Host real-time identification method based on distributed analysis of application traffic
A technology of application programs and identification methods, applied in the direction of digital transmission systems, electrical components, transmission systems, etc., can solve problems such as inability to guarantee system reliability, failure to obtain better recognition rates, weak host identification technology capabilities, etc., to achieve good reliability Scalability, improved processing capability, good concealment effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further illustrated below in conjunction with specific embodiments, and it should be understood that the following specific embodiments are only used to illustrate the present invention and are not intended to limit the scope of the present invention.
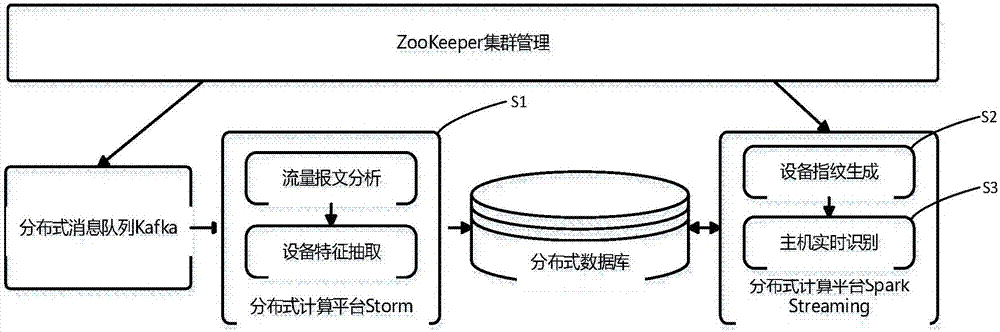
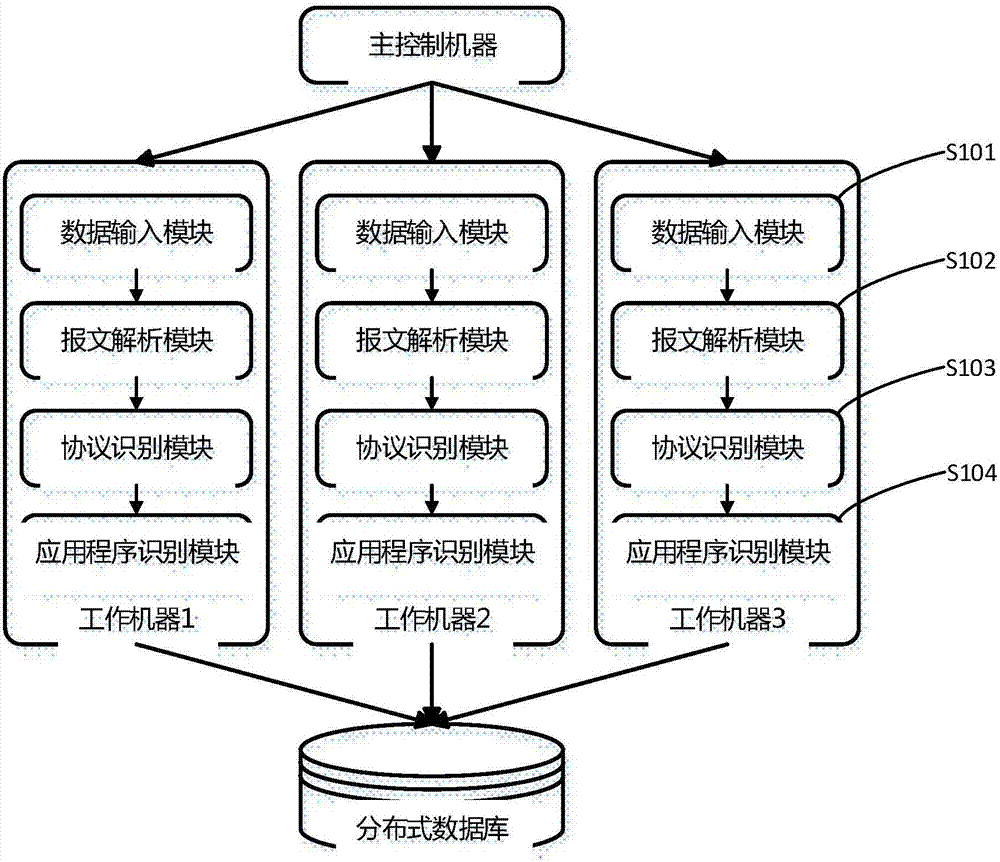
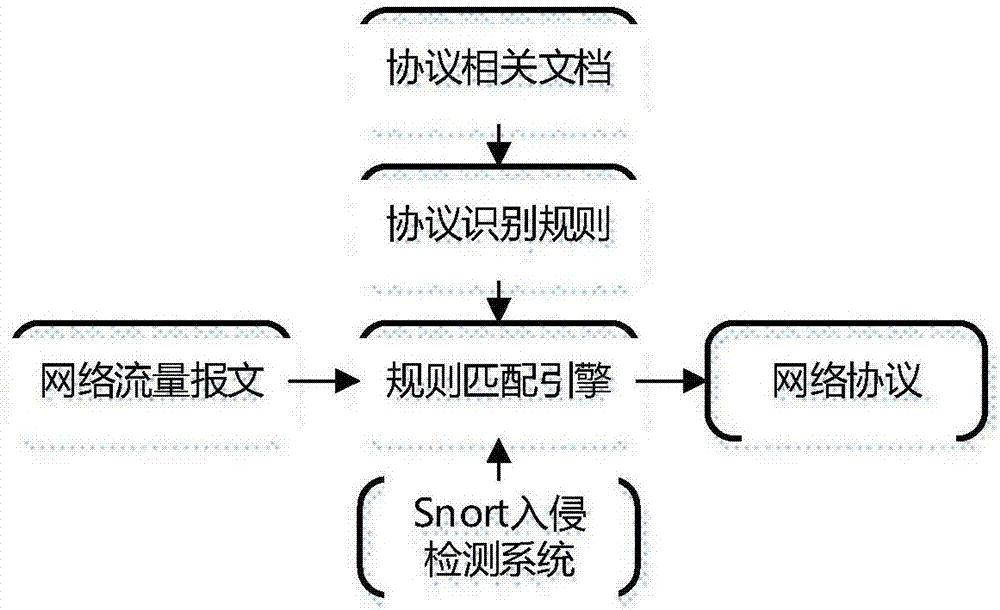
[0031] see figure 1 As shown, an embodiment of the present invention provides a method for real-time identification of a host based on a distributed computing platform design. Firstly, based on the distributed computing platform Storm, the traffic packets are read from the distributed message queue, the analysis and processing of the traffic packets are completed, and the characteristic data are extracted and stored in the distributed database, and then the device is generated by combining the characteristic data of the devices Fingerprint, and based on Spark Streaming technology to complete the classification of device fingerprints, to achieve real-time identification of the host. The spec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com