Real-time webpage Trojan detection method based on dynamic content analysis
A web Trojan, real-time detection technology, applied in instrumentation, digital data processing, platform integrity maintenance, etc., can solve the problems of confusing true intentions, easy to generate false negatives in static analysis, and achieve the effect of overcoming negative effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The specific implementation of the present invention will be further described in detail in conjunction with the accompanying drawings.
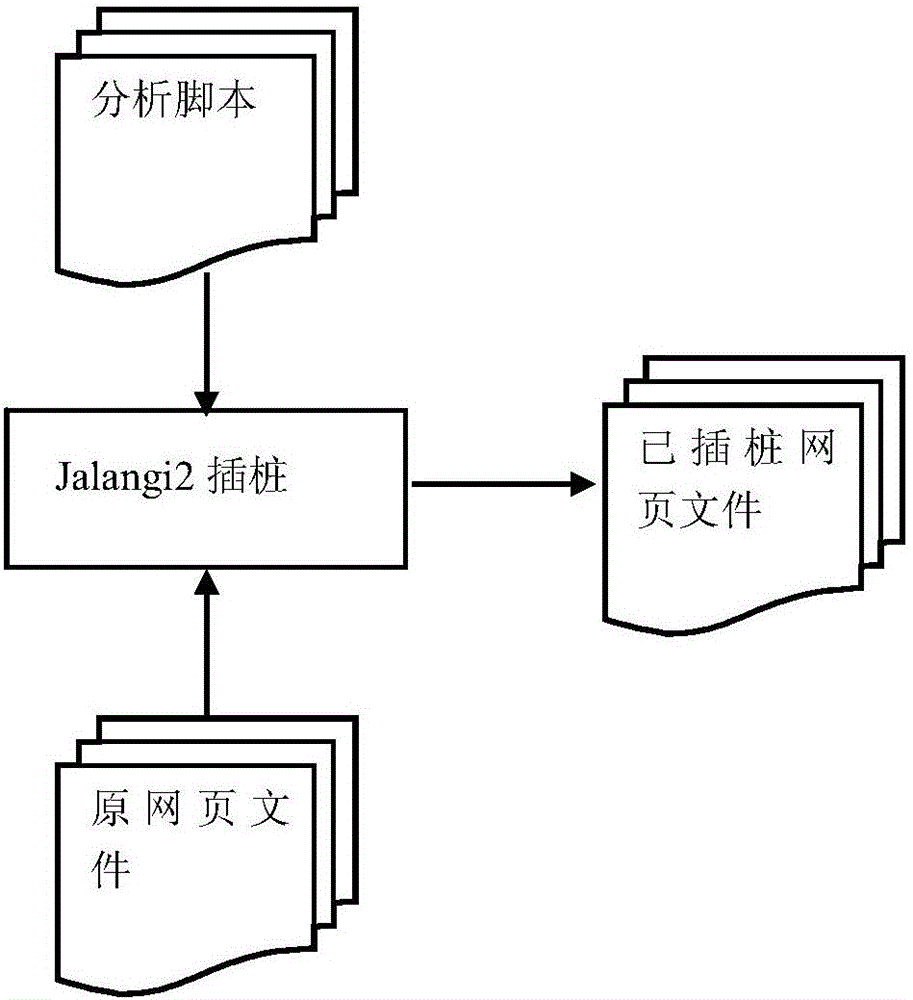
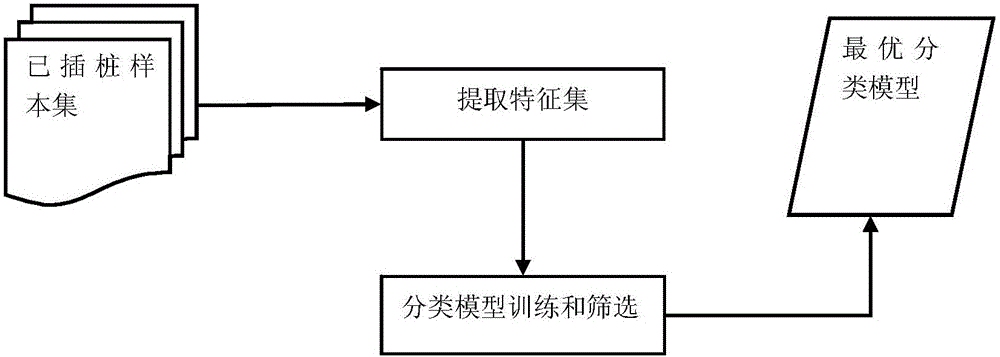
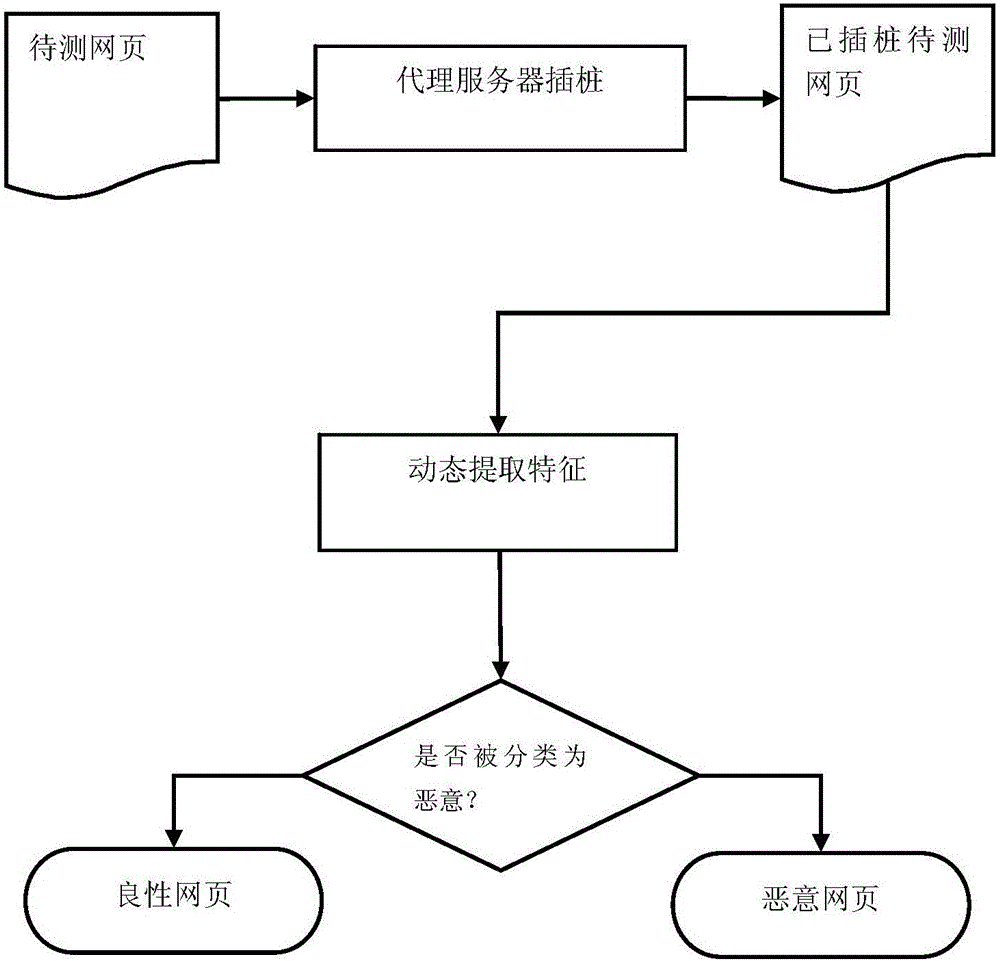
[0029] The present invention provides an embodiment of real-time detection of web page Trojan based on dynamic content analysis. This embodiment is a method for detecting Drive-by Download attacks implemented by JavaScript scripts, that is, web page Trojan horse attacks. Use JavaScript dynamic analysis software, preferably Jalangi2, to insert JavaScript code in the webpage, track string operations and extract a series of relevant behavioral features during the code running process, use the pre-trained classification model to classify, and judge whether the webpage is Perform a web Trojan horse attack.
[0030] Step 1) Collect a certain amount of malicious webpage set M and benign webpage set B to form sample libraries respectively.
[0031] Step 1.1) Obtain a certain number of top-ranked website homepages from Alexa to form a benign...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com