Authentication method, authentication device and authentication system
An authentication method and authentication system technology, applied in the field of authentication methods and device systems, can solve the problems of inconvenient implementation and insufficient security of the authentication mechanism, and achieve the effect of eliminating security problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. It should be understood that the preferred embodiments described below are only used to illustrate and explain the present invention, and are not intended to limit the present invention.
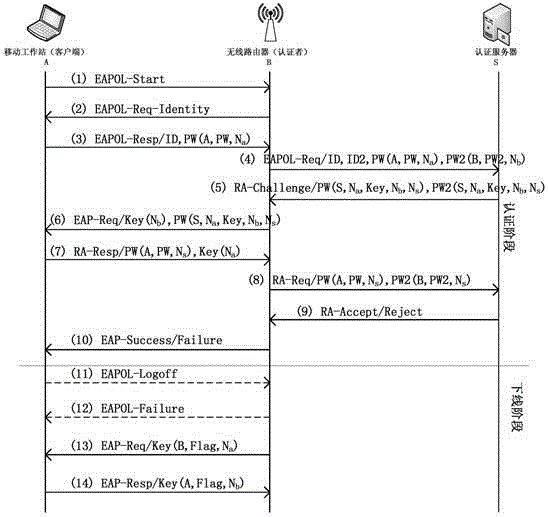
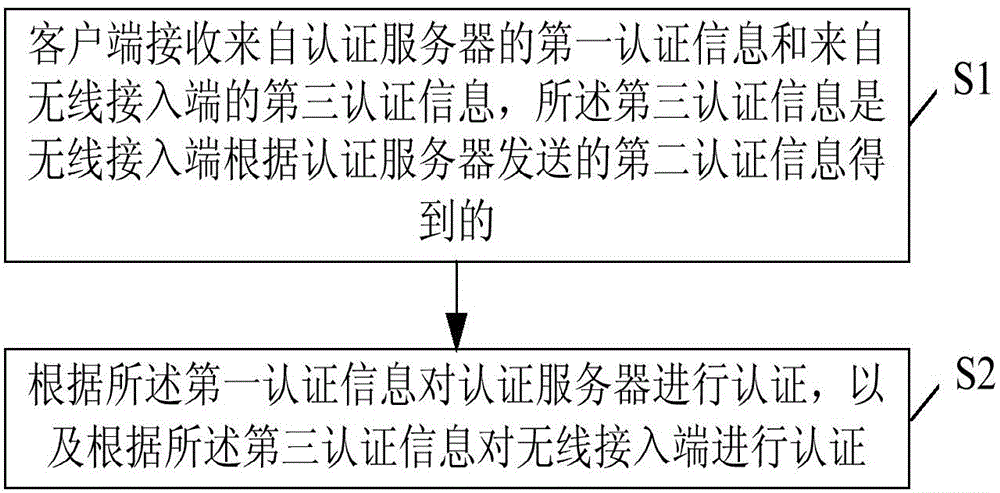
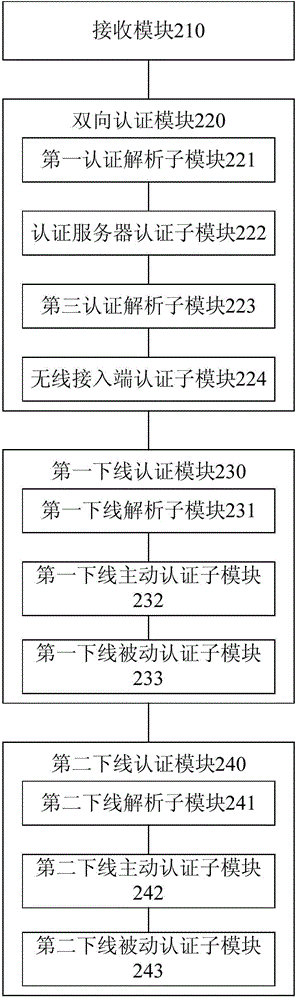
[0062] figure 1 is a schematic diagram of the authentication method provided by the embodiment of the present invention, such as figure 1 As shown, the specific steps are as follows:
[0063] Step S1: the client receives the first authentication information from the authentication server and the third authentication information from the wireless access terminal, the third authentication information is obtained by the wireless access terminal according to the second authentication information sent by the authentication server.
[0064] In step S1, the first authentication information is the authentication information used by the client to authenticate the...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap