steps for transparent decryption of electronic documents:
[0027] A. The user logs into the electronic document security management system, requests authentication and authorization, and requests authorization control policy information;
[0028] B. Judging the encryption status of the electronic document: when the user creates or opens an electronic document, if the electronic document does not contain an encryption mark, then the electronic document is defined as a new document or a plain text document; if the electronic document contains an encryption mark, then the electronic document is defined as encrypted document;
[0029] C. Obtain authorization: the user obtains the authorization control policy information and obtains the authorization to read the document, then go to step D; if the a...
Embodiment 2
[0055] This embodiment is improved on the basis of the first embodiment, and the content of the same part as the first embodiment will not be described repeatedly.
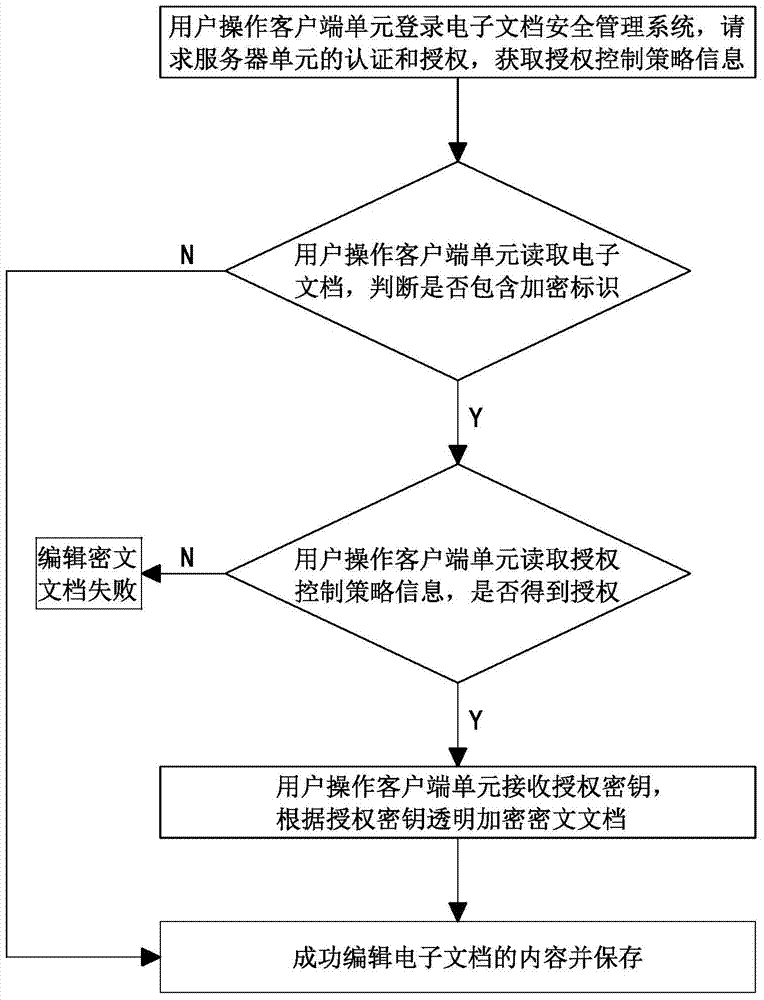
[0056] see image 3 , in this embodiment, the security management method of enterprise-level electronic documents also includes the following steps:
[0057] 2) Steps for transparent encryption of electronic documents:
[0058] E. The user obtains the authorization control policy information and obtains the authorization to write the document, then go to step F; if the authorization to write the document is not obtained, the ciphertext document cannot be edited;
[0059] F. Users who are authorized to write documents have the right to obtain the authorization key, and transparently encrypt the ciphertext document according to the authorization key and save it.
[0060] In this embodiment, the user operates the client unit to read the authorization control policy information, and if authorized to write the docume...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com