Identity authentication system and method thereof
A technology of identity authentication and authentication code, applied in the direction of digital data authentication, etc., can solve problems such as insufficient consideration in practice, and achieve the effect of increasing difficulty and reducing risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0087] Relevant detailed description and technical contents of the present invention are described as follows with regard to matching drawings now.
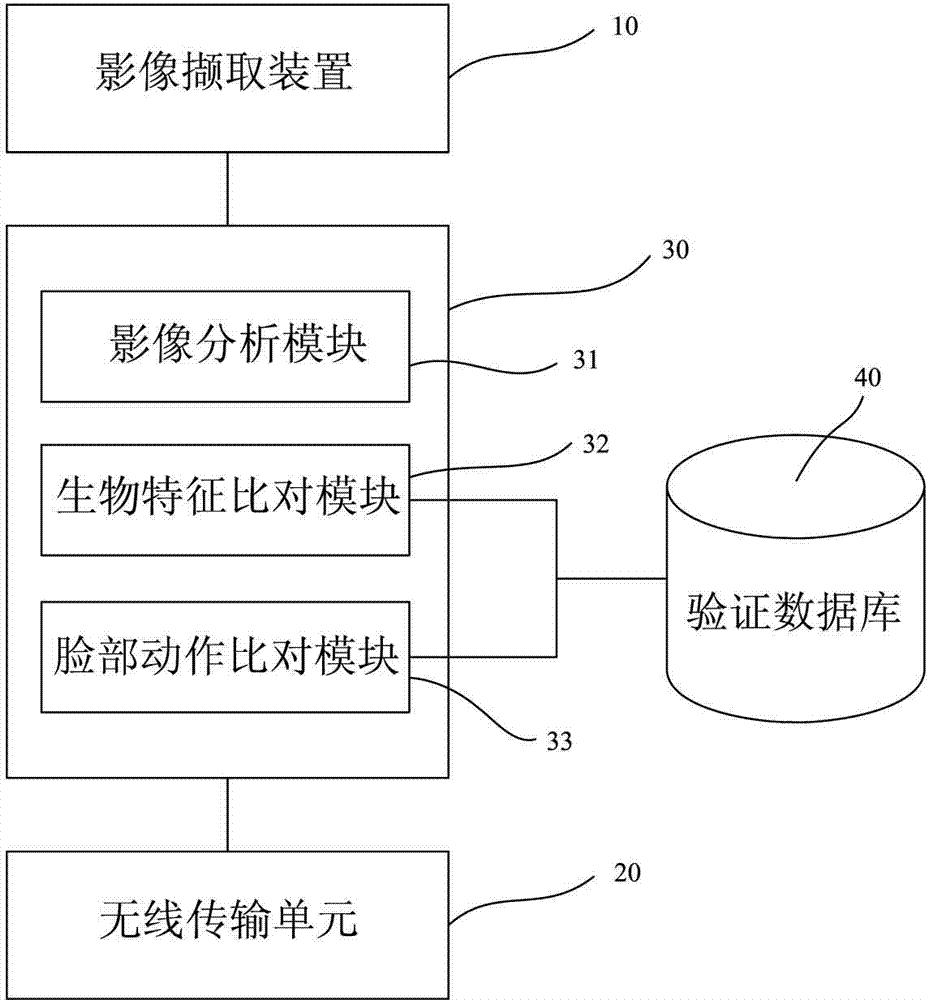
[0088] see figure 1 , is a schematic block diagram of the identity authentication device of the present invention, as shown in the figure: the present invention provides an identity authentication system for performing identity authentication on a user so as to determine whether the user is a legitimate user. The identity authentication system mainly includes an image capture device 10 for obtaining multiple user images, a verification database 40 storing pre-stored biometric templates and action information authentication codes, and a verification database 40 for processing images and targeting the above-mentioned A processing unit 30 for comparing authentication codes, and a wireless transmission unit 20 (such as Figure 9 shown). The image capture device 10 can be a general planar camera, an active depth camera (Active Depth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com