Server fingerprint mimicry and sensitive information mimicry method based on WEB security gateway
A sensitive information and security gateway technology, applied in the field of computer network security, can solve problems such as lack of active response methods and powerlessness, and achieve the effects of good scalability, leakage prevention, and flexible configuration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The purpose and effects of the present invention will become more apparent by describing the present invention in detail below with reference to the accompanying drawings.
[0037] A method of server fingerprint mimicry and sensitive information mimicry based on the WEB security gateway of the present invention comprises the following steps:
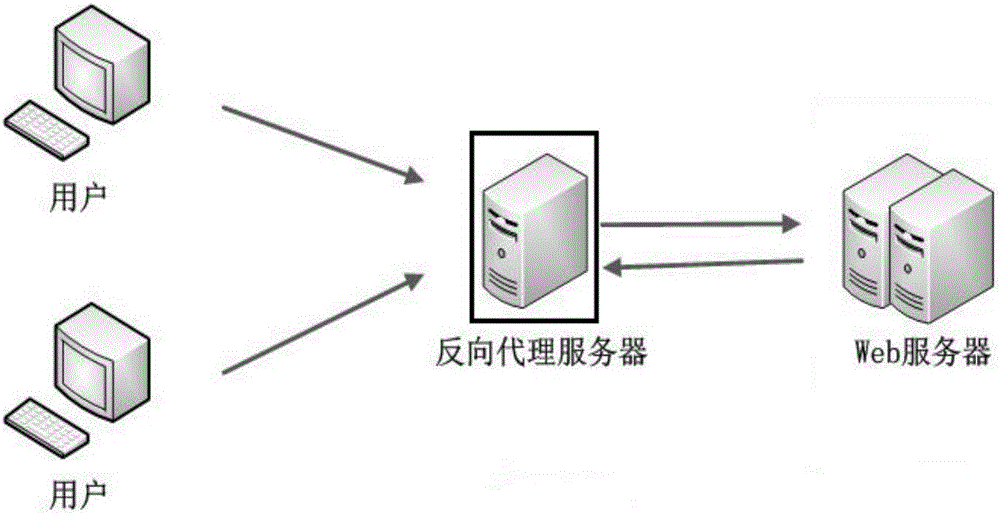
[0038] Step 1: Build a reverse proxy server between the real web server and the user, and the reverse proxy server is implemented based on Nginx. The forwarding and routing rules are set on the reverse proxy server, and then the message transmission between the user and the Web server is processed and forwarded by the reverse proxy server, and the reverse proxy server is transparent to the user and the server; network topology The picture is attached figure 1 ;
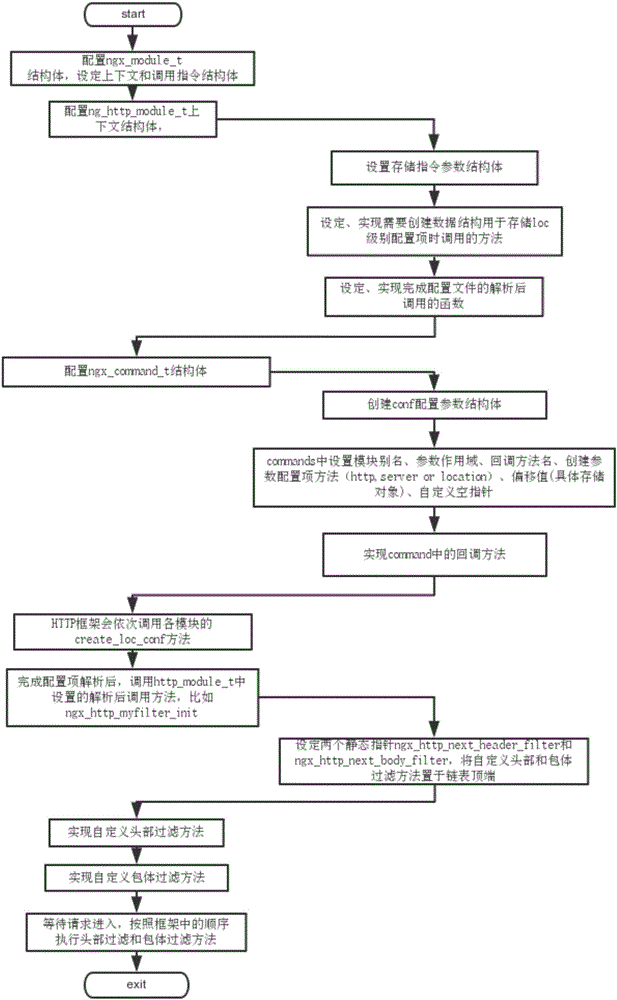
[0039]Step 2: Configure the mimic security gateway module on the reverse proxy server, including the web server fingerprint information mimic module and the sensitive i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com