Method and device for injecting Java bit codes into target process
A target process, bytecode technology, applied in program control design, electrical digital data processing, instruments, etc., to achieve the effect of improving functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
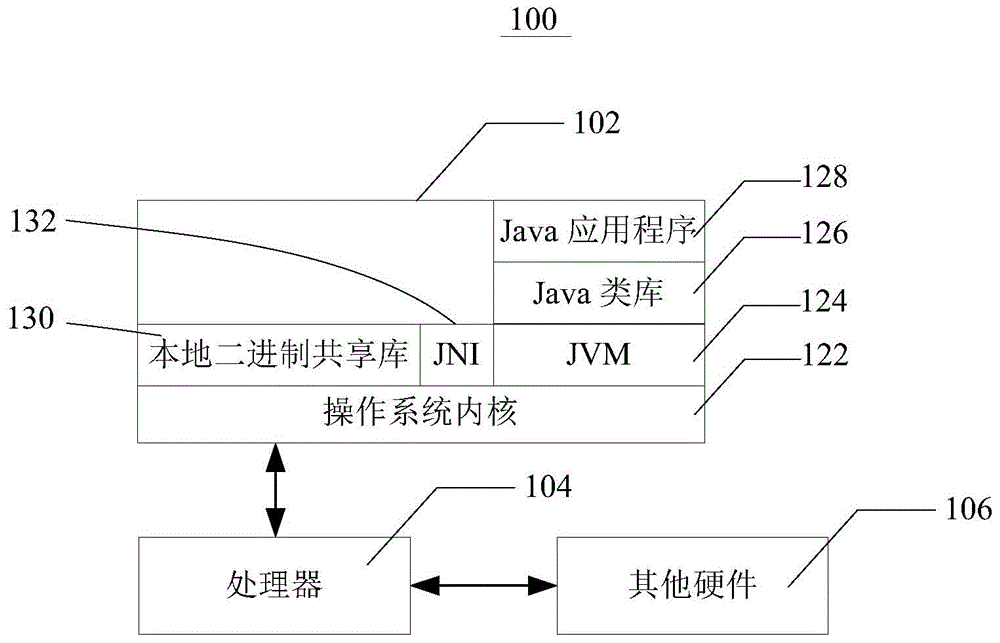
[0025] This embodiment provides a method for injecting Java bytecode into the target process, see figure 2 , the above method includes the following steps:
[0026] Step S101, modify the registers of the target process through the system call provided by the host operating system to load a binary shared library.
[0027] In a computer system, there are two modes in which program code runs, one is user mode and the other is kernel mode. Applications in the application layer run in user mode, while device drivers and file systems run in kernel mode. Programs running in user mode are strictly managed and do not disrupt system-level applications. Programs running in kernel mode have full access to the computer. A system call is when code running in kernel mode provides services to code running in user mode.
[0028] Taking the Linux system as an example, its system call is implemented through int80h, and the system call is used to distinguish the entry function. The basic pr...
no. 2 example
[0036] This embodiment provides a method for injecting Java bytecode into the target process, which is similar to the method of the first embodiment, the difference is that the method of this embodiment is applied to running the Android (Android) operating system on the device.
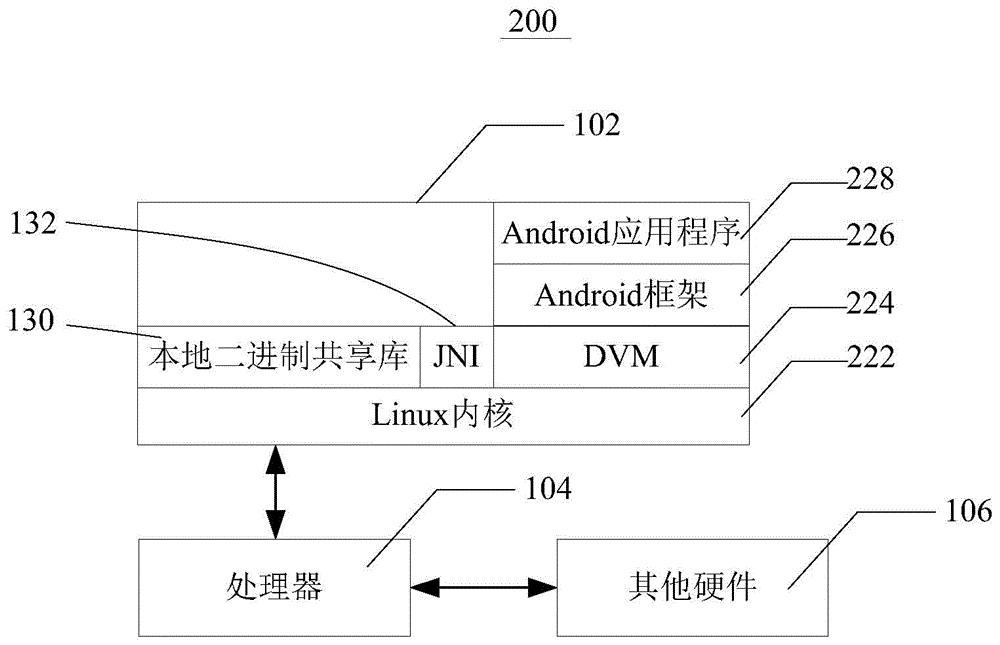
[0037] refer to image 3 , which is a schematic diagram of an Android device architecture. Such as image 3As shown, the Android device 200 includes: a memory 102, a processor 104, and other hardware 106, which are compatible with figure 1 It is similar to what is shown, and can be referred to the above description together.
[0038] image 3 The software programs and modules in the memory 102 may include, for example: Linux kernel 222 , Delvik virtual machine 224 , Android framework 226 and Android application program 228 . The Linux kernel 122 directly controls various hardware. A Delvik virtual machine (Delvik Virtual Machine, DVM) 224 runs on the system kernel 222 . JVM124 is a stack machin...
no. 3 example
[0049] This embodiment provides a device for injecting Java bytecode into the target process, see Figure 5 , which includes: a local injection module 31, and a Java bytecode loading module 32.
[0050] The local injection module 31 is configured to modify the registers of the target process through a system call provided by the host operating system to load a binary shared library.
[0051] The Java bytecode loading module 32 is stored in the binary shared library, and is automatically executed along with the loading of the binary shared library. The Java bytecode loading module 32 is used to load the file containing the Java bytecode of the specified path into the virtual machine, and call the entry function in the file containing the Java bytecode. The Java bytecode includes specific logic codes to realize specific functions.
[0052] For other details of the device in this embodiment, please refer to the first embodiment.
[0053] According to the method of this embodim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com