Method for protecting installed software on Android platform
A software protection and installed technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as insufficient protection methods, security risks of verification mechanisms, etc., and achieve the effect of avoiding complex problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
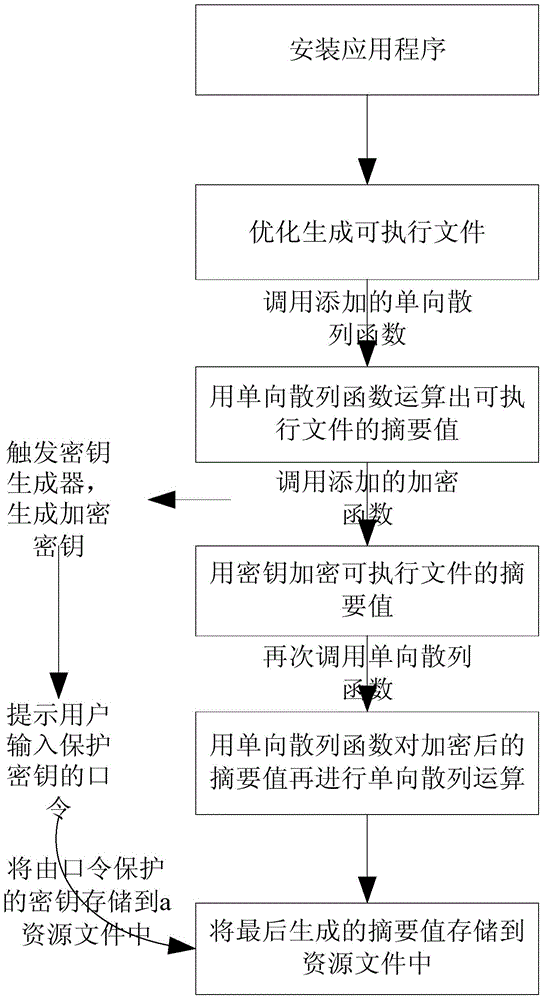
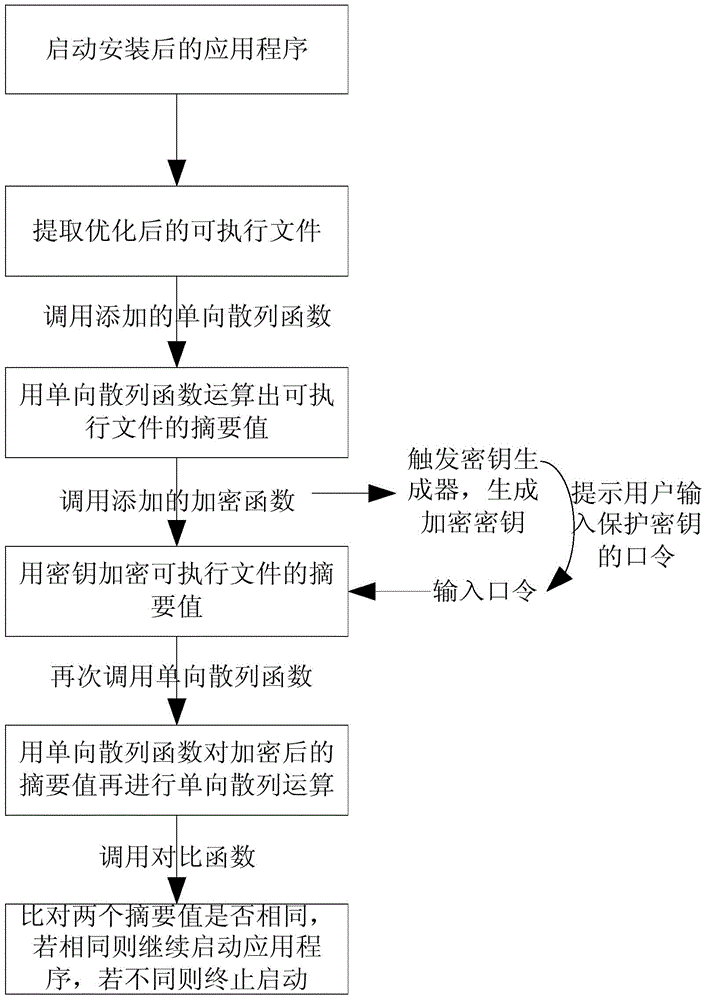
[0031] A method for protecting installed software on an Android platform, comprising the steps of:
[0032] (1) The premise and initialization of the method
[0033] ① This method considers that the applications downloaded from the application store when installing the application are safe and do not contain any malicious code.
[0034] ②When the application is started, the system will find the class to which the application is loaded, and add a one-way hash function, key generator function, encryption function, and prompt the user to enter the protection encryption key in the class that loads the application. functions and comparison functions.
[0035] Now a brief introduction to several technologies and corresponding algorithms:
[0036] Symmetric encryption technology: Symmetric encryption algorithms are also called traditional cryptographic algorithms. In most symmetric encryption algorithms, the encryption key and decryption key are the same. The main symmetric encryp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com