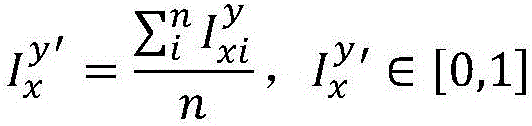Network safety management system based on alarm strategy
A network security and management system technology, applied in transmission systems, electrical components, etc., can solve the problems of lack of correction and management of alarm information, unimportant, outdated, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
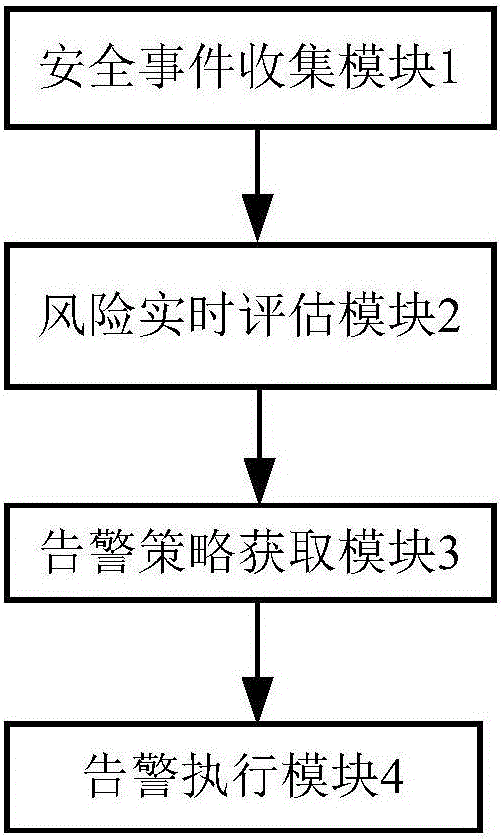
[0045] see figure 1 , figure 2 , the network security management system based on the alarm policy in this embodiment includes a security event collection module 1, a risk real-time assessment module 2, an alarm policy acquisition module 3 and an alarm execution module 4 connected in sequence; the security event collection module 1 is used to pass The network security device performs normalization processing on the security log, generates a security event, and collects the security event; the risk real-time assessment module 2 is used to assess the risk of the security event; A security event with a risk threshold sends out warning information; the warning strategy acquisition module 3 is used to receive the warning information and obtain a corresponding warning strategy; the warning execution module 4 is used to execute the warning according to the warning strategy.
[0046] The risk real-time assessment module 2 includes:
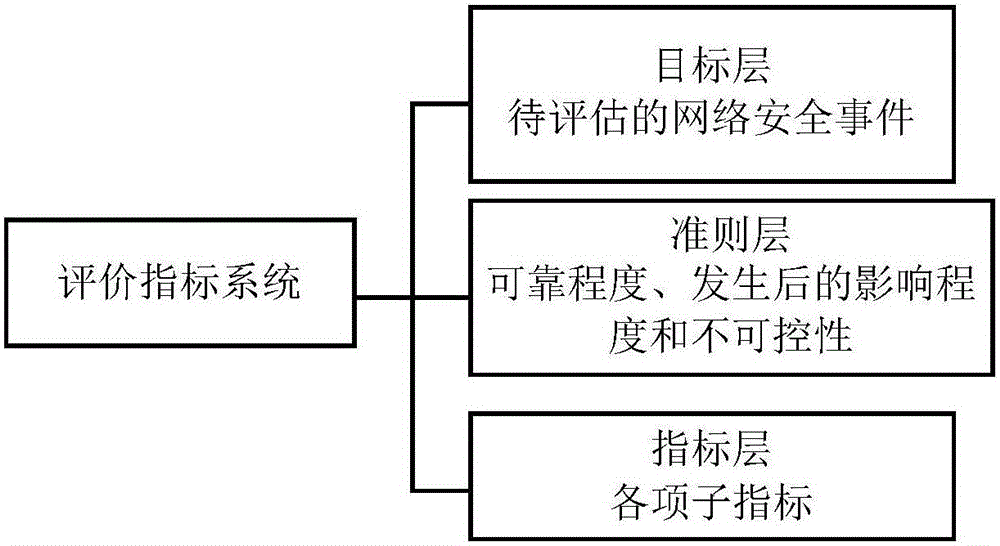
[0047] (1) An evaluation index system generation ...
Embodiment 2
[0057] see figure 1 , figure 2 , the network security management system based on the alarm policy in this embodiment includes a security event collection module 1, a risk real-time assessment module 2, an alarm policy acquisition module 3 and an alarm execution module 4 connected in sequence; the security event collection module 1 is used to pass The network security device performs normalization processing on the security log, generates a security event, and collects the security event; the risk real-time assessment module 2 is used to assess the risk of the security event; A security event with a risk threshold sends out warning information; the warning strategy acquisition module 3 is used to receive the warning information and obtain a corresponding warning strategy; the warning execution module 4 is used to execute the warning according to the warning strategy.
[0058] The risk real-time assessment module 2 includes:
[0059] (1) An evaluation index system generation ...
Embodiment 3
[0069] see figure 1 , figure 2 , the network security management system based on the alarm policy in this embodiment includes a security event collection module 1, a risk real-time assessment module 2, an alarm policy acquisition module 3 and an alarm execution module 4 connected in sequence; the security event collection module 1 is used to pass The network security device performs normalization processing on the security log, generates a security event, and collects the security event; the risk real-time assessment module 2 is used to assess the risk of the security event; A security event with a risk threshold sends out warning information; the warning strategy acquisition module 3 is used to receive the warning information and obtain a corresponding warning strategy; the warning execution module 4 is used to execute the warning according to the warning strategy.
[0070] The risk real-time assessment module 2 includes:
[0071] (1) An evaluation index system generation ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com