A Composite Chaotic Image Encryption Method Using Plaintext to Construct Initial Key
An initial key and plaintext image technology, applied in image data processing, image data processing, instruments, etc., can solve the problems of encryption algorithm key not being extremely sensitive, unable to resist differential attacks, long encryption time period, etc., to achieve differential resistance Attacks, enhanced algorithm sensitivity, and increased encryption effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] In order to make the present invention more comprehensible, preferred embodiments are described in detail below with accompanying drawings.
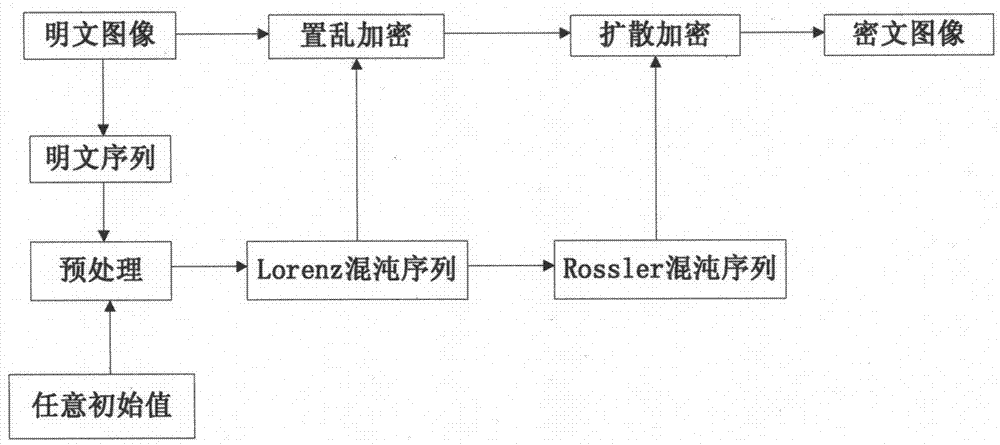
[0024] The invention provides a compound chaotic image encryption method for constructing an initial key in plain text, the steps of which are as follows:
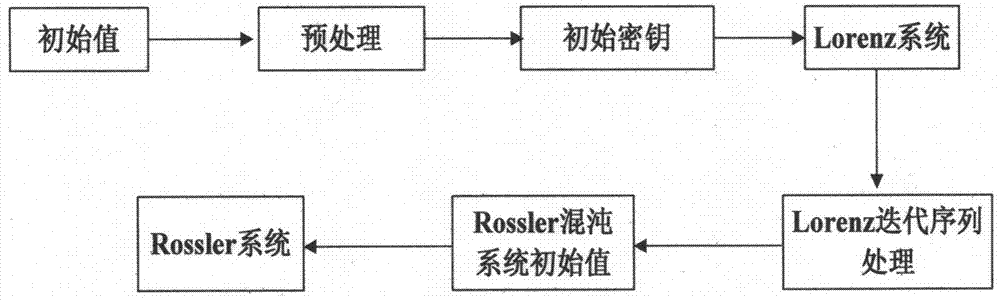
[0025] Step 1. Realize image preprocessing according to plaintext image pixel values and initial given values, and determine iteration initial values, including:
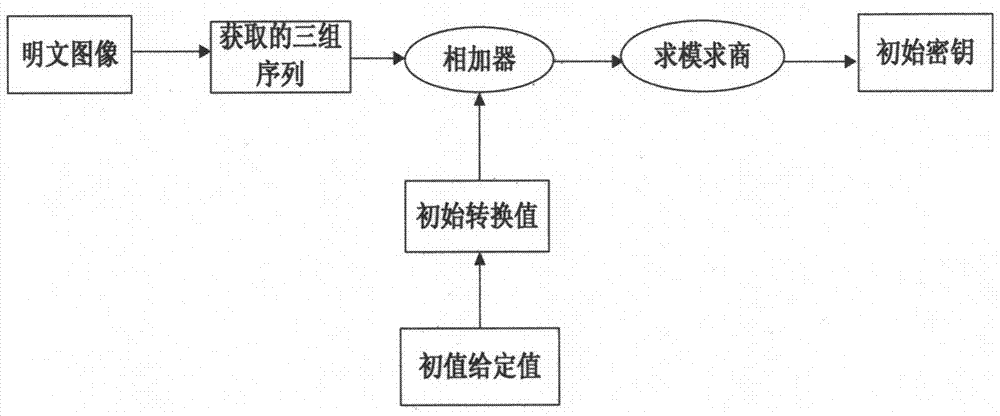
[0026] Step 1.1, take any horizontal, vertical and diagonal arbitrary majority of plaintext image pixels to form three series of numbers;
[0027] Step 1.2. Add the numbers in the three series obtained in step 1.1 to obtain three numerical values, and then calculate the modulus of 1000 to obtain R, C, and H;
[0028] Step 1.3, take three initial values arbitrarily, denoted as X 10 , X 20 , X 30 , the value range of each initial value is between [-1, 1], and it is accurate to four decimal places;
[0029] St...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com