Route construction method with strong source position privacy protection capacity
A technology of privacy protection and construction method, applied in the direction of reducing energy consumption, energy-saving ICT, advanced technology, etc., can solve the problems of difficult to use false source strategy and large energy consumption of false source
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
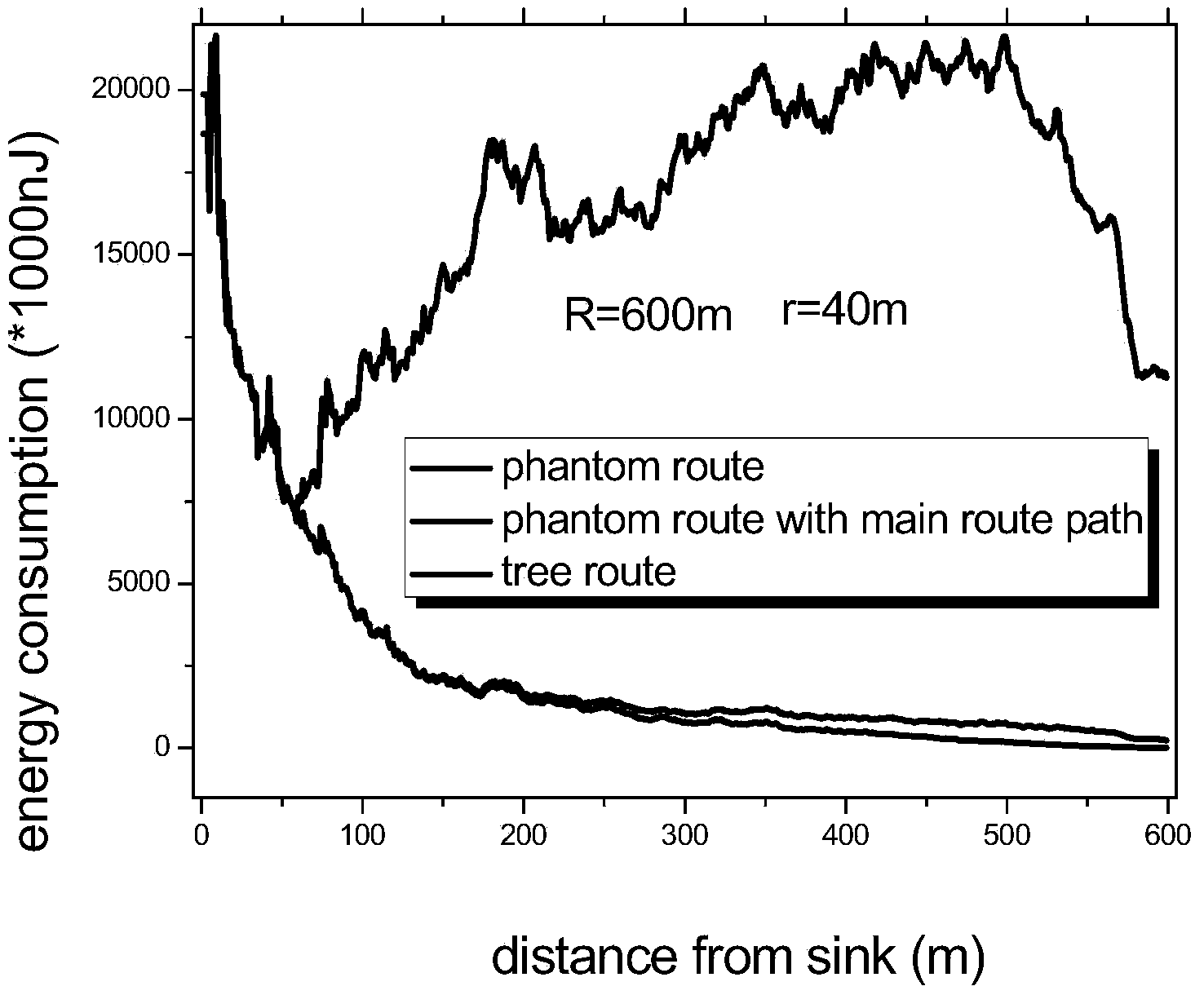
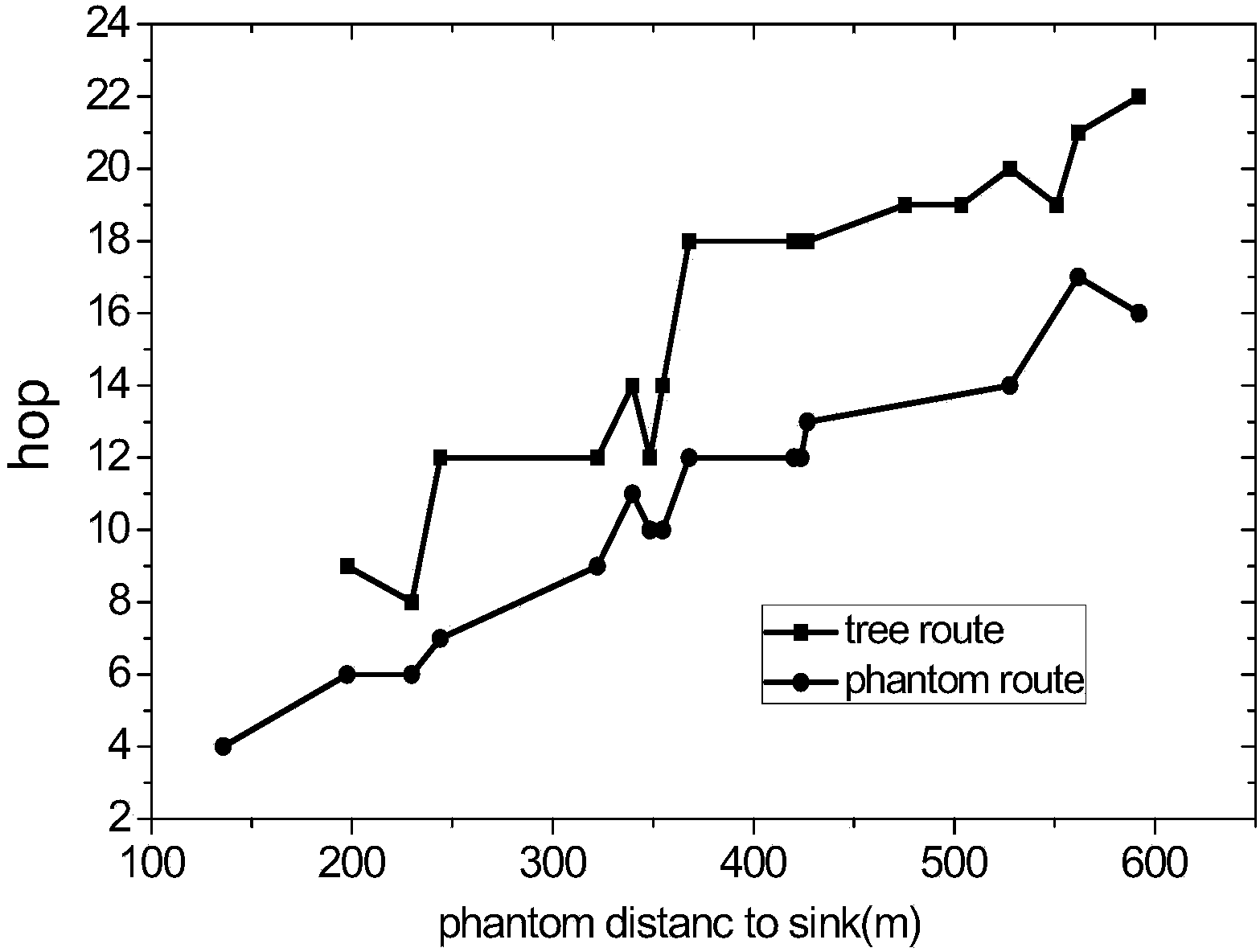
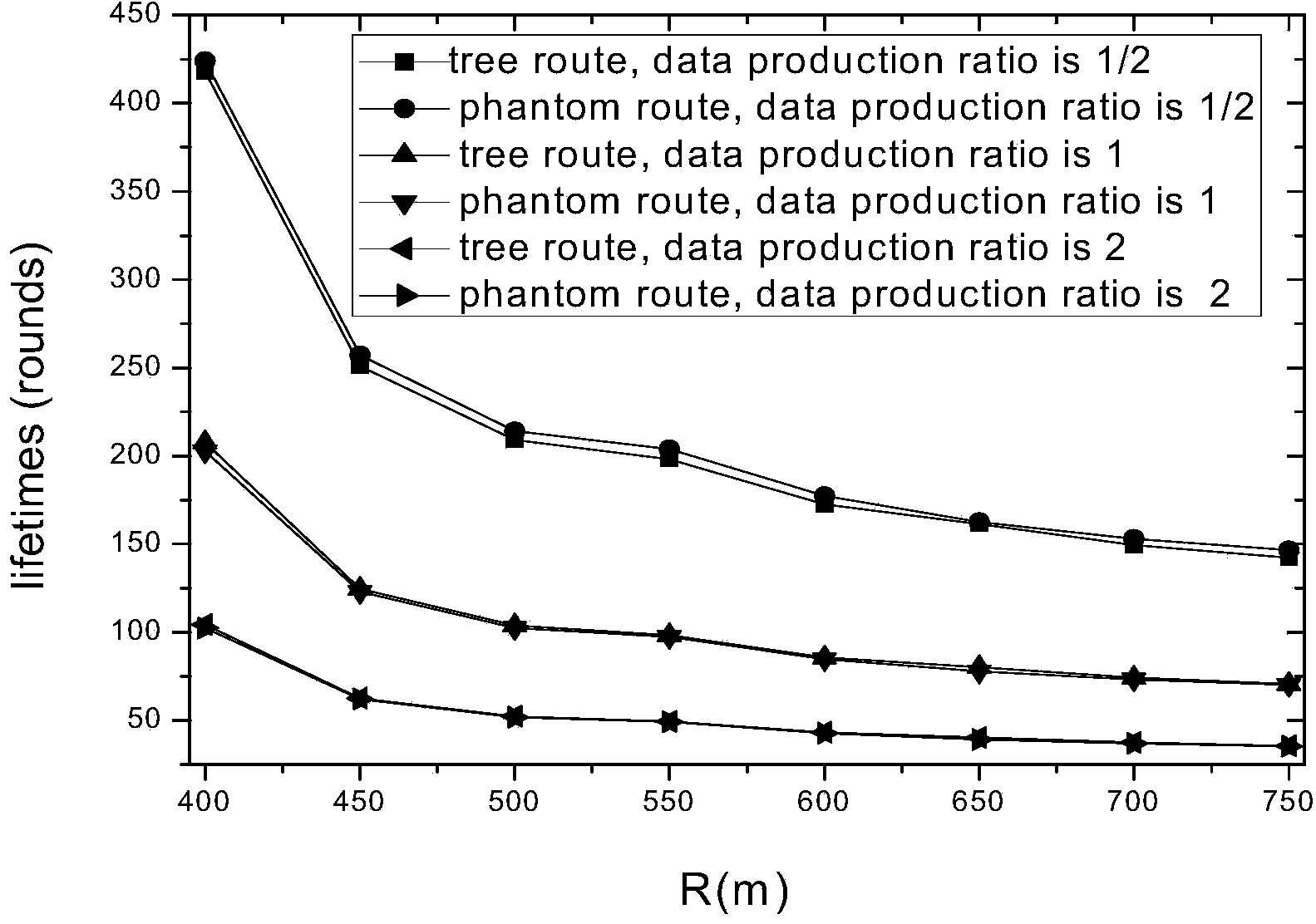
[0039]A routing construction method with strong source location privacy protection capability. First, create a phantom node P according to the existing phantom routing strategy; then, according to the set hop A branch route, wherein, A is an intermediate node, T is a network boundary node, Φ≥2; then, with the intermediate node A as the initiating node, as the initiating node, create a main trunk routing path that reaches the base station and reversely reaches the network boundary; Finally, create interfering branch paths with nodes on the main trunk routing path.
[0040] The tree routing path formed according to the method of the present invention is as follows Figure 7 shown.
[0041] The interference branch path is created outside the one-hop range of the base station.
[0042] The number k of interference branch paths created by the node located...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com