Sensitive information protection method based on virtualization technology
A virtualization technology and sensitive information technology, applied in the direction of digital data protection, digital data authentication, etc., can solve the problems of denial of service, incomplete service, inability to realize rights management, etc., to avoid information protection failure and good versatility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] Embodiments of the present invention will be described in further detail below in conjunction with the accompanying drawings.
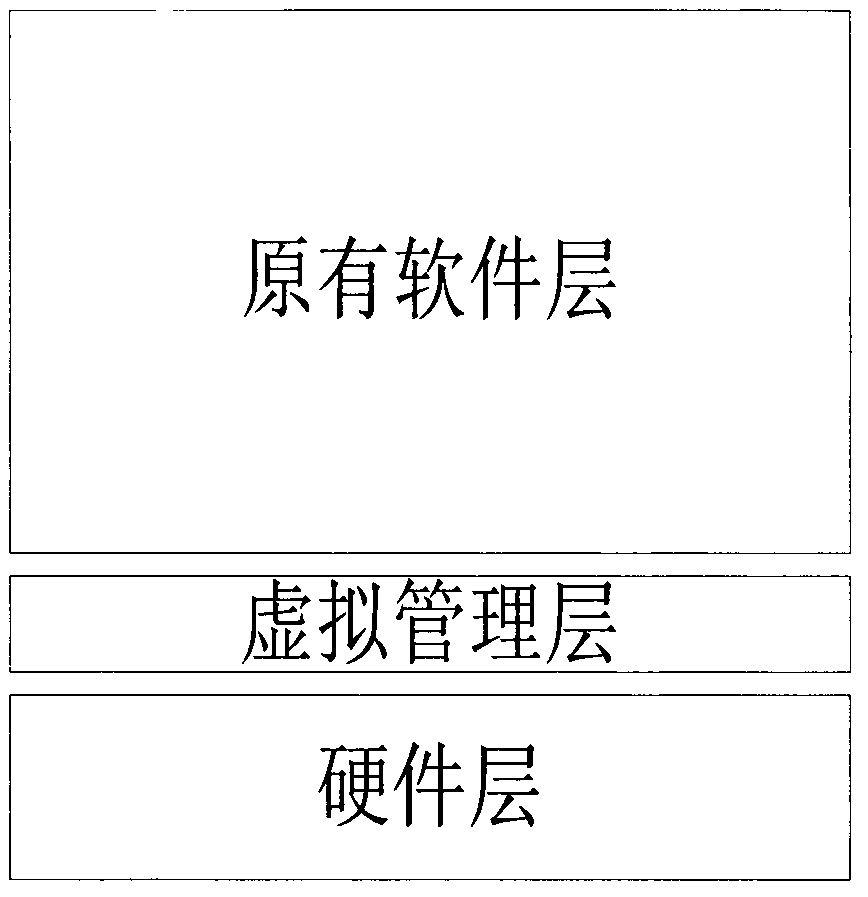
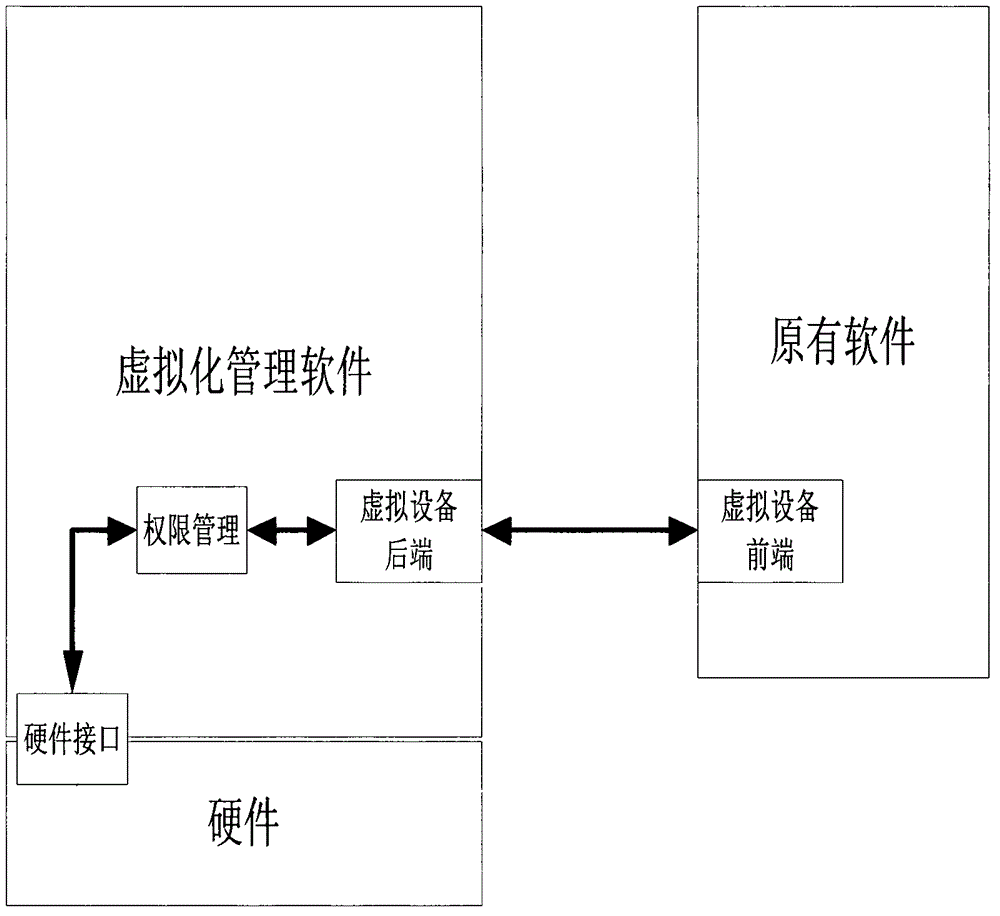
[0029] A sensitive information protection method based on virtualization technology is figure 1 The software layer architecture shown is implemented. The present invention adopts virtualization technology to design virtualized management software (virtual management layer), and the virtual management layer is between the hardware layer and the original software layer to realize seamless compatibility with the upper layer software, without modifying or modifying the upper layer software at all. Minor changes can realize the migration of all the original upper-layer software. The original software system after migration no longer directly exchanges information with the real hardware, but communicates with the virtual hardware interface simulated by the virtualization management layer, and the virtualization management layer realizes the informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com