Method and system for rapidly detecting fishing website
A technology for phishing websites and websites, applied in transmission systems, special data processing applications, instruments, etc., can solve the problem of unable to download webpage content with accurate webpage content, etc., and achieve the effect of fast and accurate detection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
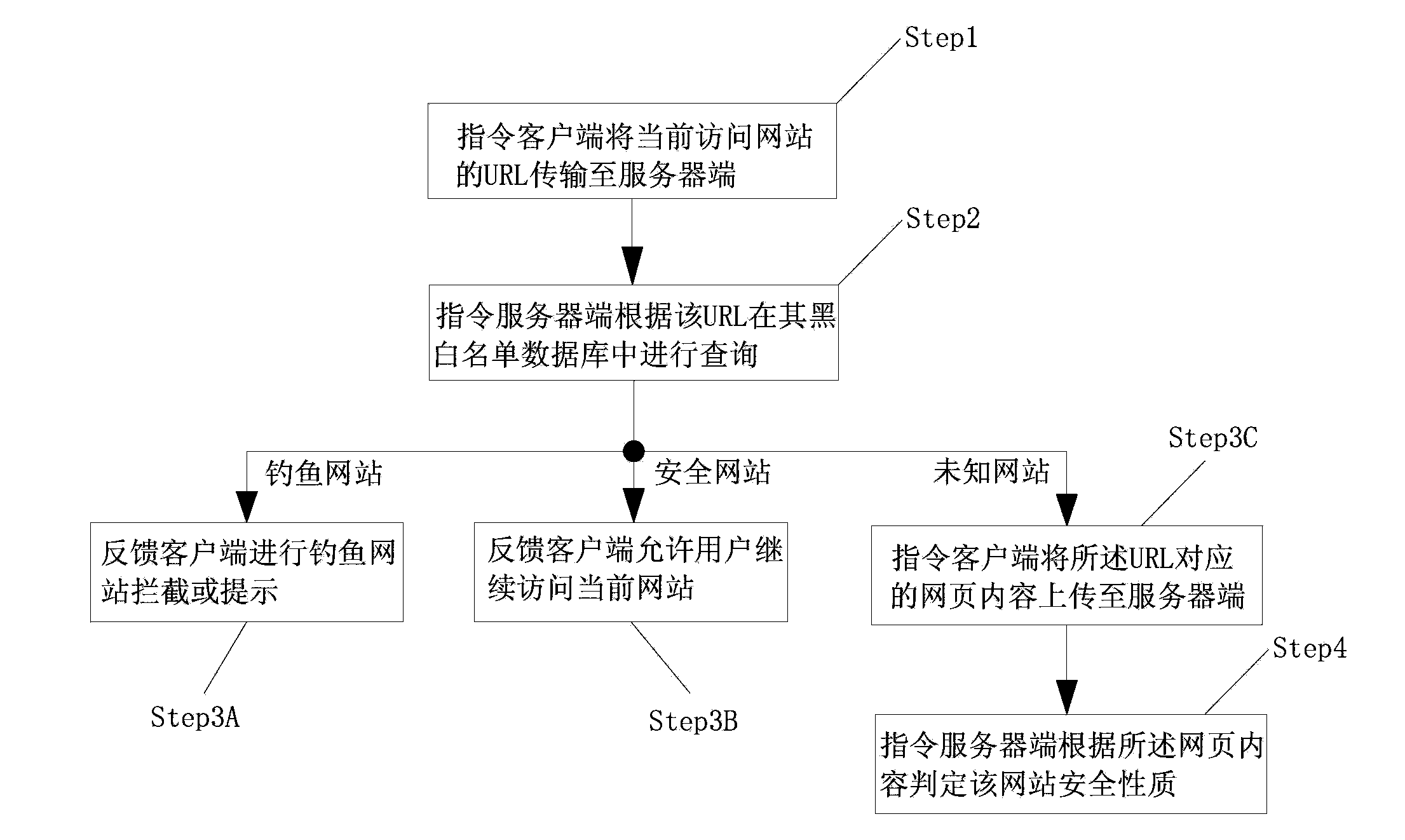
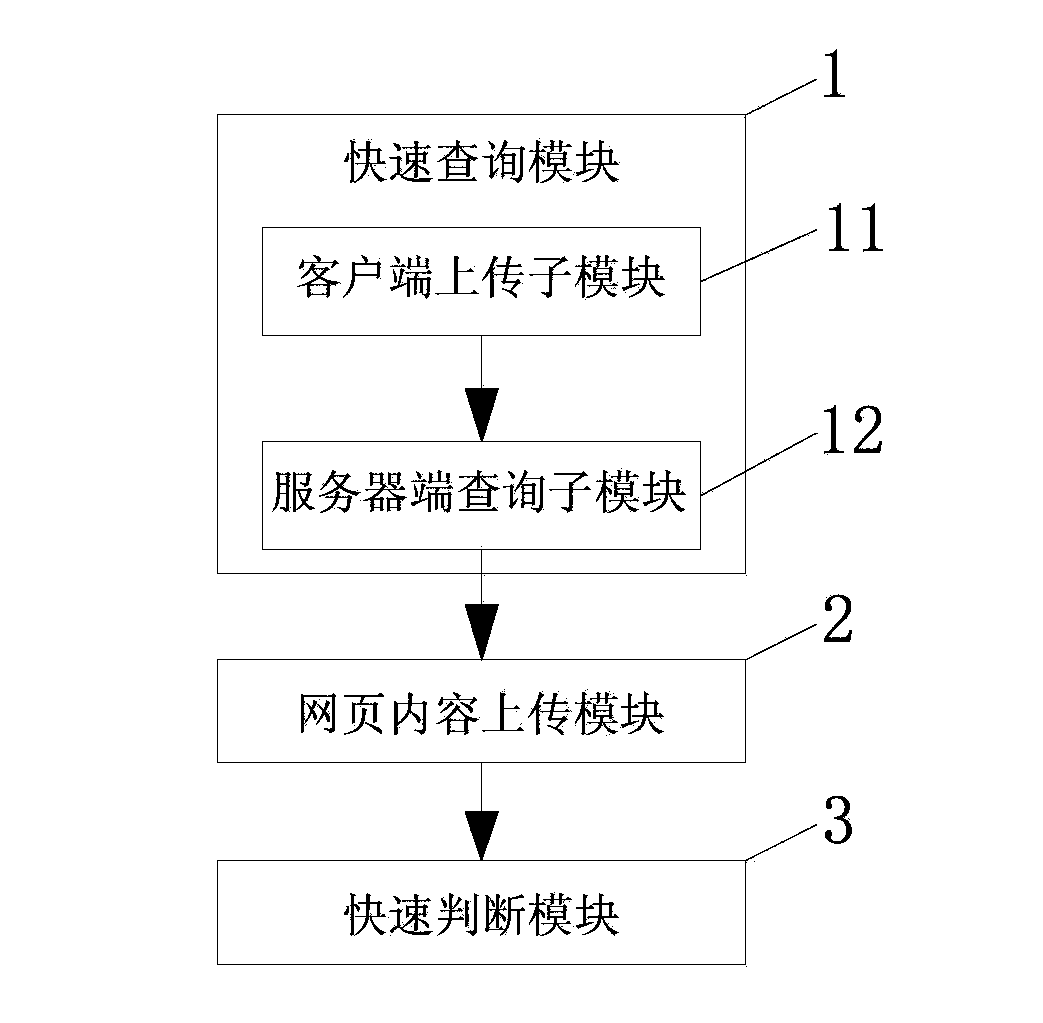
[0041] Such as figure 1 As shown, the present embodiment discloses a fast detection method of a phishing website, which is characterized in that it comprises the following steps:
[0042] Step1: Instruct the client to transmit the URL of the currently visited website to the server;
[0043] Step2: Instruct the server to query in its black and white list database according to the URL, the black list database stores the confirmed URL of the phishing website, and the white list database stores the URL of the verified safe website;
[0044] Step3A: If it is in the blacklist database, the feedback client will intercept or prompt the phishing website, that is, if the query result is a phishing website, it will intercept the user’s continued access behavior or prompt the user that the website is a phishing website. It is up to the user to decide whether to continue to visit;
[0045] Step3B: If it is in the whitelist database, the feedback client allows the user to continue to visi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com