An industrial Ethernet communication data encryption transparent transmission module
A technology of communication data and Ethernet, which is applied in the field of industrial control information security, can solve problems such as lack of security strategies, low efficiency, and failure to consider security issues, etc., achieve high code execution efficiency and code density, increase packet data size, reduce The effect of encryption and decryption times
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
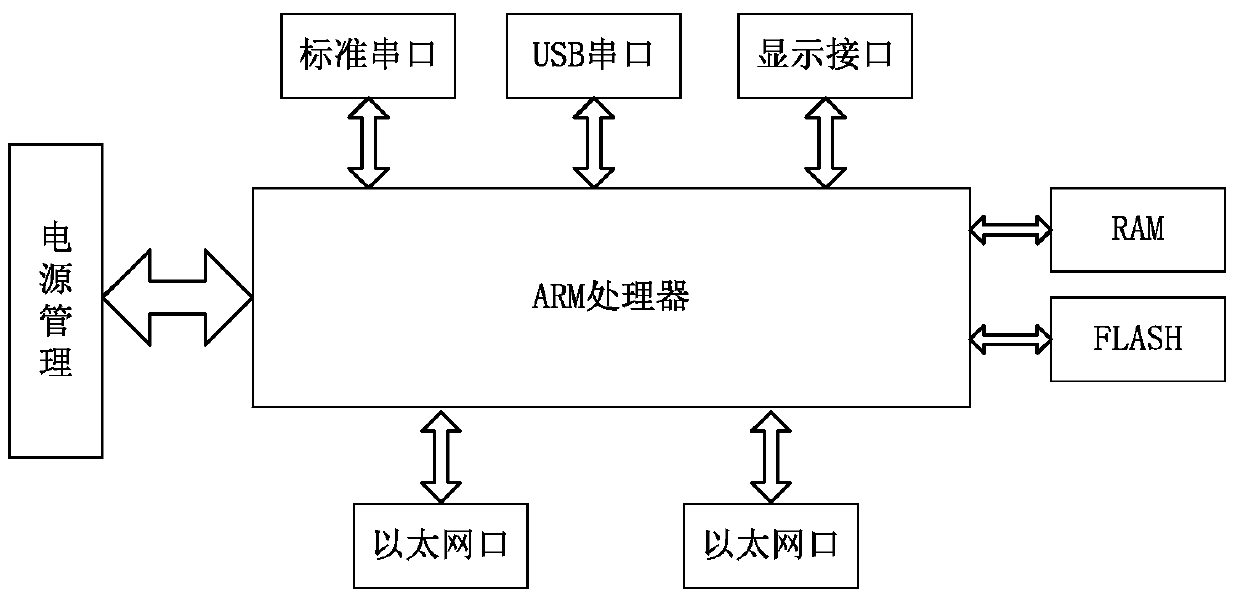
[0021] Embodiment 1, figure 1 It is a functional block diagram of the industrial Ethernet communication data encryption transparent transmission module of the present invention. The core of the module uses a 32-bit ARM Cortex-M0 core, which has strong security features on the one hand, and industry-leading low power consumption performance on the other hand, as well as efficient code execution efficiency and code density based on the ARMv6-M architecture; The chip integrates a variety of secure cryptographic modules, such as HRNG, DES, RSA / ECC, SM1, SM2, SM3, SM4 and other functional and algorithm modules, and provides a crystal-free USB2.0 full-speed interface, ISO7816 master-slave device interface and SPI interface, Support T=0 / T=1 protocol. There are two Ethernet interfaces on the module, and each interface can be realized by switching to RS232, RS485, RS422, CAN, GPRS, WIFI and other interfaces.
[0022] The technical principle of the mixed encryption algorithm of the pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com