DGA domain name detection method based on random forest
A random forest algorithm and domain name detection technology, applied in the field of network security, can solve the problems of high false negative or false positive rate, poor generalization of the method, high cost, high operating efficiency, good generalization performance, and resource utilization. less effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solutions of the present invention more clearly, but not to limit the protection scope of the present invention.
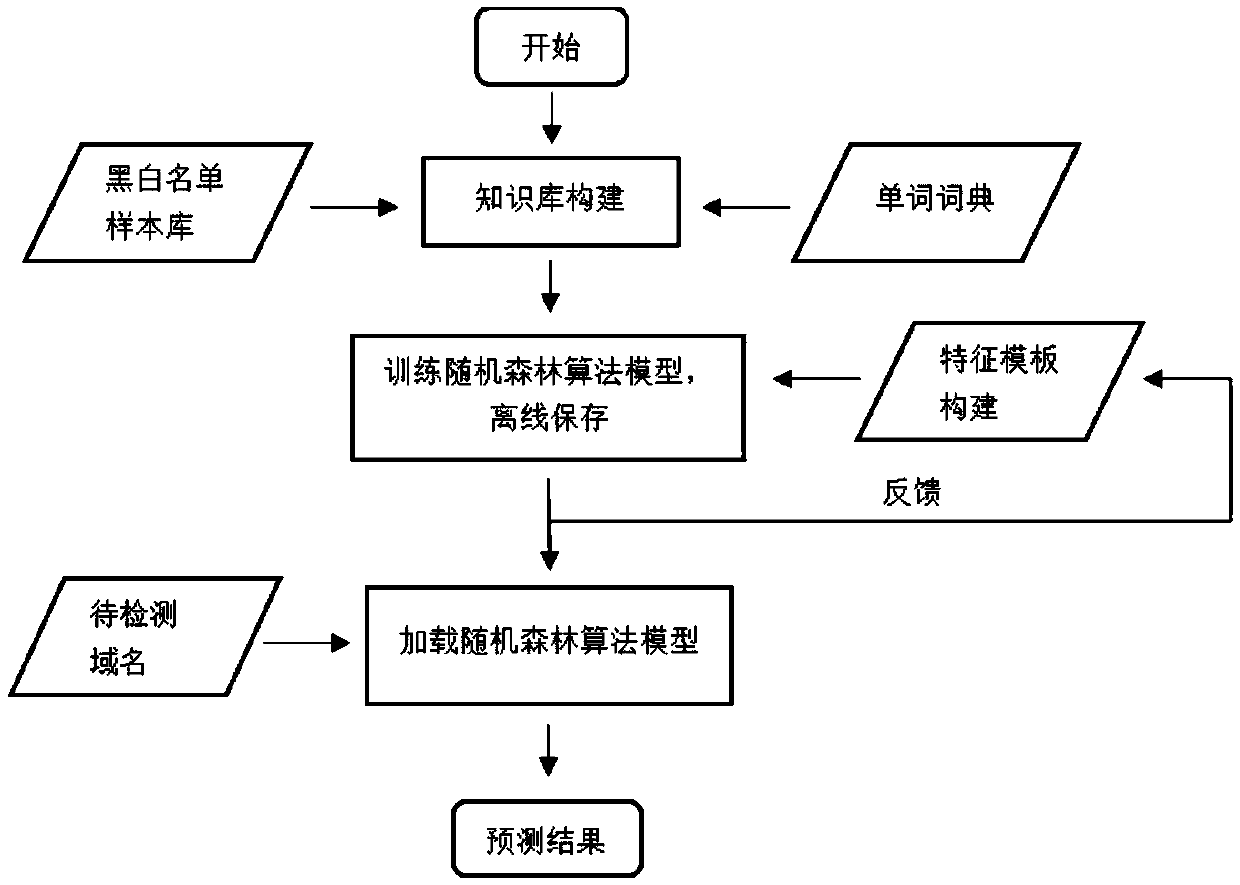
[0047] Such as figure 1 As shown, the DGA domain name detection method based on random forest includes the following steps:
[0048] Step 1, building a knowledge base, including building a black-and-white list sample library and a word dictionary.
[0049] The blacklist refers to malicious domain names obtained through open source channels, such as: malicious URLs published by Security Alliance Website Exposure Platform, malicious URL database published by Kingsoft Web Shield, MalwareDomainList, MalwareDomains, PhishTank, hpHosts, and CyberCrimeTracker malicious domain names list.
[0050] The white list refers to legal domain names obtained through open source channels, such as Alexa website...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com