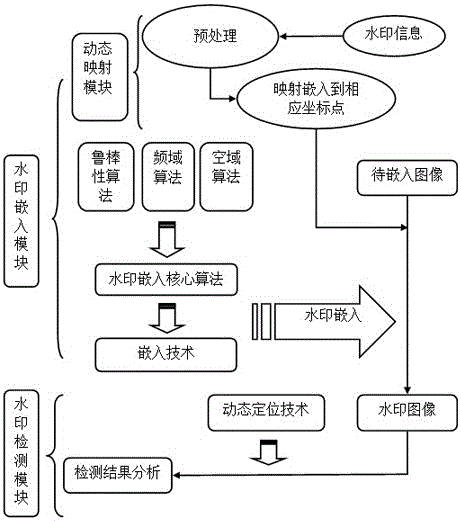
Image encryption method based on digital watermark
A technology of digital watermarking and encryption method, applied in image data processing, image data processing, instruments, etc., can solve the problem of repeated embedding of digital watermarks, etc., and achieve the effect of high data capacity and good robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
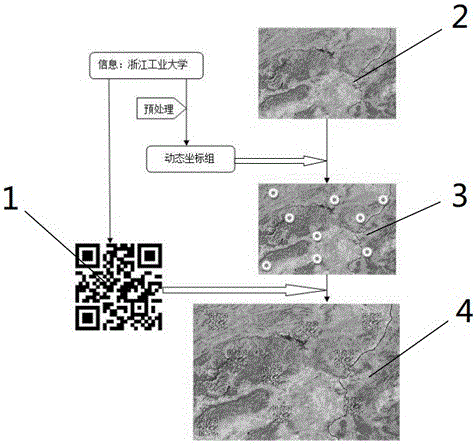
[0045] Referring to the accompanying drawings, in this embodiment, "Zhejiang University of Technology" is used as encrypted information to overwrite and encrypt the image with a watermark.
[0046] Specifically use the following:
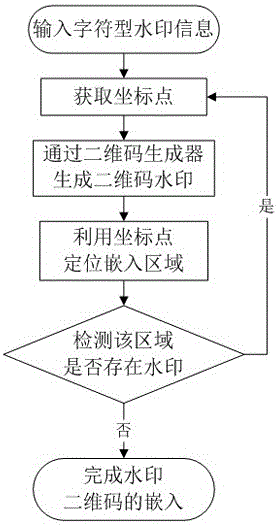
[0047] Step a, get coordinate points:
[0048] Step a1, given the watermark information sequence W "Zhejiang University of Technology", W={B 0 , B 1 , B 2 , B 3 , B 4, ..., B n},in, n is the message length 5, B 0 For "Zhejiang", B 1 is "Jiang", and so on, B5 is "Study";
[0049] Step a2, put B n The ASCII value is converted to an 8-bit byte string K=( k 0 , k 1 , ..., k i ), k i The value of is 0 or 1, i =7:
[0050] Convert the ASCII value of "浙" to an 8-bit byte string K=(01001011), and the corresponding ASCII values of the other characters are as follows:
[0051] Zhejiang: 01001011
[0052] Jiang: 01001011
[0053] Worker: 01001011
[0054] Industry: 01001011
[0055] Big: 01001011
[0056] School: 01001011
[0057...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com