Android application program code protection mechanism identification method
A protection mechanism and application technology, applied in the field of cyberspace security, can solve problems such as increasing the difficulty of project decompilation, obfuscating code, etc., and achieve the effects of facilitating supervision, providing efficiency, and ensuring reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
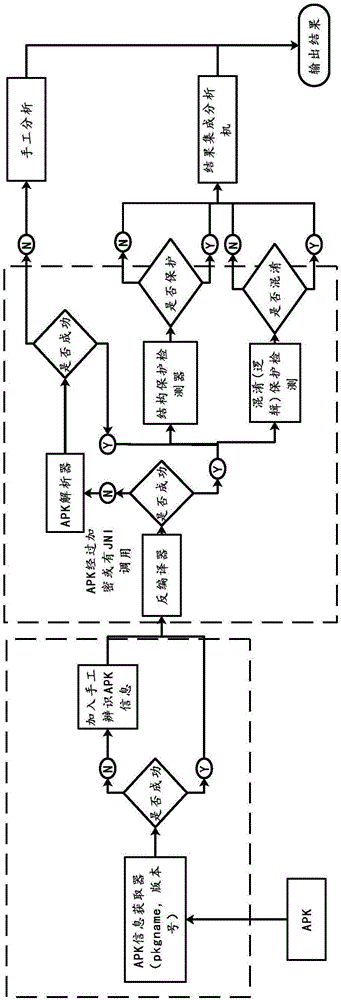
[0042] The Android application code protection mechanism identification method of the present invention first loads the APK file installation package, decompiles the APK package one by one, and then scans the decompiled files to check whether they have undergone measures such as code obfuscation and code encryption. Such as figure 1 Specifically, it includes the following steps:
[0043] Step 1: Load the APK package and read the APK package file according to the path. The loading of the APK package can be completed through the path loader, and the path loader can be written and realized by using the file operation box that comes with the Java language.
[0044] Step 2: Perform preliminary reverse engineering and decompilation of the APK package, and determine and obtain key information such as the installation package name and version of the APK. If it is successful, go to step three; if it is not successful, go to step six after adding the manual identification label. The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com