Electric power scheduling system and business monitoring method for the same
A power dispatching and business technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as inundation of safety information and alarm events, failure to repair in time, and increased maintenance costs, so as to save the time needed to find the cause of the problem. time, improve the quality of business monitoring, and avoid the effect of noise pollution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
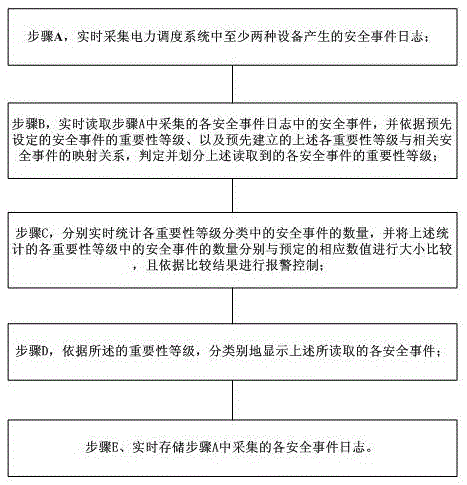
[0049] Such as figure 1 , 3 As shown, a business monitoring method for a power dispatching system of the present invention includes:
[0050] Step A, collecting security event logs generated by at least two devices in the power dispatching system in real time: in this embodiment, the devices include firewalls, intrusion detection systems, anti-virus software, network devices, operating systems, and databases;
[0051] Step B, read the security events in each security event log collected in step A in real time, and based on the preset importance levels of security events, and the pre-established mapping relationship between the above-mentioned importance levels and related security events, Determine and classify the importance level of each security event read above; the importance level includes level I, level II and level III;
[0052] Step C, respectively counting the number of security events in each importance level classification in real time, and comparing the number o...
specific Embodiment approach 2
[0072] The difference from specific embodiment 1 is that in the business monitoring method for power dispatching system described in this specific embodiment: in step D, for each importance level classification, each security event is reported in the form of a report Statistics show. This facilitates the centralized management, centralized monitoring and effective auditing of the dispatching system business, which is more practical.
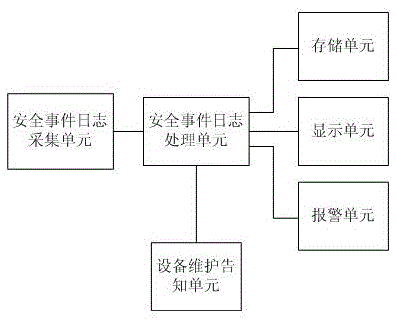
[0073] The difference from specific embodiment 1 is that in the service monitoring system for power dispatching system described in this specific embodiment: for the security event log processing unit, it is also used to call the display unit to display each of the importance levels The various security events classified are displayed in the form of reports, so as to facilitate the centralized management, centralized monitoring and effective audit of the dispatching system business; in addition, the business monitoring system for the power dispat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com