Radio frequency identification two-way authentication method based on ellipse curve
An elliptic curve and two-way authentication technology, applied in the field of information security, can solve problems such as high computational complexity, poor security performance, and high consumption of storage resources, and achieve the effects of reducing resources, improving efficiency, and reducing data length
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
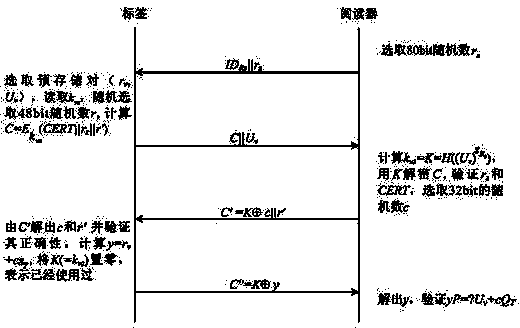
[0040] The two-way authentication method between the tag and the reader in the RFID system proposed by the present invention is based on the elliptic curve cryptography in public key cryptography, and is known to be implemented based on the elliptic curve on the finite field GF(q), where q is The length is the order of a finite field of 160 bits, and the base point on the elliptic curve is P.
[0041] The parameters required in the authentication process include: the identity ID of the reader R , The public key Q of the reader R =s R P, the private key of the reader s R , The identity ID of the label T , The tag's public key Q T =s T P, the private key of the label s T , The certificate of the label CERT, where the reader public key Q R The length is 32bit, the tag public key Q T The length is 32bit.
[0042] Reference figure 1 , The two-way authentication process of the present invention is as follows:
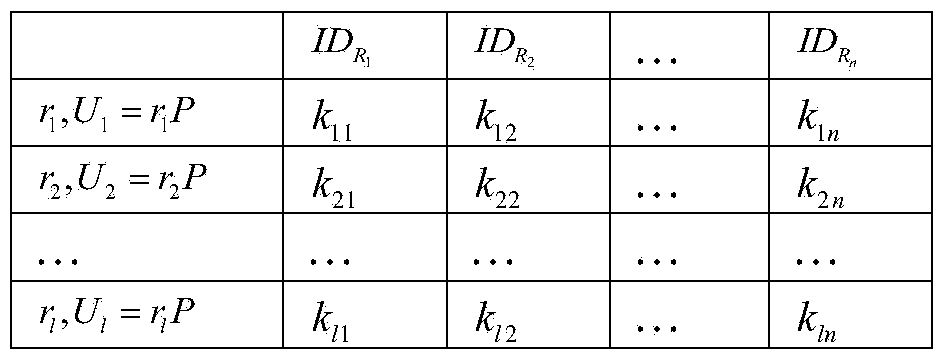
[0043] Step 1. The trusted third party injects pre-stored data into the tag.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com