Honey pot mechanism and method used for collecting and intercepting internal storage behaviors of computer
A computer and honeypot technology, applied in computer security devices, calculations, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
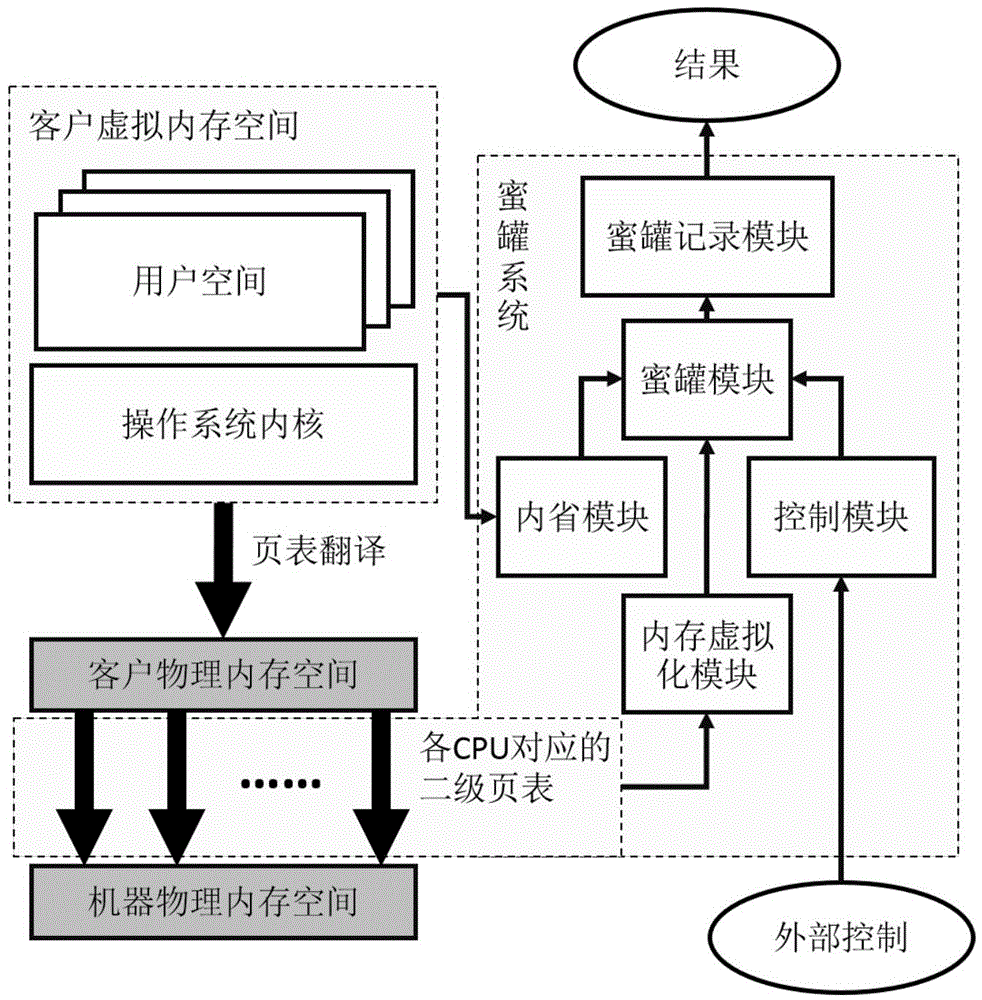
[0062] figure 1 Shown is a schematic structural diagram of the present invention, including a honeypot module, a honeypot recording module, an introspection module, a control module and a memory virtualization module.
[0063] This embodiment adopts the hardware virtualization technology, wherein the memory virtualization module uses the EPT technology in Intel VT to control the conversion from the client physical memory space to the real physical memory space. In order to independently control the write permissions in each CPU during the running phase, the memory virtualization module establishes a secondary conversion page table equal to the number of CPUs, and configures the EPTP pointer in each CPU as the PML4 page address of each page table. The memory virtualization module maps guest physical addresses to the same real physical addresses. So that after the memory virtualization module is turned off, the guest virtual machine can still run normally. The memory virtualiz...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com