Method and device for controlling access security
An access security control and access control technology, which is applied in the field of social network services, can solve the problems of user privacy leakage and other issues, and achieve the effect of intelligent privacy policy setting, expansion flexibility and robustness, and more privacy policy setting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In the following description, for illustrative purposes, many specific details are set forth in order to provide a comprehensive understanding of one or more embodiments. However, it is obvious that these embodiments can also be implemented without these specific details. In other examples, for the convenience of describing one or more embodiments, well-known structures and devices are shown in the form of block diagrams.
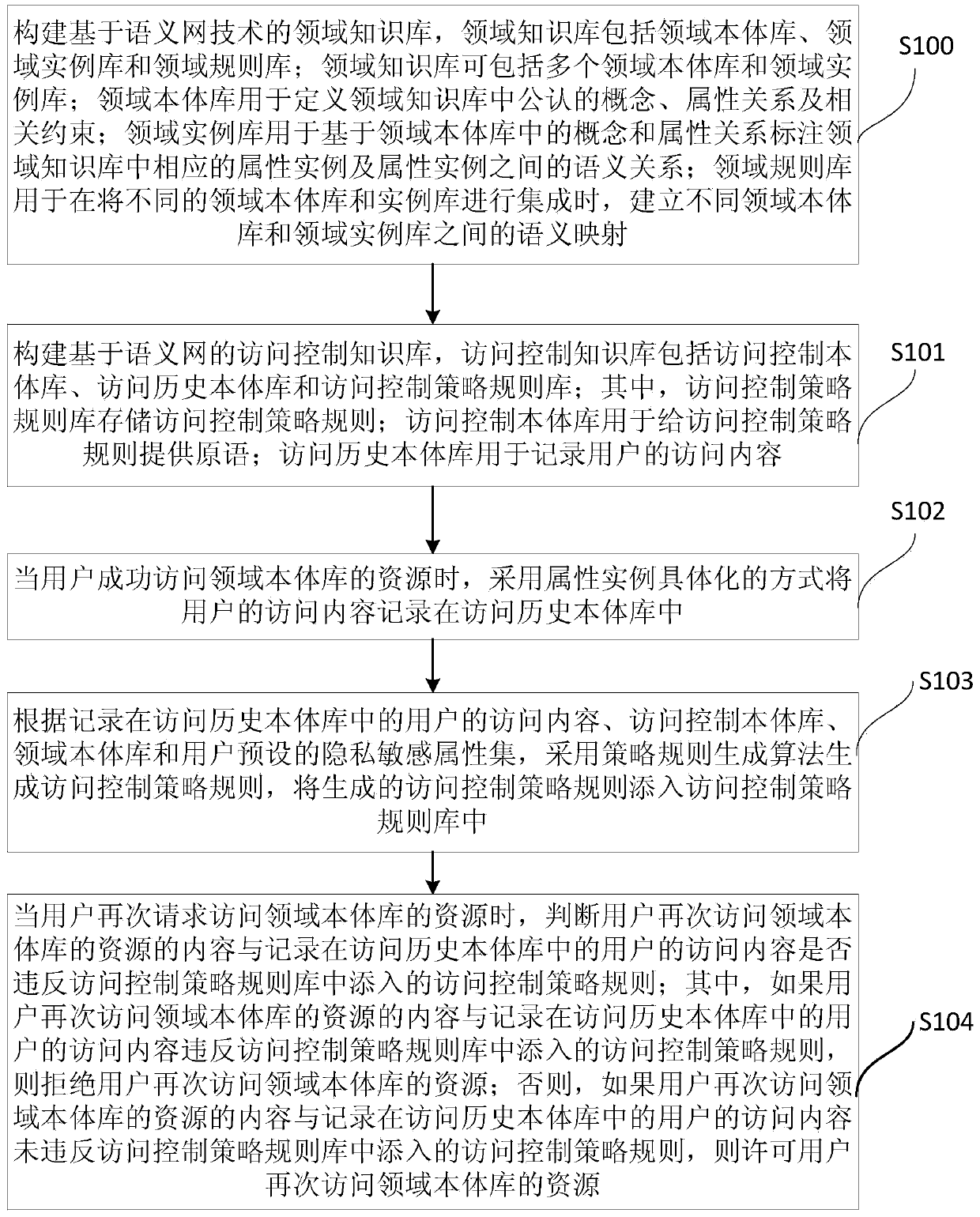
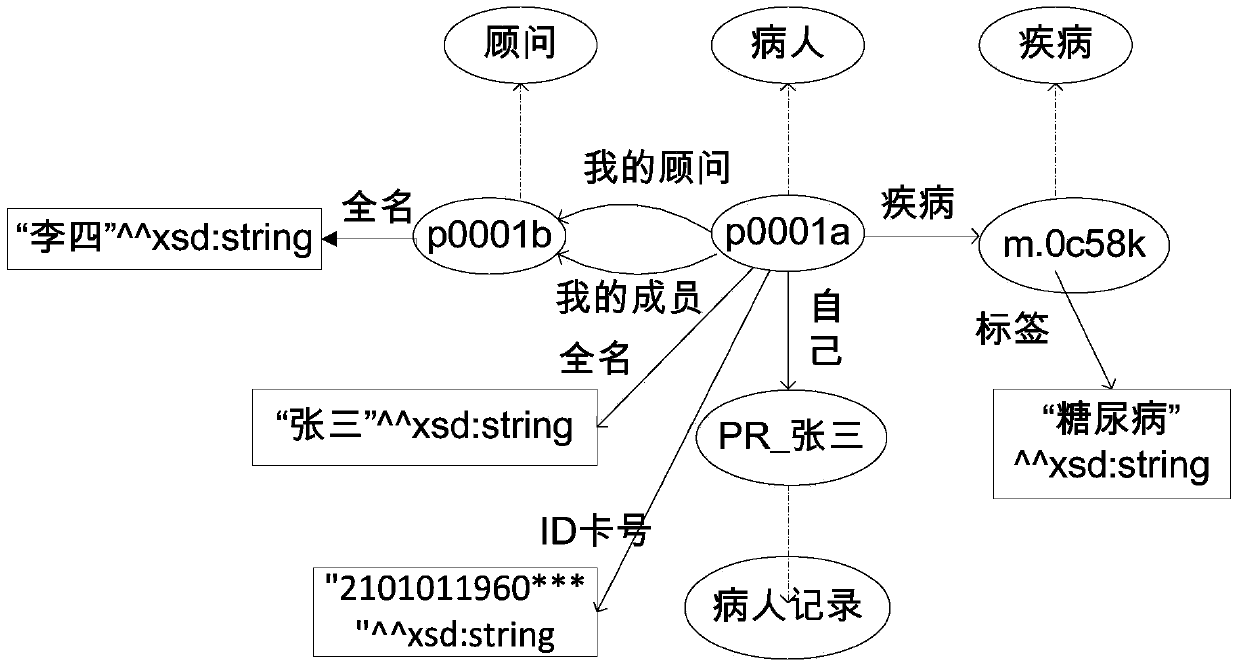
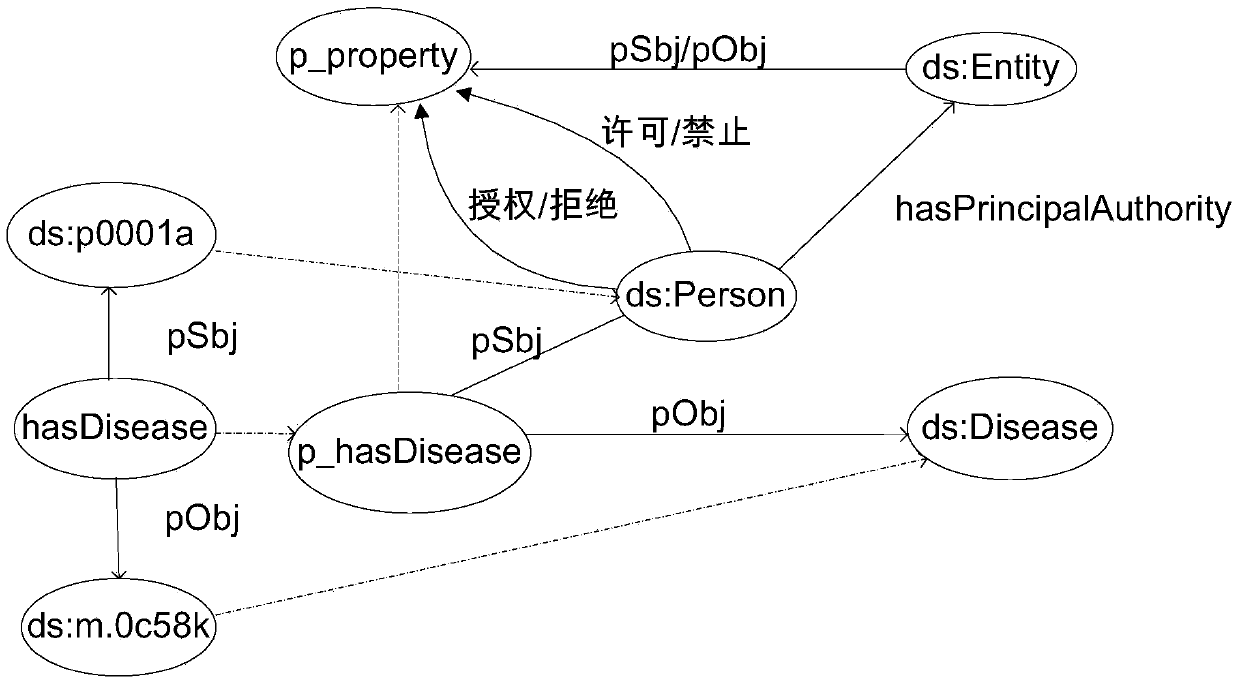
[0045] In order to solve the above-mentioned problems, the present invention uses the specific method of attribute instances to record the content of each user's successful access; according to the user's preset security / privacy sensitive attribute set, domain ontology, access control ontology, and access history ontology, and Based on the policy rule generation algorithm, generate access control policy rules; based on the user's historical access content and the user’s current access request, perform context-related constraint checking. If the access r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com