Audio Access Mobile Payment Communication Method Based on Security Algorithm
A security algorithm and mobile payment technology, applied in payment architecture, computing, user identity/authority verification, etc., can solve problems such as poor compatibility, hidden safety hazards, and poor flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
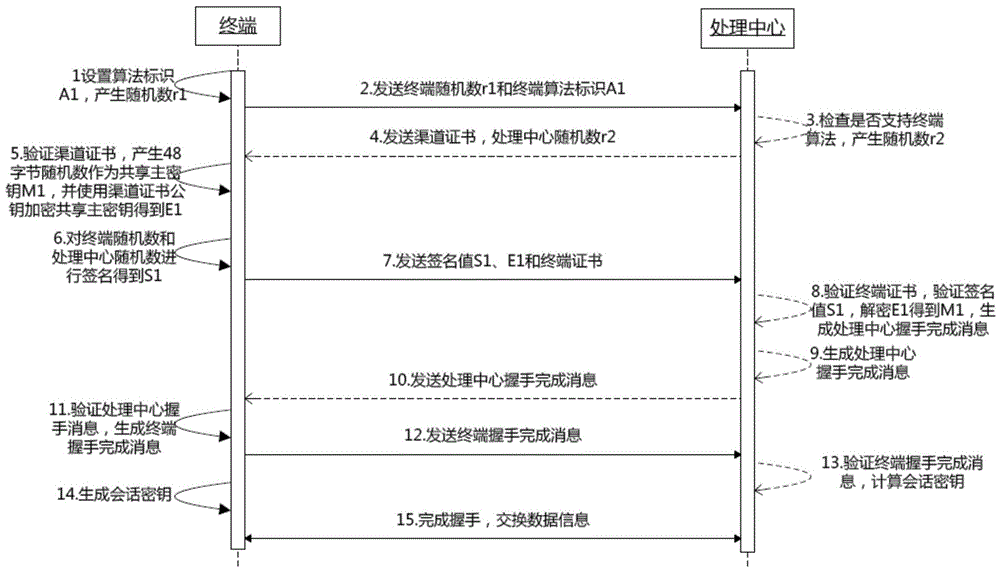
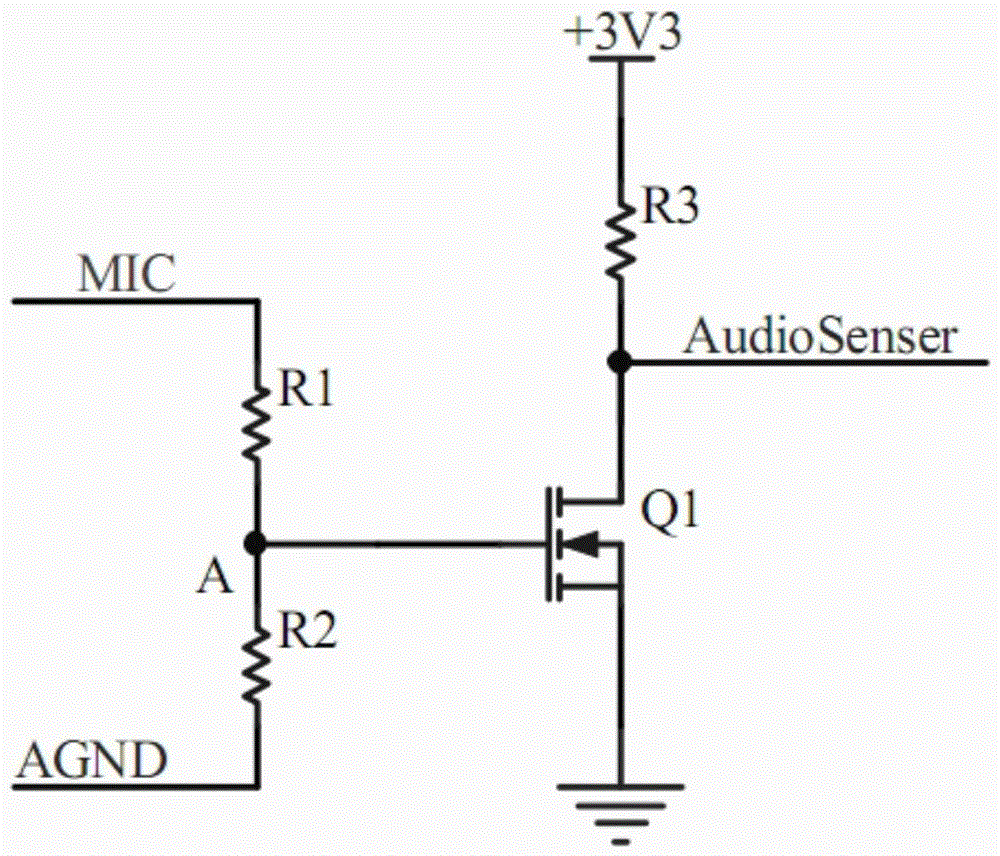
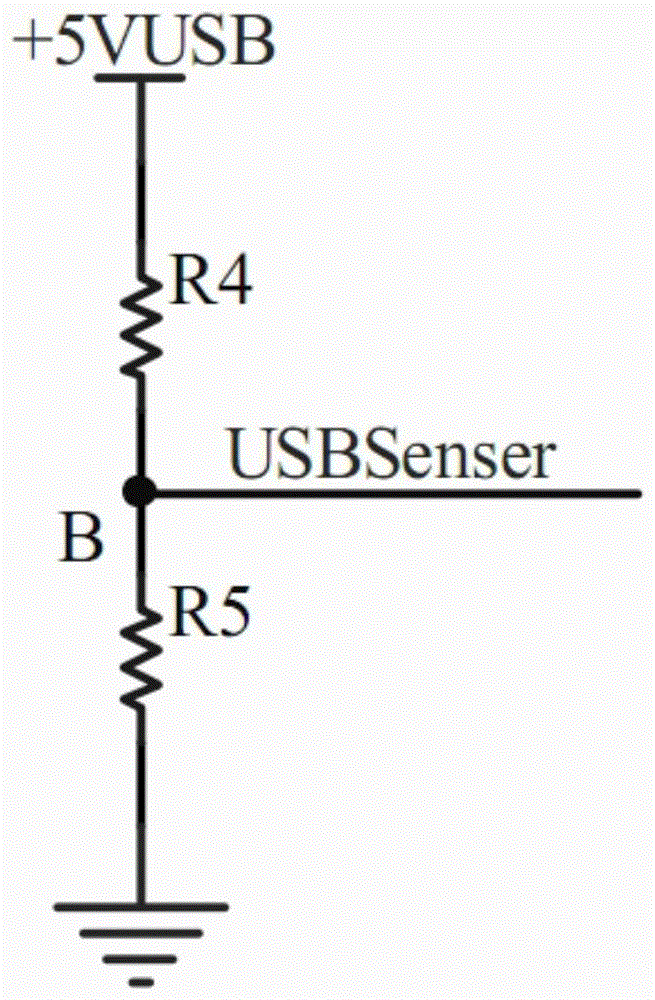
[0138] Such as Figure 1-9, with the continuous development of online banking business, more and more individual users have realized its simplicity and convenience. On PC terminals that can be connected to the Internet, businesses such as account inquiries and transfers and remittances can be handled at any time, which facilitates people's lives, reduces the pressure on bank counters, and reduces the bank's operating costs. However, with the rampant crimes of magnetic stripe cards, the security flaws of magnetic stripe cards have become more and more prominent, and it has become an inevitable fact that financial IC cards will replace magnetic stripe cards. With the popularization of mobile smart devices such as smartphones, tablet computers, PDAs, etc., fully utilize and reflect the powerful functions of mobile smart terminals and the mobile Internet to create an invisible online security payment system, and allow users to truly experience convenience and security mobile paym...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com