Method for detecting hardware Trojan based on active optical watermark
A hardware Trojan detection, active optics technology, applied in electronic circuit testing and other directions, can solve the problems of small scale, small change range, difficult to determine, etc., to reduce the test complexity and reduce the effect of noise.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be further described below in conjunction with specific drawings and embodiments.
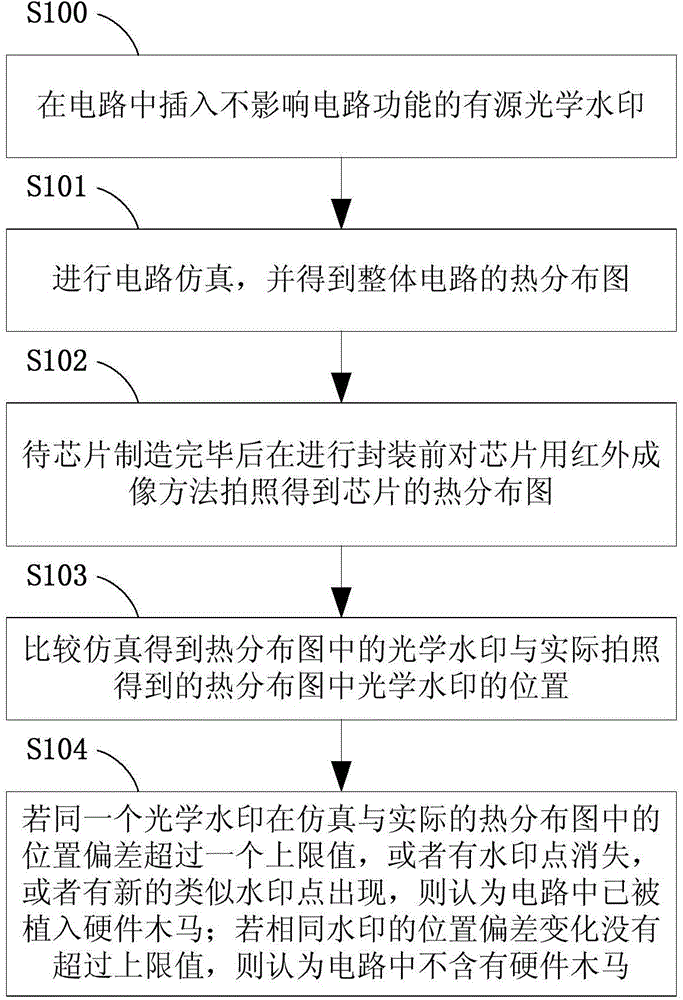
[0041] Hardware Trojan horses are formed by artificially adding, deleting or modifying the original circuit structure inside the chip during uncontrollable links such as circuit design and manufacturing.
[0042] Traditional detection methods, such as removing the circuit package and taking pictures layer by layer, and comparing it with the original circuit layout; or logic testing and bypass analysis are methods to detect the hardware Trojan itself.
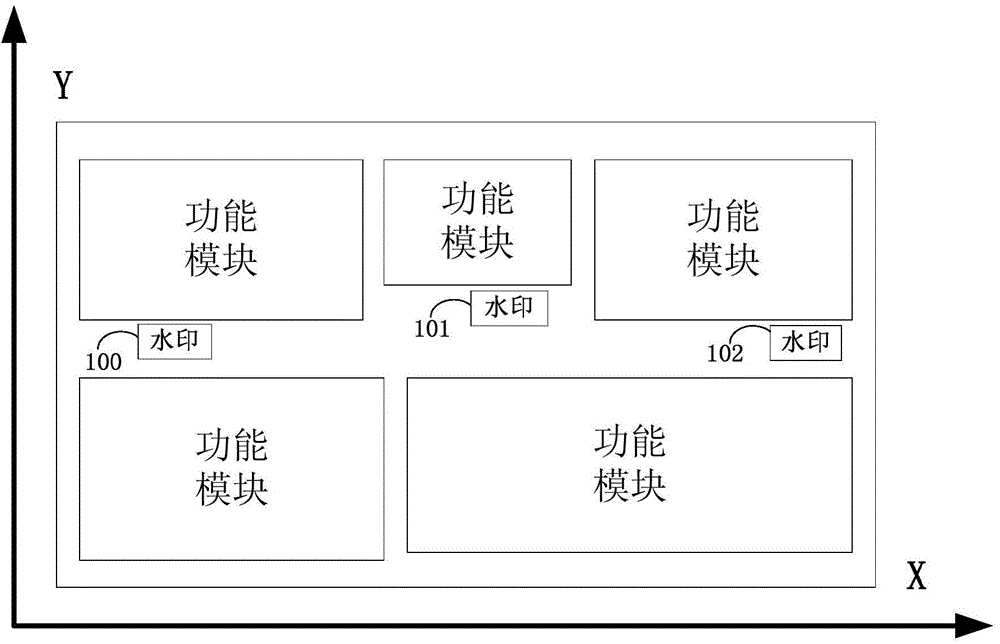
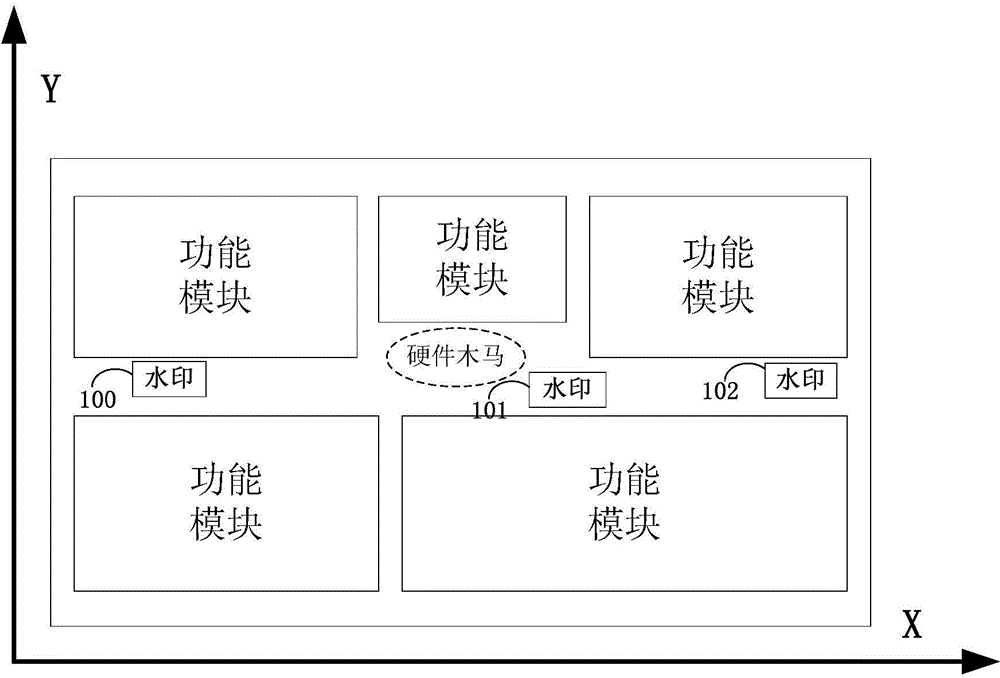
[0043] The main method of the patent of the present invention is not to directly find the hardware Trojan itself, but to indirectly judge whether the inside of the circuit has been modified by checking whether the positions of some signs inside the circuit have changed compared with the original layout.
[0044] When the original circuit is modified, such as adding some logic, the layout of the circuit needs to b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com