An Identity-Based Data Storage Method and Integrity Verification Method in Cloud Computing
A technology for integrity verification and data storage, applied in user identity/authority verification, electrical components, transmission systems, etc., to achieve efficient data integrity protection and security assurance, low communication overhead, and fewer rounds of interaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to make the purpose, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the implementation methods and accompanying drawings.
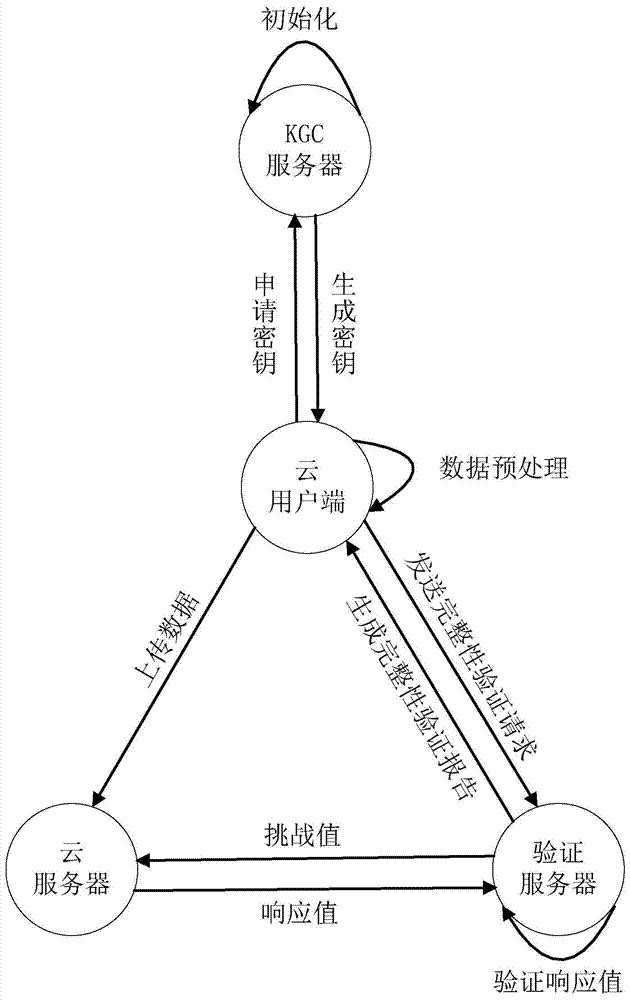
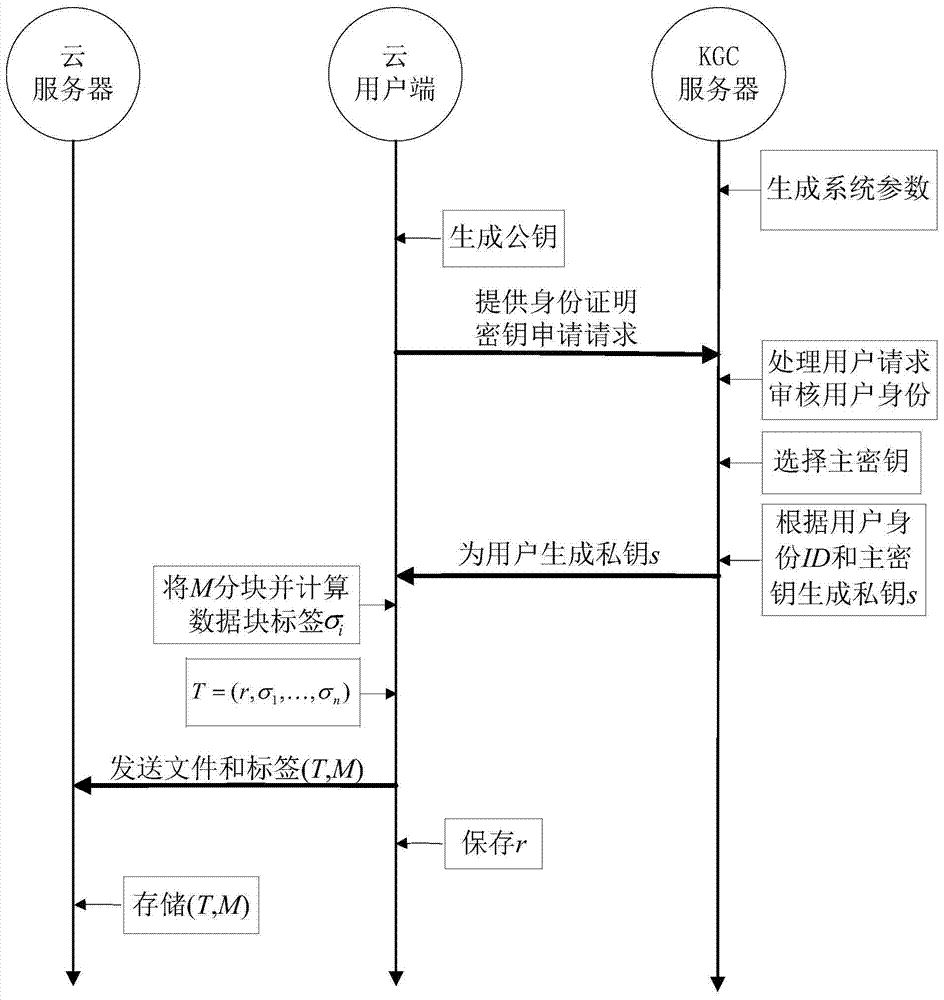
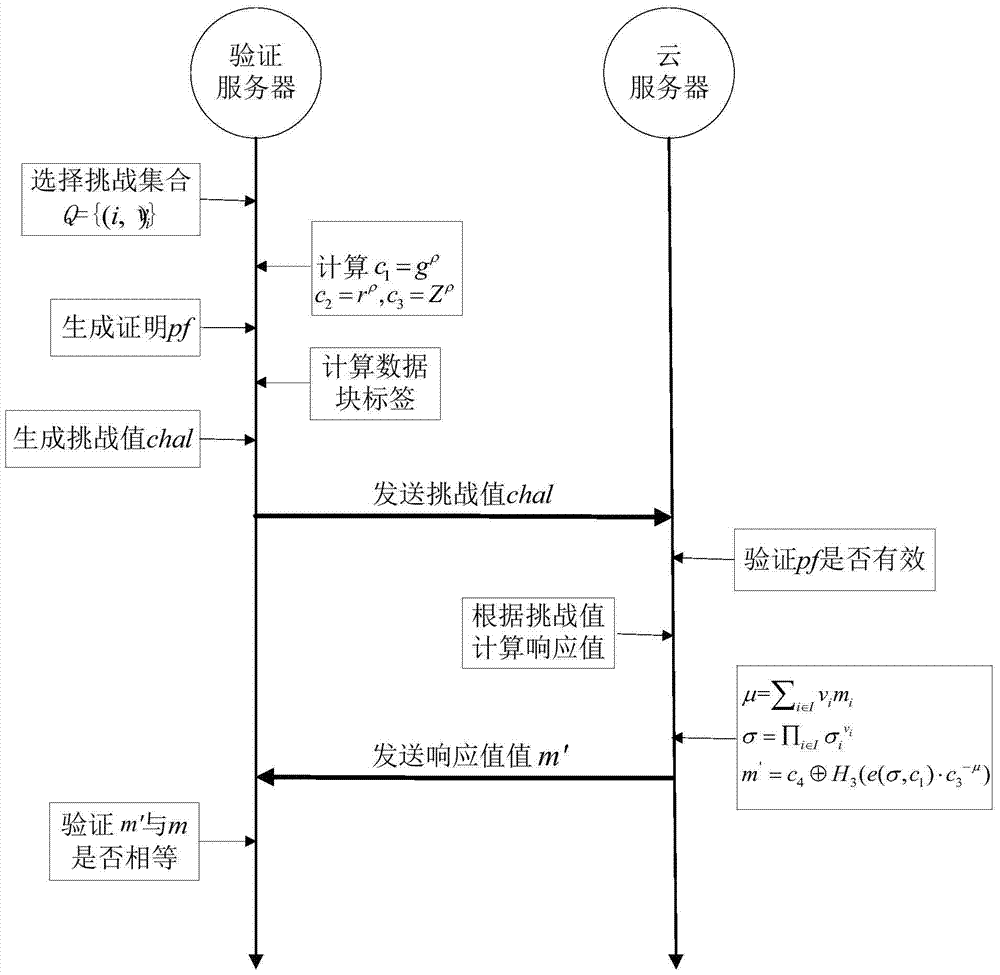
[0043] Based on the identity-based public key cryptography theory, the present invention proposes an identity-based data storage and integrity verification method in cloud computing, which is applied to a cloud storage environment with high security requirements. The cloud user uses the private key generated by the KGC server to calculate the data block label of the file to be uploaded to ensure the integrity of the data. When the cloud user wants to verify the integrity of the cloud data, the verification server uses the challenge response method to verify the data in the cloud server. data, in order to realize an efficient remote data verification mechanism and zero-knowledge privacy protection, the present invention uses aggregatable ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com