Security access control method for chip storage circuit
A security access control and access control technology, applied in the direction of preventing unauthorized use of memory, digital data authentication, etc., can solve problems such as software attacks and false comparisons, improve security, improve flexibility, and solve anti-software attacks Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
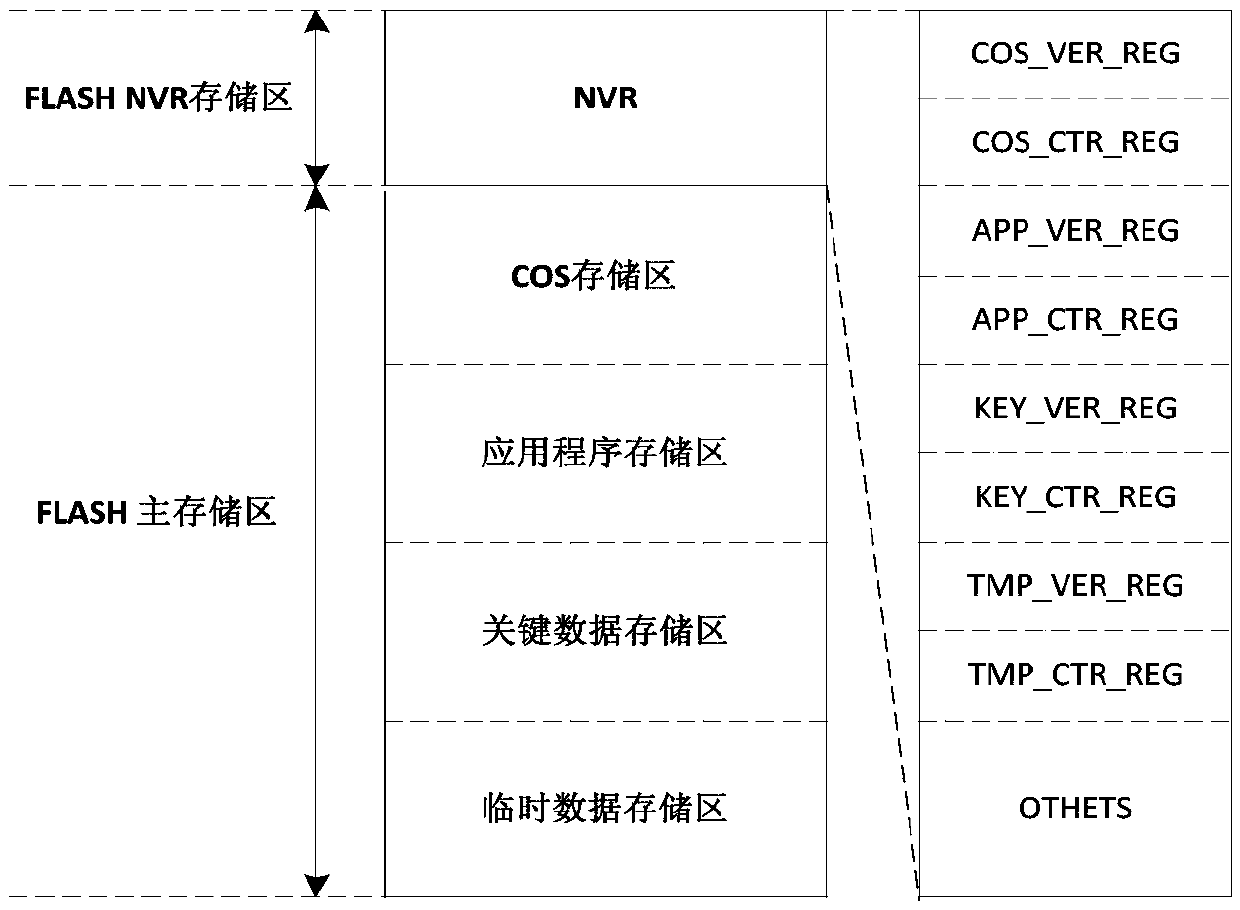
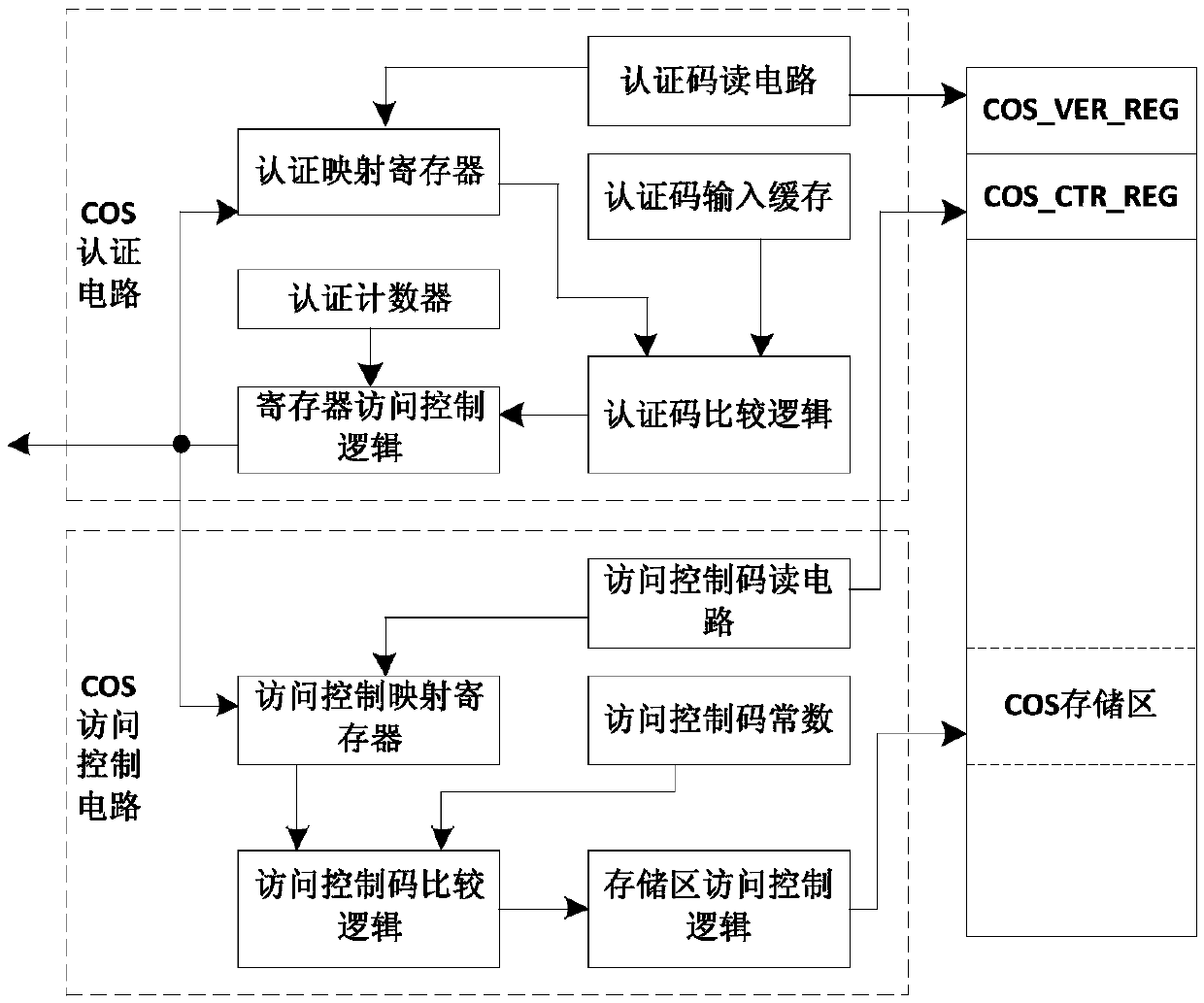
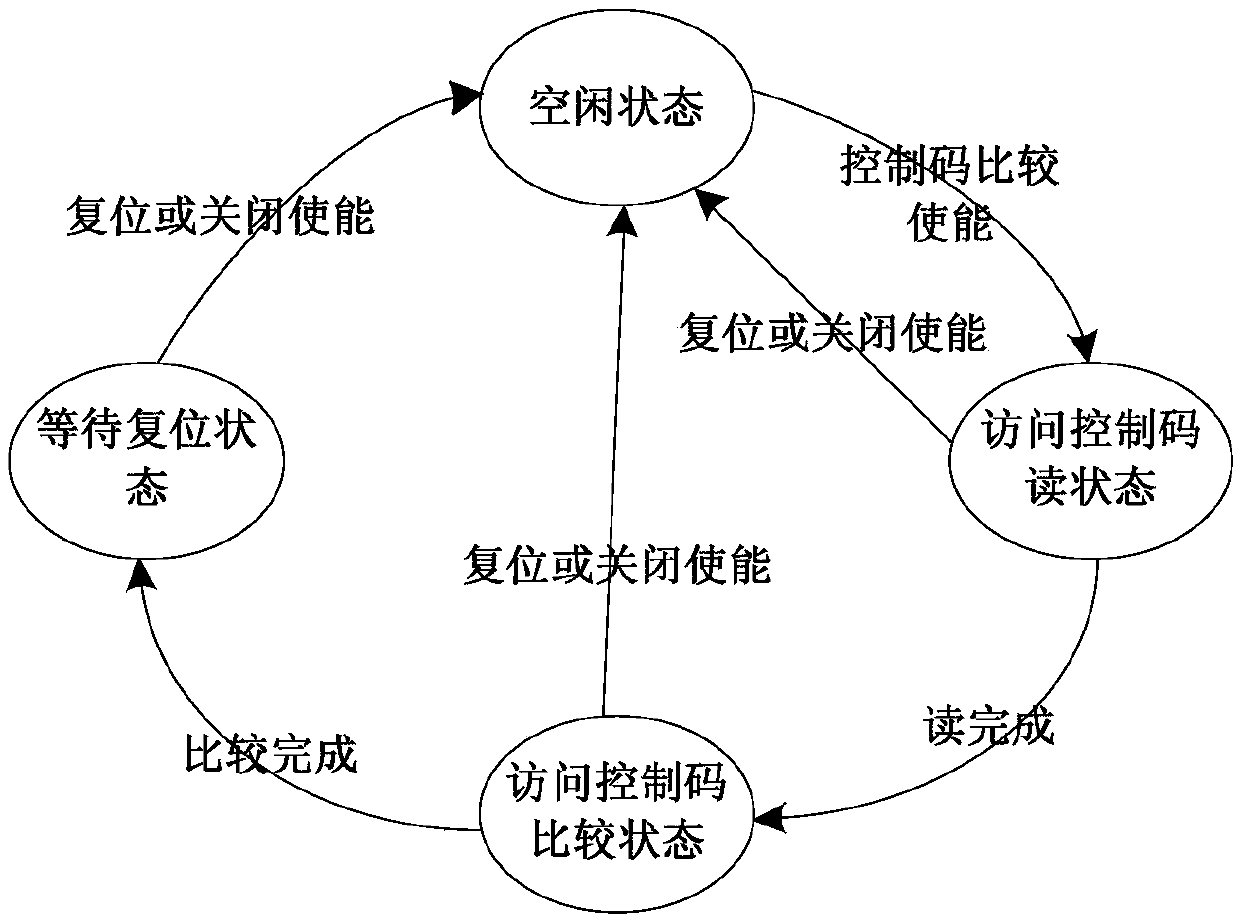
[0020] The invention provides a pure hardware security protection solution based on identity authentication and access control control for chip storage circuits. The invention adopts two-level authentication of identity authentication and access control code authentication, and simultaneously uses pure hardware circuits to realize identity authentication and access The comparison of the control code not only improves the flexibility of authorized access control, but also improves its security.
[0021] In the present invention, the storage circuit is partitioned first, and then an independent identity authentication and access control circuit is set for each partition to complete the reading and comparison operation of the identity authentication code and the access control code, and output corresponding control signals. After the identity authentication is passed, the operator has the right to update the identity authentication code itself and rewrite the access control code, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com